Twitter’s Latest Security Breach Reveals the Value of a Proactive Compliance Program
You’ve likely already heard about Twitter’s latest data breach, which allowed scam-filled messages to be sent from some of the most prominent people on the platform, including Elon Musk, Joe Biden, Barack Obama, Jeff Bezos, and Kanye West. If your organization is highly security conscious, your security team may have already conducted a review of user access to key internal systems to avoid falling victim to the same type of security breach.
Although specifics of how the attack happened are still not confirmed, what’s interesting about this particular breach is that it was not another case of Twitter users being careless with their credentials. It was the result of security vulnerabilities within Twitter’s internal systems and missteps made by employees.
Twitter announced on Wednesday night that it suspected that several employees who had access to internal systems had their accounts compromised in a “coordinated social engineering attack,” a spokesman said, referring to attacks that trick people into giving up their credentials. The attackers then used Twitter’s internal systems to tweet from high-profile accounts like Mr. Biden’s.
“We’re looking into what other malicious activity they may have conducted or information they may have accessed,” Twitter’s spokesman added. “We’ve taken significant steps to limit access to internal systems and tools while our investigation is ongoing.”
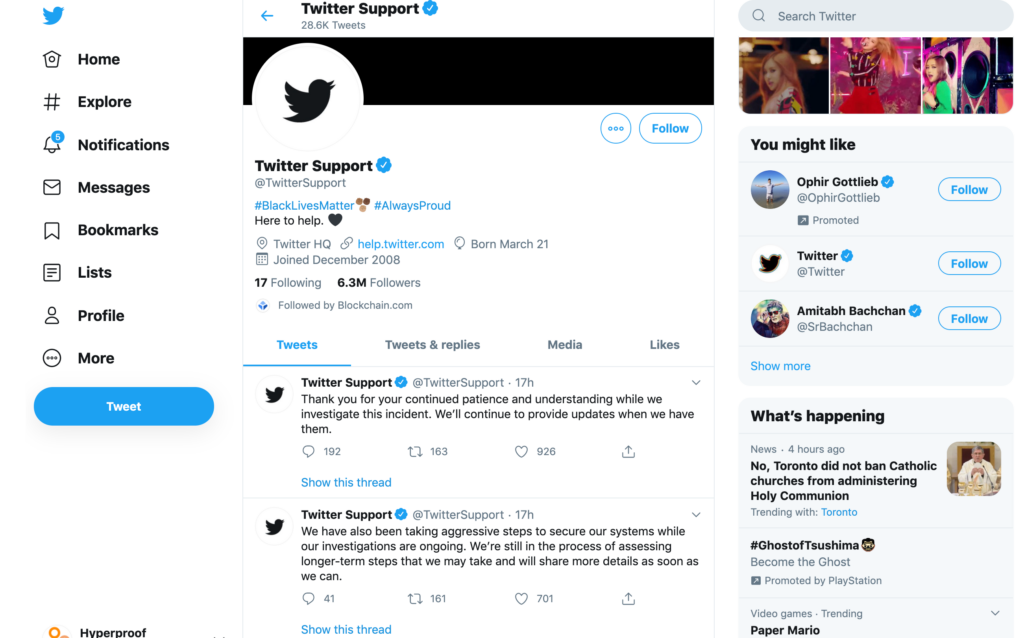
Further, Twitter has indicated to Vice’s Motherboard, a tech publication, that whoever was behind the breach had gotten someone inside Twitter to provide the access willingly. Motherboard reported that people who claimed responsibility for the attack had worked with someone at Twitter and that one person even said the Twitter employee was paid for the access.
The Twitter breach highlights the value of proactive compliance
Twitter’s latest security breach has shown that being occasionally compliant (or having a “paper-only” compliance program) is simply not an option anymore for any company.
Here’s what we mean by this statement: Many organizations understand the value of having a compliance program, but many of them are not following through on their compliance programs in a way that creates meaningful change.
They know that cybersecurity experts from organizations like NIST, ISO, and AICPA have created guidelines they can follow to protect their information systems and networks from common threats, intrusions, and the errors made by their employees and contractors. For instance, several cybersecurity frameworks include requirements for reviewing user access rights to internal systems on a regular basis and limiting user access to internal systems on a need-to-know basis. The reason this requirement exists is because security experts know that organizations shouldn’t underestimate the role that human weaknesses play in data breaches.
Many organizations make efforts to abide by these compliance frameworks; compliance teams conduct risk assessments, create internal controls (e.g. policies, procedures) to mitigate risks to an acceptable level, and ask employees to incorporate these controls into their day-to-day work. However, employees get busy, and sometimes they forget. This means that even though an organization might have a strong compliance program in theory, it isn’t always being carried out the way it should be.

According to recent research from NetRix, 54% of surveyed IT pros said they do not follow the security best practice of reviewing user access rights to data on a regular basis. Assuming this data is directionally correct, this should raise alarm bells for a corporate compliance team, because it means that system administrators are ignoring compliance 54% of the time.
Although Twitter hasn’t confirmed how the breach occurred, it has announced that it suspected that several employees who had access to internal systems had their accounts compromised in a “coordinated social engineering attack”.
This raises some questions: Did these employees truly need access to these internal systems to do their jobs? Did anyone in IT security review these employees’ access privileges recently? Was multi-factor authentication enabled on the compromised systems?
Here’s the real challenge for compliance teams: there’s simply not enough time in the day for compliance teams to micro-manage all control operators or review all controls on a timely basis.
Yet, some controls, such as reviewing user access rights to certain administrative tools (e.g. a tool that allows key personnel to control end user accounts), are simply too important to be left unexamined.
If a compliance team doesn’t have visibility into whether high-risk controls are being performed or not, it may take the team weeks or months to discover the problem. That leaves plenty of time for hackers to penetrate an organization’s internal systems and wreak havoc.
As the Twitter breach has shown, an organization can incur an incredibly high cost when it doesn’t know whether its controls are working as intended.
At this point, some business leaders may object and say “Well, we’re doing just fine in terms of protecting our information systems. We just received our SOC 2 report a month ago and our auditor gave us a clean opinion.”
However, this misses a key point: A point-in-time audit can only tell you whether the system that was in the scope of that audit was secure at that specific moment. Having passed an audit will be cold comfort to your organization, and your customers, if you let your compliance program lapse and do not carry out all of the necessary controls.
At this time, maintaining security and operational resilience requires a continuous compliance approach, where controls are monitored and evaluated on an ongoing basis and where the right data is fed into the compliance system for compliance officers to act upon.
Today, compliance officers are often missing critical information on the health of controls that are meant to mitigate high-priority risks. Compliance officers need an easier way to collect evidence, so they can see which controls are being performed and which ones are not — and have enough time to talk to the right people and fix the issue before it causes a bigger problem.
About Hyperproof
Hyperproof’s continuous compliance software helps security and compliance teams gain real-time visibility into the health of their compliance program and whether controls are being performed on-time, allowing teams to identify gaps in their control environment and remediate issues on time to reduce risks.
To learn more about how the software might help you run a continuous compliance program and reduce risk, contact us for a personalized consultation.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?