What Is Cloud Security Posture Management?
Cloud Security Posture Management (CSPM) represents a framework of tools and practices designed to continuously monitor and secure cloud environments. As organizations increasingly migrate their operations to cloud platforms, CSPM plays an important role in identifying vulnerabilities, misconfigurations, and compliance violations.
Modern cloud environments present complex security challenges that traditional security approaches struggle to address effectively. CSPM solutions automate the detection and remediation of these challenges while helping organizations maintain compliance with regulatory standards across diverse cloud infrastructures.
Defining cloud security posture management

Cloud security posture management is a comprehensive approach to securing cloud infrastructure by continuously monitoring configurations and identifying potential security risks. CSPM solutions provide organizations with automated tools to detect misconfigurations, assess compliance status, and implement remediation procedures across multiple cloud platforms.
What does cloud security posture management entail?
Cloud security posture management involves the systematic evaluation of cloud resources against established security standards and best practices. CSPM tools automatically scan cloud environments to identify improper configurations, exposed data storage, weak encryption settings, and unauthorized access permissions.
These solutions operate through application programming interfaces (APIs) provided by cloud service providers. This enables real-time assessment without requiring agent installations on individual resources. The technology works by comparing current cloud configurations against predefined security policies and industry frameworks.
When deviations are detected, CSPM systems generate alerts. They provide step-by-step guidance for addressing identified issues.
What is the primary purpose of CSPM?
CSPM’s primary purpose is to continuously monitor cloud environments for security misconfigurations, compliance violations, and vulnerabilities while providing automated remediation capabilities. This helps organizations maintain a secure cloud infrastructure without manual oversight of every configuration change.
How does CSPM differ from traditional security tools?
Unlike traditional security tools designed for static, on-premises environments, CSPM is built specifically for dynamic cloud environments where resources change constantly. CSPM provides agentless scanning, real-time monitoring, and automated responses to configuration changes across multiple cloud platforms.
What types of organizations benefit most from CSPM?
Organizations with significant cloud infrastructure, regulatory compliance requirements, or multi-cloud deployments benefit most from CSPM. This includes companies in healthcare, financial services, retail, and any organization handling sensitive data in cloud environments.
How does CSPM serve cybersecurity and GRC purposes?
CSPM serves multiple functions that align with organizational security objectives. CSPM tools help security teams maintain consistent security policies across dynamic cloud environments while supporting compliance requirements for various regulatory frameworks.
These frameworks include GDPR, HIPAA, and PCI-DSS. The technology contributes to technical risk reduction by providing continuous oversight of cloud configurations. This prevents misconfigurations from going unnoticed for extended periods.
This continuous monitoring approach proves particularly valuable given the rapid pace at which cloud resources are deployed and modified in modern DevOps environments.
How does cloud security posture management differ from cloud access security broker solutions?
While cloud access security broker (CASB) solutions focus primarily on controlling and monitoring user access to cloud applications and data, CSPM concentrates on the security configuration of the underlying cloud infrastructure itself. CASB tools sit between users and cloud services to enforce access policies.
CSPM solutions examine the configuration of cloud resources, like virtual machines, storage systems, and network settings. This distinction means that CASB and CSPM serve complementary roles within a comprehensive cloud security strategy.
CASB addresses user behavior and access controls, while CSPM focuses on infrastructure configuration and compliance.
Why is CSPM important in modern cloud strategies?
According to Gartner, “99 percent of cloud security issues will be the customer’s fault through 2025,” highlighting that misconfigurations account for most cloud security incidents rather than provider vulnerabilities. This insight confirms that CSPM plays an important role in addressing the primary source of cloud-related security risks.
As organizations adopt multi-cloud strategies and deploy increasingly complex cloud architectures, manual oversight of security configurations becomes impractical. CSPM solutions provide the automated capabilities necessary to maintain security standards across diverse and rapidly changing cloud environments.
What are the core features and capabilities of CSPM solutions?
CSPM platforms offer a range of capabilities designed to address the unique security challenges of cloud environments. These features work together to provide comprehensive visibility and control over cloud security posture, though the effectiveness may vary depending on implementation approach and organizational context.
How do CSPM tools monitor for vulnerabilities continuously?
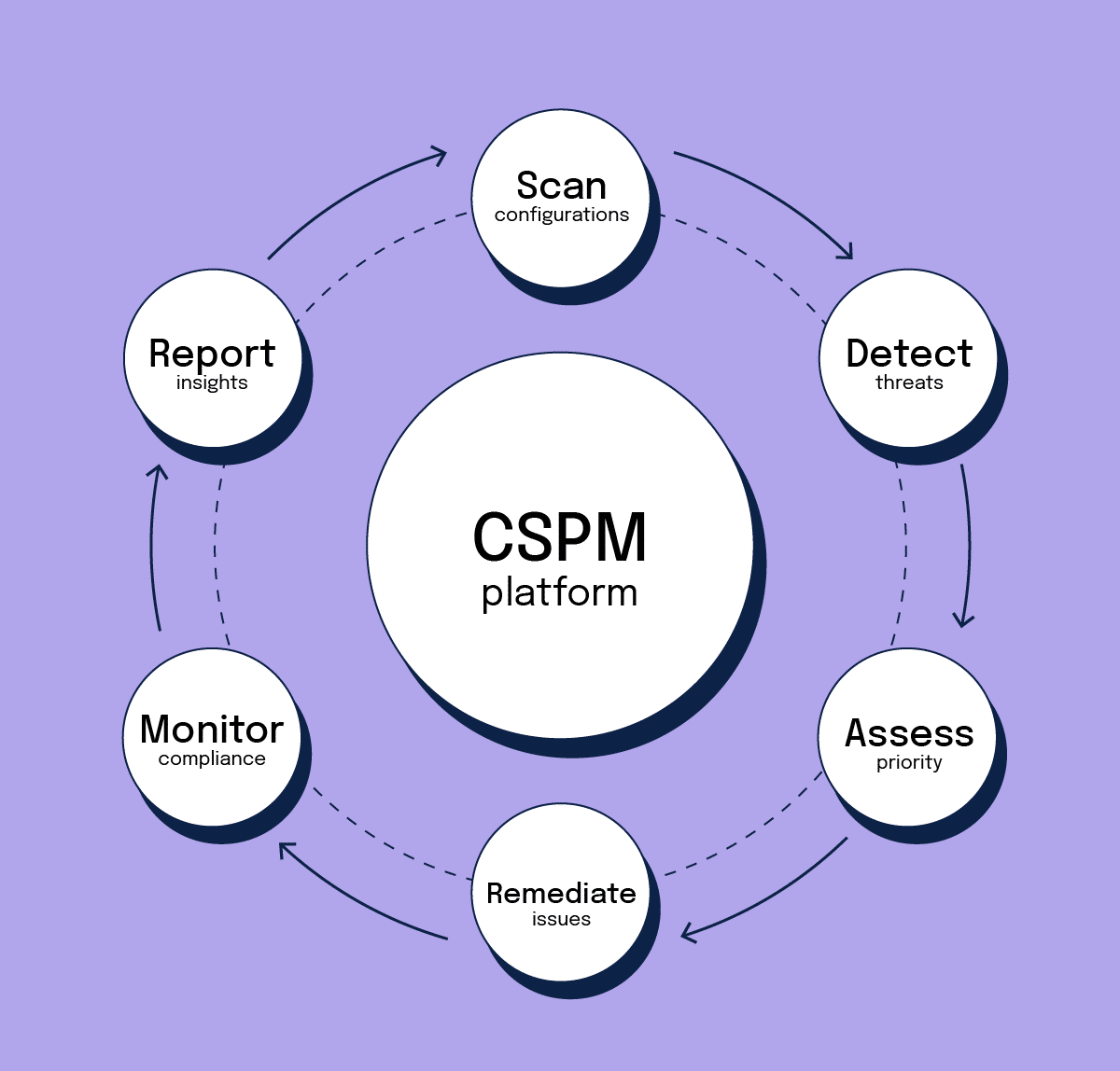
Modern CSPM solutions operate through continuous scanning mechanisms that continuously assess cloud environments. These tools connect to cloud provider APIs to gather real-time information about resource configurations, network settings, and access permissions without requiring downtime or service interruptions.
The scanning process includes an evaluation of various cloud components. These include virtual machines, containers, databases, storage systems, and networking configurations. CSPM tools identify issues such as publicly exposed storage buckets, overly permissive security groups, unencrypted data transmission, and weak authentication settings.
Modern cloud security posture management solutions have moved beyond legacy tools that required agent installations. Contemporary platforms use agentless scanning capabilities that can assess workload configurations using an agentless workload scanner. This eliminates security blind spots, performance impact, and ongoing maintenance required for agent-based solutions.
Can CSPM tools integrate with existing security infrastructure?
Yes, modern CSPM solutions are designed to integrate with existing SIEM systems, ticketing platforms, and incident response tools. They typically provide APIs and standard connectors for seamless data sharing and workflow integration.
What automated risk detection and remediation capabilities do CSPM solutions provide?
CSPM solutions provide automation of both risk detection and remediation procedures. These tools not only identify misconfigurations but also provide automated fixes for certain types of issues, reducing the time between detection and resolution.
The automation capabilities include the ability to automatically apply security patches. They can adjust access permissions, enable encryption settings, and modify network configurations based on predefined policies. Organizations can configure which remediation actions are automated versus those that require manual approval.
Modern CSPM tools perform cloud risk assessment at the cloud, application, and OS layers. This goes beyond simple configuration checks to provide host and application-level misconfiguration assessment against CIS benchmarks to improve compliance and reduce risk.
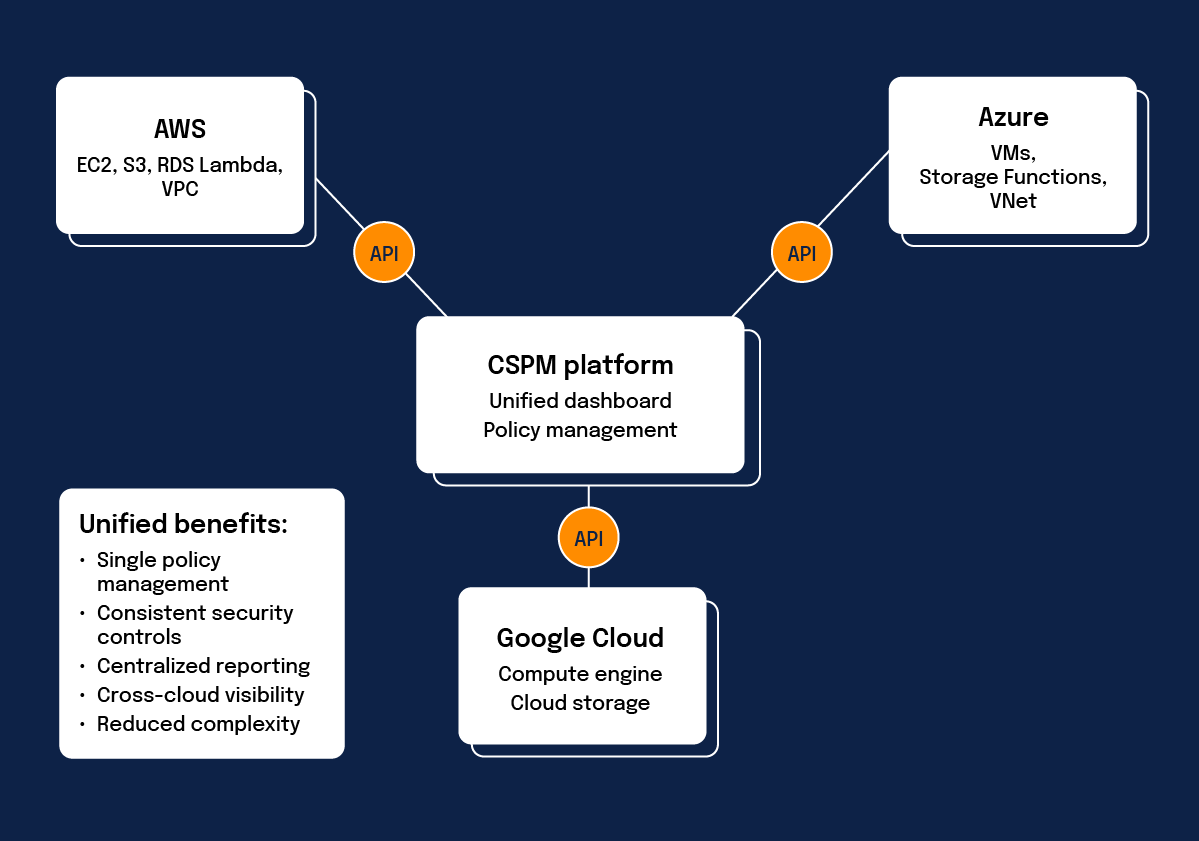
How do CSPM solutions support multiple cloud platforms?
Cloud security posture management solutions provide unified security management across multiple cloud platforms, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), and various Platform-as-a-Service (PaaS) offerings. This multi-cloud support proves particularly valuable for organizations that have adopted hybrid or multi-cloud strategies.
The ability to manage security policies consistently across different cloud providers helps organizations avoid the complexity of maintaining separate security tools for each platform. This unified approach permits better overall visibility into your organization’s complete cloud security posture.
What real-time alerting and oversight capabilities do CSPM platforms include?
CSPM platforms include alerting capabilities that notify security teams immediately when potential issues are detected. These alert systems are configurable to trigger notifications based on severity levels, specific types of misconfigurations, or particular regulatory compliance requirements.
The real-time nature of these alerts enables rapid response to emerging security issues. This prevents minor misconfigurations from developing into more significant security incidents. Many solutions provide integration with existing security information and event management (SIEM) systems or ticketing platforms.
What reporting and analytical insights do CPSM solutions provide?
Comprehensive reporting capabilities are a standard feature of cloud security posture management solutions, providing organizations with detailed insights into their cloud security posture over time. These reports include compliance status assessments, trending analysis of security issues, and detailed documentation suitable for audit purposes.
The analytical features help you identify patterns in your security posture. They help you understand the effectiveness of your security policies and make data-driven decisions about resource allocation and security improvements. These insights support both operational security management and strategic planning activities.
How legacy CSPM differs from modern CSPM
The cloud security posture management market has undergone significant development, with modern solutions addressing limitations present in earlier generations of tools. Understanding these differences helps you make informed decisions about CSPM implementation.
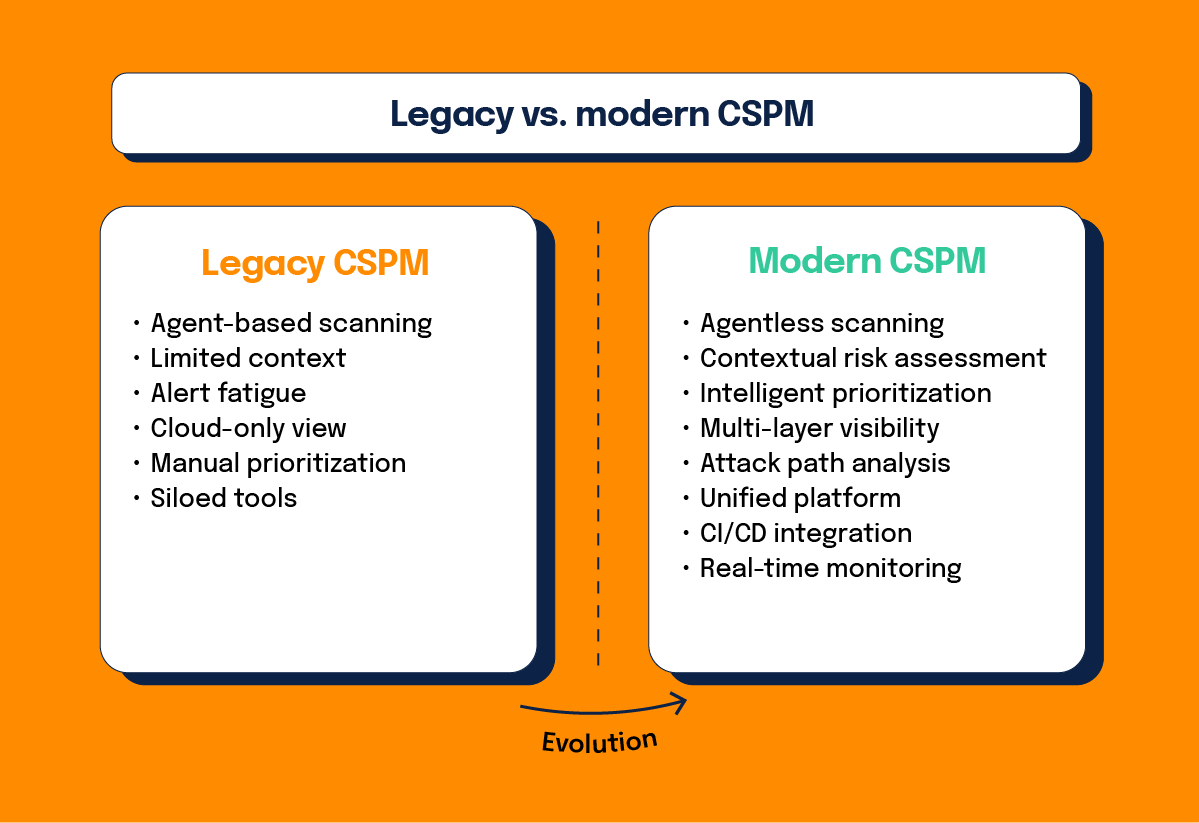
What gaps do legacy cloud security posture management tools have?
Legacy CSPM tools operate with tunnel vision, focused primarily on cloud resource misconfigurations, missing out on many other threats that could significantly impact security posture and increase attack surface. These tools lack the context needed to understand threats in their environment fully.
Legacy CSPMs give lengthy lists of issues without a full understanding of their criticality. Without context, security teams cannot prioritize these issues effectively. This leads to alert fatigue and potentially missing important security concerns.
Legacy tools are often not comprehensive. They miss support for cloud service providers or Kubernetes, resulting in teams using unique tools per CSP and requiring different processes owned by different teams. This creates further silos in people, processes, and technologies, and no holistic view or context.
How do modern CSPM solutions bridge these gaps?
Modern cloud security posture management solutions provide contextual risk assessment capabilities that enrich the context of legacy cloud security posture management findings. These include several advanced capabilities that legacy tools cannot provide.
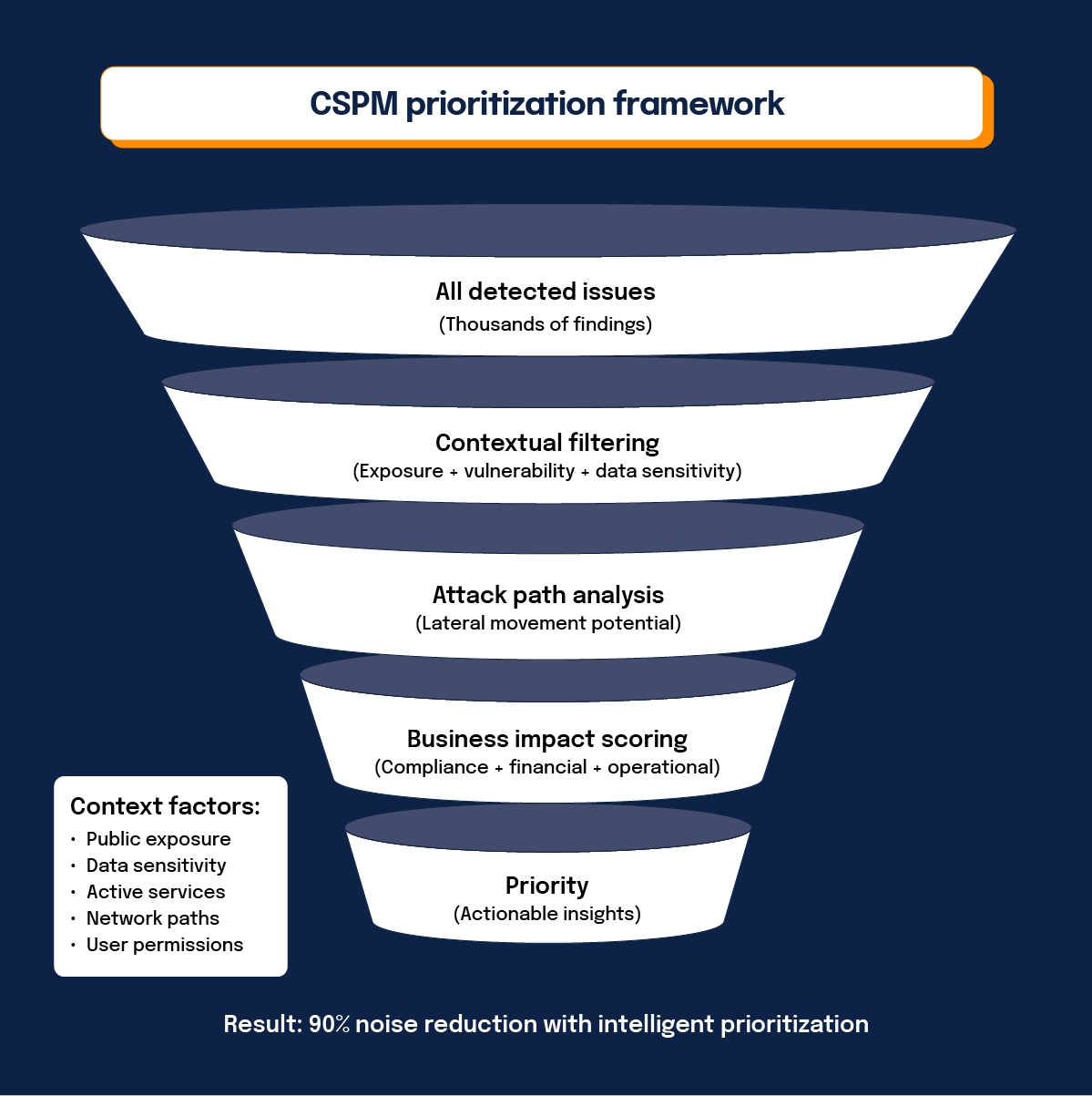
Agentless workload scanning
Modern CSPM provides visibility into workload configurations using an agentless workload scanner. This identifies configurations of the OS, applications, and libraries across all compute, including virtual machines, containers, and serverless functions.
Cloud risk assessment
Understanding misconfigurations at the cloud level is not enough. Organizations need misconfiguration rules to assess each layer of their cloud environment, including the security of their applications.
Agentless vulnerability detection
Vulnerabilities can allow attackers to execute code in your environment or elevate their privileges. Modern CSPMs uncover vulnerabilities across your cloud environment without deploying agents. These are discovered across virtual machines, containers, and serverless resources.
Attack path analysis
Modern CSPM can immediately identify escalation paths in your environment that allow threat actors to gain access to your crown jewels. This enables you to address even the most sophisticated and hidden risks swiftly.
How CSPM supports compliance and data protection
CSPM solutions play an important role in helping organizations meet their regulatory compliance obligations while protecting sensitive data in cloud environments. These capabilities form a foundation for maintaining regulatory compliance across dynamic cloud infrastructure.
How do cloud security posture management tools align with regulatory standards?
CSPM tools support compliance with a wide range of regulatory frameworks by continuously assessing cloud configurations against specific compliance requirements. These solutions map cloud security controls to standards like GDPR, HIPAA, PCI DSS, SOC 2®, and various industry-specific regulations.
The automated compliance assessment capabilities help organizations maintain continuous compliance rather than relying on periodic manual audits. This approach proves particularly valuable given the dynamic nature of cloud environments, where configurations change frequently.
Modern CSPM solutions provide extensive out-of-the-box reports for PCI DSS, HIPAA, GDPR, CIS Critical Security Controls, and for custom compliance requirements. Reports are typically organized by region, cloud provider service category, and severity level.
How does CSPM safeguard data privacy?
Data protection is a central focus of CSPM implementations, with tools designed to identify and address risks that could lead to unauthorized data exposure. Cloud security posture management solutions detect issues such as publicly accessible databases, unencrypted storage systems, and improper data handling procedures.
The data privacy capabilities include automated scanning for sensitive data types. They assess data encryption status and monitor data access permissions. These features help you identify potential privacy violations before they result in data breaches or regulatory penalties.
How does CSPM prevent configuration drift?
Configuration drift occurs when cloud resources gradually deviate from their intended security configurations over time, which is often a result of manual changes or automated deployment procedures. CSPM solutions help prevent this drift by continuously monitoring for unauthorized or unintended configuration changes.
The drift prevention capabilities include baseline configuration management and change detection algorithms. They also include automated restoration of approved configurations when deviations are detected.
How does CSPM support audit preparation and documentation?
CSPM platforms provide valuable support for audit preparation by maintaining detailed records of security configurations, compliance assessments, and remediation activities over time. This documentation demonstrates compliance to auditors and regulators.
The audit support features include automated report generation and historical compliance tracking. They also include detailed logs of all security-related activities within the cloud environment.
Implementation steps for CSPM in cloud environments
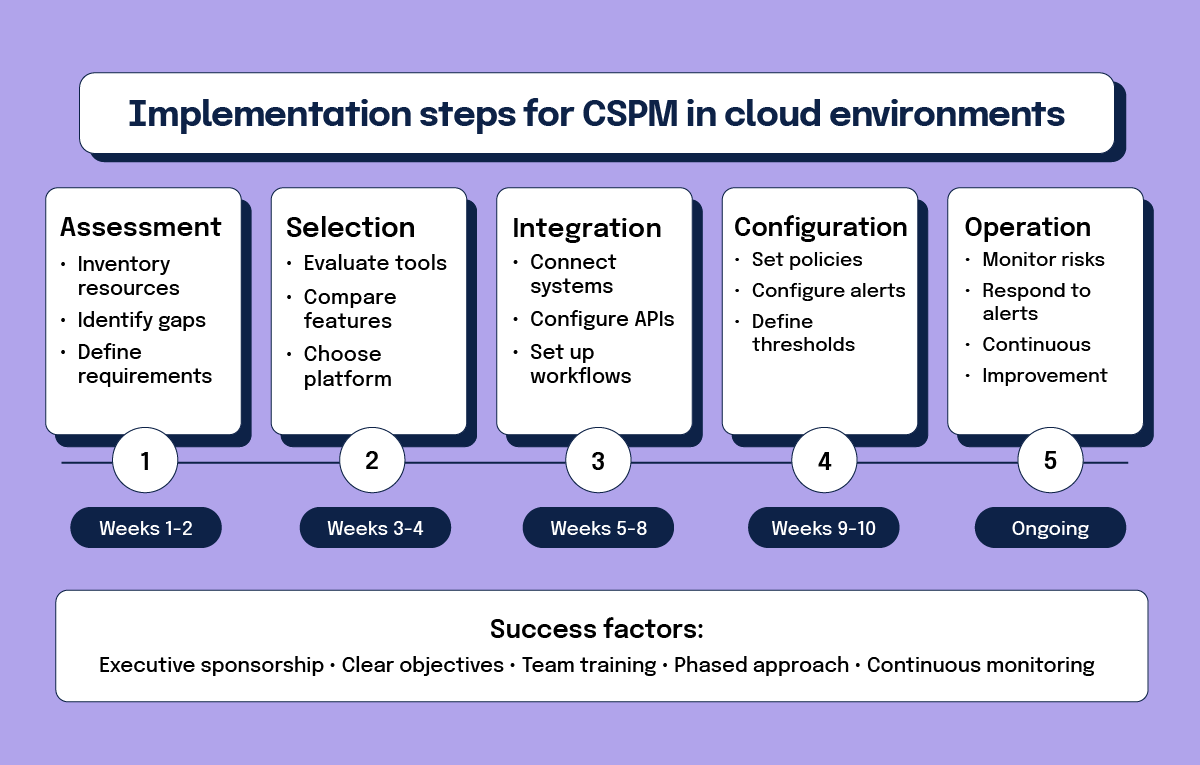
Organizations considering CSPM implementation should follow a structured approach to ensure the successful deployment and operation of these solutions. A systematic implementation process increases your likelihood of success and maximizes return on investment.
How long does CSPM implementation take?
CSPM implementation timelines vary from a few weeks for basic deployments to several months for complex, multi-cloud environments with extensive customization requirements. The assessment and planning phases typically require the most time and attention.
How should organizations assess current cloud security needs?
The initial assessment phase is important for understanding your organization’s specific cloud security requirements and identifying areas where CSPM can provide the most value. This assessment should include a comprehensive inventory of existing cloud resources, evaluating current security controls, and identifying compliance requirements.
You benefit from mapping your current cloud architecture and documenting existing security procedures. You should also identify gaps between current practices and desired security outcomes. This assessment should also include evaluating existing security tools and their integration capabilities with potential CSPM solutions.
How do you select a CSPM solution for multi-cloud use?
The selection process for CSPM tools requires careful consideration of various factors, including cloud platform compatibility, feature completeness, integration capabilities, and organizational requirements. You should evaluate solutions based on their ability to support all relevant cloud platforms and provide the specific security capabilities needed.
You should consider factors such as the solution’s ability to customize security policies. Consider the comprehensiveness of its compliance frameworks and its integration capabilities with existing security tools and procedures. The scalability of the solution and its ability to grow with your organization are also important considerations.
How do you integrate CSPM with existing security systems?
CSPM implementation involves integration with various existing security tools and procedures, including SIEM systems, incident response platforms, and vulnerability management solutions. Successful integration requires careful planning and coordination between different security teams and technologies.
The integration process includes configuring data sharing between systems. It includes alignment of alerting procedures and establishment of consistent security policies across all platforms. You also need to consider how CSPM fits into your existing security workflows and incident response procedures.
How do you set up monitoring and response procedures?
Once deployed, CSPM solutions require configuration of appropriate monitoring thresholds, alerting procedures, and response workflows. You should establish clear procedures for handling different types of security alerts and define roles and responsibilities for incident response activities.
The monitoring configuration includes setting appropriate sensitivity levels for different types of security issues. It includes defining escalation procedures for various severity levels and establishing regular review cycles for security policies and configurations.
How do you handle misconfigurations and threats?
Effective CSPM implementation requires clear procedures for addressing identified misconfigurations and security threats. You should develop standardized response procedures that can be consistently applied across different types of security issues.
The response procedures include automated remediation for low-risk issues. They include manual review requirements for high-risk situations and clear escalation paths for complex security incidents. You should also establish procedures for learning from security incidents and updating your security policies based on lessons learned.
What skills do teams need to manage CSPM effectively?
Teams need a combination of cloud platform knowledge, security expertise, and understanding of compliance frameworks. Training on the specific CSPM tool and integration with existing workflows is typically required for successful adoption.
Advantages CSPM adoption provides for organizations
CSPM implementation provides various benefits that contribute to improved security posture and operational efficiency. These advantages typically justify the investment in CSPM technology and resources.
How does CSPM enable proactive threat mitigation?
CSPM solutions enable proactive identification and mitigation of security threats before they can be exploited by malicious actors. This proactive approach helps you avoid the costs and disruption associated with security incidents.
How does CSPM boost efficiency for security teams?
By automating routine security monitoring and assessment tasks, CSPM solutions allow security teams to focus on more strategic activities and higher-value security initiatives. This shift in focus can improve overall security effectiveness and team satisfaction.
What challenges exist with CSPM deployment?
Organizations implementing CSPM encounter various challenges that require careful planning and management to address effectively. Understanding these challenges helps you prepare for successful implementation.
How do you manage unauthorized resource deployments?
Shadow IT and unauthorized cloud resource deployment create security risks that can be difficult to detect and manage. CSPM solutions help identify these unauthorized resources, but you need additional governance procedures to prevent their creation.
How do you control excessive user permissions?
Overly broad access permissions represent a common security risk in cloud environments. CSPM tools help identify these issues, but addressing them requires careful coordination with application teams and business users to avoid disrupting legitimate business activities.
How do you maintain team adoption and training?
Successful CSPM implementation requires significant training and change management to confirm that security teams and other stakeholders understand how to use the tools effectively. They must integrate them into their existing workflows.
How do you balance automation with manual oversight?
While automation can improve efficiency, you need to carefully balance automated responses with human oversight to confirm that automated actions don’t create unintended consequences. They should not interfere with legitimate business activities.
How does CSPM handle false positives?
Modern CSPM solutions use contextual analysis and machine learning to reduce false positives by understanding the actual risk level of detected issues. They prioritize findings based on exploitability, exposure, and potential business impact rather than just configuration deviations.
How does CSPM support incident response and recovery?
CSPM solutions provide important capabilities that strengthen your organization’s incident response and recovery processes. Rather than operating as standalone security tools, modern CSPM platforms integrate with incident response workflows to reduce detection time, improve investigation efficiency, and minimize business impact from security incidents.
Organizations using integrated CSPM approaches report significantly faster incident resolution times and reduced breach costs. This integration becomes increasingly important as cloud environments grow more complex and security incidents become costlier to resolve.
How does CSPM reduce incident detection time?
CSPM platforms facilitate early incident detection through continuous monitoring that catches threats before they escalate into major business disruptions. Unlike traditional security tools that rely on periodic scans, CSPM solutions provide real-time visibility into configuration changes and suspicious activities across your entire cloud infrastructure.
The average cost of a data breach is $5 million, according to IBM’s Cost of a Data Breach 2025 Report, with organizations that contained breaches in under 200 days saving an average of $1.14 million compared to those that took longer. CSPM’s continuous monitoring directly supports faster containment by detecting incidents within minutes rather than days or weeks.
Modern CSPM tools reduce alert fatigue by prioritizing notifications based on business risk. Instead of overwhelming security teams with hundreds of low-priority alerts, these solutions analyze context like data sensitivity, network exposure, and existing vulnerabilities to surface only the most business-critical threats.
This risk-based approach means your security teams spend time investigating real threats rather than chasing false positives. Integration with existing SIEM platforms and notification systems ensures important alerts reach the right people immediately through channels like Slack, PagerDuty, or email.
What business value does CSPM provide during incident investigations?
During incident investigation, CSPM tools accelerate response times by providing security teams with comprehensive forensic capabilities and attack path analysis. When security incidents occur, every hour of investigation delay can cost organizations thousands in lost productivity, customer impact, and regulatory exposure.
CSPM platforms map potential attack vectors and lateral movement paths, helping investigators quickly understand the scope and business impact of breaches. The detailed asset inventory maintained by CSPM solutions provides investigators with complete visibility into affected resources, their configurations, and relationships to business-critical systems.
This visibility is valuable for determining which customer data may have been compromised, what business processes require immediate attention, and how attackers might attempt to expand access to additional systems. Multi-domain correlation capabilities connect seemingly unrelated events across different cloud services, helping incident response teams identify the full business impact of complex attacks.
How does CSPM automation reduce incident response costs?
CSPM platforms support immediate incident containment through automated remediation that can reduce the business impact of security violations by hours or days. According to Gartner’s research, nearly all successful attacks on cloud services result from customer misconfigurations, making automated response capabilities particularly valuable for preventing escalation.
When security violations are detected, CSPM tools can automatically execute predefined response actions like isolating compromised resources, revoking excessive permissions, and blocking suspicious network traffic. This automation prevents minor configuration issues from becoming major business disruptions.
Integration with ticketing systems creates incident tickets with business context, including affected resources, potential customer impact, and recommended remediation steps. For organizations with mature security operations, CSPM platforms can trigger response playbooks that coordinate actions across multiple security tools without manual intervention.
For example, when a publicly exposed database containing customer information is detected, the CSPM solution might automatically restrict network access, generate forensic snapshots, notify compliance teams, and create remediation tickets while preserving evidence for potential regulatory reporting.
How does CSPM support business continuity and compliance requirements?
Following incident resolution, CSPM tools provide documentation and process improvements that can protect your organization from similar future incidents and support regulatory compliance requirements. The detailed audit trails maintained by CSPM platforms serve as important evidence for compliance audits and can help demonstrate due diligence to regulators and customers. This documentation reduces the time and cost associated with compliance audits while demonstrating continuous security improvement to stakeholders.
CSPM solutions help implement lessons learned by helping security teams to create custom policies based on incident findings. If an incident uncovered a new attack technique or configuration weakness, teams can develop detection rules and preventive controls that automatically identify similar issues across the entire infrastructure.
The value of CSPM
Cloud security posture management represents a necessary approach to addressing the unique security challenges of modern cloud environments. Through continuous monitoring, automated threat detection, and comprehensive compliance management, CSPM solutions help you maintain secure cloud infrastructure while supporting your business objectives.
The implementation of CSPM requires careful planning, appropriate tool selection, and ongoing management to achieve optimal results. You benefit from approaching CSPM as part of a comprehensive cloud security strategy that includes appropriate governance procedures, staff training, and integration with existing security tools and processes.
Key takeaways for your CSPM initiative:
As cloud adoption continues to expand and cloud environments become increasingly complex, CSPM will play an increasingly important role in helping you manage your cloud security risks effectively. The investment in CSPM capabilities contributes to improved security posture, reduced compliance costs, and improved operational efficiency for organizations operating in cloud environments.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?