What is SPRS scoring?
Supplier Performance Risk System (SPRS) scores are a daily reality for companies that do business with the Department of Defense. A strong score tells a contract officer that the organization can protect controlled unclassified information. A weak score raises doubts that can close doors before a bid is even considered. The same 110 NIST 800-171 controls that underpin the Cybersecurity Maturity Model Certification (CMMC) are used to calculate the score, and they serve both as a compliance checkpoint and as a business-level indicator of risk posture.
Let’s break down how the SPRS scoring model works, why it matters to GRC leaders, and how Hyperproof can turn a cumbersome spreadsheet process into a real-time, auditable workflow.
Why does SPRS scoring matter?
SPRS translates the technical state of a contractor’s security program into a single numeric value that ranges from 110 to -203. The starting point of 110 assumes every NIST 800-171 control is fully in place. Points are removed when a control is only partially applied, missing, or marked “Not applicable” without meeting the narrow DoD criteria that allow a waiver. The DoD procurement portal displays the resulting figure, and contracting officers use it to gauge eligibility for new work. A high positive score signals that the organization has addressed the most impactful controls, while a negative score flags serious gaps that could jeopardize contract performance and expose the government to data breach risk.
For GRC professionals, the score is a concrete metric that ties regulatory compliance directly to business outcomes. It surfaces hidden weaknesses that might otherwise remain buried in lengthy control matrices. By monitoring the score over time, GRC teams can see whether remediation projects are delivering measurable risk reduction or merely shifting paperwork. In addition, SPRS aligns with CMMC 2.0 Level 2 and Level 3 requirements, so a strong score demonstrates the control maturity expected for those certification levels. As a result, SPRS is a bridge between technical compliance and executive decision-making, allowing senior leaders to allocate resources where the score indicates the greatest upside.
Beyond compliance, the SPRS score provides strategic business value:
Risk-focused decision-making
Each point maps to a specific control, so a five-point loss highlights a high-impact vulnerability that may require immediate investment following investigation.
Competitive differentiation
Contractors with consistently high scores can stand out to DoD buyers during negotiations, potentially leading to faster award decisions and larger contracts.
Long-term compliance confidence
Because organizations must refresh the score regularly, they are motivated to keep security controls up to date, which reduces drift and eases adoption of new regulations.
How is the SPRS score calculated?
Each of the 110 NIST 800-171 requirements carries a weight that reflects its impact on overall security.
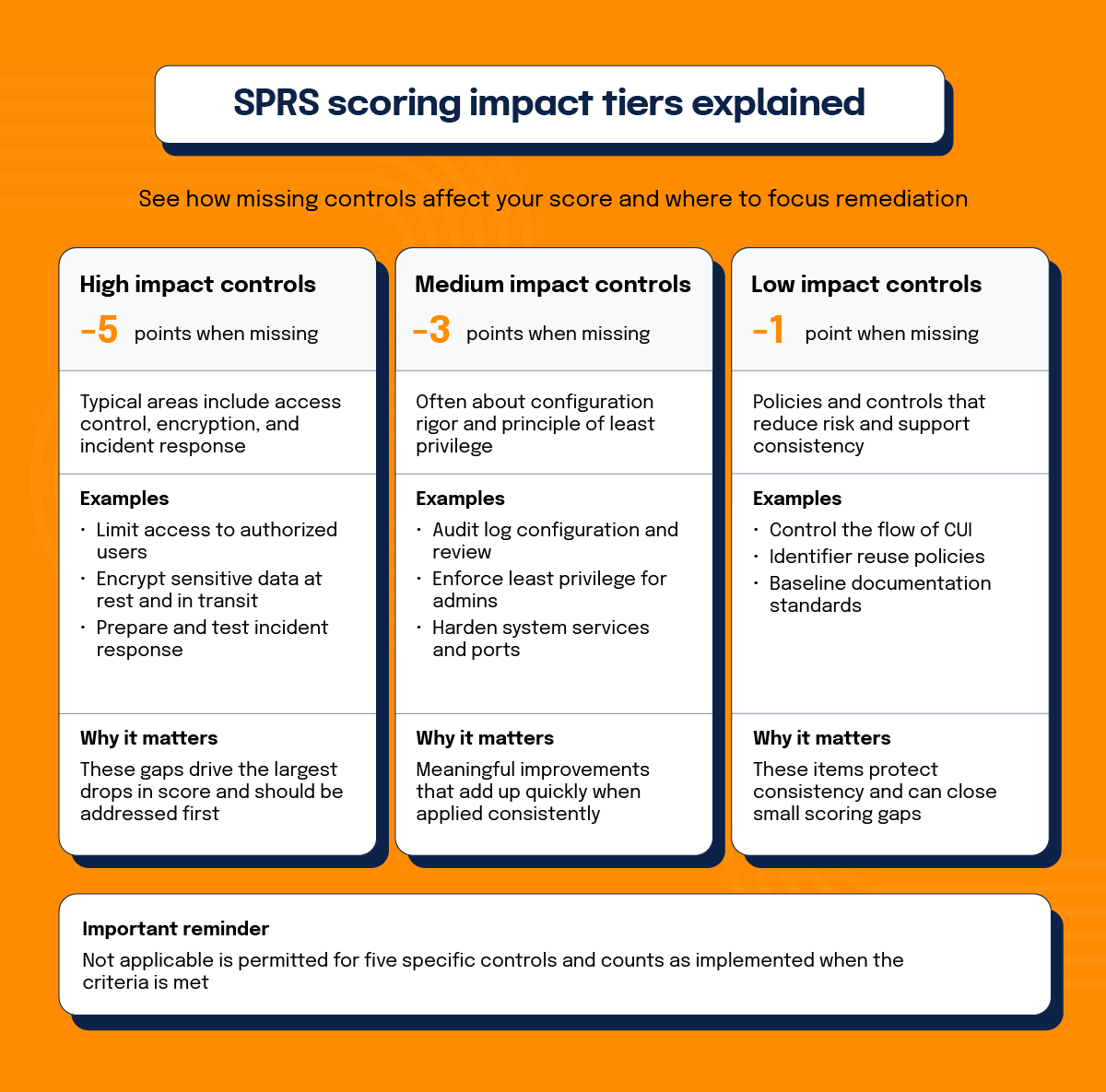
High-impact controls
Typically related to access control, encryption, and incident response, these deduct five points when they are not implemented. For example, consider control 3.1.1, “Limit system access to authorized users, processes acting on behalf of authorized users, and devices (including other systems).” This control forms the foundation of access security, ensuring that only legitimate users and devices can interact with the system. If this control is not implemented, it represents a critical vulnerability that could compromise the entire network. As a result, non-compliance with this requirement leads to a deduction of 5 points from the total score.
Medium-impact controls
Controls like specific audit log configurations remove three points for non-implementation. For example, control 3.1.5 states, “Employ the principle of least privilege, including for specific security functions and privileged accounts.” This control restricts access rights for users, accounts, and processes to only the resources necessary to perform their roles, minimizing the potential for abuse or exploitation of privileges. If this control is not implemented, it creates a potential vulnerability that could allow unauthorized actions or access to sensitive data. As a result, non-compliance with this requirement leads to a deduction of 3 points from the total score. This is a lower point deduction than a high-impact control that is commensurate with the level of potential exploitation or misuse.
Low-impact controls
These include controls like unique identifier reuse policies, and deduct one point when missing. For example, control 3.1.3, “Control the flow of CUI in accordance with approved authorizations.” This control ensures that CUI is only accessed, shared, or transmitted based on established permissions, helping to reduce the risk of unauthorized access or data leakage. Failure to implement this control results in a deduction of 1 point, meaning that while it is important, its impact on the broader network security is considered limited or indirect (particularly when compared with the prior examples). However, failing to control the flow of CUI can still pose risks to an organization, making implementation of this control essential for protecting CUI across the DiB.
Partial implementation can soften the deduction for a handful of controls, but the DoD’s default stance is all-or-nothing. Only two controls explicitly allow partial credit. The rest must be either fully satisfied or counted as a loss. When a control truly does not apply to the contractor’s environment, the “Not applicable” designation is permitted for five pre-approved items (controls 3.1.12, 3.1.13, 3.1.16, 3.1.17, and 3.1.18), and it counts as fully implemented for scoring purposes. Organizations must document all other exceptions in the system security plan (SSP) and obtain approval before allowing them to avoid a penalty.
Because the calculation is deterministic, contractors can predict how each remediation effort will move the score. Adding a missing encryption mechanism for a high-impact control instantly adds five points, while fixing a low-impact password policy contributes a single point. This transparency makes the score a useful planning tool for risk-based budgeting.
How do you implement and maintain SPRS scores?
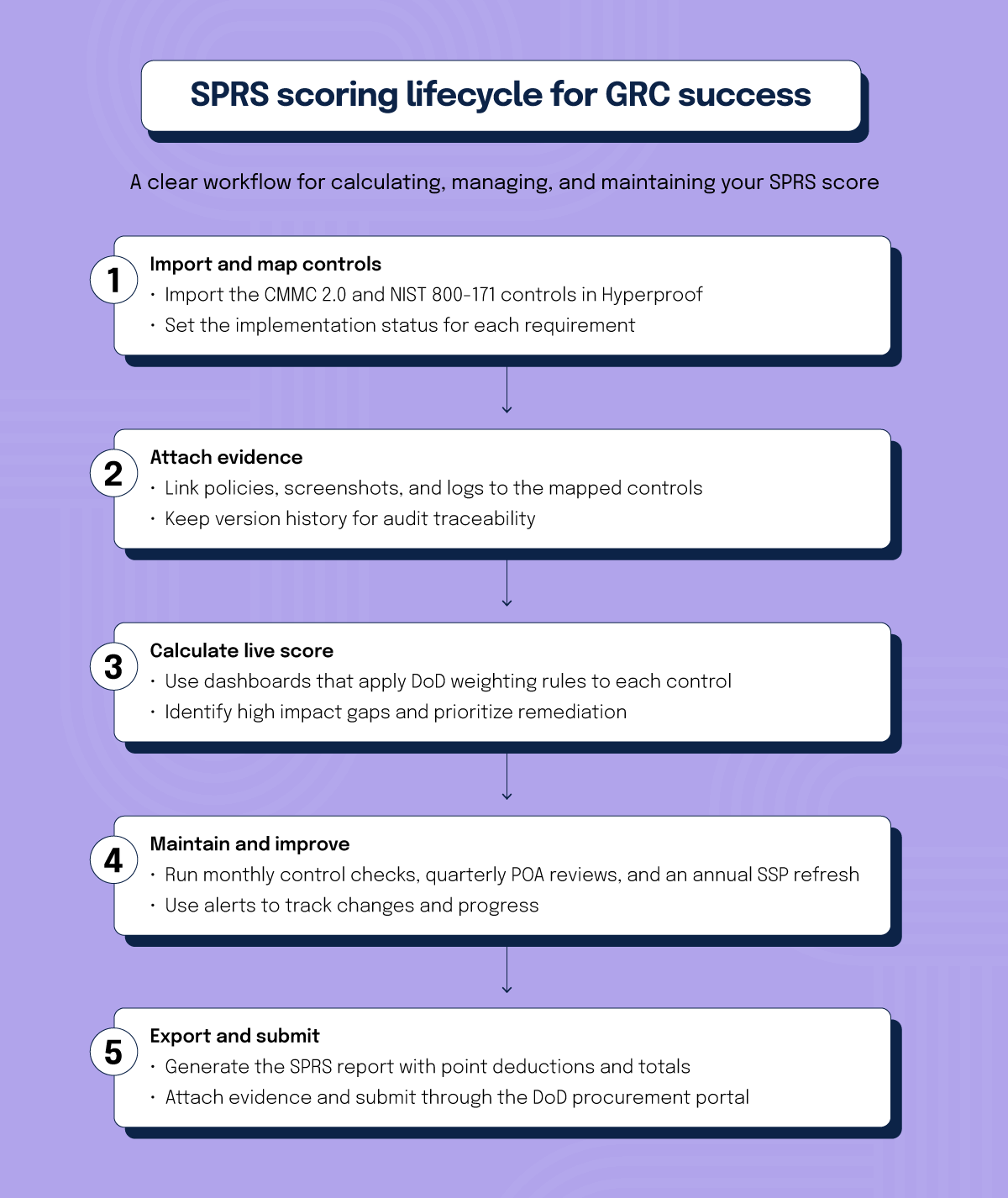
Initial setup and control mapping
Log in to Hyperproof, open the framework library, and import the CMMC 2.0 framework. The exact set of 110 controls from NIST 800-171 forms the basis of the SPRS algorithm. Hyperproof automatically creates a control inventory that matches the DoD specification, eliminating the need for manual creation.
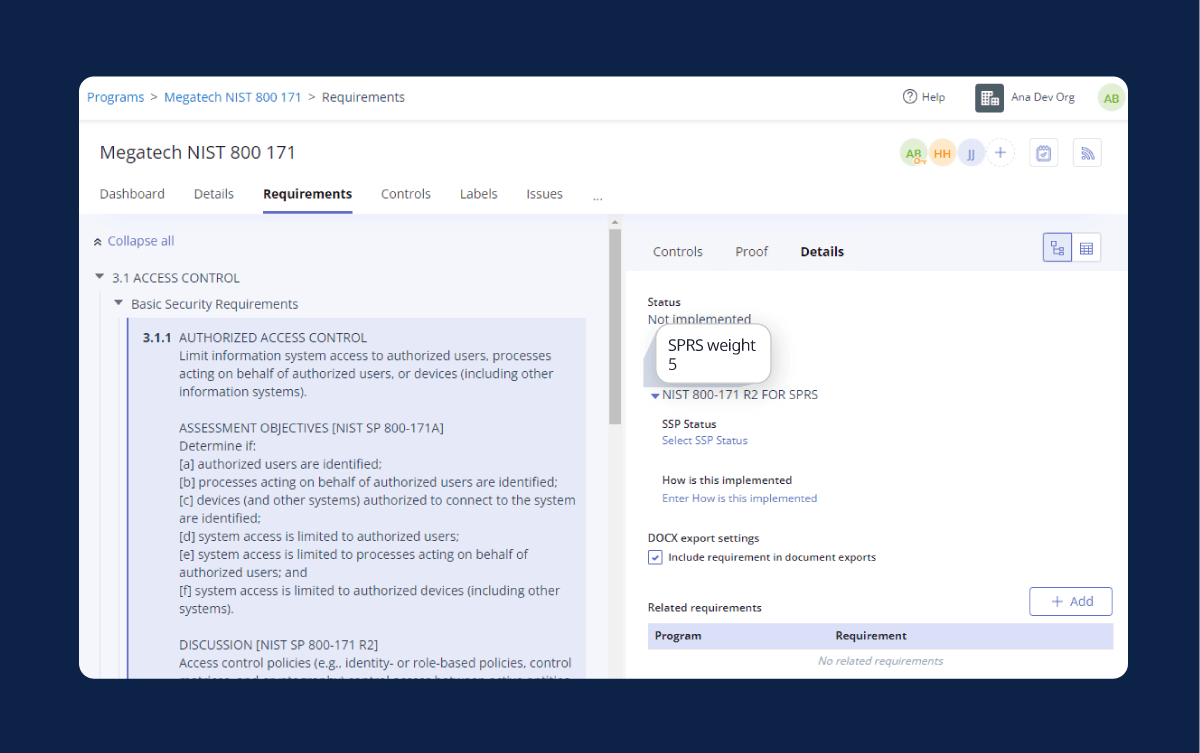
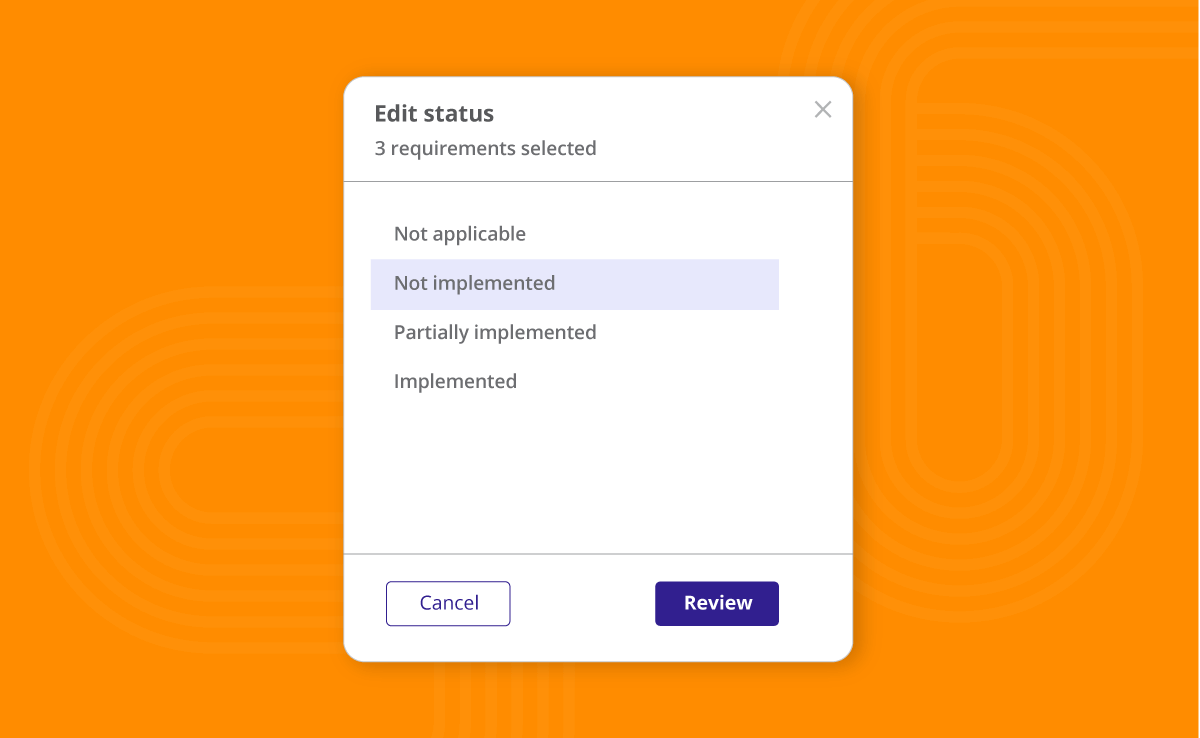
For each control, select the appropriate implementation status:
| SPRS Status | Hyperproof Status |
|---|---|
| Not implemented | Not started |
| Partially implemented | In progress |
| Implemented | Completed |
| Not applicable | Not applicable |
You can attach evidence, like policy documents, configuration screenshots, audit logs, or other relevant evidence directly to the control. Versioned evidence lets auditors trace when someone added a piece of documentation and who added it.
Real-time dashboards and score generation
Hyperproof’s widget library includes a pre-built SPRS tracker. The widget pulls the current status of every control and calculates the live score using the DoD weighting rules. Teams can filter the view by impact tier, quickly spotting which high-impact controls are still pending. The dashboard refreshes automatically whenever a control’s status changes, giving stakeholders an up-to-date picture without waiting for a quarterly report.
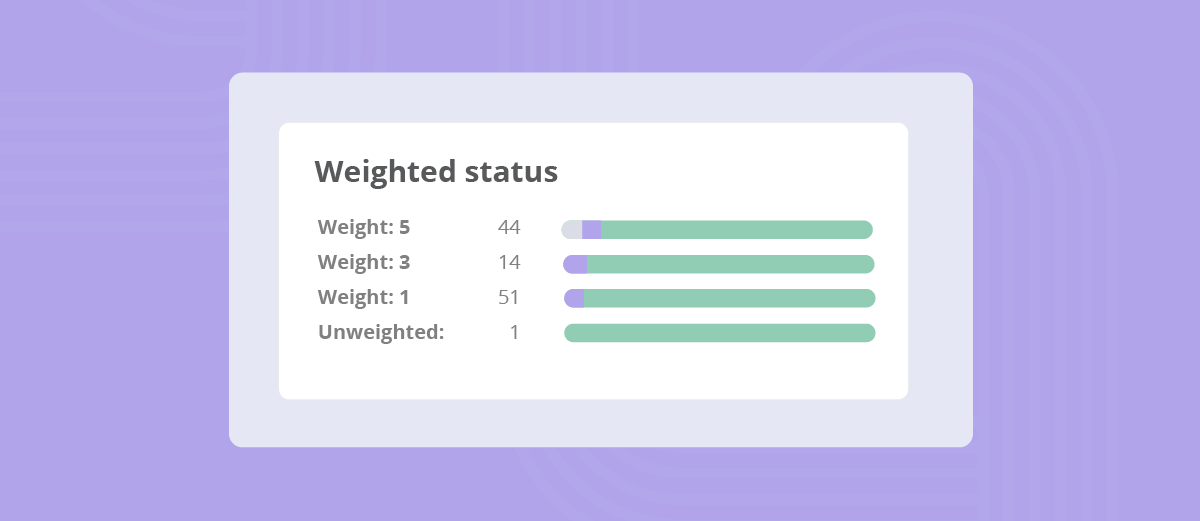
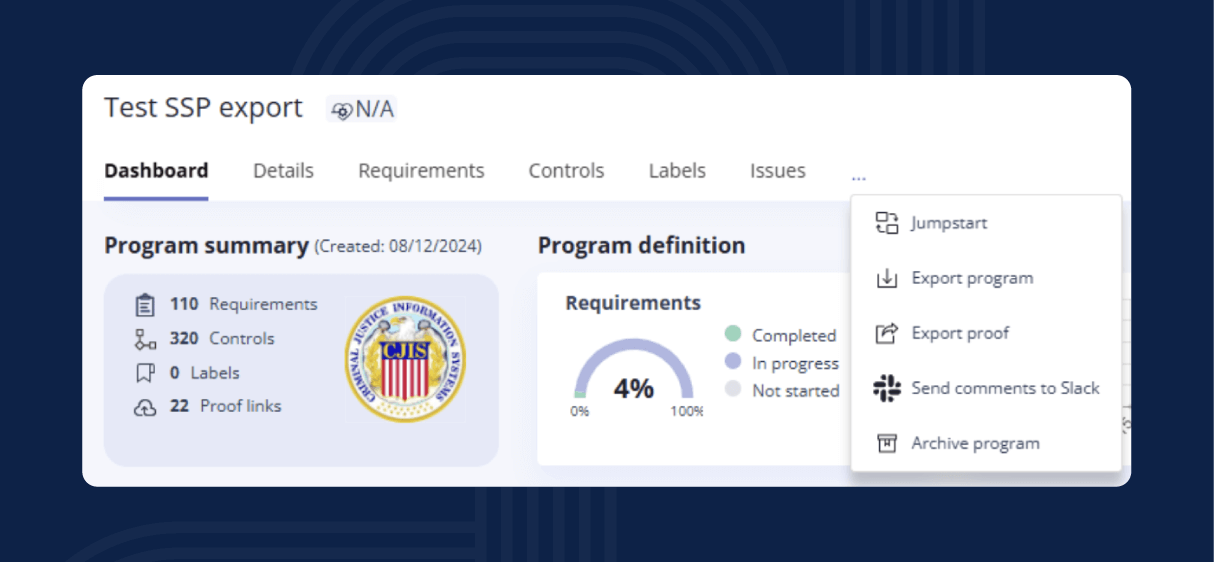
Hyperproof provides several additional functions that support maintaining your SPRS score over time: the Export program function lets users download the full control set and scores, the exported analytics sheet offers a detailed breakdown of each requirement, alerts can be configured to notify stakeholders of status changes, and a bulk status update tool enables mass editing of control statuses.
When you’re ready to submit a score, use Hyperproof’s Export program function to export a SPRS report spreadsheet. The report lists each control, its status, the point deduction applied, and the cumulative total. Review the document with the compliance manager, resolve any lingering Partially implemented entries, and confirm that any Not applicable decisions meet the DoD criteria.
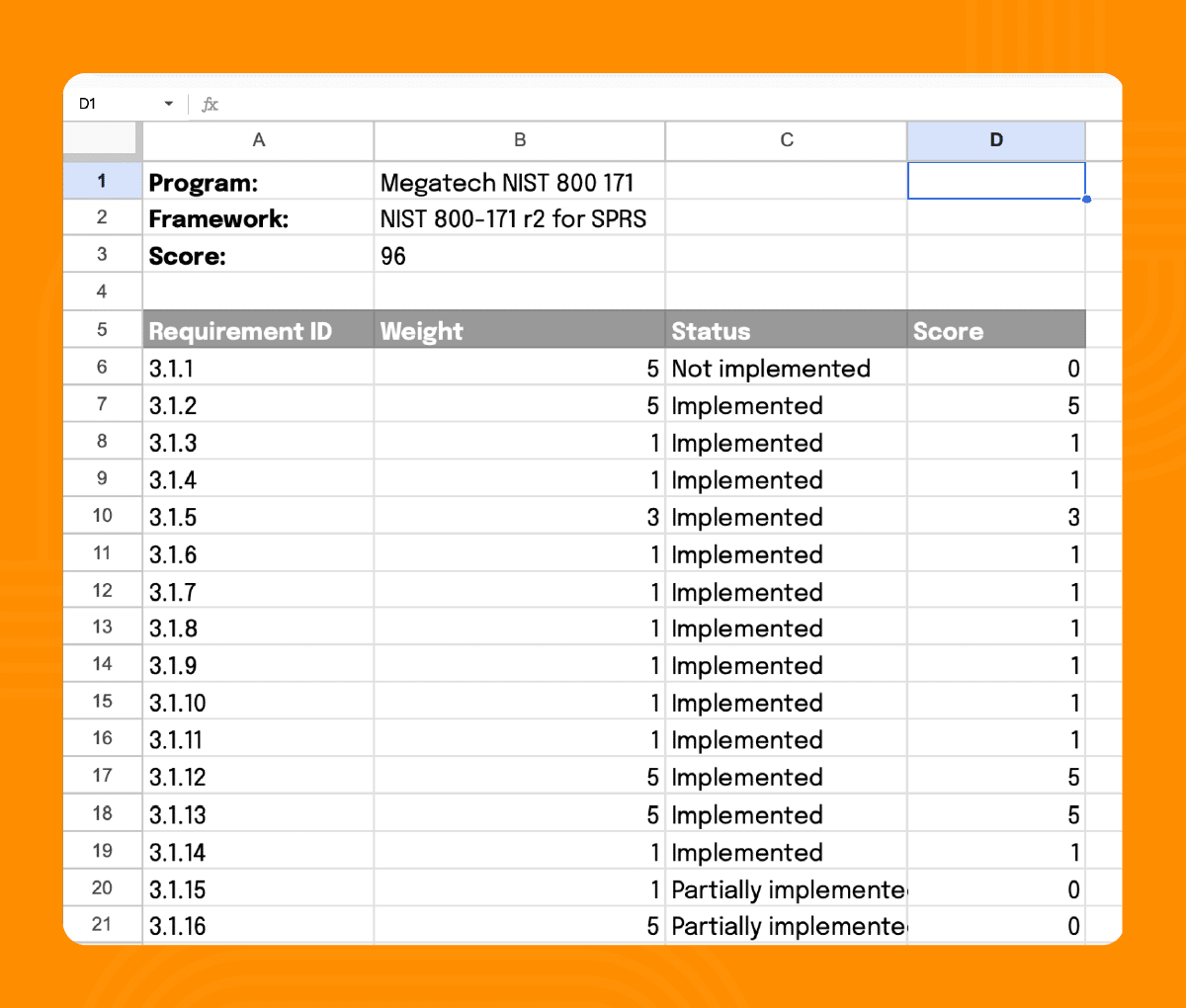
Ongoing health checks and updates
Completing the following tasks regularly can help with SPRS scoring:
Monthly control health check
Review all five-point controls and resolve any in-progress items before they become permanent deductions in your SPRS score.
Quarter-yearly POA&M review
Align the Plan of Action and Milestones (POA&M) with Hyperproof’s Issues feature or risk register. Update each milestone’s status, owner, and target date. Closed milestones automatically remove the associated point deductions.
Annual SSP refresh
Verify that the system security plan reflects the current control implementations and attach the latest SSP version as evidence in Hyperproof.
Pre-submission audit
Two weeks before a scheduled SPRS filing, generate a fresh report, compare it against the previous submission, and resolve any discrepancies.
Keeping your score current and exporting evidence
After any remediation work, update the control status in Hyperproof. The dashboard instantly reflects the new points, and the next export will contain the revised total. Hyperproof tracks change history, so the contractor can demonstrate to the DoD that the score improvement resulted from documented actions, not from a one-off data entry.
Hyperproof also allows users to download the entire control set, evidence attachments, and the SPRS calculation as a PDF or CSV file. Save the export with a timestamp, archive it in a secure repository, and attach it to the formal SPRS submission in the procurement portal. The exported package satisfies the DoD’s requirement for a complete audit trail that links each point to verifiable proof.
What happens when a score is inaccurate?
Submitting a score that does not match the actual control environment can have severe fallout.
Legal exposure
The False Claims Act penalizes contractors who knowingly or negligently submit false information to the government. Fines can reach three times the amount of the claimed loss, plus attorney fees.
Future bidding disadvantages
The contractor’s performance history records past inaccuracies. Future solicitations may assign a lower rating, which makes it harder to win work even after you correct the issue.
Because a deterministic formula derives the score, errors in control-status entry or unjustified Not applicable claims are usually what cause mismatches. Hyperproof’s versioned evidence and change logs help prove that the organization acted in good faith, but proactively preventing this through disciplined data entry remains the most effective way of minimizing this risk.
What are some best practices to avoid common pitfalls?
Treat Not applicable as a rare exception
Only the five controls expressly allowed by the DoD may receive this label. This restriction limits the misuse of Not applicable statuses based on the published DoD Assessment Methodology.
How-to: Confirm DoD waiver eligibility before marking a control “not applicable” in Hyperproof.
Use automated validation
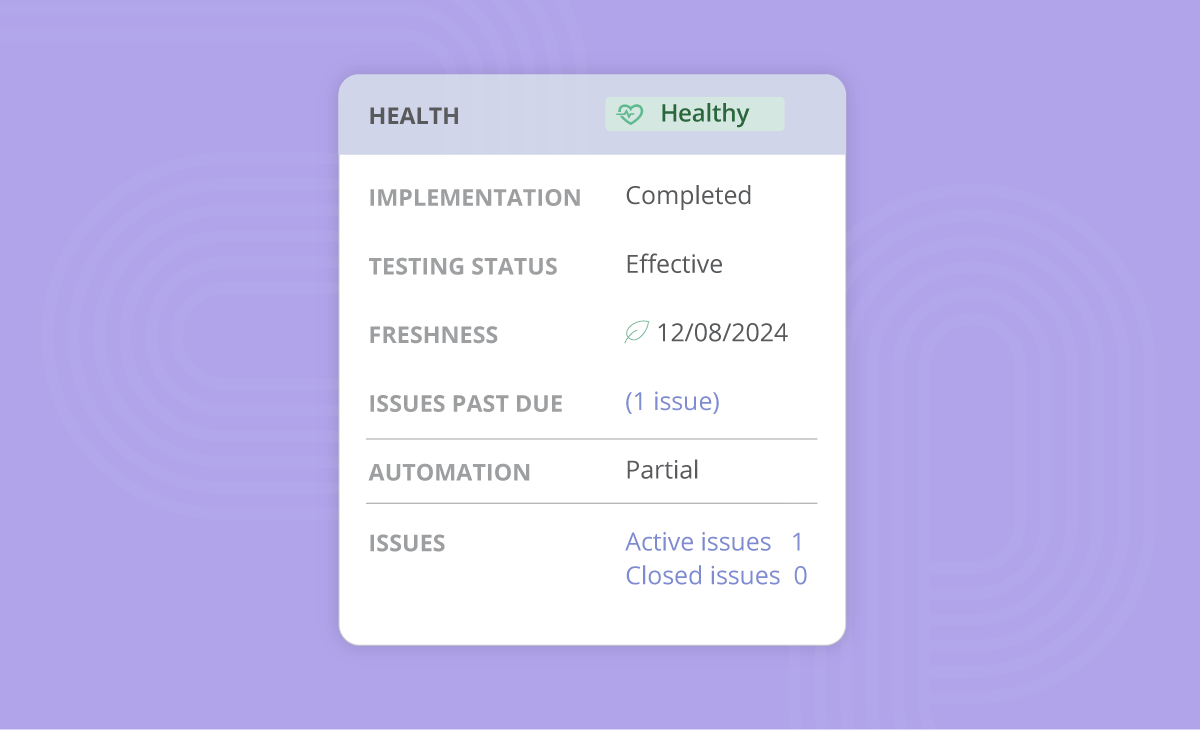
Hyperproof shows controls that lack attached evidence or have contradictory statuses, which should prompt a review before exporting the score. Automated checks help to catch this missing evidence early.
How-to: Check the freshness of each control before exporting data.
Run a double-check against the official DoD template
Export the control matrix from Hyperproof and compare it line-by-line with the DoD submission worksheet. This step prevents transcription errors.
How-to: Use Export program to download the control matrix, then compare it with the DoD’s worksheet.
Engage subject-matter experts early
When a control is marked Partial or Not applicable, bring in the security architect or system owner. Their input helps make sure that the status reflects reality, not optimism. Early expert review helps verify true implementation.
How-to: Talk to the security architect or system owner before finalizing Partial or Not applicable statuses.
What immediate actions can a GRC team take to get started?
Treating the SPRS score as a living KPI rather than a static filing turns compliance into a driver of business growth. These sample tasks should be customized for your GRC team structure.
- A compliance manager creates the Hyperproof workspace for SPRS scoring, by importing the CMMC program, mapping controls, and inviting the compliance team
- A security architect runs the initial score calculation, which identifies the top high-impact gaps and helps to assign owners
- A project manager develops the remediation timeline by targeting the highest-impact gaps first, scheduling fixes during low-traffic periods, and recording progress in Hyperproof
- The IT operations team sets up automated dashboard alerts by configuring alerts to notify the team when a control status changes from Partial to Full
- A GRC lead schedules quarterly reviews by using the exported report to compare the current score with the previous quarter, discussing trends, and adjusting resource allocation as appropriate
Key takeaways
By adopting a disciplined, technology-enabled approach, DoD contractors can turn SPRS scoring from a compliance hurdle into a strategic asset that drives risk reduction, operational resilience, and competitive advantage.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












