Understanding Cyber Security Posture: Assess and Strengthen Your Organization’s Defenses

It’s no secret that the need for strong cybersecurity defenses is at an all-time high. Cyber attacks, no matter their cause, can be costly. IBM reported that in 2020, the average cost of a data breach was USD 3.86 million globally, and USD 8.64 million in the United States. Meanwhile, ransomware attacks continue to wreak havoc on large companies, small businesses, local governments, and educational institutions. These attacks can have harrowing financial effects, but can also do major damage to an organization’s reputation. Of equal importance, think of what could be at stake for your customers if their personal information got into the wrong hands.
Seeing as enhancing cybersecurity protections is now a necessity, organizations need to be creating security and compliance measures that are preventative, as opposed to reactive. It’s smart to proactively protect your organization from a potential data breach instead of just doing damage control once one has already occurred.
In this article, we will cover the definition of security posture, what it protects against, how to assess your cyber security posture, and what you can do to strengthen it.
What is security posture?

Security posture refers to an organization’s strength of protection over its networks, data, and systems (hardware and software). In other words—your security posture measures how vulnerable your organization is to cyber attacks or data breaches. Another key piece of security posture is how an organization reacts when an attack or breach takes place. For instance, do you have key data backed up somewhere secure to reduce the impact of a data breach?
What does a strong security posture protect you from?
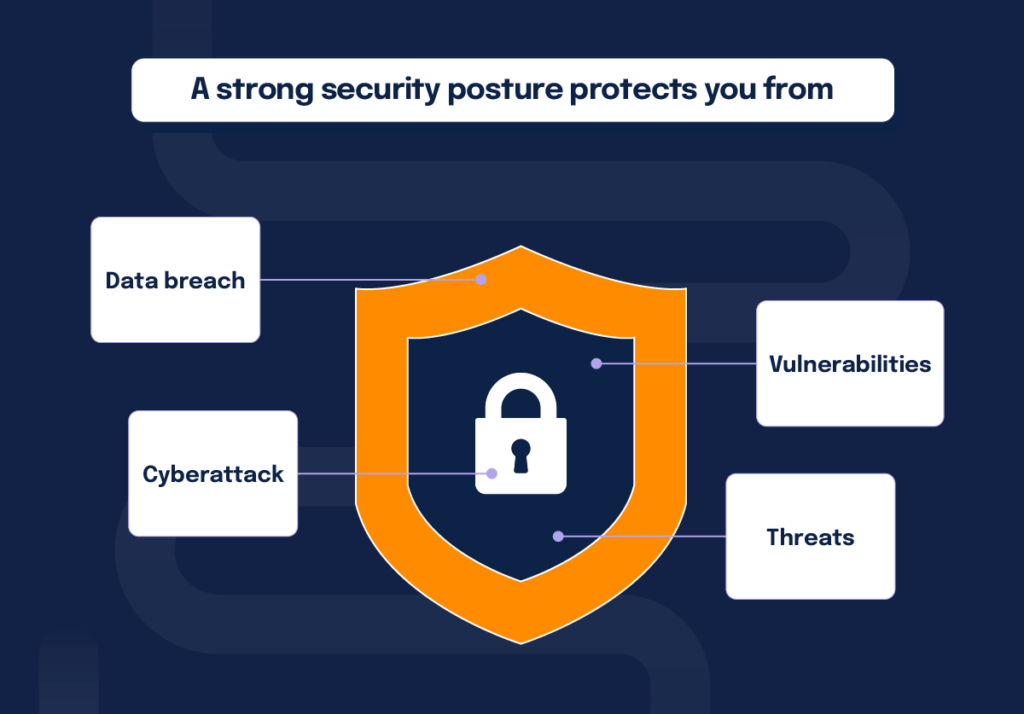
In order to build a strong security posture, you need to know what you are working to protect your organization from. Security attacks and breaches are often viewed as coming from a malicious party, but sometimes they happen unintentionally.
Data breach
A data breach occurs when confidential and/or personal information is viewed or shared without authorization. Some data breaches are intentional—a hacker targets network vulnerabilities, email phishing, etc. That said, data breaches can be unintentional as well—if a piece of hardware containing confidential information is lost, wrong access permissions are given to an employee, etc.
Cyberattack
Unlike some data breaches, all cyber attacks are committed with deliberate ill intent. Cyber attacks occur when an organization’s computer network is targeted with the goal of disrupting, disabling, and/or controlling stored information. These attacks can be carried out by external actors (hackers, criminal groups, etc.) or by people within the organization (disgruntled employees, contract workers, etc.).
Vulnerabilities and threats
Breaches and attacks may immediately come to mind in conjunction with security posture, but the development of a strong cyber security posture will also help to surface potential vulnerabilities and threats.
A security vulnerability is a weakness within an organization’s network. Vulnerabilities can vary greatly—from weak password requirements to operating systems not working properly. It should be noted that a vulnerability is something already present in an organization’s network.
Threats, on the other hand, are hypothetical instances that could negatively affect an organization due to security vulnerabilities. Understanding and analyzing potential threats and their likelihood are vital to protecting your organization against data breaches and cyber attacks.
How to assess your organization’s cyber security posture
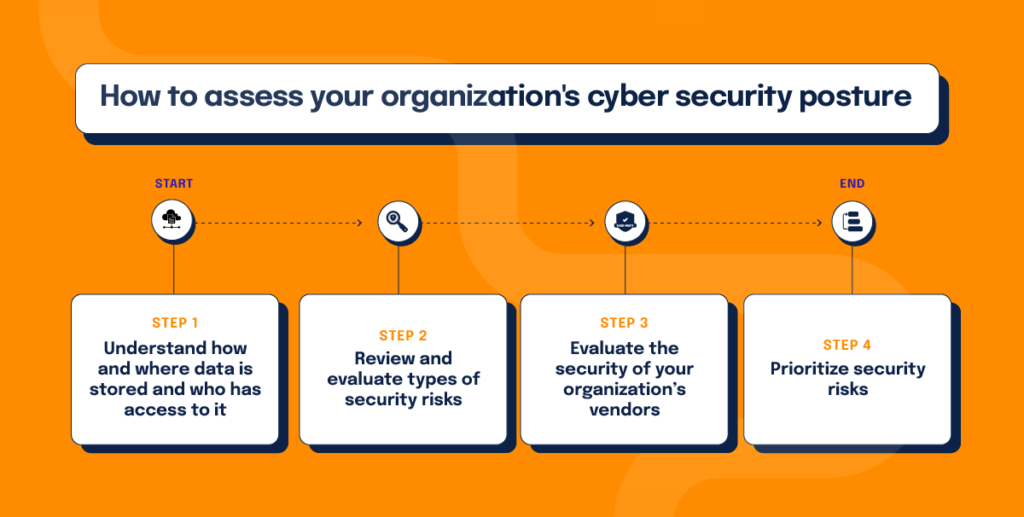
Before working to develop a new or strengthen an existing security posture, it may be helpful to complete an internal security risk assessment. Here are a few steps an organization can take to complete such an assessment:
- Understand how and where data is stored and who has access to it. No matter the size of your organization, it is important to keep an up-to-date inventory of your organization’s information assets. Once inventory is taken, it’s vital to track who has access to this data. In reviewing information storage and access, an organization will be able to see if there are any vulnerabilities that could lead to breaches or attacks.
- Review and evaluate types of security risks. It might not always be in an organization’s best interest to expect the worst, but understanding the different types of security risks out there allows for proactive protection against such risks. This piece of your security risk assessment might start as simply as listing every possible security risk that your organization’s network could encounter (i.e., weak security permissions, attacks from hackers, email phishing, poor software encryption, etc.). From there, you can focus on risk prioritization, and dive deeper into how each of these risks might affect your organization and what the consequences of each risk could be.
- Evaluate the security of your organization’s vendors. This is a piece that is oftentimes overlooked in security risk assessments. While it might be obvious to assess company-built tools or those used specifically to store sensitive corporate data, all vendor platforms that touch your networks and/or process sensitive data should also be evaluated. For instance, the payroll/HR/benefits platform and your customer relationship management (CRM) platform may be at high risk of attack if not evaluated properly. With this in mind, many companies require their vendors to show proof of various compliance frameworks in order to work together. Learn more about how to protect your business from third-party risks.
- Prioritize security risks. Once you’ve listed, reviewed, and analyzed potential security risks, prioritizing them will allow you to take action. As you will find, some risks have a low likelihood of occurring and/or will have little to no impact on your organization if something were to happen due to the risk. With the most critical risks identified, you can put time and resources into eliminating or mitigating those risks before an attack or breach can occur. A risk register, like that found in Hyperproof, can support prioritization.
6 steps to strengthen your cyber security posture

Whether security posture is a new or established priority in your organization, here are six steps you can follow to build a strong security posture:
1. Conduct regular security posture assessments
Knowing where your organization stands when it comes to security risks is the first step toward creating a strong security posture. As mentioned above, it is easier to protect against risks that you’re actively aware of. While it may be time-consuming to conduct your initial assessment, doing so will save you time and resources in the long run. And if you need some help, you can turn to vCISO and security advisory firms that can conduct risk assessments for your organization.
Deeper Dive: How to Perform a Successful IT Risk Assessment

2. Consistently monitor networks and software for vulnerabilities
Even with risks defined and prioritized, it’s vital to continue to keep an eye on your organization’s network vulnerabilities. Vulnerabilities have the potential to change in seriousness as shifts occur in an organization’s software usage and as time goes on. Additionally, in the ever-changing landscape of cyber security, new vulnerabilities could develop at any point. The only way to get in front of any issues is to continuously monitor networks and key business systems and quickly patch software when vulnerabilities are discovered.
3. Define which department owns what risks and assign managers to specific risks
As we’ve outlined, there can be a vast number and wide variety of potential risks an organization could face. With this in mind, ownership of these various risks needs to be spread out across departments. Once risks are defined and prioritized, they should be assigned to the proper department. Then, within the assigned department, specific managers should be tasked with owning and monitoring each risk. This way, every risk can be tracked by a knowledgeable party and responsibility can be distributed throughout the organization as opposed to it all falling to one team.
4. Regularly analyze gaps in your security controls
Building out security controls is a fundamental part of creating a resilient organization and ensuring your company is meeting its regulatory compliance obligations. Controls are specific policies, procedures, processes, and technologies your organization has chosen to implement to mitigate certain risks and meet compliance requirements. While you might feel confident in the security controls you already have in place, it is important to consistently test your security controls and look for potential gaps in these controls. As with continuously monitoring your network for vulnerabilities, regularly analyzing gaps in your security controls will help you to be proactive in protecting your organization against cyber-attacks and data breaches.
5. Define a few key security metrics
To understand how your organization is doing from a cybersecurity standpoint, you need to select a few metrics—without getting too technical—to paint a picture of the current threat landscape. These metrics help you establish a baseline for security posture and health. Your C-level leaders and board members likely want to see cybersecurity improvements over time. These metrics could include:
- Detected intrusion attempts
- Vulnerability patch response times
- Incident rates
- Severity level of incidents
- Incident response time and time to remediation
- Number of users broken out by application/data access level
- The overall volume of data the business generates (while not a security metric necessarily, changes in traffic volume can help justify the need for new or upgraded security tools)
6. Create an incident response plan
A cybersecurity incident response plan (CSIRP) is a document that gives instructions on how to respond to a serious security incident. Here are the four phases that make up a comprehensive CSIRP:
- Preparation
The planning you do before a security incident occurs will help you respond to an issue as quickly and efficiently as possible. Your CSIRP needs to detail who is on the incident response team and what their role is if/when an attack or breach occurs. Another piece to this phase of your plan is incident prevention—refer to steps one (conduct regular security posture assessments) and two (consistently monitor networks and software for vulnerabilities) above to support this. - Detection and analysis
The detection and analysis phase in your CSIRP is triggered when an incident has just occurred and your organization needs to determine how to respond to it. Security incidents can originate from many different sources and be detected in a variety of ways. With this in mind, your CSIRP should give directions for documenting the incident and prioritizing the response. You will then need to notify the correct parties of the attack or breach, such as customers, attorney generals within the states you operate within, etc. - Containment, eradication, and recovery
Everything you do in response to an attack will revolve around containing the incident, eradicating the threat, and recovering from the attack. Eradication will involve different steps depending on what type of incident you’re experiencing, but essentially you will be eliminating whatever you need to in order to stop the attack. In recovery, you should make changes and updates to your security plan, address the vulnerability that enabled the security incident, and complete any training to prevent any future attacks. - Post-incident activity
After the incident has been stopped, security updates have been made, and your organization is back on track, your organization should take some time to debrief. During this phase, your organization should reflect on what has happened, assess the severity and damage, reevaluate the effectiveness of your CSIRP, and begin the notification process.
All of this said, owner education may be the most important piece of ensuring the success of a CSIRP. It’s vital for involved parties to know exactly what their role is before, during, and after an incident occurs. Without owner education, a CSIRP cannot be efficiently and effectively carried out, making it essentially useless.
For more information about how to write a cybersecurity incident response plan, check out this article: https://hyperproof.io/resource/cybersecurity-incident-response-plan/
Having a central platform where you can see all of your risks, descriptions of controls, and health status of controls and work on remediation items will go a long way in being able to accomplish all of this effectively. A compliance operations platform like Hyperproof can help to take your security posture to the next level.
Hyperproof can help improve your cyber security posture

What we’ve highlighted above will help to get your organization’s security posture to a healthy place. That said, if your organization wants to proactively create the strongest security posture possible, it could be in your best interest to align your security program to a best-in-class cybersecurity framework like ISO 27001, ISO 27701, or Cloud Security Alliance’s Cloud Control Matrix.
With Hyperproof, this is easy to do. Utilize our compliance operations platform to:
- Implement security controls aligned to best-in-class standards and guidelines — for instance, ISO 27001.
- Foster accountability by assigning control ownership. Assign tasks and communicate with stakeholders without having to switch tools.
- Monitor your security posture by defining cadences for control monitoring. Automatically set up Hyperproof to pull in evidence of control activities so time is spent on testing that evidence rather than simply trying to gather evidence.
- Track risk assessment results and put risk remediation plans into action in order to maintain accountability.
Ready to see how Hyperproof can support your security posture? Book a demo.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?