Cybersecurity in Financial Disclosures: 11 Topics Your Section 1C of 10-K Filings Should Address
Last year, the Securities and Exchange Commission (SEC) announced new disclosure rules for publicly traded companies. Regulation S-K Item 106, which mandates cybersecurity disclosures in corporate 10-K filings, sheds light on how companies are navigating regulatory expectations in this digital age. This is the first time companies have been required at scale to report on their cybersecurity to the SEC, and I expected there would be a high degree of variance at first. Since the start of January 2024, I’ve been reviewing section 1C disclosures from companies to predict what they’ll be disclosing in 2025, and to also determine what effect those disclosures may have on future regulatory enforcement activity.
Despite the SEC only asking for four specific disclosures, we found that almost half of companies are sharing additional information on eleven different topics. These include cybersecurity frameworks, risk assessments, risk management, and more.
Companies are going beyond what’s required to reassure investors and address regulatory concerns, even discussing areas like third-party risks and incident response plans. This proactive approach reflects their commitment to cybersecurity and navigating regulatory expectations.
First, let’s dive deeper into what SEC Regulation S-K Item 106 — and Section 1C of 10-K filings — mean for you.
What is Section 1C of 10-K filings?

Let’s define exactly what we’re talking about. The SEC describes it best:
New Regulation S-K Item 106 will require registrants to describe their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats, as well as whether any risks from cybersecurity threats, including as a result of any previous cybersecurity incidents, have materially affected or are reasonably likely to materially affect the registrant. Item 106 will also require registrants to describe the board of directors’ oversight of risks from cybersecurity threats and management’s role and expertise in assessing and managing material risks from cybersecurity threats.
Regulation S-K Item 106 from the SEC
Despite this guidance mandating only four disclosures (identifying and managing risks, disclosing material breaches, board oversight, and management’s role), over 40% of the 2,100+ 10-K filings I’ve reviewed between January 1 and March 11, 2024 disclosed eleven distinct topics.
Companies are disclosing more information than required in their 10-K filings for various reasons. One is that they lack a broad consensus how much detail to disclose in Section 1C. The recent civil litigation of SEC vs. Tim Brown and SolarWinds (case 1:23-cv-09518 in the Southern District of New York) significantly influences the disclosure requirements.
Businesses must balance providing enough information to assure investors and the SEC of their due care while mitigating a critical risk: that insufficient or inaccurate details may lead to regulatory investigation and enforcement actions following a breach or sales of securities by institutional investors.
Let’s discuss the eleven topics I found when reviewing over 2,000 10-K filings:
11 topics addressed in 10-K filings
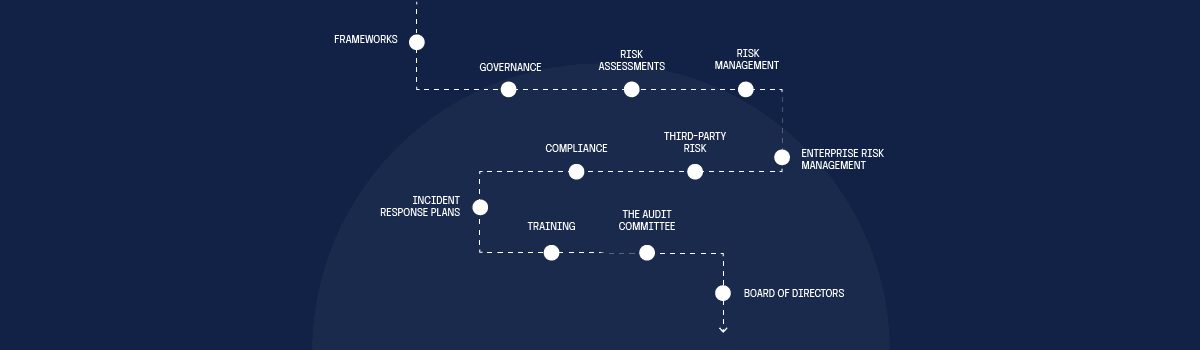
1. Frameworks
51% of companies reference one or more cybersecurity frameworks, attestations, or external regulatory requirements as the foundation of their cybersecurity program, likely as a proxy for showing due care. The NIST Cybersecurity Framework (NIST CSF) is the most frequently mentioned framework, cited in 29% of disclosures. This aligns with our survey of GRC professionals, as NIST CSF was also the most commonly used framework by survey respondents. By comparison, PCI-DSS is the most frequently mentioned external regulatory requirement, appearing in 4% of disclosures. The SEC does not require this disclosure.
2. Governance
Often, governance is an entire subsection in Section 1C, detailing how companies internally manage cybersecurity-related processes and identify process owners. This aims to reassure investors of the companies’ diligence in cybersecurity considerations, like disclosing quarterly cybersecurity risk assessments and board communication of these assessments. This disclosure is not mandated by the SEC.
3. Risk assessments
Risk assessments are the first of four risk disclosures in Section 1C. Companies share the frequency, scope, and internal distribution of their risk assessments. The SEC requires this disclosure.
4. Risk management
Risk management is the second of the four risk disclosures in Section 1C. Companies detail their methods for addressing identified risks, often including their approach to determining risk impact and likelihood, using equal measures of qualitative and quantitative methods. The SEC requires this disclosure.
5. Enterprise risk management
Enterprise risk management is the third of the four risk disclosures in Section 1C. Descriptions often relate cybersecurity risk management to overall Enterprise Risk Management (ERM) processes, highlighting the audit committee’s role, to present a comprehensive view of business risks. This disclosure is not mandated by the SEC.
6. Third-party risk
The fourth risk disclosure in Section 1C involves detailed descriptions of how companies evaluate the risks associated with their vendors, suppliers, and customers, including the use of questionnaires and requests for external documentation such as SOC 2 Type 2 or ISO 27001. The nature of this recurring, annual risk assessment process is emphasized. The SEC does not require this disclosure.
7. Compliance
Disclosures often link cybersecurity programs to external regulatory requirements. Surprisingly, 3% of disclosures mention Sarbanes-Oxley (SOX), traditionally associated with IT General Controls (ITGC) rather than broader cybersecurity programs. FFIEC (2%) and HIPAA (3%) also appear frequently, though this is an effect of the companies that have already released their 10-K disclosures. This disclosure is not mandated by the SEC.
8. Incident response plans
Companies often provide an overview of their incident response plans, aligned with NIST 800-61 or the SANS Incident Response Handling Template, focusing primarily on management, board, and regulatory body notifications. This disclosure is not required by the SEC.
9. Training
Training was the most common technical control discussed, coming in at 83%. In this section of the disclosure, companies describe their cybersecurity training programs for employees and contractors, including role-specific and threat-specific training, such as against phishing. This disclosure is not mandated by the SEC.
10. The audit committee
Disclosures often mention that the audit committee, sometimes referred to as the “kitchen sink committee,” receives cybersecurity reports, potentially diluting their focus due to the broad range of topics they cover. This disclosure is not required by the SEC.
11. The Board of Directors
Disclosures often include the board’s cybersecurity experience and expertise, such as certifications (e.g., CISSP) or previous board positions in cybersecurity companies, and how the board receives cybersecurity information from management. The SEC requires this disclosure.
How to get peace of mind about 10-K filings

Companies must carefully balance their disclosures in Section 1C and be ready to demonstrate that their disclosures are not just for show. While no SEC enforcement actions based on Regulation S-K Item 106 have occurred following the current SEC vs. Tim Brown and SolarWinds case, future enforcement actions will likely require evidence of continuous control operation.
This preparation allows CISOs, CIOs, and other management members responsible for cybersecurity to limit the risks of enforcement actions and ensure effective risk reduction through operational controls. As a bonus, they’ll have the peace of mind to know that the controls are operating and reducing risks.
Transparency matters in cybersecurity

Cybersecurity disclosures aim to assure investors that companies are taking appropriate steps to mitigate business risks associated with cybersecurity. They’re also an opportunity for the SEC to understand what’s in common practice, and the level of detail that companies are willing to disclose. This transparency and accountability in cybersecurity matters are relatively new for public companies.
We will continue to review cybersecurity disclosures throughout 2024 to identify and predict best disclosure practices for 2025. Look for our upcoming cohort analysis that compares industry-specific trends as well, coming in early Q2. What we cannot predict is how the SEC plans to enforce the new disclosure regulations, particularly for those companies that have provided a minimal or occasionally combative-toned disclosure.
Wondering how you can ease the process of 10-K filings?
10-K filings are more taxing than ever, and a GRC platform can help. Get peace of mind and full visibility into your compliance and risk management processes with an integrated platform like Hyperproof. The Hyperproof platform helps you see where your cybersecurity risks stand and enable your team to mitigate them faster. And, with integrations into the tools you use every day, you’ll save time and money, making your team more efficient so they can focus on more strategic work.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












