Guide
Understanding the Relationship Between NIS2 and the EU Cyber Resilience Act

Introduction

The European Union has established two key regulations to improve cybersecurity throughout its member states: the NIS2 Directive and the Cyber Resilience Act (CRA). This article examines the specifics of these legislative measures, highlighting their distinct areas of focus, what they mean for organizations doing business in the EU, and how these measures compare with other established frameworks.
NIS2 is a European Union directive that strengthens cybersecurity for essential service providers across critical sectors like energy, transport, and healthcare. It requires organizations to implement risk management practices, report security incidents, and collaborate with other member states.
NIS2 became effective January 16, 2023, giving EU member states until October 17, 2024, to implement it into their national laws. Organizations classified as essential or important entities then have 21 months from the directive’s start date to comply with the new requirements.
The Cyber Resilience Act (CRA) focuses specifically on product security, requiring manufacturers to build cybersecurity features directly into products with digital elements before they can enter the EU market. The CRA emphasizes secure-by-design principles and mandates ongoing security assessments and updates throughout a product’s lifecycle.
The CRA took effect on December 10, 2024. The main obligations introduced by the CRA will apply from December 11, 2027. Manufacturers, importers, and distributors must ensure their products meet CRA standards before EU market entry and must update existing products within the transition period.
Together, these regulations create consistent cybersecurity standards across the EU.
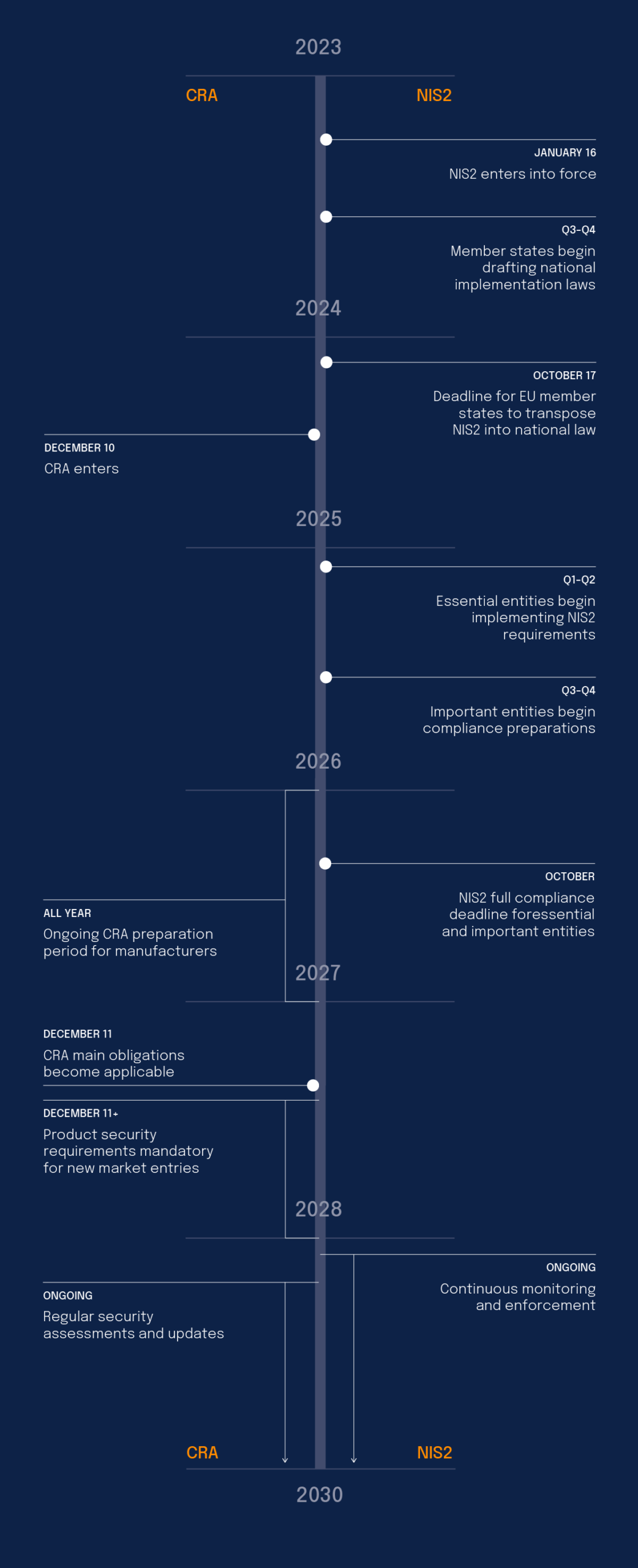
Key implementation timeline
The implementation of NIS2 and CRA follows a structured timeline spanning several years, with key milestones and deadlines for different stakeholders. The following table outlines the critical dates and requirements:
|
Year |
Quarter/Date |
NIS2 Milestones |
CRA Milestones |
|---|---|---|---|
|
2023 |
January 16 |
NIS2 enters into force |
– |
|
2023 |
Q3-Q4 |
Member states begin drafting national implementation laws |
– |
|
2024 |
October 17 |
Deadline for EU member states to transpose NIS2 into national law |
– |
|
2024 |
December 10 |
– |
CRA enters into force |
|
2025 |
Q1-Q2 |
Essential entities begin implementing NIS2 requirements |
– |
|
2025 |
Q3-Q4 |
Important entities begin compliance preparations |
– |
|
2026 |
October |
NIS2 full compliance deadline for essential and important entities |
– |
|
2026 |
All Year |
– |
Ongoing CRA preparation period for manufacturers |
|
2027 |
December 11 |
– |
CRA main obligations become applicable |
|
2027 |
December 11+ |
– |
Product security requirements mandatory for new market entries |
|
2028-2030 |
Ongoing |
Continuous monitoring and enforcement |
Regular security assessments and updates |
Core framework distinctions
NIS2 focuses on protecting essential and important service providers across the EU. It covers critical sectors like energy, transport, banking, health, and digital infrastructure. The directive requires organizations to implement strong risk management practices and report security incidents quickly to maintain critical infrastructure reliability during cyber threats.
The CRA specifically addresses products with digital components, including both hardware and software. Manufacturers, importers, and distributors must prove their products meet security requirements before entering the EU market. Products need built-in security features from the design phase plus regular security testing and updates throughout their lifecycle.

While NIS2 and the CRA have different focuses within the EU’s cybersecurity framework, many organizations need to comply with both regulations. Understanding where these requirements overlap and differ helps organizations better plan their compliance efforts and allocate resources effectively.
Many organizations find that requirements between the two regulations complement rather than contradict each other. By identifying shared requirements, security teams can implement controls that satisfy both regulations at once, creating more efficient compliance programs. The following table breaks down these requirements in detail:
Technical requirements comparison
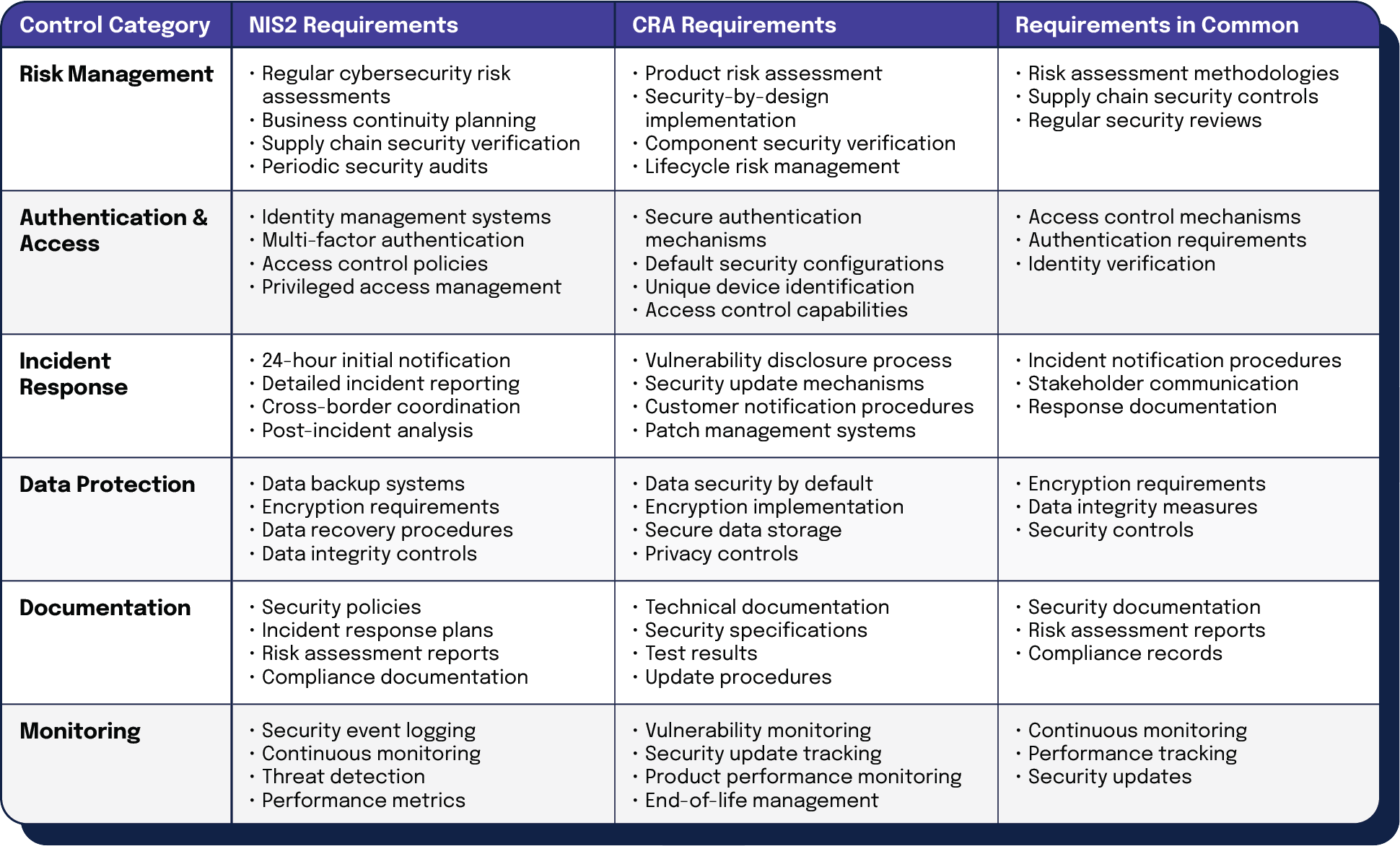
| Control Category | NIS2 Requirements | CRA Requirements | Requirements in Common |
| Risk Management | • Regular cybersecurity risk assessments • Business continuity planning • Supply chain security verification • Periodic security audits | • Product risk assessment • Security-by-design implementation • Component security verification • Lifecycle risk management | • Risk assessment methodologies • Supply chain security controls • Regular security reviews |
| Authentication & Access | • Identity management systems • Multi-factor authentication • Access control policies • Privileged access management | • Secure authentication mechanisms • Default security configurations • Unique device identification • Access control capabilities | • Access control mechanisms • Authentication requirements • Identity verification |
| Incident Response | • 24-hour initial notification • Detailed incident reporting • Cross-border coordination • Post-incident analysis | • Vulnerability disclosure process • Security update mechanisms • Customer notification procedures • Patch management systems | • Incident notification procedures • Stakeholder communication • Response documentation |
| Data Protection | • Data backup systems • Encryption requirements • Data recovery procedures • Data integrity controls | • Data security by default • Encryption implementation • Secure data storage • Privacy controls | • Encryption requirements • Data integrity measures • Security controls |
| Documentation | • Security policies • Incident response plans • Risk assessment reports • Compliance documentation | • Technical documentation • Security specifications • Test results • Update procedures | • Security documentation • Risk assessment reports • Compliance records |
| Monitoring | • Security event logging • Continuous monitoring • Threat detection • Performance metrics | • Vulnerability monitoring • Security update tracking • Product performance monitoring • End-of-life management | • Continuous monitoring • Performance tracking • Security updates |
Special considerations for critical infrastructure providers
Critical infrastructure providers face heightened requirements under both regulations.
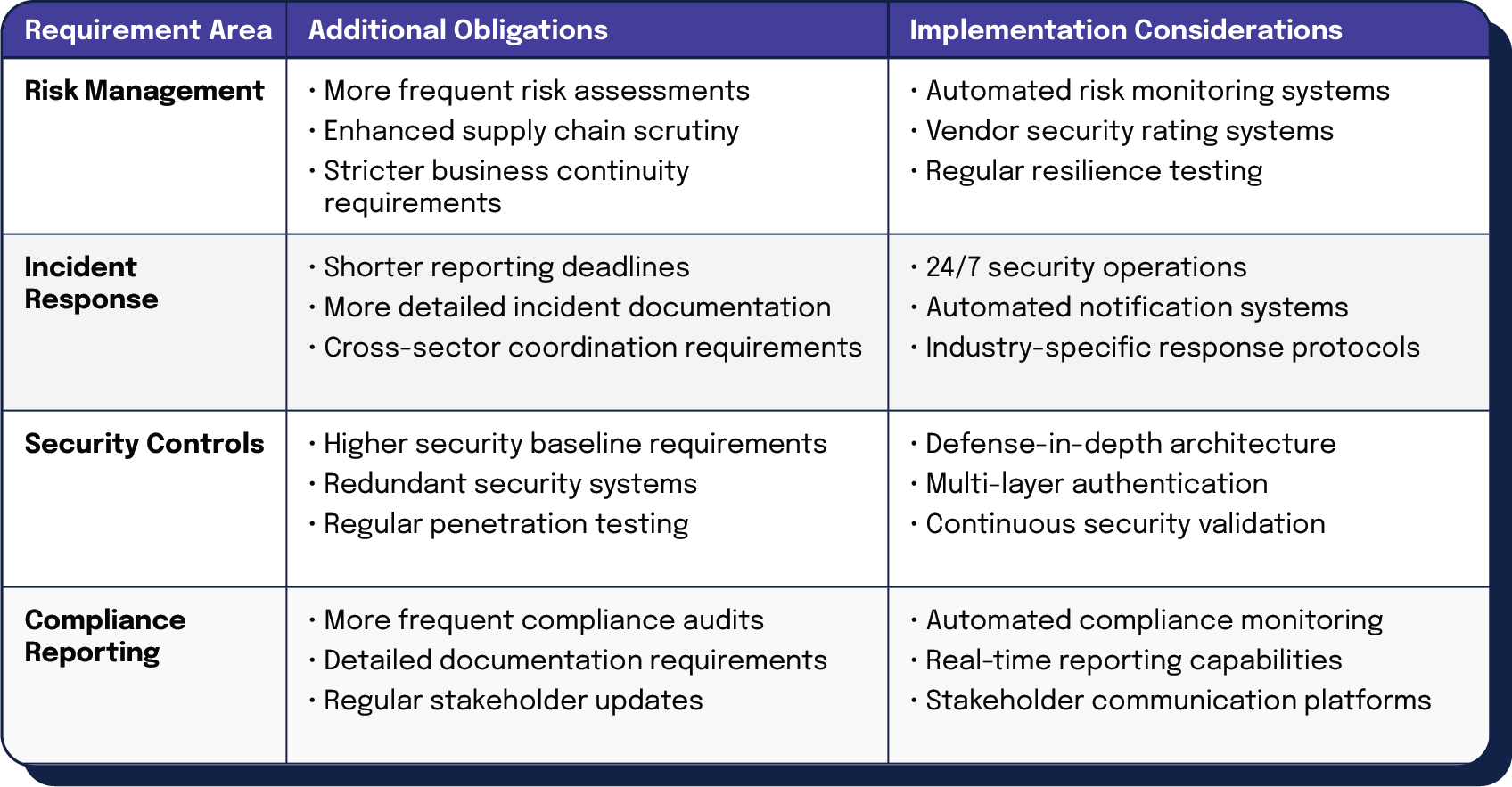
| Requirement Area | Additional Obligations | Implementation Considerations |
| Risk Management | • More frequent risk assessments • Enhanced supply chain scrutiny • Stricter business continuity requirements | • Automated risk monitoring systems • Vendor security rating systems • Regular resilience testing |
| Incident Response | • Shorter reporting deadlines • More detailed incident documentation • Cross-sector coordination requirements | • 24/7 security operations • Automated notification systems • Industry-specific response protocols |
| Security Controls | • Higher security baseline requirements • Redundant security systems • Regular penetration testing | • Defense-in-depth architecture • Multi-layer authentication • Continuous security validation |
| Compliance Reporting | • More frequent compliance audits • Detailed documentation requirements • Regular stakeholder updates | • Automated compliance monitoring • Real-time reporting capabilities • Stakeholder communication platforms |
Sector-specific requirements
Different critical infrastructure sectors face unique challenges:
Energy sector
Healthcare providers
Transportation
Financial services
Cross-sector dependencies

Critical infrastructure providers must consider:
Extraterritorial reach
NIS2 extends to all organizations providing essential or important services in the EU market, regardless of where they’re headquartered. These organizations must follow EU security standards, including implementing risk management protocols and meeting incident reporting requirements to operate within EU territories.
The CRA applies to all companies selling digital products in the EU, regardless of their location. Products must meet the act’s security standards and incorporate security by design before entering the EU market, creating a uniform security baseline across the EU marketplace.
Comparison with global cybersecurity frameworks

Organizations already aligned with established frameworks like NIST CSF and ISO 27001 may find overlapping requirements with NIS2 and CRA, though important distinctions exist.
NIST CSF alignment
The NIST Cybersecurity Framework provides a voluntary, risk-based approach to managing cybersecurity risk that complements NIS2 requirements:
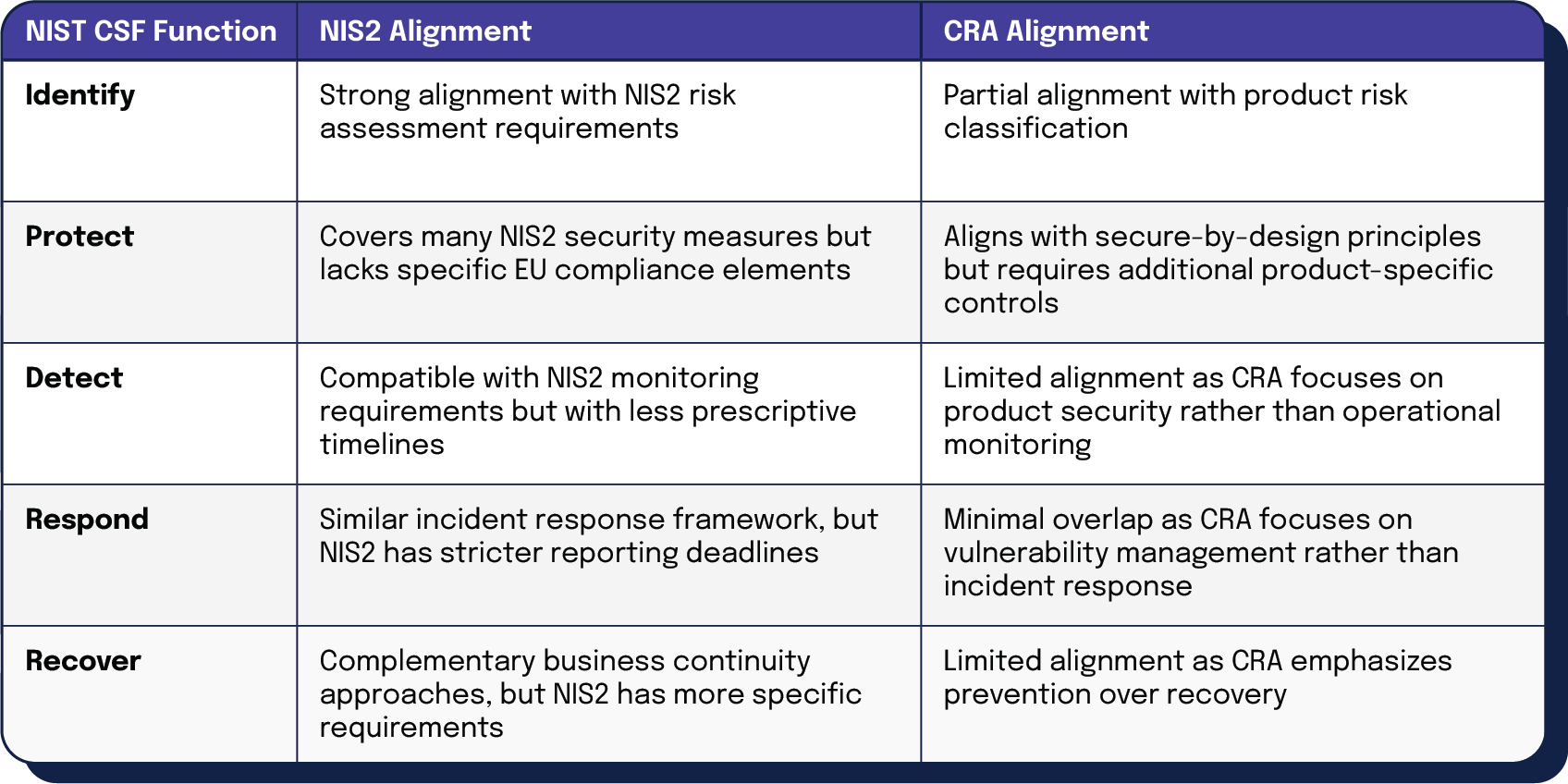
| NIST CSF Function | NIS2 Alignment | CRA Alignment |
| Identify | Strong alignment with NIS2 risk assessment requirements | Partial alignment with product risk classification |
| Protect | Covers many NIS2 security measures but lacks specific EU compliance elements | Aligns with secure-by-design principles but requires additional product-specific controls |
| Detect | Compatible with NIS2 monitoring requirements but with less prescriptive timelines | Limited alignment as CRA focuses on product security rather than operational monitoring |
| Respond | Similar incident response framework, but NIS2 has stricter reporting deadlines | Minimal overlap as CRA focuses on vulnerability management rather than incident response |
| Recover | Complementary business continuity approaches, but NIS2 has more specific requirements | Limited alignment as CRA emphasizes prevention over recovery |
Organizations using NIST CSF will need to enhance their frameworks with EU-specific requirements, particularly around incident reporting timelines and cross-border coordination mechanisms.
ISO 27001 compatibility
ISO 27001, as an internationally recognized standard for information security management systems (ISMS), provides a strong foundation for NIS2 compliance:
Risk assessment methodology
ISO 27001’s risk-based approach aligns with NIS2 requirements but must be expanded to include EU-specific threat scenarios and sector-specific vulnerabilities.
Control implementation
Many ISO 27001 Annex A controls map directly to NIS2 security measures, though organizations must implement additional controls specific to EU operations.
Documentation requirements
ISO 27001’s documentation approach supports NIS2 compliance evidence but requires enhancement to meet specific EU reporting formats.
For CRA compliance, ISO 27001 provides valuable security development practices but lacks product-specific security requirements. Organizations must supplement their ISMS with:
Organizations with mature ISO 27001 implementations will find themselves well-positioned for NIS2 and CRA compliance, but will still need targeted enhancements to address EU-specific requirements and product security elements.
Impact on small and medium-sized enterprises
Small and medium-sized enterprises (SMEs) face unique challenges under both directives, particularly when supporting essential services or developing digital products.
While NIS2 mainly targets larger organizations, SMEs providing critical services or supporting major entities must meet stricter cybersecurity standards. This often requires significant investments in security systems and expertise, stretching their limited resources thin.
The Cyber Resilience Act (CRA) adds more compliance hurdles for SMEs that make or distribute digital products. Meeting secure-by-design principles and maintaining regular security updates requires substantial resources, which can strain SMEs’ tight budgets and limited technical teams.
Enforcement mechanisms
National authority oversight
National authorities enforce both directives through distinct yet complementary roles. For NIS2, they actively monitor cybersecurity implementation within their jurisdictions by conducting regular audits and compliance checks. These authorities collaborate across EU member states to share threat intelligence and best practices.
For the CRA, national authorities verify that digital products meet required security standards through market surveillance. They ensure manufacturers, importers, and distributors follow secure-by-design principles and maintain up-to-date security requirements. These bodies have the power to impose sanctions, restrict market access for non-compliant products, and work with other EU nations to tackle cross-border security challenges.
Noncompliance consequences
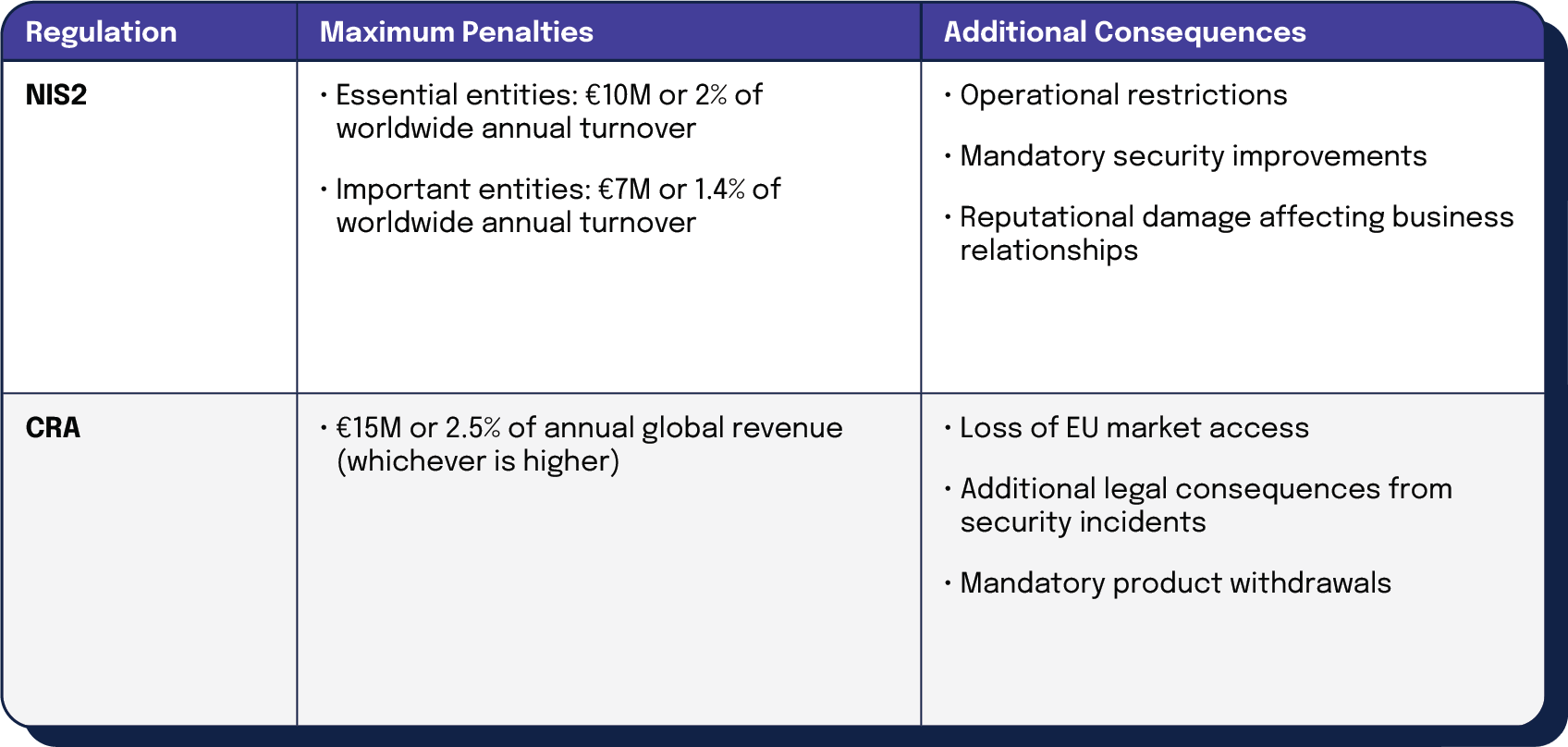
| Regulation | Maximum Penalties | Additional Consequences |
| NIS2 | • Essential entities: €10M or 2% of worldwide annual turnover • Important entities: €7M or 1.4% of worldwide annual turnover | • Operational restrictions • Mandatory security improvements • Reputational damage affecting business relationships |
| CRA | €15M or 2.5% of annual global revenue (whichever is higher) | • Loss of EU market access • Additional legal consequences from security incidents • Mandatory product withdrawals |
Security and risk management
The EU places secure-by-design and secure-by-default standards at the heart of its cybersecurity strategy. These principles require developers to integrate security features into products and systems during initial development, not as afterthoughts. This proactive approach prevents common vulnerabilities and builds stronger, more resilient digital infrastructure.
Security measures must cover a product’s complete lifecycle, from concept to maintenance. Products come with the strongest security settings pre-configured, protecting users from common configuration mistakes. These standards help build consumer trust and create a more secure digital marketplace.
Integration with EU privacy laws
Regulatory alignment
NIS2 and CRA work alongside existing EU privacy frameworks, particularly the General Data Protection Regulation (GDPR). While GDPR protects personal data, NIS2 and CRA extend protection to include comprehensive cybersecurity requirements. Organizations can build on their existing GDPR compliance systems to meet many NIS2 and CRA requirements, particularly in areas such as:
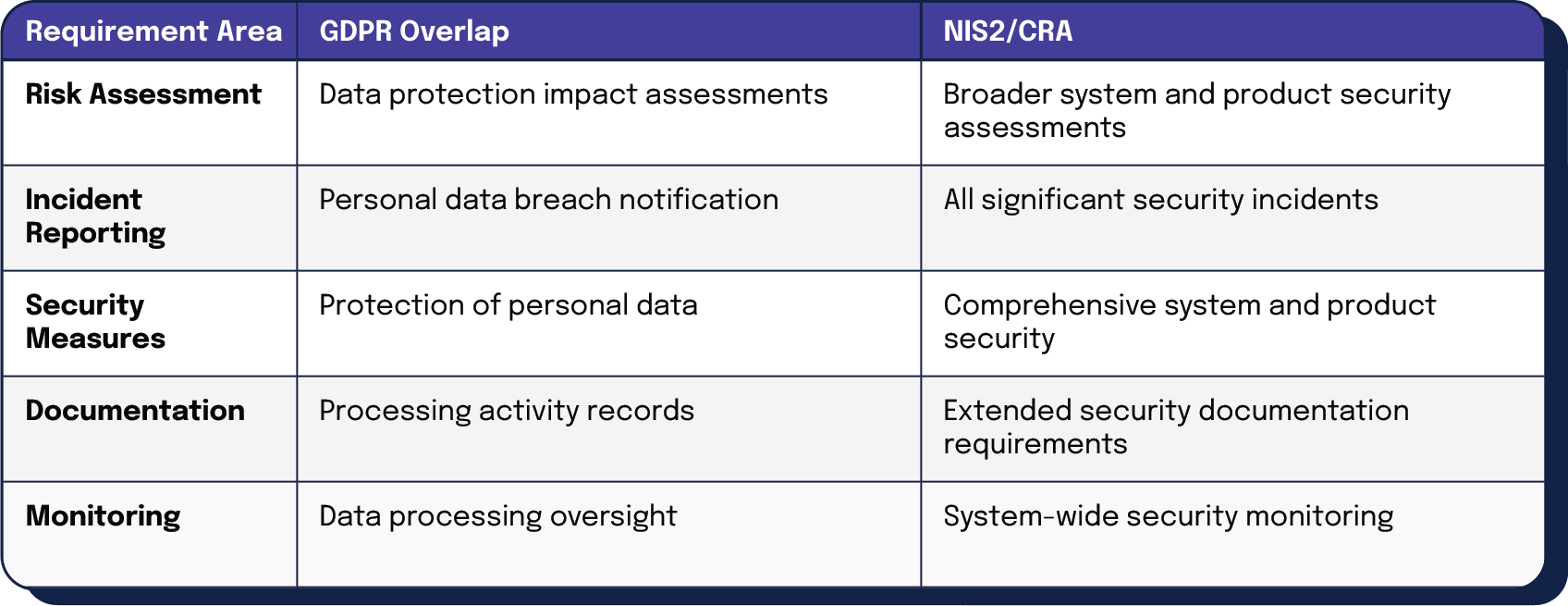
| Requirement Area | GDPR Overlap | NIS2/CRA |
| Risk Assessment | Data protection impact assessments | Broader system and product security assessments |
| Incident Reporting | Personal data breach notification | All significant security incidents |
| Security Measures | Protection of personal data | Comprehensive system and product security |
| Documentation | Processing activity records | Extended security documentation requirements |
| Monitoring | Data processing oversight | System-wide security monitoring |
Compliance similarities
Organizations can streamline their operations by:
Key distinctions
Integration with other EU cybersecurity initiatives
Alignment with ENISA guidelines
The European Union Agency for Cybersecurity (ENISA) provides crucial implementation guidance for both NIS2 and the CRA:
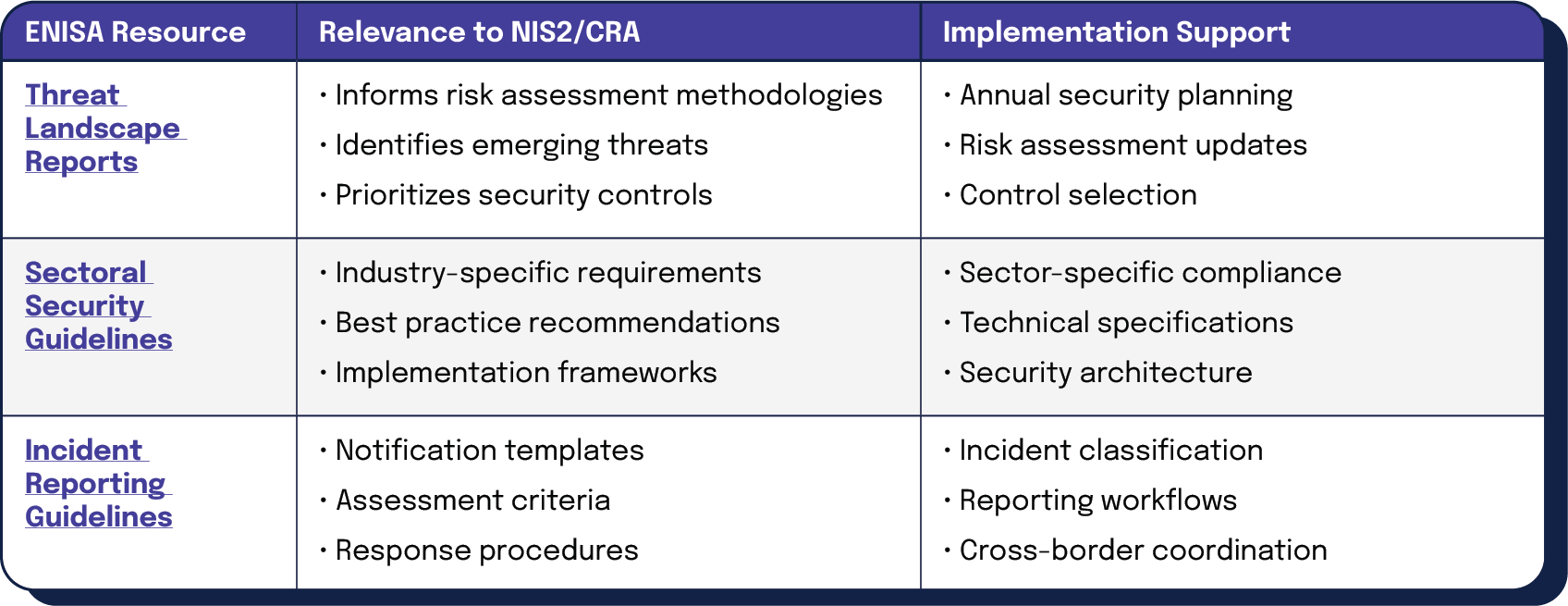
| ENISA Resource | Relevance to NIS2/CRA | Implementation Support |
| Threat Landscape Reports | • Informs risk assessment methodologies • Identifies emerging threats • Prioritizes security controls | • Annual security planning • Risk assessment updates • Control selection |
| Sectoral Security Guidelines | • Industry-specific requirements • Best practice recommendations • Implementation frameworks | • Sector-specific compliance • Technical specifications • Security architecture |
| Incident Reporting Guidelines | • Notification templates • Assessment criteria • Response procedures | • Incident classification • Reporting workflows • Cross-border coordination |
ETSI Standards Integration
European Telecommunications Standards Institute (ETSI) standards provide technical specifications supporting compliance:
EN 303 645 – IoT Security Standard
TS 103 1645 – Cyber Security for Consumer IoT
EN 303 647 – Security Assessment Requirements
Certification frameworks
EU cybersecurity certification schemes complement regulatory requirements:
Supply chain security
NIS2 and the CRA establish robust supply chain security requirements.
NIS2
Requires comprehensive risk management practices, including detailed vendor and service provider assessments. Organizations must verify their suppliers follow equivalent security standards.
CRA
Enhances product security in supply chains by setting cybersecurity standards for market entry. Manufacturers must integrate security during product design and maintain ongoing security assessments and updates.
Both directives encourage stakeholder cooperation and information sharing to strengthen supply chain security, enabling participants to identify and address risks within complex supply networks more effectively.
Cooperation and information sharing
NIS2 and the CRA establish robust frameworks for cooperation and information sharing among EU member states through structured frameworks and collaborative platforms.
NIS2
Creates a Cooperation Group where member states exchange threat intelligence, share best practices, and develop unified cybersecurity strategies. It also establishes a network of Computer Security Incident Response Teams (CSIRTs) to enhance operational cooperation and information exchange.
CRA
Builds on these efforts by increasing digital product security transparency. Manufacturers must provide clear information about their products’ security features, including how they manage vulnerabilities and handle security updates.
These initiatives create a collaborative environment where member states can work together to improve their cybersecurity stance and respond to emerging threats more quickly.
Industry trends and external influences
NIS2 and the CRA guide the development of emerging technologies like IoT and Artificial Intelligence (AI) through security requirements that emphasize safety and resilience.
Global impact

NIS2 and the CRA establish robust cybersecurity standards that influence practices worldwide. Their emphasis on secure-by-design principles and thorough risk management provides a blueprint for organizations seeking to strengthen their security.
These regulations affect any business operating in the EU market, setting strict security standards. When global companies enhance their security practices to meet EU requirements, they typically improve security across their entire operations.
Impact on software development lifecycle
The NIS2 Directive and Cyber Resilience Act potentially impact software development practices, requiring security integration throughout the development lifecycle:
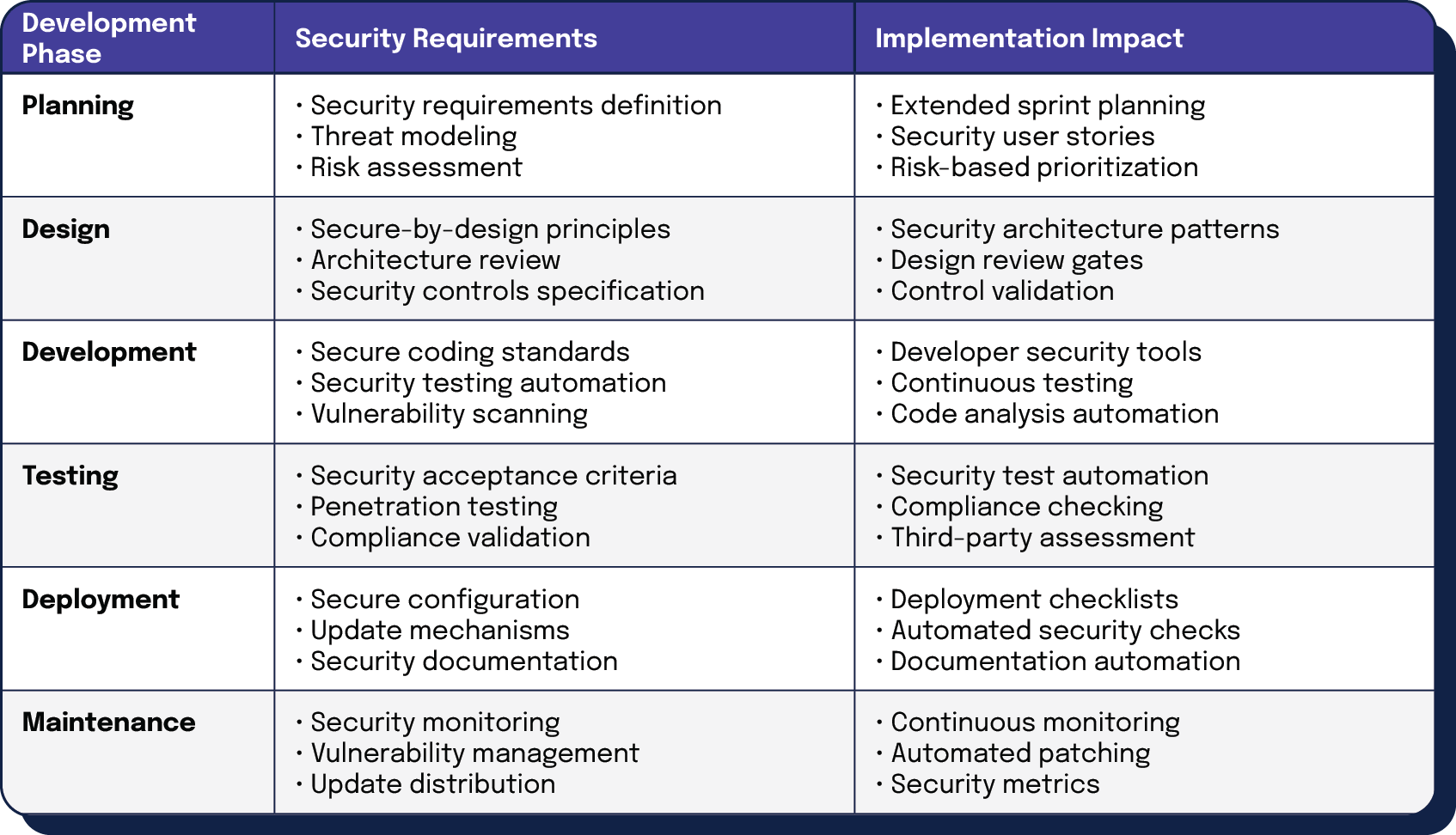
| Development Phase | Security Requirements | Implementation Impact |
| Planning | • Security requirements definition • Threat modeling • Risk assessment | • Extended sprint planning • Security user stories • Risk-based prioritization |
| Design | • Secure-by-design principles • Architecture review • Security controls specification | • Security architecture patterns • Design review gates • Control validation |
| Development | • Secure coding standards • Security testing automation • Vulnerability scanning | • Developer security tools • Continuous testing • Code analysis automation |
| Testing | • Security acceptance criteria • Penetration testing • Compliance validation | • Security test automation • Compliance checking • Third-party assessment |
| Deployment | • Secure configuration • Update mechanisms • Security documentation | • Deployment checklists • Automated security checks • Documentation automation |
| Maintenance | • Security monitoring • Vulnerability management • Update distribution | • Continuous monitoring • Automated patching • Security metrics |
Open source software considerations
The NIS2 and CRA regulations also impact open-source software development and distribution within the EU market:
Implementation challenges
NIS2 directive implementation
Organizations face several hurdles when implementing NIS2.
Smaller organizations particularly struggle with resource allocation. Cross-border cooperation and information sharing complicate compliance, especially for companies working across multiple jurisdictions.
Cyber Resilience Act requirements
The CRA sets itself apart from traditional international standards by mandating specific product security requirements through secure-by-design and secure-by-default principles. Unlike frameworks focused on organizational security, the CRA requires manufacturers, importers, and distributors to demonstrate product compliance before entering the EU market.
The act applies consistently across EU member states, ensuring uniform enforcement, unlike international standards that depend on voluntary adoption or national laws. The CRA’s hefty financial penalties for violations distinguish it from less stringent international standards.
Harmonization challenges
Implementing uniform cybersecurity standards across EU member states faces obstacles due to diverse regulatory systems and varying cybersecurity maturity levels. Each country maintains distinct laws, enforcement approaches, and cultural attitudes toward cybersecurity, resulting in inconsistent standard implementation.
Getting all member states to agree on specific cybersecurity policies is a complex process. Each country balances its national interests against EU-wide security goals, with different priorities based on their unique threats and economic circumstances.
Compliance cost considerations
Understanding the financial implications of NIS2 and CRA compliance is crucial for effective resource planning. The following table outlines key cost factors, their variables, and essential planning considerations:
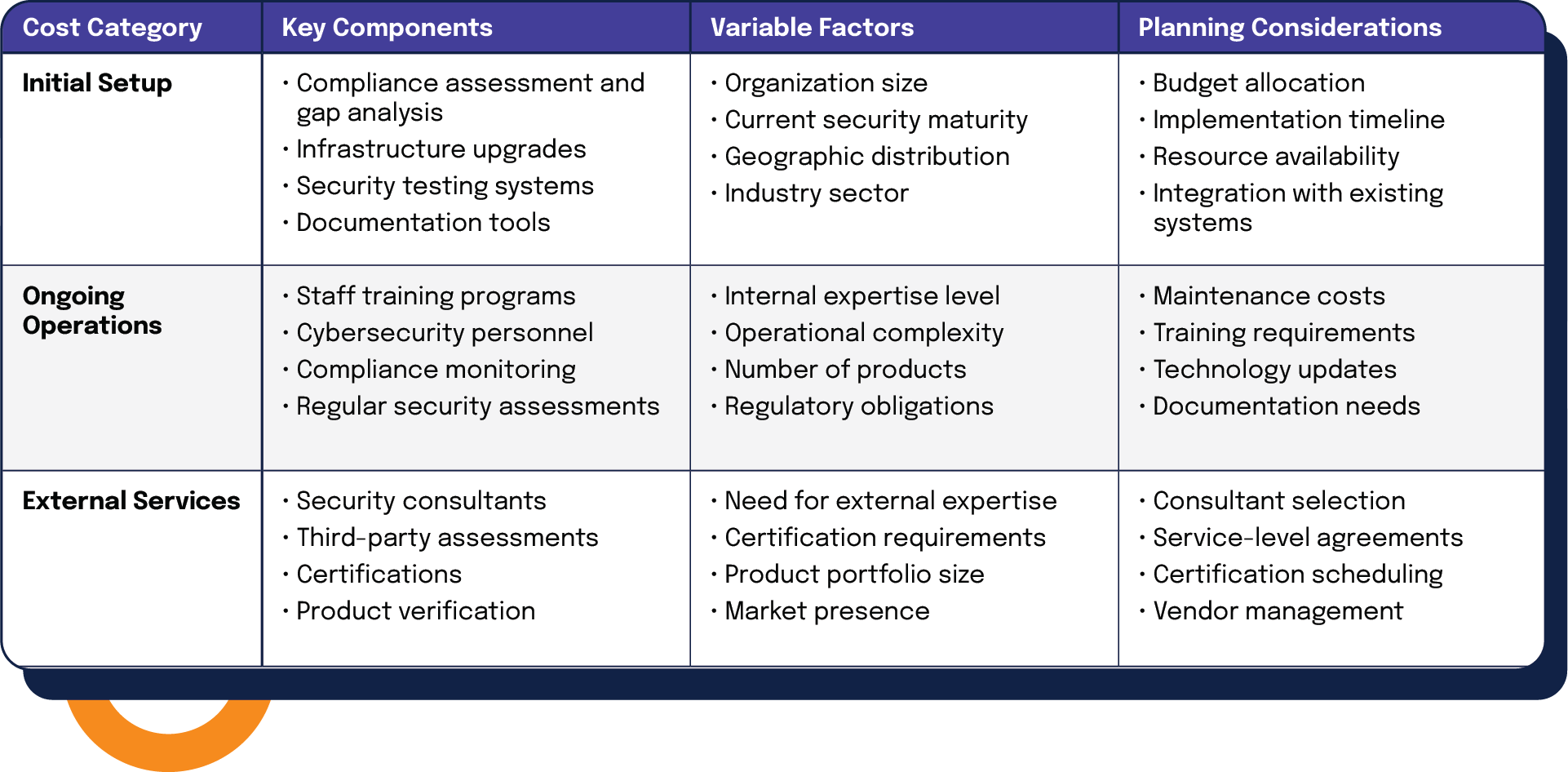
| Cost Category | Key Components | Variable Factors | Planning Considerations |
| Initial Setup | • Compliance assessment and gap analysis • Infrastructure upgrades • Security testing systems • Documentation tools | • Organization size • Current security maturity • Geographic distribution • Industry sector | • Budget allocation • Implementation timeline • Resource availability • Integration with existing systems |
| Ongoing Operations | • Staff training programs • Cybersecurity personnel • Compliance monitoring • Regular security assessments | • Internal expertise level • Operational complexity • Number of products • Regulatory obligations | • Maintenance costs • Training requirements • Technology updates • Documentation needs |
| External Services | • Security consultants • Third-party assessments • Certifications • Product verification | • Need for external expertise • Certification requirements • Product portfolio size • Market presence | • Consultant selection • Service-level agreements • Certification scheduling • Vendor management |
Strategic considerations for cybersecurity compliance
The key challenge lies in balancing regulatory compliance with operational efficiency and innovation while maintaining strong security practices.
Organizational structure and processes
Balancing innovation and compliance
Organizations must meet both regulatory requirements and innovation goals without compromising either priority. By embedding security into product development from the start, organizations can satisfy both NIS2 and CRA requirements while driving innovation. Cross-functional collaboration between IT, compliance, and product teams helps align security with new initiatives.
Regular policy reviews keep security measures current with evolving threats and regulations. Automated compliance monitoring reduces administrative burden while maintaining innovation focus. Industry partnerships provide valuable intelligence about emerging threats and effective countermeasures.
Three recommendations to achieve dual compliance

Updated risk management framework
Organizations should implement an integrated risk management framework that addresses both NIS2 and CRA requirements through:
Gap analysis
Organizations should use the following compliance status rating system to evaluate their current implementation progress:
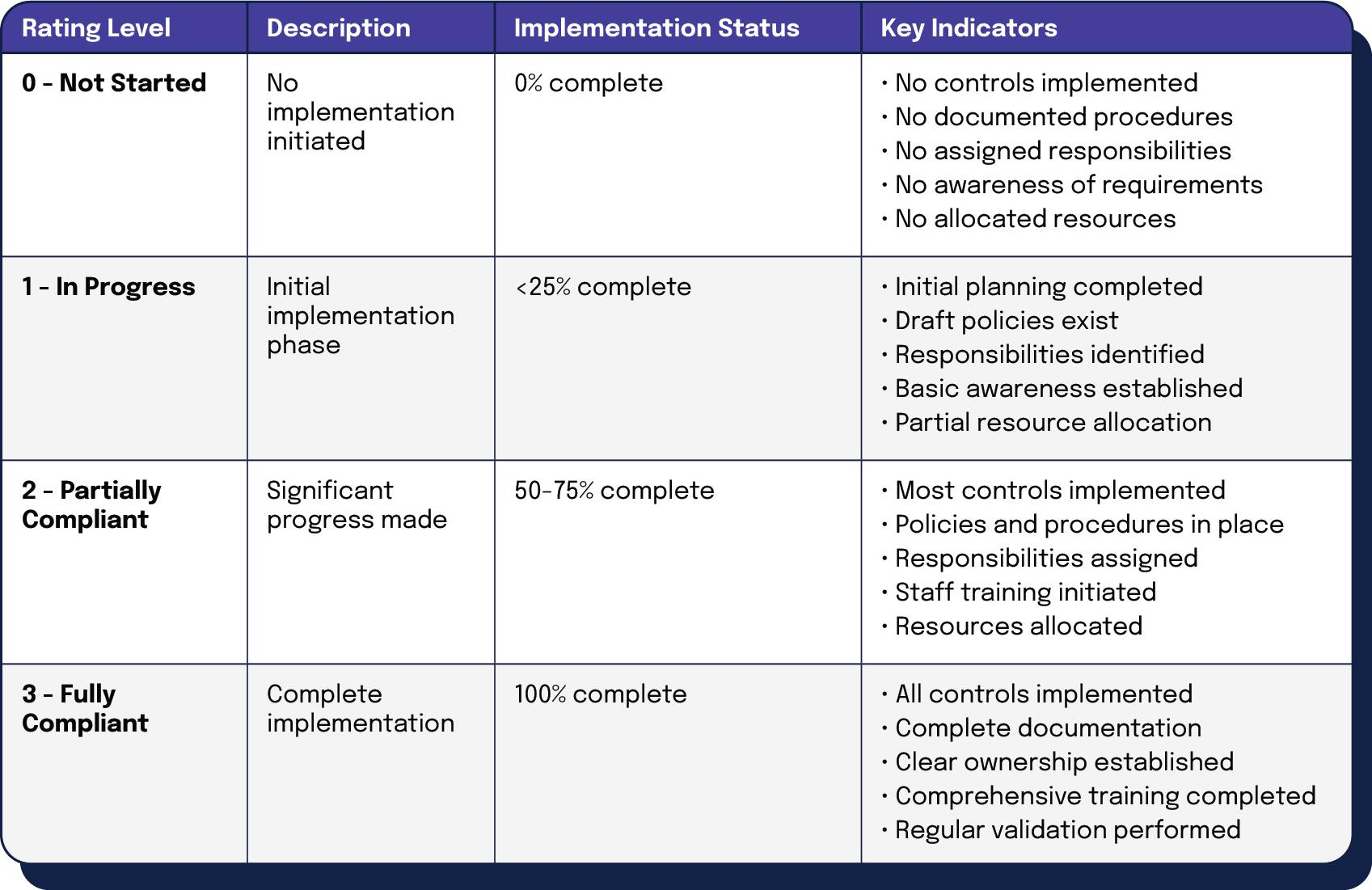
| Rating Level | Description | Implementation Status | Key Indicators |
| 0 – Not Started | No implementation initiated | 0% complete | • No controls implemented • No documented procedures • No assigned responsibilities • No awareness of requirements • No allocated resources |
| 1 – In Progress | Initial implementation phase | <25% complete | • Initial planning completed • Draft policies exist • Responsibilities identified • Basic awareness established • Partial resource allocation |
| 2 – Partially Compliant | Significant progress made | 50-75% complete | • Most controls implemented • Policies and procedures in place • Responsibilities assigned • Staff training initiated • Resources allocated |
| 3 – Fully Compliant | Complete implementation | 100% complete | • All controls implemented • Complete documentation • Clear ownership established • Comprehensive training completed • Regular validation performed |
Recommended operational practices
To maintain compliance and security, organizations should:
Success depends on clear leadership commitment and organization-wide engagement. By taking this comprehensive approach, companies can effectively navigate EU cybersecurity requirements while protecting their critical assets and stakeholders.
NIS2 and the CRA build trust and strengthen resilience against cyber threats

While NIS2 and the CRA address different aspects of cybersecurity – NIS2 focusing on service providers and the CRA on digital products – they share significant overlap in their core security principles and requirements. Many security controls, risk assessment methodologies, and documentation practices required by both regulations align well with existing cybersecurity frameworks like ISO 27001 and NIST CSF that many organizations already follow.
For businesses with mature security programs, achieving compliance may be less burdensome than anticipated. Organizations that have invested in information security management systems, risk assessments, and security monitoring will find they already have many of the building blocks needed for NIS2 and CRA compliance. The additional requirements often represent extensions or enhancements to existing practices rather than completely new processes.
However, organizations starting with minimal security infrastructure face a steeper implementation curve. Small and medium-sized enterprises without dedicated security resources or established governance frameworks will need to make more substantial investments in technology, expertise, and processes to meet compliance requirements.
The complementary nature of these regulations creates an opportunity for organizations to develop integrated compliance approaches rather than treating each regulation separately. By identifying shared requirements across NIS2, CRA, and other frameworks like GDPR, companies can implement controls that satisfy multiple regulatory obligations simultaneously, creating more efficient compliance programs.
As these regulations come into full effect over the next several years, organizations can expect a more uniform cybersecurity baseline across the EU, ultimately strengthening resilience against cyber threats and building greater trust in digital products and services. Organizations that view compliance not merely as a regulatory burden but as an opportunity to enhance their security posture will be best positioned to thrive in this new regulatory environment.
Download the PDF