The Ultimate Guide to
Service Organization Control (SOC) 2®
What is SOC 2®?
SOC 2® is an auditing procedure developed by the American Institute of CPAs (AICPA) that ensures your business or application is handling customer data securely and in a manner that protects your organization and the privacy of your customers.
Businesses that handle customer data proactively perform SOC 2® audits to ensure they meet all of the criteria. Once an outside auditor performs an SOC 2® audit, if the business passes, the auditor will issue an SOC 2® certificate showing that the business complies with all of the requirements.
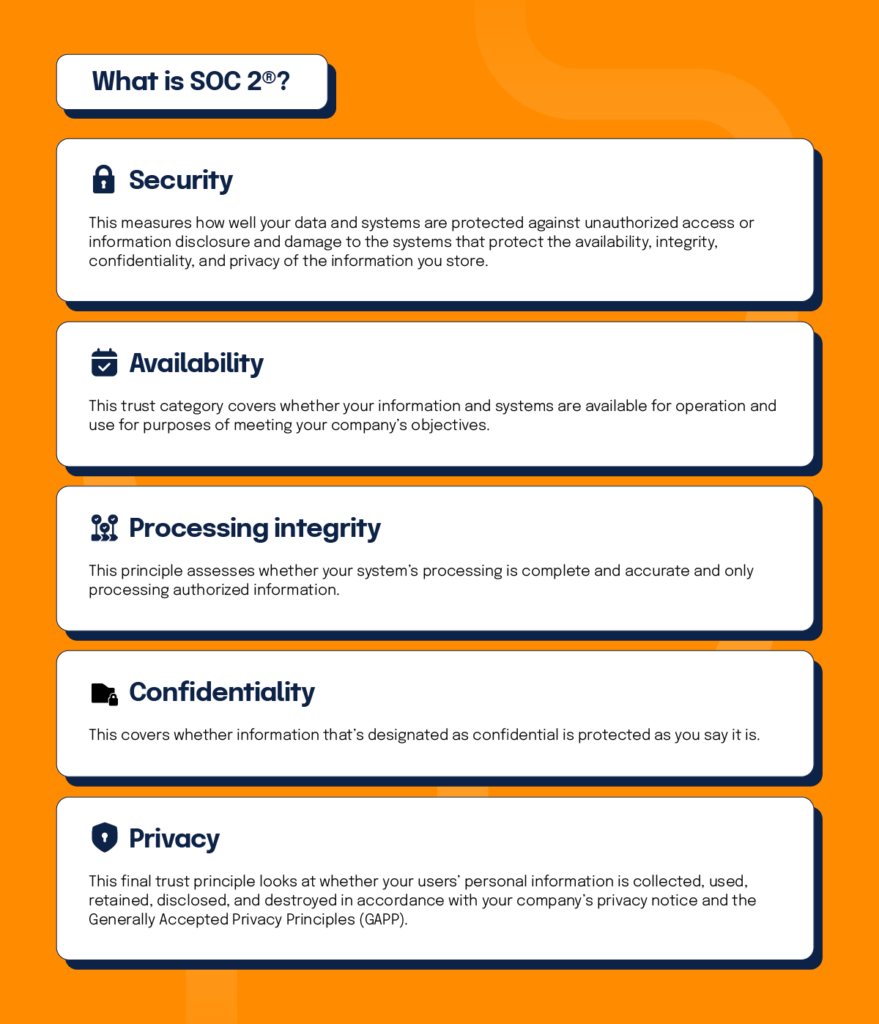
External auditors assess and grant SOC 2® attestation based on the following five Trust Service Criteria:
- Security: This measures how well your data and systems are protected against unauthorized access or information disclosure and damage to the systems that protect the availability, integrity, confidentiality, and privacy of the information you store.
- Availability: This trust category covers whether your information and systems are available for operation and use for purposes of meeting your company’s objectives.
- Processing integrity: This principle assesses whether your system’s processing is complete and accurate and only processing authorized information.
- Confidentiality: This covers whether information that’s designated as confidential is protected as you say it is.
- Privacy: This final trust principle looks at whether your users’ personal information is collected, used, retained, disclosed, and destroyed in accordance with your company’s privacy notice and the Generally Accepted Privacy Principles (GAPP).
What is SOC 2® compliance?
SOC 2® compliance involves being granted an attestation for a collection of reports that an external CPA uses to validate the security, availability, processing integrity, confidentiality, and privacy controls of confidential business data that your organization has established.
SOC 2® compliance can be particularly useful for SaaS providers and any company that handles customer data. Pro tip: If applicable, your SOC 2® report can show how your organization adheres to other applicable privacy requirements such as the Privacy Management Framework, GDPR, or CCPA.
| Note: Your organization only needs to include the SOC 2® Trust Service Categories that apply to your processes. You need not adhere to all five SOC 2® Trust Service Categories. For example, if your company only stores customer information and doesn’t handle any information processing, you don’t need to audit for the Processing Integrity trust principle. |
What is a SOC 2® report?
A SOC 2® report is an important asset for organizations, and it’s becoming more of a mandate than a nice-to-have. But reporting can be time-consuming and expensive, especially if your organization doesn’t have compliance expertise or modern tools to handle the work. Here’s the good news: there is a way to gain control over your SOC 2® compliance program and dramatically reduce your workload.
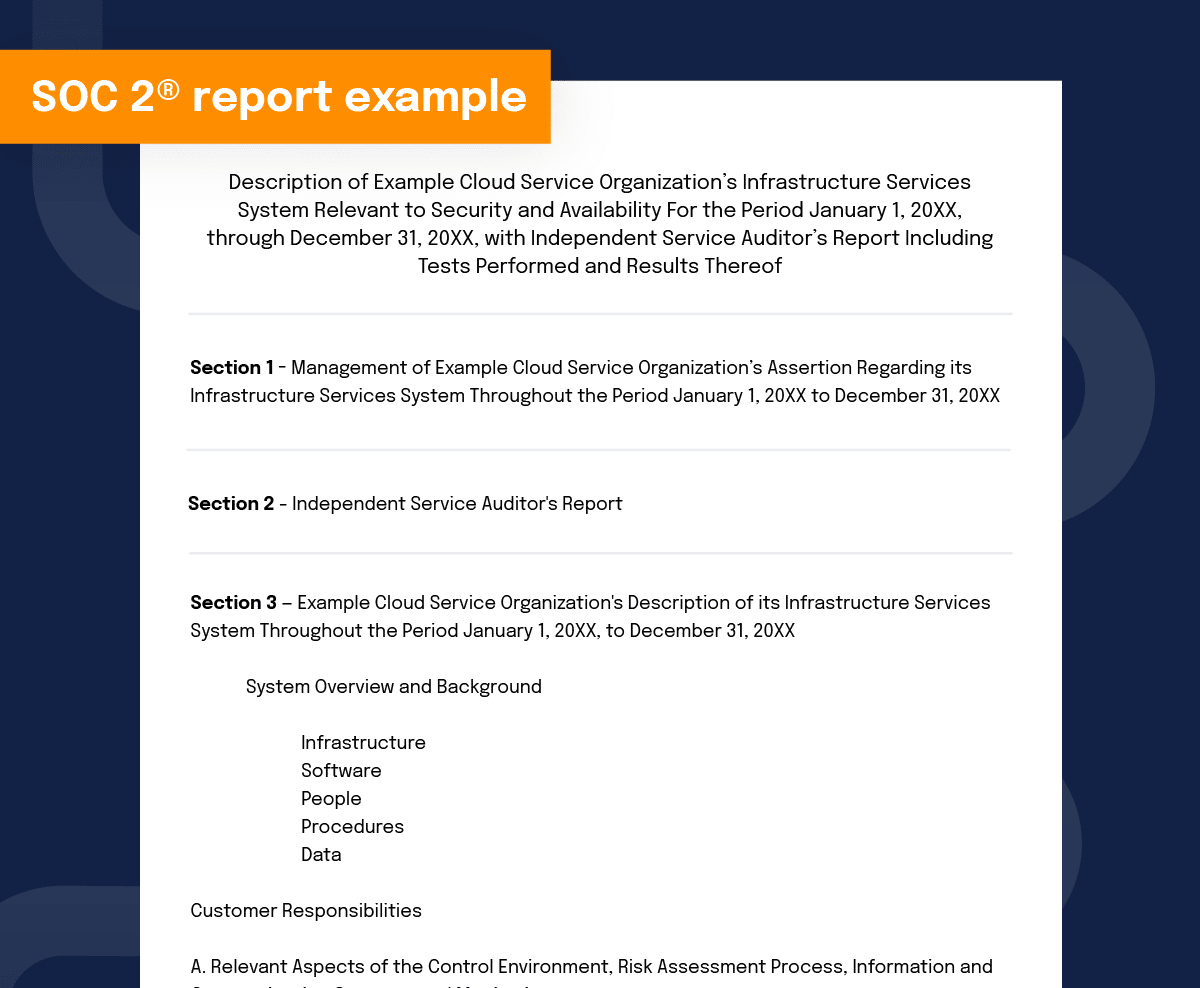
Developed by the American Institute of CPAs (AICPA), this reporting provides insight into internal controls that exist within an organization to address risks related to security, availability, processing integrity, confidentiality and/or privacy. A CPA independently validates the report and uses specific criteria, methodology and expectations that enable consistency in comparison across organizations. Before a report is issued, an independent CPA conducts an assessment of the scope, design, and (for Type 2 reports) the effectiveness of internal control processes. Your organization and your SOC 2® assessor determine the scope of a SOC 2® report.
Learn how to get a SOC 2® report in our step-by-step guide
What are the benefits of SOC 2® compliance?
SOC 2® is a must-have for any organization that manages customer data or integrates with business partners. If you’re selling software or services, your customers will want to see your SOC 2® report to have confidence that their data will be protected and that you won’t introduce vulnerabilities into their systems. If your customers or business partners are in highly regulated fields or are publicly traded companies, a SOC 2® report is imperative to be considered as a viable vendor.
A SOC 2® report can also help reduce audit fatigue by eliminating or reducing the need for audits from customers and business partners. As part of their risk management practices, many companies annually audit their customers and business partners. This can result in being bombarded with a high volume of time-consuming audits coming from multiple sources. A SOC 2® report is a great solution for this, as companies will often accept a SOC 2® report in place of conducting a separate audit.
What should be the scope of a SOC 2® audit?
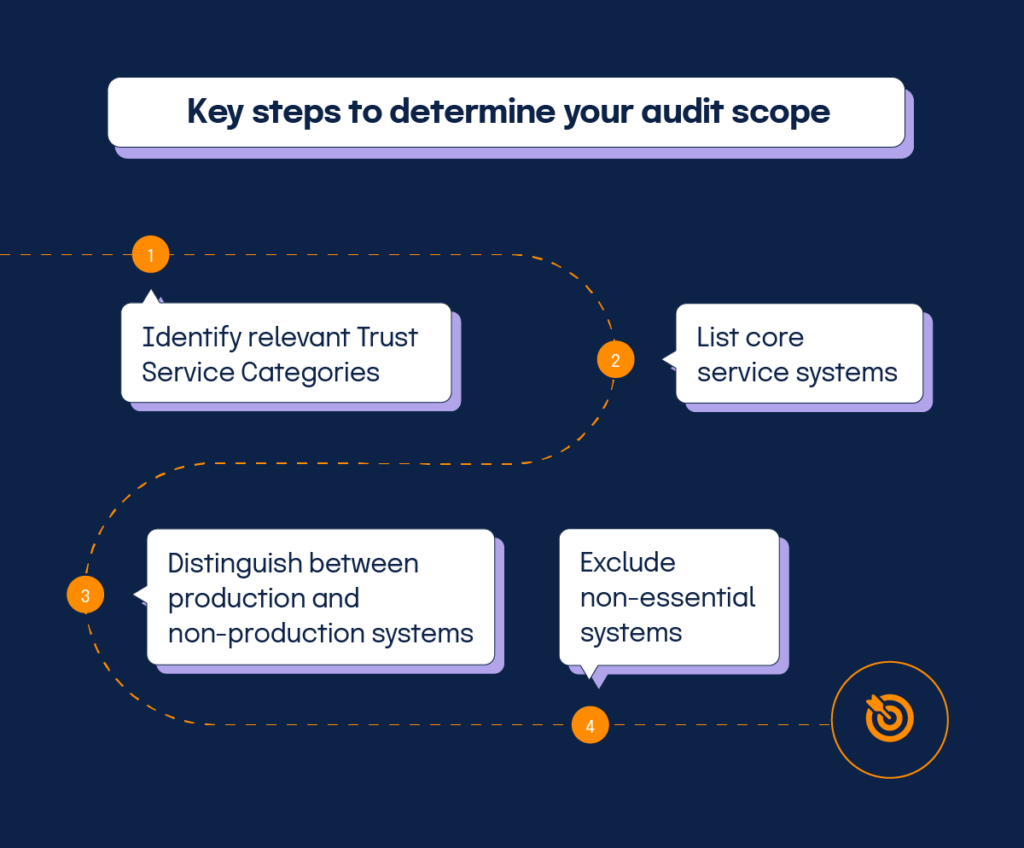
Determining the scope of your SOC 2® audit is critical to its success. If you include too much in the scope of your audit, you’ll waste unnecessary time on processes and procedures you don’t have or need, and if your scope is too narrow you won’t be evaluating the things that matter to your current and prospective customers, risking the chance of spending more on remediation measures and future audits.
To get started, review our SOC 2® Audit Checklist
Will my SOC 2® audit cover all five Trust Service Categories?
Every audit doesn’t have to include all five of the trust service categories because those categories won’t apply to every company. For example, if your company only stores customer information and doesn’t handle any information processing, you don’t need to audit for the Processing Integrity trust principle; likewise, if you don’t store any data that is considered confidential, you don’t need to audit for the Confidentiality principle. The scope of your audit should be informed by what is most relevant to your customer base and their primary concerns.
There are two types of SOC 2® audits: Type 1 and Type 2. The difference between them is pretty simple: A Type 1 audit looks at the design of a specific security process or procedure and one point in time, while a Type 2 audit assesses how successful that security process is over time.
A SOC 2® audit will include:
- Optional additional information
- An opinion letter
- Management assertion
- A detailed description of the system or service
- Details of the selected trust services categories
- Tests of controls and the results of testing
- Optional additional information
What industries need SOC 2® certification?
As we mentioned earlier, SOC 2® isn’t legally required, and getting certified isn’t technically mandatory. However, B2B and SaaS businesses should seriously consider becoming certified if they aren’t already because it’s often a requirement in vendor contracts.
Because it’s so widely adopted and acknowledged, many procurement and security departments may require a SOC 2® report before they approve the purchase of your software.
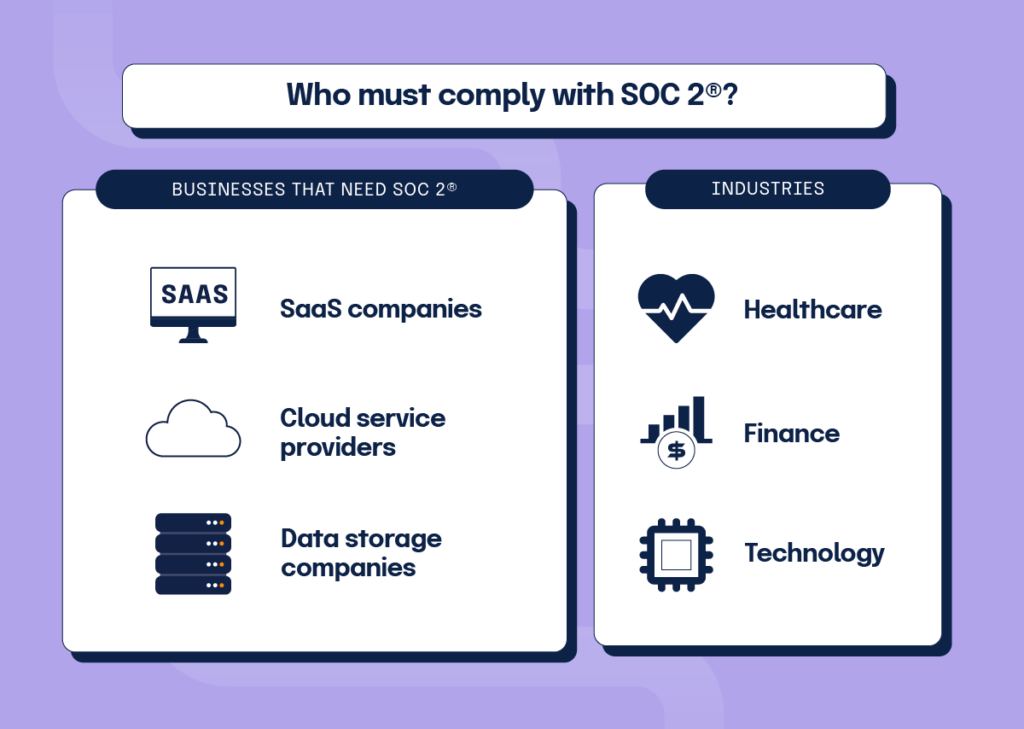
If your business handles any kind of customer data, getting a SOC 2® report will help show your customers and users that you take data security and protection seriously. Healthcare, retail, financial services, SaaS, and cloud storage and computing companies are just some of the businesses that will benefit from SOC 2® compliance certification.
| Further Reading: SOC 2® Audit Checklist What’s New in SOC 2® 2023 Revisions |
How to prepare for your SOC 2® audit
The following 7-step SOC 2® compliance checklist will guide your organization through a successful SOC 2® audit.
- Conduct a comprehensive risk assessment to identify potential security and privacy risks to your systems and data. Prioritize these risks based on severity and develop a remediation plan.
At the very least, include physical risks (missing security locks on data center doors), human risks (poor cybersecurity training), regulatory risks (your incident response plan doesn’t meet expectations), and business continuity risks (you don’t have a list of alternative service providers).
- Establish written policies and procedures that address each identified risk. Also, ensure that all policies and processes are aligned with the goals of at least one of the SOC 2® Trust Services Categories that you’ve included in your audit.
Demonstrate how you communicate and enforce these policies among all relevant personnel. For instance, you should highlight the integration of cybersecurity training into the onboarding process for every new employee.
- Implement user access controls, such as strong passwords, multi-factor authentication, and password reset policies. Highlight all software and IT controls that restrict unauthorized access to sensitive business data.
In addition to preventing unauthorized users, ideally, your access controls must also restrict even your employees from accessing sensitive business information from a personal account or device. If possible, also show how each user can only access the information they need. For example, a regional manager won’t be able to access the personal information of a user who isn’t from the same region.
- Set up monitoring and logging mechanisms to track system activities. Regularly review and analyze logs to detect any unusual behavior.
Detailed logs from various sources, such as security software, servers, firewalls, and networking equipment, can offer clues to investigating a security incident. You can organize this information to draft a quick and effective incident response plan.
- Draft an incident response plan that outlines the steps to be taken during a security incident. Assign tasks to specific roles, provide up-to-date contact information, and train employees on their roles.
Additionally, your incident response plan should include up-to-date contact information for all key employees. An effective plan must also train everyone on their roles, so they know what to do in a crisis.
- Manage vendor risk by assessing the security controls of your vendors, mitigating identified risks, and monitoring them regularly. Consider requesting a SOC 2® audit from your vendors.
- Perform a pre-audit readiness assessment to review the work done and identify any remaining gaps. Consider hiring an external auditor for an objective assessment.
Just like making changes in the design phase is far more cost-effective than changing an actual building, it is far better (read: cheaper) to spend more time on remediation before the formal SOC 2® audit after the external auditor finds shortcomings.
SOC 2® Type 1 vs. Type 2
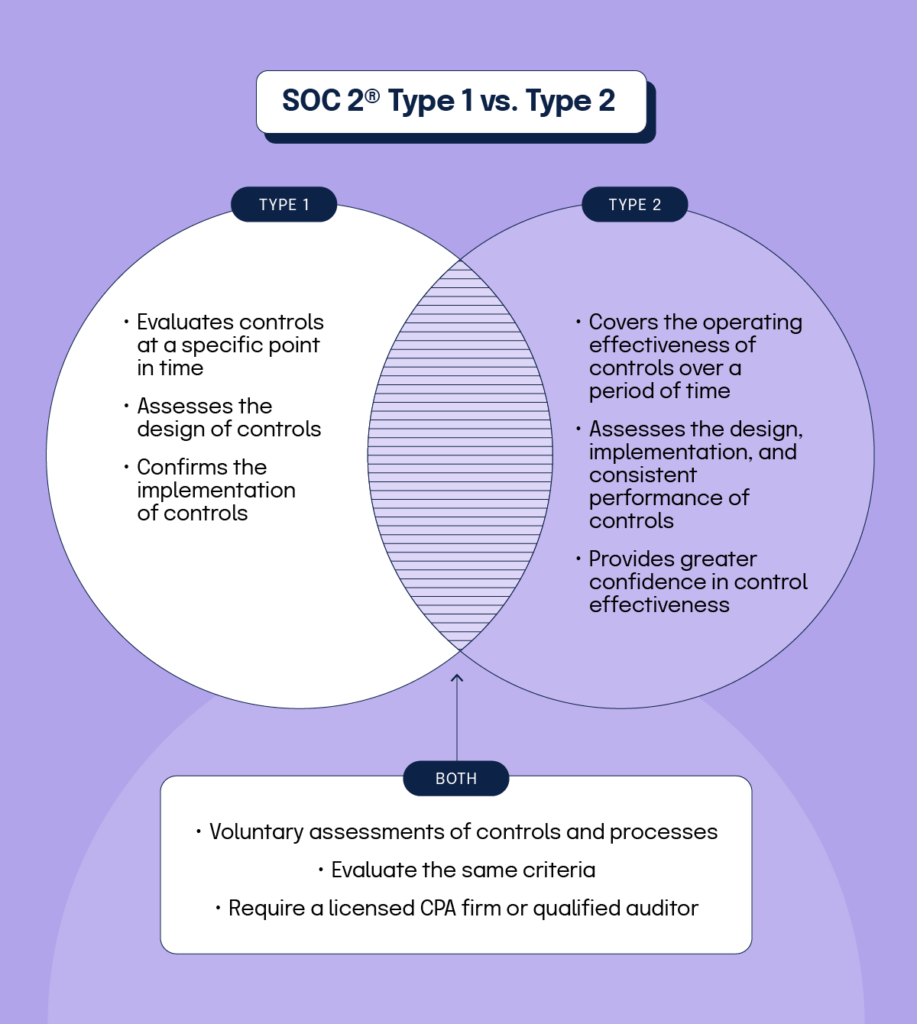
There are two types of SOC 2® reports – a Type 1 and a Type 2.
SOC 2® Type 1
A SOC 2® Type 1 examination evaluates controls at a point in time. This means that the design of the controls are assessed, and implementation is confirmed, but consistent performance is not evaluated in a Type 1 report.
SOC 2® Type 2
A SOC 2® Type 2 examination covers the operating effectiveness of controls over a specific time, such as over a six- to 12-month period. A SOC 2® Type 2 report has a higher bar than a Type 1 because, in addition to evaluating the design and implementation of control processes, it also assesses that the controls were consistently performed throughout the period. This provides customers and business partners with a greater level of confidence in the effectiveness of control processes.
SOC 2® vs. ISO 27001: What are the similarities and differences?
SOC 2® and ISO 27001 are widely recognized data security and compliance standards. An organization will choose either SOC 2® or ISO 27001 (or, at times, both) as proof of having secure business processes that handle sensitive user data. Both standards share significant overlaps but also have a few key differences.
Most clients will be satisfied that your organization is certified with one of these two standards. However, specific industries and clients may prefer one standard over the other in some cases. So make an informed decision after understanding the key differences and similarities between SOC 2® and ISO 27001 standards.
Key similarities between SOC 2® and ISO 27001
SOC 2® and ISO 27001 assess security principles like data security, integrity, availability, and confidentiality.
Both provide independent assurance or validation of an organization’s controls to meet specific data security requirements.
Both frameworks are widely accepted. So, most clients will view either standard as viable proof of your company’s ability to protect data.
Having either a SOC 2® Type 2 report or ISO 27001 certification will improve your brand reputation and help you win new business deals.
Key differences between SOC 2® and ISO 27001
The most significant difference between these frameworks is attestation vs. certification.
The SOC 2® attestation report outlines the controls that meet the applicable Trust Services Criteria based on the company’s principal service commitments and system requirements. A SOC 2® report should not be referenced as a “certification.”
An accredited assessment organization conducts an ISO 27001 certification audit to investigate whether an organization’s ISMS conforms to the “standard requirements” of the ISO 27001 framework.
Another significant difference is the time frame considered during the examination. The ISO 27001 certification is a forward-looking three-year cycle, while the SOC 2® examination covers either a point in time (in the case of a Type 1 report) or a period that occurred in the past (in the case of a Type 2 report).
Also, the ISO 27001 certification doesn’t provide details of an organization’s environment or related controls. However, the SOC 2® report provides details regarding the controls and the environment. This additional information may be useful to customers from regulated industries.
For SOC 2®, an organization new to SOC 2® would start with a Type 1 assessment and then move on to annual Type 2 assessments. For ISO 27001, an organization would go through an initial certification audit—consisting of two stages—followed by surveillance audits in years 2 and 3. After three years, the organization must go through a full recertification audit.
| Further Reading: Breaking Down SOC 2® and ISO 27001: Is One Really Better? |
When should your organization implement SOC 2® compliance?
Start early
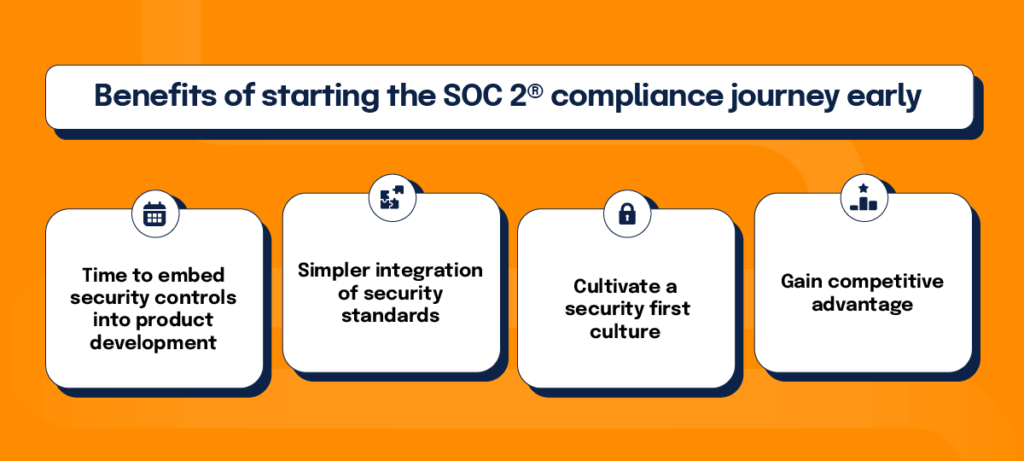
If you know you’ll be selling technology services/software to enterprises and storing and/or accessing sensitive customer data, it’s a good idea to work on becoming compliant early in your company’s journey.
Our company’s founder and CEO — Craig Unger — believes that a good time to kick the process into gear is when your team has already developed the majority of features for your core service and you’re close to shipping production-ready software. When you start the SOC 2® compliance journey, you want to make sure you have already established some key processes. You need to have sufficient IT security processes and documentation of those processes for an auditor to react to, so they can provide insights on the gaps.
Starting early gives you the opportunity to embed security controls into your product as it’s being developed, which is a far easier endeavor than completely re-architecting the system later to meet certain security standards. When you start early, you are able to integrate processes and controls into your team’s culture from the beginning. This can be a source of competitive advantage that industry incumbents cannot replicate.
Six questions to ask to determine when it’s the right time
To figure out when it’s the right time to invest in SOC 2®, you’ll need to consider the following six factors
If you’re looking to sell software or services to B2B customers, you’ll quickly find at least some of your customers demanding to review your latest SOC 2® report before they’re willing to be in business with you.
You need to have established software development processes before you schedule an audit. Security controls (e.g. access controls, change management, logging and monitoring) should be built into your software development lifecycle. If you haven’t developed processes to govern how you develop software at your organization, there isn’t going to be enough content for an auditor to audit.
Auditors will want documentation of your key company-wide processes during an audit. Thus, it is essential to implement certain company-wide processes before engaging with an auditor. Documents and policies you’ll need to have include:
You need someone who has the time and sufficient expertise to drive the SOC 2® readiness process forward. A project leader requires an adequate understanding of your business and your technology stack and be able to figure out what controls the organization needs to create to meet the program’s requirements. Typically, someone with a deep product, engineering and security background should be the one to lead this process. If you don’t have someone internally to lead the process, you may consider outsourcing these duties to a virtual, fractional compliance officer (professional service firms with expertise in delivering compliance-as-service).
You’ll need to invest internal resources in program design and program implementation and reserve some budget towards the SOC 2® audit itself.
Get your free personalized demo today.
| Further SOC 2 ® Implementation Resources: Conducting an Internal SOC 2® Type 1 Audit Using Hyperproof Conducting an Internal SOC 2® Type 2 Audit Using Hyperproof |
How to choose an auditor
The most important thing to understand when choosing a SOC 2® auditor to work with is that only CPA firms can perform a SOC 2® audit. CPA firms might employ non-CPAs with expertise in areas such as data security to assist with these audits, but the final audit has to be provided and issued by a CPA.
After you’ve gotten your SOC 2® report, you may also want to be certified in other frameworks (e.g. ISO 27001 or HIPAA). You might consider choosing a firm that specializes in several of the compliance frameworks that you’re pursuing compliance with or that has experience working with the industry you’re in. When you engage a firm that has experience in all of the frameworks you’re working towards, you can complete your audits faster and at a lower cost.
Preparing for an audit
Once you’ve decided on the scope of your SOC 2® audit and selected an auditing firm, there are a few other things you can do in advance of your audit to get ready.

Gather documentation
First, gather all of the compliance documentation that you have in one place. Depending on which of the five Trust Service Categories you’re auditing for, you’ll need to present different types of documentation and compliance evidence. If you have compliance management software, that will be a huge help here. A software platform like Hyperproof allows you to store, tag, and call up documentation quickly and alerts you when documentation needs to be updated.
Complete audit readiness assessment
Once all of you’ve collected all your documentation, you should work with your auditor to complete an audit readiness assessment, which can help you prepare for an audit months before it happens. with the help of your auditor. It can be beneficial to be important to take advantage of this pre-audit opportunity because it lowers the chances that your auditor will find big gaps in your security or compliance programs that force them to fail you.
An audit readiness assessment also gives you a tool to rally your organization and educate stakeholders about the importance of establishing data compliance and IT security measures. When you have to “get your house in order” in time for an auditor’s visit, it can impress upon your stakeholders, such as executives and engineering managers, a sense of urgency to jump start your compliance program.
Meet with your auditor
Finally, meeting with your auditor prior to the actual audit is beneficial because your auditor can answer questions, address concerns, and give you an idea of whether a specific control you’ve implemented is up to snuff.
Preparing for an audit is time well spent. It smooths the audit process and decreases the chances of a repeat due to a failed audit.
What to expect during the security audit
An independent Certified Public Accountant (CPA) should conduct a SOC 2® audit. For each applicable Trust Services Category, the auditor will evaluate the efficacy of your controls by reviewing the evidence you submit.
During the assessment, your auditor will ask you to submit all types of documents electronically, such as organizational charts, asset inventories, onboarding and offboarding processes, and change management processes. Your auditor may also interview key stakeholders within your organization (e.g., security engineers, and IT staff) to better understand your internal processes and operating procedures.
The audit itself can take anywhere between a few days to a couple of weeks to complete, but thorough preparation may require several months.
How to comply with SOC 2® on a continual basis
Most SOC 2® reports cover a 12-month period, but some companies choose to complete these audits every six months. After the initial effort to become SOC 2® compliant is over, ideally you will only have to complete maintenance activities and not have to build any systems or processes from scratch.
Like almost any other compliance framework, maintaining SOC 2® compliance is easiest when automating. The more manual processes, the more chances there are for missed compliance activities, out-of-date evidence, and procrastinated responsibilities.
Compliance management software that tracks your program is invaluable here. A good one will not only help you prepare for an audit, but also ensure that you are alerted when some part of your process is falling out of compliance, whether it’s due to a change in regulations or someone not completing a procedure.
SOC 2®: Frequently Asked Questions
Hyperproof partners with professional service firms with proven track records and deep expertise in helping organizations get SOC 2® ready. Our partners help customers design their compliance programs, build them out, and conduct readiness assessments to ensure no surprises when the audit occurs. If you need a referral, we’d love to talk. Get your demo today.
Ready to see
Hyperproof in action?