Compliance Programs 101: Creating a Quality and Consistent Program
As a leader within a growing company, you know that compliance is something you cannot avoid as your business expands. That said, establishing your organization’s corporate compliance program can feel overwhelming at the start. You’re likely to confront the following questions:
In this article, when we talk about a compliance program, we’re talking about a specific set of internal policies and procedures a firm develops to comply with a particular security/privacy standards (SOC 2®, ISO 27001) or regulation (GDPR). Industry standards often have overlapping requirements, so an organization may develop one policy or a set of policies that satisfies multiple requirements. It’s important to note that an audit is always executed on a specific industry standard, so you will need to get to know the requirements of each program and budget for each audit.
Keep in mind that your organization can be compliant with certain industry standards and regulatory requirements (like HIPAA) without having a formal program. However, you’ll eventually be required to start a formal compliance program because your customers, partners, and investors need to see more formal or “official” evidence of compliance to feel comfortable working with you.
What is a compliance program?

A compliance program is a set of internal policies and procedures within a company to comply with laws, rules, and regulations or to enforce the business’s standards for good conduct. Where requirements of a regulatory authority do not apply, a compliance program within an organization addresses the conduct of employees to abide by internal policies (e.g. spending corporate funds or keeping confidentiality) and, more importantly, to maintain the firm’s reputation among its customers, suppliers, employees, and even the community where the business is located.
A company can have (indeed, should have) some sort of compliance program, even if your business has no particular regulatory obligations pushing you to do so. For example, you might want a compliance program simply to enforce your own expectations for spending corporate funds or protecting confidential information. More importantly, a compliance program also tells customers, suppliers, employees, and other stakeholders that your business is one that can be trusted to do what it promises.
Factors that will impact your timeline
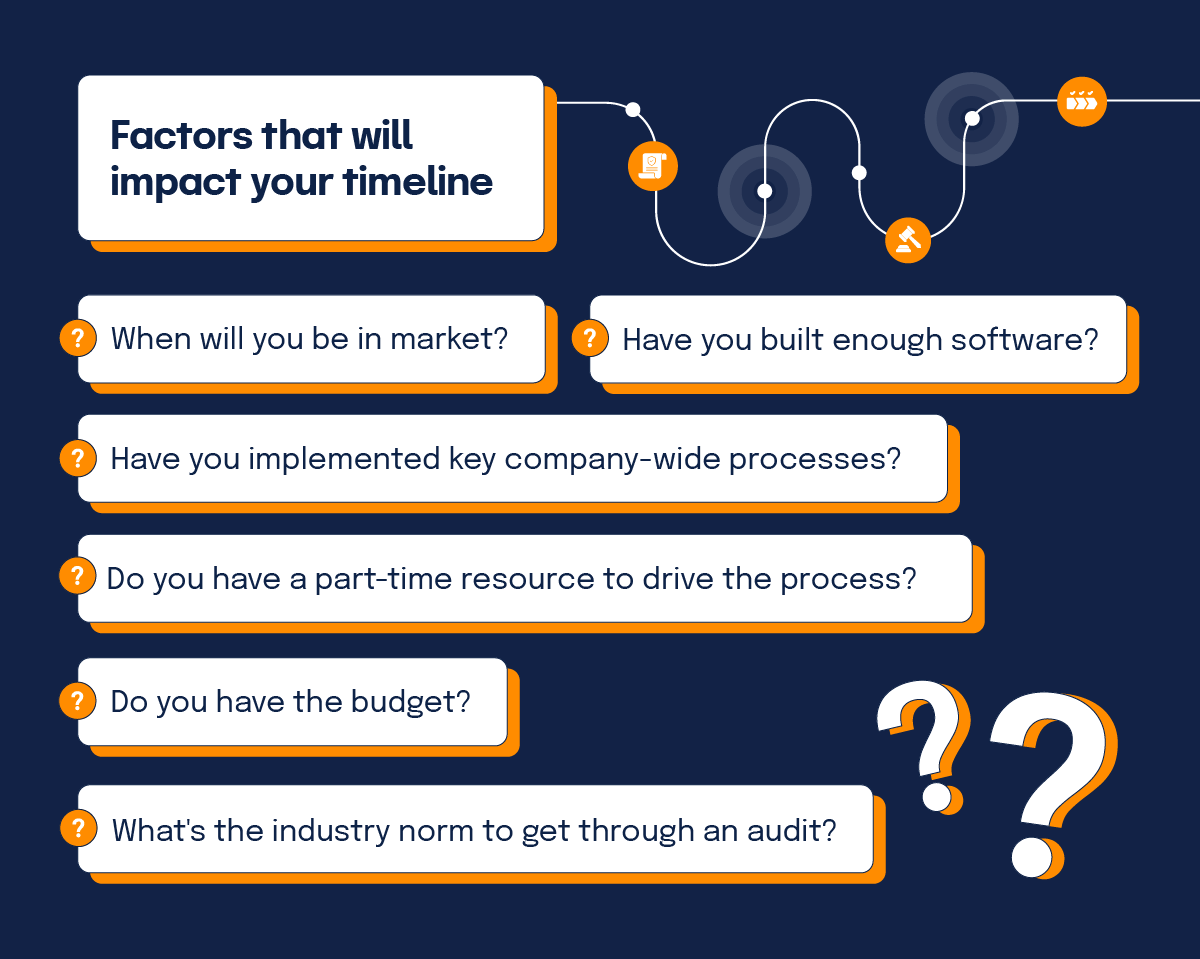
When is the right time to start a formal compliance program and work towards passing an audit? Well, that depends on your particular circumstances. Here are the key factors to consider.
When will you be in-market?
When are you launching your product? What do your customers care about? Are your customers large enterprises or in highly regulated industries?
You’ll need a compliance program — and to pass assessments (e.g. SOC 2®, ISO 27001) — when your customers, partners, and/or investors ask for it. If you’re selling software or services to B2B enterprise customers, it is just a matter of time before a customer will demand proof of compliance (like a SOC 2 report) before they’re willing to do business with you.
Have you built enough software?
If you want to get certified against any security standard, you must have established software development processes before you schedule a compliance audit. Security controls — who has access to data — should be built into your software development lifecycle. If you haven’t developed the processes to govern how you develop software at your organization, you won’t have enough content for an auditor to audit.
Have you implemented key company-wide processes?
One critical part of your compliance program is to ensure that employees abide by internal policies and your organization’s code of conduct. Auditors will want documentation of your key company-wide processes during an audit, which means you need to have certain company-wide processes in place before engaging with an auditor.
Documents and policies you’ll need to have include:
Do you have a part-time resource to drive the process?
You need someone who has the time and sufficient expertise to drive the compliance program forward and keep everyone on track. Managing compliance doesn’t need to be someone’s full-time job, but at a minimum, you need someone who can devote a good portion of his or her time to managing the process. Additionally, the project leader needs a sufficient understanding of your business and your technology stack, and what controls the organization needs to create to meet the requirements of the program. Typically a CTO, VP of product, VP of engineering, or someone else who has a deep security background should be the one to lead this process, often in close coordination with someone from the legal department.
Do you have the budget?
You’ll need to invest internal resources in program design and program implementation, and you’ll need to allocate time to work with your auditors. You may need to invest money in hiring consultants to help you design controls for your environment, and you will need to pay auditors to audit your program. For an early-stage startup, you may find that your compliance spending is one of the largest spending categories for your business.
What’s the industry norm to get through an audit?
There are industry norms for how long it takes to get through certain types of audits. For example, SOC 2® compliance is something many tech companies undertake to sell to enterprise customers. It may take about four months to get through the first SOC 2® audit (a Type I audit) followed by 6-12 months for the more in-depth SOC 2 Type II audit.
The difference between a SOC 2® Type 1 report and a SOC 2® Type 2 report is pretty simple: A SOC 2® Type 1 audit looks at the design of a specific security process or procedure and one point in time, while a SOC 2® Type 2 audit assesses how successful that security process is over time.
Sample SOC 2® timeline
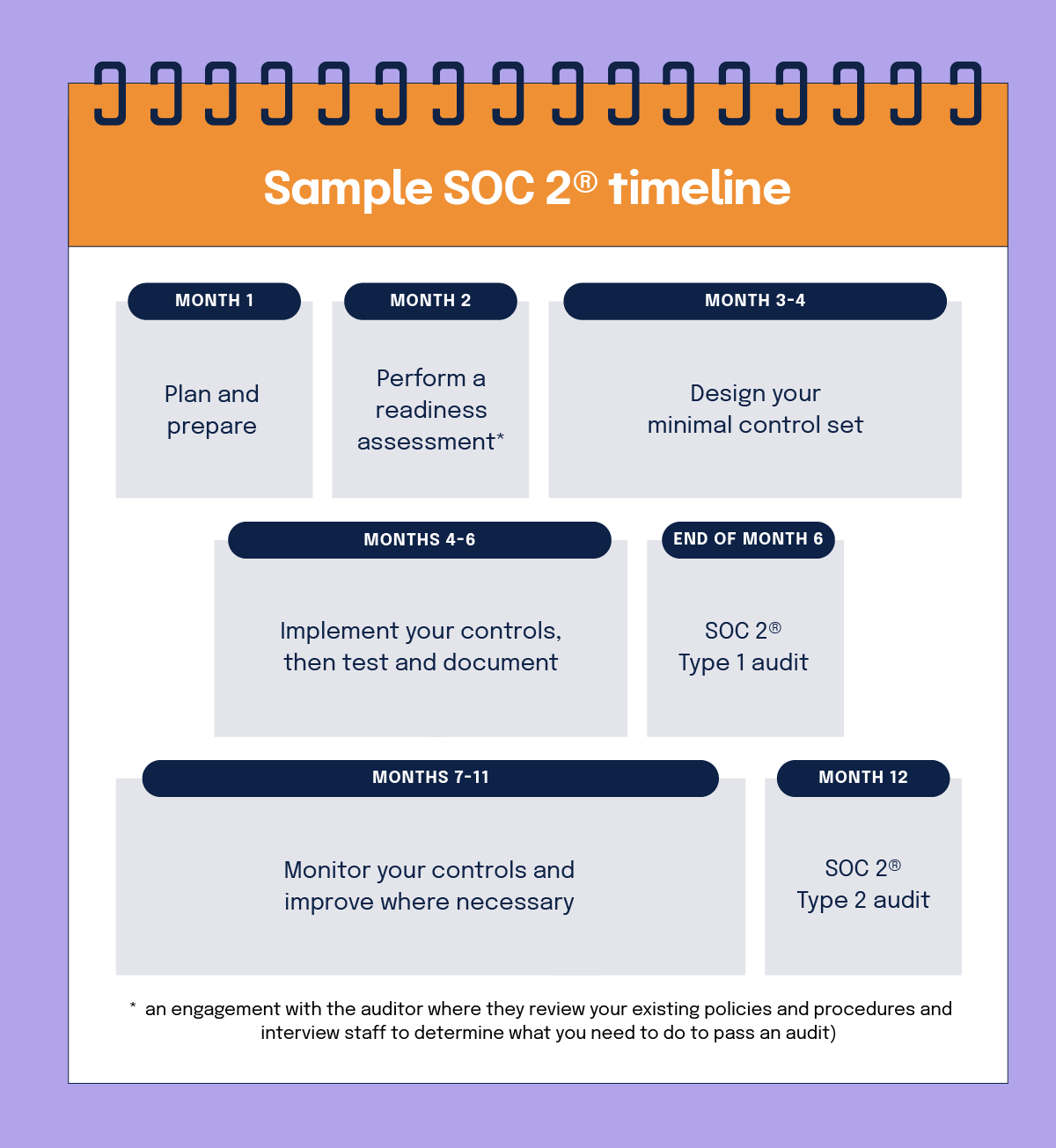
- Month 1: Plan and prepare
- Month 2: Perform a readiness assessment (an engagement with the auditor where they review your existing policies and procedures and interview staff to determine what you need to do to pass an audit)
- Months 3-4: Design your minimal control set
- Months 4-6: Implement your controls, then test and document
- End of month 6: SOC 2® Type 1 audit
- Months 7-11: Monitor your controls and improve where necessary
- Month 12: SOC 2® Type 2 audit
Once you have determined when to start, it’s time to figure out which programs you want to pursue. To do this, you’ll want to consider your customer base and your product development strategy.
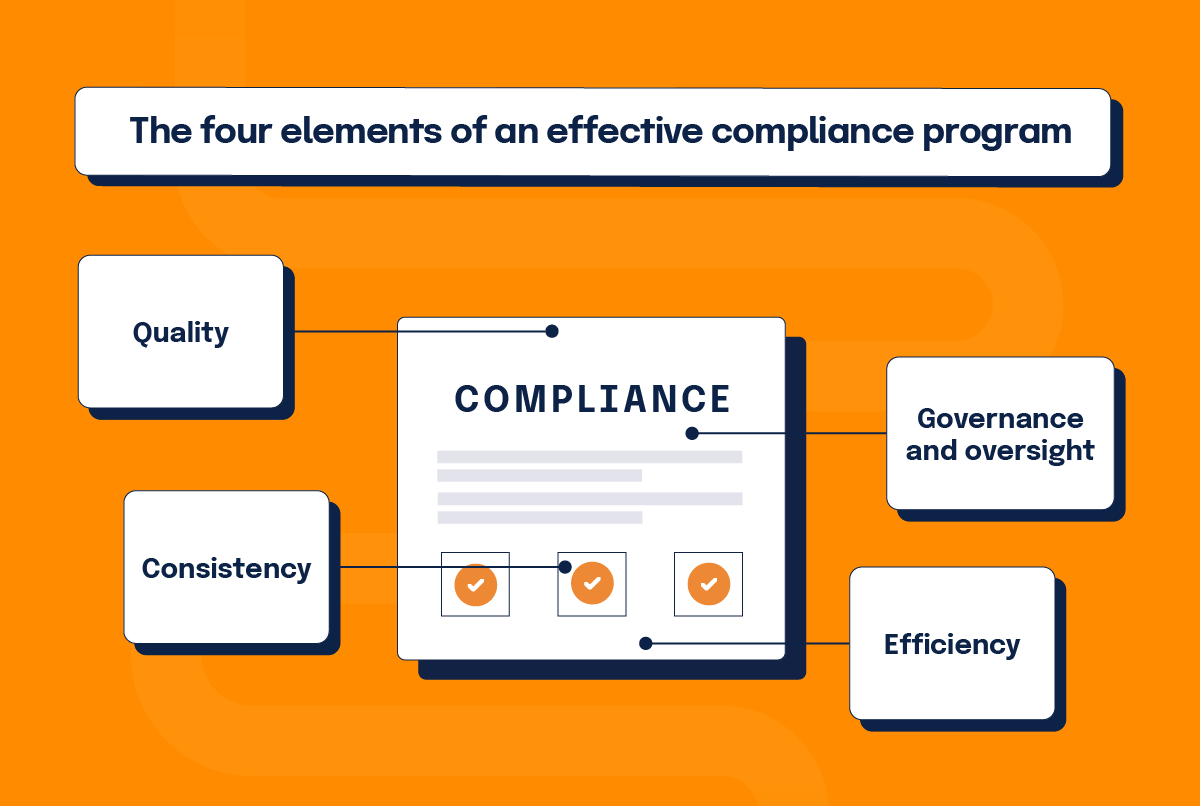
The four elements of an effective compliance program
An effective compliance program supports an organization’s ability to operate with integrity, consistency, and quality and to maintain trust and credibility with organizational stakeholders, including customers, partners, vendors, employees, and investors. Your compliance program is also an important component of an effective risk management program.
1. Quality
An effective compliance program should align with a broader risk management strategy. Risk assessments should be performed at least annually, and more frequently for higher risk areas.
The ultimate goal of an effective risk management strategy is to maintain a risk environment that stays within an acceptable risk tolerance level for the organization. To accomplish this, an organization must identify its risks, define risk tolerances (risk levels that are acceptable) and then design controls in a manner that effectively addresses the risks.
Below, are some questions to consider in evaluating the quality of your compliance program:
By using innovative compliance operations software like Hyperproof, it’s easy to ensure your control environment effectively aligns with your overall risk management strategy. As new risks are identified, Hyperproof provides visibility to see if existing controls are already in place to address the risks or if new controls are needed.
Hyperproof also enables you to see the gaps between your existing control set and what would be needed to adopt leading cybersecurity frameworks like NIST SP 800 series or the ISO 27000 series.
2. Consistency
The design of the control impacts its effectiveness. Additionally, consistency in performing the control process is an important factor in having an effective compliance program. In this context, consistency means that your controls are operating at the specific time interval and in the same manner as they were designed to. To ensure that your controls are operating consistently, you’ll need to have sufficient oversight and visibility into the performance of control processes.
For instance, deploying patches is an important component of vulnerability management. If patches are not deployed consistently, and at the time that they become available, your systems may be left exposed to vulnerabilities. As such, it is important to have visibility into control processes that were not performed promptly so that you can quickly resolve issues. This is particularly important for high-risk areas such as vulnerability management.
Continuous compliance helps you manage risk more effectively. With continuous compliance, control processes are consistently performed, and evidence from the control processes is evaluated and acted upon accordingly. If you are evaluating control processes on a continuous basis, you have an opportunity to refine your risk management strategies in real time.
For example, if you are using a SIEM solution that does not have both logging and monitoring alerts turned on, that could potentially prevent notifications of attack indicators. The need for notifications and alerts reduces the ability to make timely adjustments to network controls. This scenario could have been prevented with continuous compliance. Specifically, continuous compliance would have discovered, in a timely manner, that logging and monitoring alerts were not turned on.
Many organizations wait to collect and evaluate evidence until right before they need to submit that evidence to their auditor or security assessor. This is unwise; by delaying evidence collection and evaluation, organizations miss the opportunity to adjust and adapt to their risk environment. If evidence is only collected and evaluated immediately before an audit or assessment, the control process becomes a lagging indicator with little room for adjustment.
Technology can make a big impact when adopting continuous compliance. For instance, you can use a compliance operations solution such as Hyperproof to keep all your evidence organized (for example, linked to the right control/requirement) and use automated reminders to alert control operators to review controls on a regular basis and submit evidence on time.
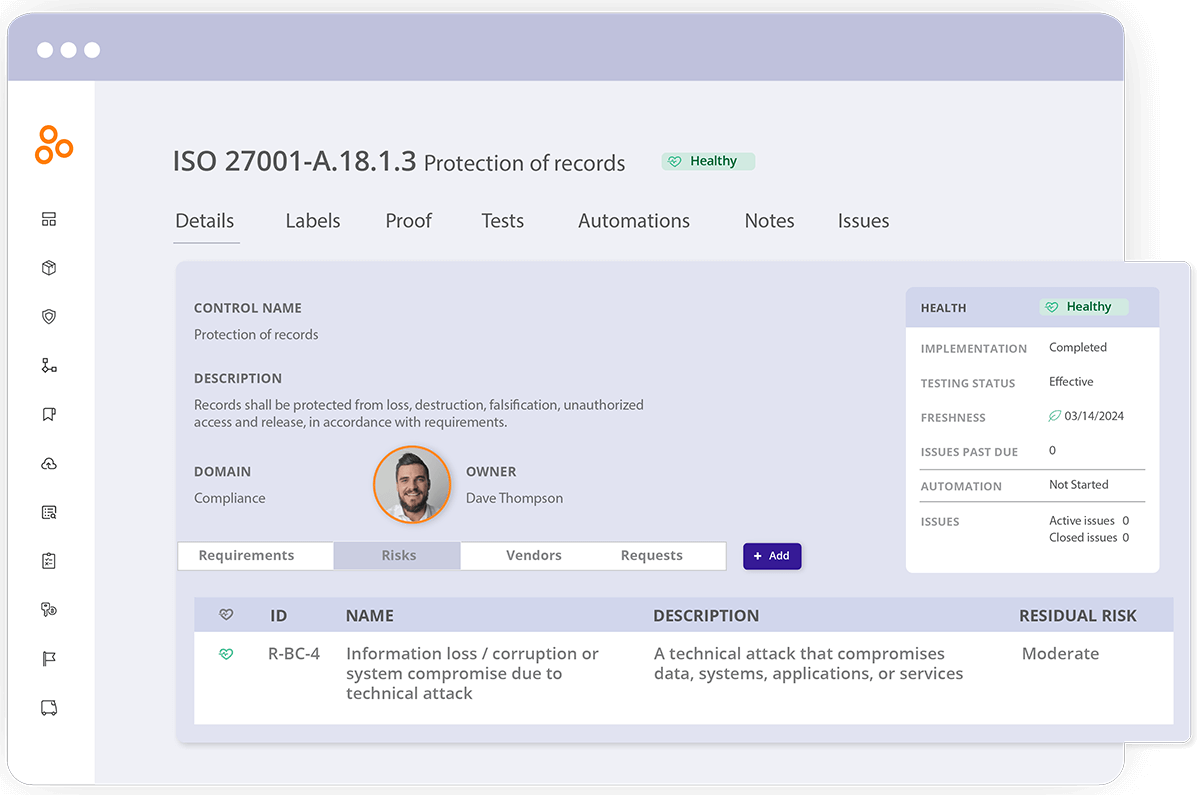
Additionally, Hyperproof has a feature called Freshness. You can set a Freshness policy to remind yourself and your team to review controls on a cadence so that all controls are appropriately evaluated throughout the year. This helps ensure that no one will forget any compliance tasks, which ultimately makes your entire organization more secure and resilient.
Compliance operations software like Hyperproof can also eliminate duplicative work (say, having to collect the same piece of evidence five times to meet five different compliance frameworks) by helping users identify common controls and common evidence across compliance frameworks.
3. Governance and oversight
Governance and oversight are key components of an effective compliance program. At the highest level, senior risk leaders need the right information to effectively monitor the effectiveness of the compliance program and make adjustments as needed. Adjustments may include incorporating new controls to address emerging risks, redesigning weak control processes to make them stronger, or developing new training to improve security awareness among employees.
At a tactical level, compliance managers need another set of information to understand how prepared they are for upcoming audits or assessments, quickly see which controls need attention, and assure that control processes are performed correctly and on time. They should also have visibility into the issues that need immediate attention or escalation.
Getting sufficient visibility into the effectiveness of a compliance program can be a difficult challenge for many organizations. This is especially an issue for organizations that manage their compliance efforts through a variety of different tools, such as elaborate spreadsheets, email inboxes, and file storage systems like Box, Dropbox, or OneDrive.
When organizations start to manage all of their compliance projects in one single place, on the other hand, gathering the right metrics for decision-making becomes much easier.
For instance, Hyperproof gives organizations a central location where all of their compliance requirements, controls, and proof can be stored and managed; compliance managers and external auditors can see everything in one streamlined system. It allows compliance managers to quickly answer questions like:
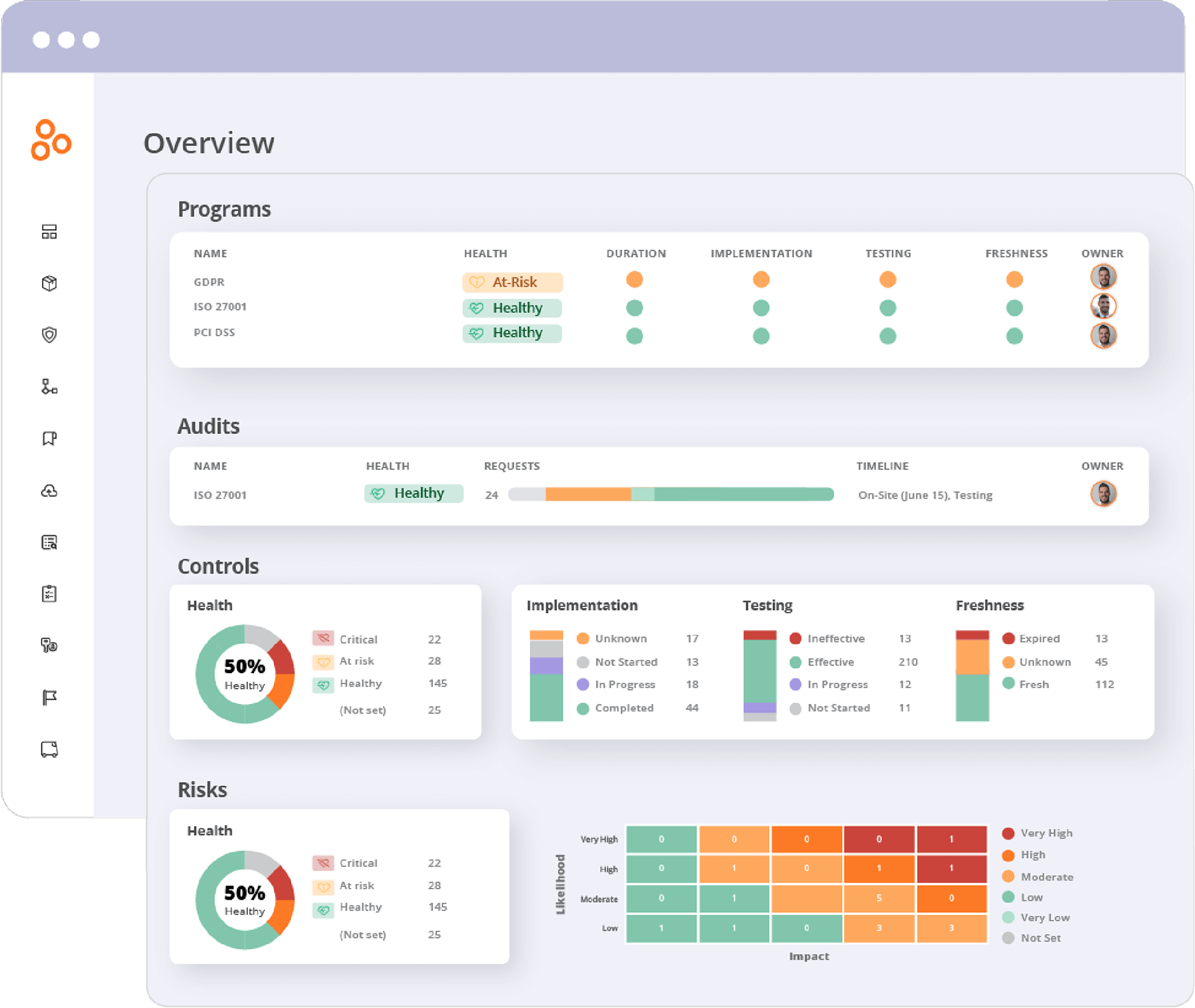
Hyperproof also helps senior risk leaders understand how well their current compliance program compares with several best-in-class cybersecurity and data privacy frameworks.
4. Efficiency
Efficiency has to do with how well an organization is managing its resources, including time, employees, and budget. Being efficient means that your team is able to achieve quality, consistency and effective oversight with an optimal amount of resources. With limited resources, it is particularly important to focus your compliance efforts on the more critical areas.
Making compliance activities more efficient is key to reducing the cost of compliance, which always seems to be going up due to factors such as the rise of data privacy regulations, the growing awareness of third-party risks, a rise in vendor-to-vendor audits, and the shortage of cybersecurity talent.
For operational efficiency, technology will be incredibly important. In fact, Hyperproof was built to help organizations become far more efficient in compliance management. Hyperproof serves as a single source of truth for all of your compliance activities and can reduce the administrative work around collecting evidence and managing tasks (such as updating controls) by half.
Hyperproof comes with a set of features that enable greater efficiency, including:
- Control Crosswalks that help users identify the overlapping requirements and controls between various compliance frameworks
- Integrations with file storage systems where evidence is stored and productivity tools
- Collaboration capabilities among compliance managers, control operators, senior leaders, and external auditors
- Automated reminders to review controls and evidence
- Smart folders and labels to efficiently link a batch of evidence to controls
- Automated task creation that reduces the time spent on creating tasks for control owners
Related content: The Complete Guide to Continuous Compliance
Building a compliance program checklist
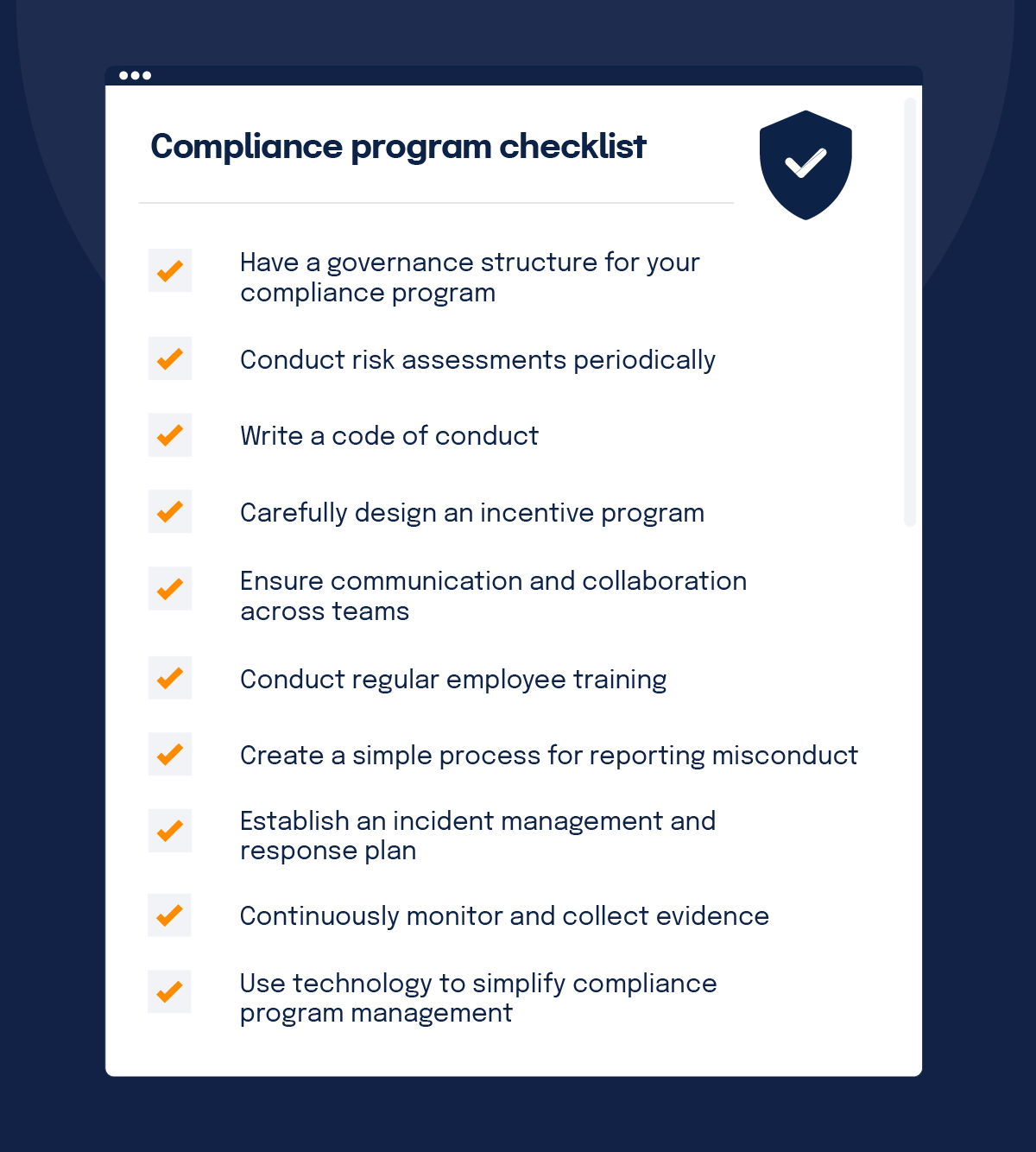
A compliance program is only effective when it shapes the way leaders and employees make decisions, large and small. The ultimate goal of doing all this work is to foster a culture of compliance within your organization. Here’s what a culture of compliance means:
- Each individual understands their role in the company’s compliance program and fulfills their individual responsibilities.
- Software and IT systems that handle data are designed to comply with the laws and industry standards governing data privacy, security, availability, and confidentiality. In other words, compliance is baked into your products and business processes.
Here are 10 things you and your leadership team can do to ensure that your compliance program truly influences behaviors and effectively protects your business.
1. Have a governance structure for your compliance program
When you create a compliance program, you’ll want to answer governance questions first. You want to have clear roles and responsibilities and regular and helpful communication between the key stakeholders with compliance responsibilities. Determine the following:
To build a culture of compliance, you need a dedicated leader for your program. Because compliance issues have a material impact on a business, the compliance officer needs to have a direct line to the CEO and a company’s board, adequate resources to do their job properly, and respect from the rest of the organization for what compliance does.
2. Conduct risk assessments periodically
Compliance programs must be customized to the needs and challenges facing each company and be comprehensive enough to deal with all of the risks the company has identified. An effective risk assessment should begin with a detailed picture of the compliance landscape your company inhabits. The two questions to answer are:
- Where are you doing business?
- What regulations cover businesses like yours?
An effective risk assessment must also include a clear picture of how your organization operates. In other words, you need to know the “who, what, where, when, and how” of the day-to-day operations happening on the ground in your company.
It’s important to note that a risk assessment shouldn’t be a one-off event. Events such as the acquisition of new companies, movement into new geographical or sector markets, corporate reorganization, and engagement with new customers and regulators will raise different types of compliance risks. Similarly, changes in regulations and how enforcement authorities interpret these risks can create new compliance risks. None of those new risks should be allowed to linger unaddressed. Implementing a deliberate, recurring process to periodically update your risk assessment is essential.
3. A code of conduct
A code of conduct reflects an organization’s daily operations, vision, mission, core values, and overall company culture. This document should be readily available to employees and placed on the homepage of the company’s intranet or wherever it will be easily accessible for every employee. Make sure people always know where to find the code of conduct and understand its importance.
If you need some help writing a code of conduct for your company or want some examples of what great code of conduct documents look like, check out these 18 examples.
4. Carefully designed incentive program
When properly used, incentives motivate workers to achieve organizational goals. When improperly used, however, incentives can encourage bad behaviors (cheating to meet a sales quota, for example) and pose a compliance risk. When doling out rewards to employees, consider not only the results they achieved but also how they achieved those results. Before you roll out an incentive program, review it from a compliance perspective, consider potential risks, and develop mitigation measures.
5. Communication among teams
Many different groups within the company are responsible for various aspects of compliance. For example, HR is responsible for sexual harassment claims, IT security handles data privacy and security, and marketing must adhere to laws governing user data collection, email communication, and advertising. The compliance team acts as the quarterback of the company’s compliance efforts.
One important thing for compliance to understand is whether all areas of company risk are sufficiently covered — and if not, how to address the risks in the compliance program and determine which group is responsible.
The compliance function also needs to ensure coordination and collaboration among the groups and make sure they address issues and share best practices. A compliance officer needs to create the right process so that different compliance issues are routed to the right group and there’s no duplication of effort or groups operating cross-functionally.
6. Regular employee training
One hallmark of a well-designed compliance program is appropriately tailored training and communication. Everyone at the company, including executives, needs to know what is in your code of conduct. In addition to knowing the rules they’re expected to follow, employees also need to know who they can contact for guidance if they have questions about compliance and how they can report violations and concerns.
7. A simple process for reporting misconduct
To foster a culture of compliance, all employees need to understand when they need to report something and how to do so. The code of conduct should detail all the ways employees can raise issues, such as through a toll-free hotline, a monitored email alias, a meeting with their manager or some other executive, or however else you want issues reported in your company. It is much better for your company to empower employees to raise issues early, while there’s time to prevent bigger problems from materializing.
If you want people to report questionable behavior or misconduct, you must put in place and enforce a no-retaliation policy. Employees must believe they won’t face punishment for bringing forth an issue in good faith. There should also be a general policy to ensure confidentiality for both the person bringing the complaint and any employees implicated by the complaint.
8. An established incident management and response process
Being prepared to handle incidents of non-compliance is as important as putting in place controls to mitigate compliance risks. Poor incident management can dramatically increase the costs a brand must pay for non-compliance, and it is often what gets brands into public headlines. Whether you are dealing with someone who has violated a standard or a system issue that represents a compliance violation, having the steps laid out and understood in advance is key.
9. Ongoing monitoring and evidence collection
To inculcate a culture of compliance, you need to continuously document your compliance program and collect evidence to confirm that your controls are working as intended. Along with potentially protecting your company from being fined in the event of an incident such as a data breach, having evidence of your compliance processes on hand can give you an opportunity to find your compliance blind spots. If your compliance evidence doesn’t exist, you’re likely not meeting standards.
If you establish a habit of collecting evidence on a regular basis, it makes external audits smoother and less stressful because you won’t need to scramble to find the evidence you need just days before the auditor shows up at your office.
Going forward, we can expect to see regulations increase in areas such as user privacy or cybersecurity at the local, state, federal, and international levels. To reduce compliance risks, you’ll want to dedicate resources to help your organization stay current with new laws that may impact your business so that you can update your internal control environment to sufficiently mitigate risks.
10. Technology that simplifies compliance program management
You can manage your compliance program through spreadsheets, emails, and file storage systems like Dropbox, G-Drive or Box, but if your compliance data is all over the place, getting a holistic picture of your compliance program will be nearly impossible. If you can’t easily see what policies, controls, and evidence already exist and what’s missing, you won’t be able to get a true handle on your risks.
Using the right technology makes it that much easier to develop and manage your compliance program. When you use a compliance operations system such as Hyperproof, you can quickly map your controls to a new compliance framework, streamline the management of evidence, automate tasks and easily collaborate with various stakeholders in your ecosystem (employees, vendors, external auditors, and the like) to get work done and maintain an acceptable risk level.
Focus on four key elements for a well-functioning program
With compliance, it’s important to understand what it actually takes to become compliant and maintain that position. Organizations should focus on four key elements: quality, consistency, effective oversight, and efficiency. Deliberate attention to each area will ultimately lead to a well-functioning compliance program.
Additionally, effective risk management is about being active instead of reactive. That includes quickly responding to the alerts indicating weaknesses of critical systems and consistently evaluating or updating the control processes established for the mitigation of potential security incidents.
When compliance costs are rising quickly for organizations of all industries, sizes, and types, prioritizing the right areas — with a solution that is agile, intuitive, and cost-effective — becomes essential.
Ready to transform your compliance journey? Request a demo of our innovative solution tailored for optimizing compliance programs.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?