How SaaS Providers Should Parse the Biden Cybersecurity Executive Order
Government contractors, and specific providers of software-as-a-service (SaaS), received quite the message in May when the Biden Administration issued an executive order calling for enhanced cybersecurity across the federal government and its supply chain.
The order arrived at the height of concern over the ransomware attack that shut down Colonial Pipelines, but security and compliance officers should be clear that this order was a long time in the making — and its implications will be long-lasting, too. SaaS providers should start thinking now about how to position themselves to comply with the heightened standards sure to come.
The order had three principal directives:
- Mandatory reporting of cybersecurity incidents to federal agencies;
- Better cybersecurity within the federal government by using multi-factor authentication and zero-trust architecture more widely;
- More oversight of the software supply chain, especially of third-party software code you might use in your own products.
Despite those new requirements, the executive order also stressed that the Biden Administration does want to continue using cloud-based providers of IT services; it simply wants stronger, more uniform security across the federal government as agencies continue to embrace cloud-based services.
In other words, government contractors — and particularly, contractors who provide software as a service — are soon going to face numerous new compliance burdens. You need to understand what’s coming and plan accordingly. (It’s also a safe bet to assume that other large, corporate organizations will watch this closely and implement similar demands of their own in the future.)
What specific new compliance burdens are likely?
The executive order directs several government agencies to propose revisions to federal contracting rules; those proposed revisions are where we’ll see specific new compliance requirements that SaaS providers and other government contractors will need to meet. That said, Biden’s order still lists numerous policy goals those revisions will need to achieve. They are:
Mandatory disclosure of attacks. Contractors that suffer a cybersecurity attack will need to report that attack to their government agency customer, usually within 72 hours of discovering it.
Enhanced technical capabilities for better monitoring, detection, and preservation of attack evidence. Contractors will then be expected to share that information with regulators and to cooperate in any follow-on investigations — potentially including criminal investigations run by law enforcement.
An embrace of zero-trust architecture and other strong cybersecurity measures. Specifically, the executive order tells the FedRAMP program to evaluate the security of SaaS providers should incorporate zero-trust architecture; and government agencies should use multi-factor authentication more broadly.
More scrutiny of the software supply chain. SaaS providers and other government contractors will need to attest to the integrity of any third-party software code used in their products and services and impose policies, procedures, and controls to govern their software development processes.
See how to defend your organization against software supply chain attacks
Those goals are supposed to be incorporated into the Federal Acquisition Rule (for most government contractors) and the Defense Federal Acquisition Rule Supplement (DFARs, for defense contractors) within the next several months. Technical guidance around zero-trust architecture and multi-factor authentication is supposed to come from the National Institute of Standards and Technology, which has churned out many cybersecurity standards over the years.
The state of government cybersecurity today

As luck would have it, the Government Accountability Office published a report at the end of May reviewing how well federal agencies are coping with cybersecurity risks in the software supply chain.
The news was not good. The GAO assessed 23 civilian government agencies against seven “foundational practices” for supply chain risk management (SCRM) that had been developed by NIST. Among all 23 agencies studied, none had fully implemented all seven practices, and 14 agencies had not implemented any of the practices at all.
NIST’s seven foundational practices are these:
- Establish executive oversight of IT activities, including assigning responsibility for leading agency-wide SCRM activities;
- Develop an agency-wide strategy for SCRM, to provide the context in which risk-based decisions will be made;
- Establish an approach to identify and document agency IT supply chains;
- Establish a process to conduct agency-wide assessments of cybersecurity supply chain risks;
- Establish a process to conduct an SCRM review of potential suppliers, including reviews of the processes suppliers themselves use to design, develop, test, implement, verify, deliver, and support IT products and services;
- Develop SCRM requirements for suppliers to assure that suppliers adequately address the risks associated with IT products and services; and
- Develop organizational procedures to detect counterfeit and compromised IT products prior to their deployment.
So which of those processes were most widely adopted? Which ones weren’t used at all? Figure 1 below gives us a sense of the shortcomings here.
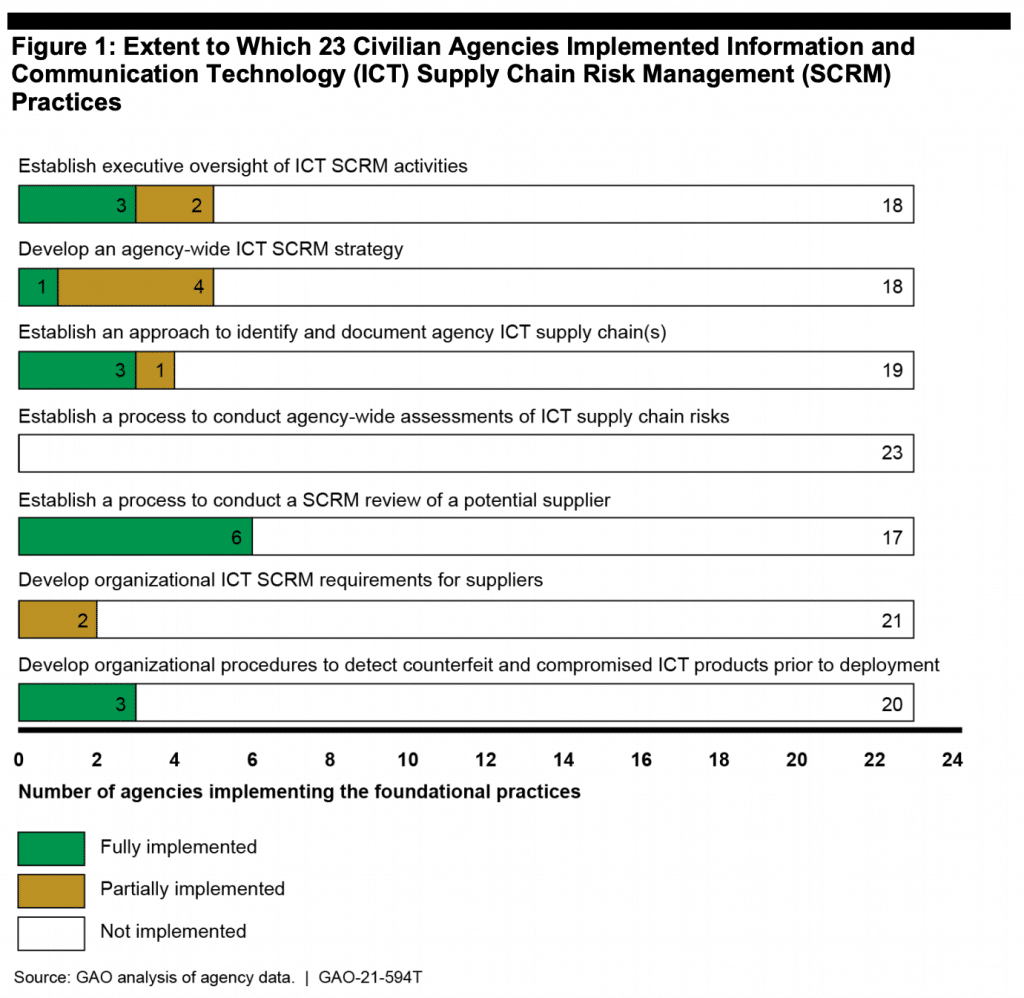
As we can see, federal agencies are nowhere near where they should be in terms of managing cybersecurity threats in their supply chain. No wonder the Biden Administration has issued an executive order to address the problem; it is widespread and severe.
The practical point for SaaS providers is this: government agencies will need more assurance from providers like you that your cybersecurity risks are under control.
Anticipate that need. Assess your own vendor risk management capabilities, including your ability to document the program and provide evidence of your compliance with FedRAMP and other cybersecurity standards. It will make you a more attractive business partner than rivals whose vendor risk management process is in disarray.
What capabilities will you need?
Let’s tie this point about preparedness back to the Biden Administration’s executive order. At a high level, we can already see the capabilities SaaS providers will need to improve if you want to remain competitive when bidding on government contracts.
Technical capabilities. You’ll need better management of penetration testing and network monitoring. You’ll also need to be better at redesigning access controls and business processes to accommodate the push for zero-trust architecture and multi-factor authentication.
Related article: Critical Data Security Controls Every Organization Needs
Evidence collection. This means both the forensic ability to investigate cyberattacks and the collection and storage of that evidence so you can present it to regulators or other government investigators pursuing the attackers.
Related article: Evidence Collection for Security Assurance: The Challenges and the Solutions
Third-party risk management. You’ll need stronger oversight of third-party software code used in your own products and services. That will mean steps such as:
- Including specific language in the contracts you have with your own vendors to ensure that they monitor their own third-party risks;
- Implementing policies, procedures, and training for employees on how to source software code they incorporate into your products;
- Implementing controls to enforce those policies and procedures, followed up with periodic audits to ensure that they work.
Remediation and documentation. Complying with a higher standard of cybersecurity means implementing remediation. You’ll need a system to assign those tasks and track that work. Moreover, you’ll need to ensure that this remediation work dovetails with other compliance burdens you have, such as HIPAA or PCI-DSS — so data mapping and control mapping will become critical capabilities.
Conclusion
Ransomware and other cybersecurity abuses are now an epidemic in the business world; nobody should be surprised that the Biden Administration is trying to address the problem through higher cybersecurity standards. Compliance with those standards might be challenging, but it’s necessary. CISOs should start planning on that now.
Need help with controls monitoring, evidence collection and managing third-party risk?
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












