How to Operationalize Supply Chain Risk Management
We live in a world where vendors’ vulnerabilities can become your headline-making disaster. That’s why managing supply chain risk requires a commitment across the entire organization, not just the procurement team. Supply chain risk management (SCRM) is no longer just procurement’s problem, it’s everyone’s responsibility.
COVID-19 exposed the fragility of our global supply chains. The SolarWinds breach showed us how third-party software can be the back door to a full-blown cyberattack. The war in Ukraine disrupted logistics and energy markets. Tariffs continue to throw unexpected punches at your bottom line.
Modern supply chains are more complex, interconnected, and digital than ever before. This means they’re exposed to more cyber threats, regulatory scrutiny, and operational disruptions. Compliance teams are now front and center, helping organizations manage risk and prove that they are doing their due diligence to maintain compliance across a web of vendors and suppliers.
What is supply chain risk management?
Supply chain risk management is the process of identifying, assessing, mitigating, and monitoring risks within an organization’s supply chain. These risks can originate from third-party vendors, suppliers, partners, logistics providers, or even digital systems that power the supply chain. An effective SCRM strategy is a dynamic, ongoing process with the goal of building resilience and accountability across every supplier relationship.
6 types of supply chain risk
To effectively manage supply chain risk, it’s important to understand the various types and determine which apply to your organization. The five common types of supply chain risk are:
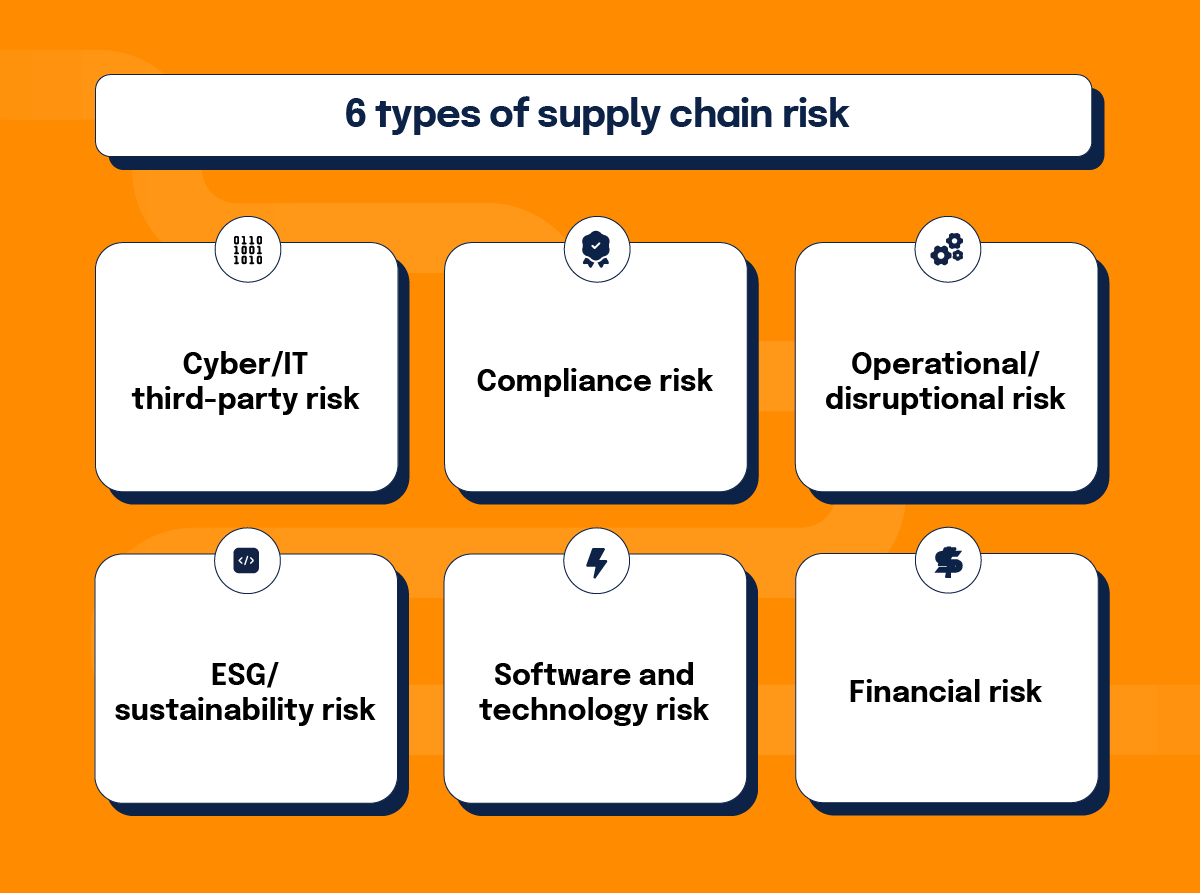
1. Cyber/IT third-party risk
As digital transformation accelerates, cybersecurity threats like code injection attacks, phishing, malware, and others escalate. Third-party software, cloud platforms, and Internet of Things (IoT) devices all create potential access points for attackers. A single vulnerability in a vendor’s system can expose sensitive data, disrupt operations, or result in regulatory violations.
2. Compliance risk
The regulatory world is growing more complex by the day. Frameworks such as ISO/IEC 27001, NIST CSF, PCI DSS, and the EU Cyber Resilience Act require strict adherence to information security, data privacy, and software development best practices. Suppliers that fail to meet these standards can introduce serious downstream risks.
3. Operational/disruption risk
Disruptions come in many forms, including delays, logistics issues, natural disasters, pandemics, or geopolitical instability that affect supply continuity. Operational risk directly impacts your ability to deliver products or services on time and within budget.
A significant operational risk is single-source dependency, or choosing to buy from one supplier. While this may seem efficient, relying on a sole supplier leaves organizations subject to the supplier’s terms and conditions. If your single supplier experiences any sort of disruption and you have no viable backup, it leaves your operations at a standstill. It’s important to have visibility into the lower tiers of your supply chain to avoid these risks.
4. ESG/sustainability risk
Environmental, social, and governance (ESG) risks are under increasing scrutiny from investors and regulators. Investors, customers, and regulators want to ensure your product is ethically sourced, emissions are managed, and human rights are protected. ESG risk compliance in the supply chain is now business-critical. Common examples of ESG risks include:
Environmental risks: Resource scarcity, climate change, biodiversity, pollution and waste, and environmental regulations
Social risks: Health and safety, labor or human rights violations, diversity and inclusion, and community impact
Governance risks: Corruption and bribery, business ethics, risk management, leadership, and corporate governance
5. Software and technology risk
Your supply chain likely relies on a variety of tools, like cloud services, IoT, and artificial intelligence (AI). All of which introduce new vulnerabilities. These technologies increase efficiency, but a bug, breach, or API failure in your tech stack can have ripple effects throughout your operations.
6. Financial risk
The financial stability of a supplier is often underestimated. If one of your key vendors experiences financial distress, their ability to deliver goods or services can be impacted and trigger delays, disruptions, and potential contract breaches.
Financial risks can stem from economic downturns, currency fluctuations, interest rate increases, or the sudden collapse of a supplier. Financial risk can also be more subtle. It might look like a pattern of late payments to subcontractors, thinning profit margins, or increasing debt, all of which are potential red flags that a vendor is struggling behind the scenes.
For these reasons, it is important to assess a supplier’s financial viability during onboarding and to maintain that visibility over time. Reviewing financial statements, continuously monitoring risks, and requesting regular updates can help you catch issues early.
Financial risk can also show up in other forms, including theft, inventory shrinkage, invoice fraud, or compliance with financial regulations. All of these risks can cause ripple effects through your supply chain if left unaddressed.
Managing supply chain risk types
Several frameworks and regulations aim to manage and mitigate these risks:
The rise of agentic AI in SCRM
One of the latest developments in SCRM is the rise of agentic AI. These are AI systems that can independently monitor, assess, and act on supply chain risks in real time. According to a recent IBM report, agentic AI is redefining how businesses build resilience by automating repetitive tasks, enhancing decision-making, and enabling dynamic risk response.
Agentic AI solutions can:
By integrating agentic AI into your SCRM strategy, you can scale risk monitoring efforts and increase agility across global operations. This is particularly valuable in environments where disruption is constant and human bandwidth is limited.
5 steps to reduce supply chain risk
Operationalizing SCRM starts with a proactive, methodical approach. Here’s how organizations can reduce supply chain risk:
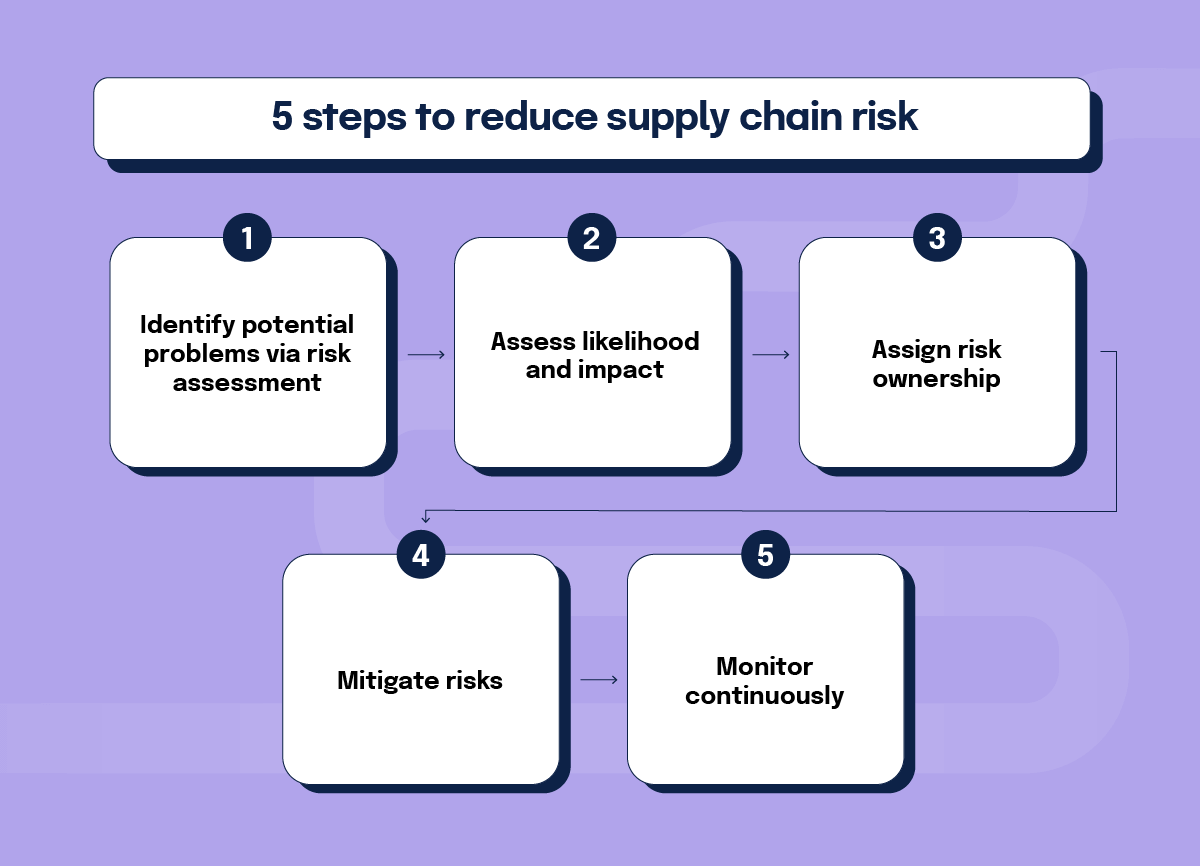
1. Identify potential problems via risk assessment
Start with a supply chain risk assessment to uncover hidden vulnerabilities across your vendor ecosystem. Map out every supplier, categorize them by function and criticality, and determine where risk exposure is highest.
2. Assess likelihood and impact
For each identified risk, evaluate the likelihood of occurrence and potential impact. Quantify both short- and long-term consequences, including financial loss, reputational damage, and regulatory penalties.
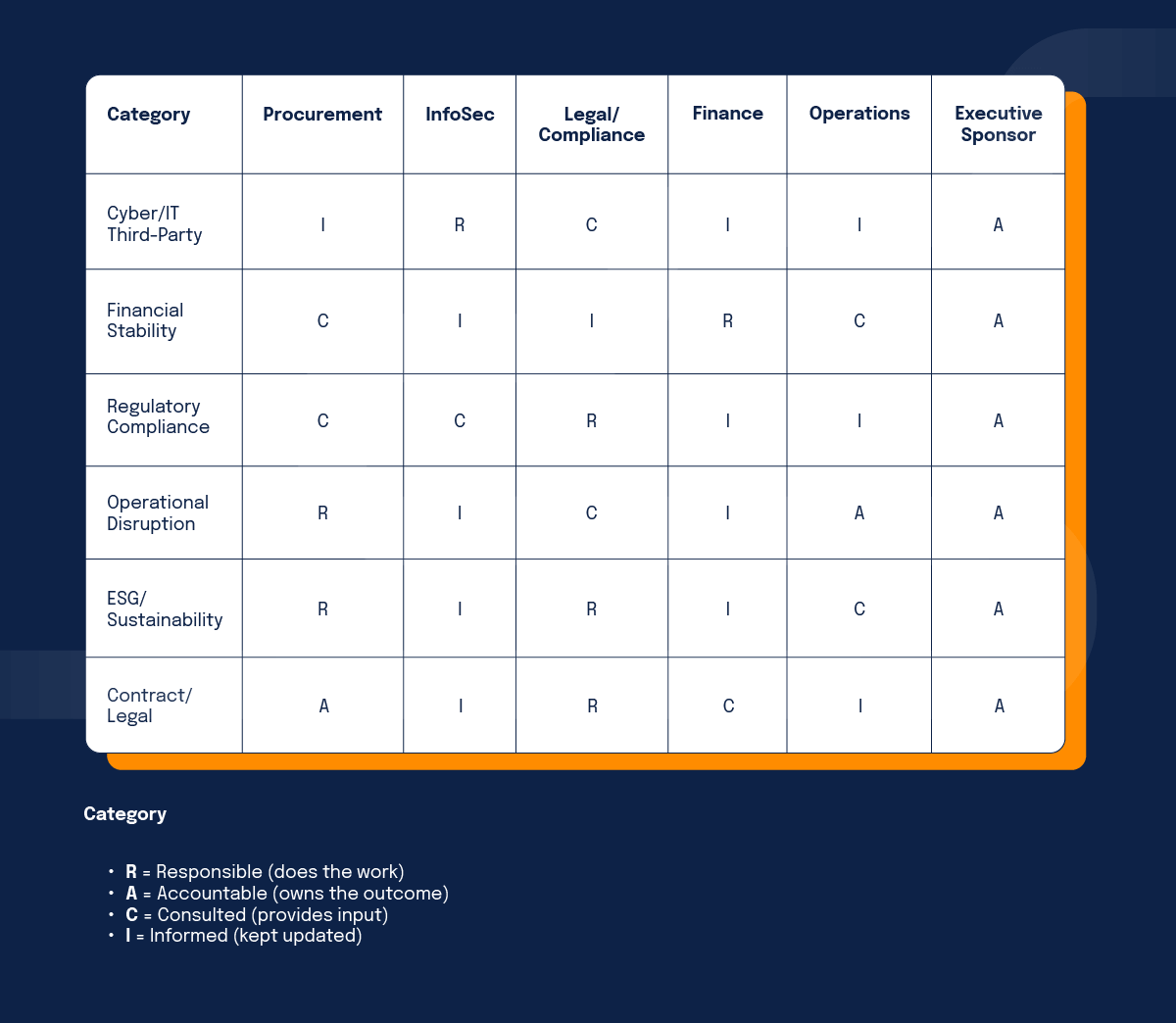
3. Assign risk ownership
Communication breakdowns commonly happen when no one knows who is responsible for what. To avoid any gaps, delays, or duplicated efforts and to know who is accountable or the point of contact for a specific area, it is important to assign clear ownership of different risk areas.
Start by designating teams to different areas, like your InfoSec team leads cyber risk management, legal oversees regulatory compliance, and procurement manages financial and operational due diligence. Then, you can break this down on an individual level by creating a RACI chart. RACI stands for:
Responsible: You are doing the work
Accountable: You own the outcome of the work
Consulted: You provide input on the work
Informed: You are kept in the loop about the work
This level of clarity will help ensure nothing slips through the cracks and everyone knows the role they play in mitigating supply chain risk. For example:
4. Mitigate risks
Create a strategy for mitigating risks with tactics such as:
5. Monitor continuously
Any form of risk management is never a one-and-done exercise, it requires continuous monitoring and attention. Examples include using KPIs and dashboards to track supplier performance, conducting regular audits, and engaging stakeholders. Monitoring should be continuous and adaptive.
Testing should also occur regularly to validate your response plans. Consider conducting simulations and tabletop exercises on a regular cadence
Related resource: How to Assess Your Vendor Risk Management Program Health
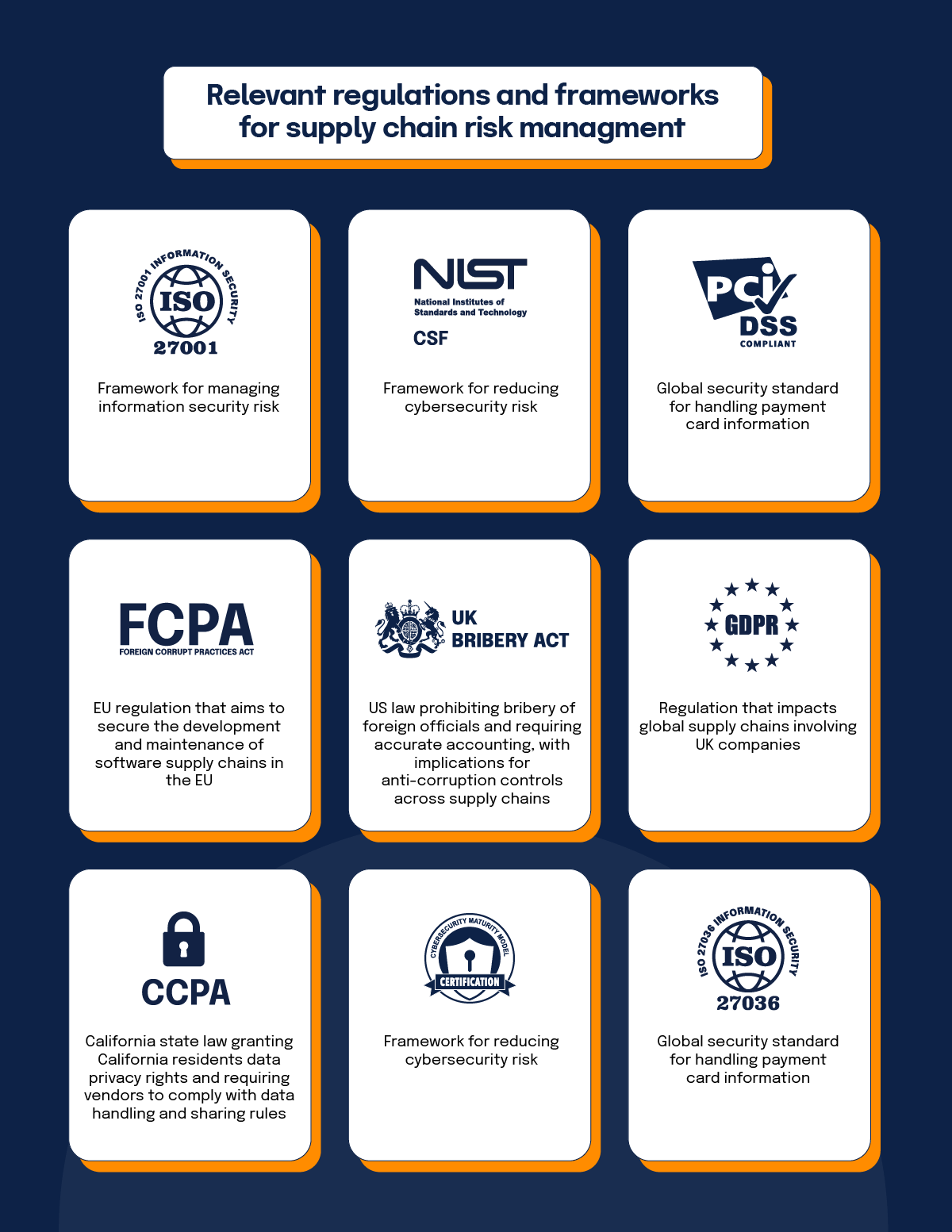
Regulatory compliance in SCRM
Compliance is a non-negotiable aspect of supply chain risk management. Organizations must manage third-party vendor risks and adhere to industry-specific standards and regulations.
The role of compliance teams in SCRM strategy
Compliance professionals play a role in SCRM by:
Common challenges in enforcing compliance
Common challenges of enforcing compliance in SCRM include:
How to build a risk-ready supply chain program
To build a mature SCRM program, companies must operationalize risk and compliance activities across the full vendor lifecycle.
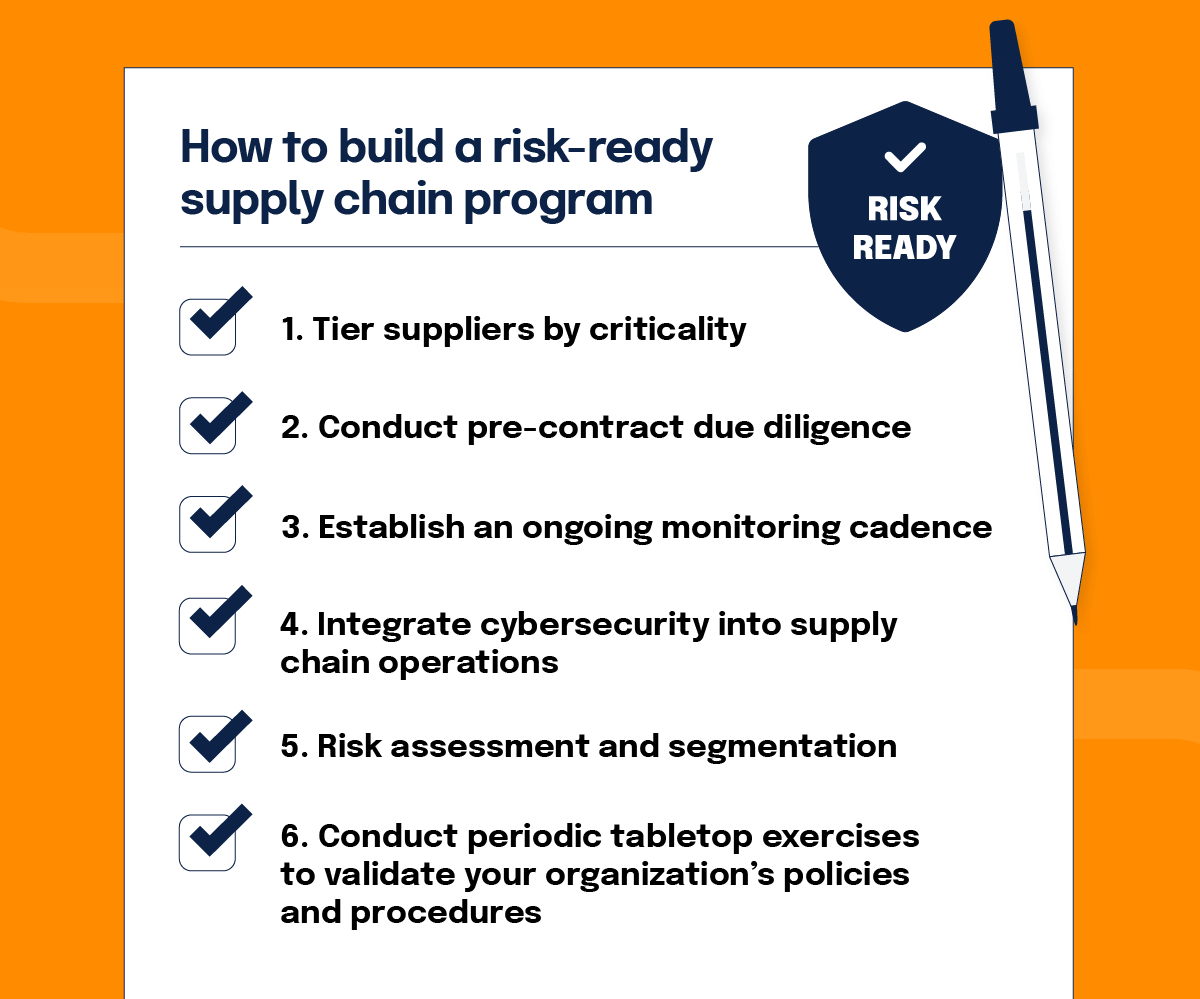
1. Tier suppliers by criticality
Classify vendors based on business impact. High-tier vendors require deeper assessments and more frequent monitoring.
2. Conduct pre-contract due diligence
Before onboarding a new vendor, assess their security posture, compliance status, and operational maturity. Use standardized checklists to streamline this process.
3. Establish an ongoing monitoring cadence
Don’t stop at onboarding. Build in regular check-ins, assessments, and audits. Track changes to a vendor’s risk profile and hold them accountable to performance metrics.
4. Integrate cybersecurity into supply chain operations
Cyber resilience isn’t optional. Integrate security reviews into procurement workflows. Establish incident response protocols for third-party breaches and simulate scenarios to test preparedness.
5. Risk assessment and segmentation
Build a risk map of your supply chain. Segment vendors by geography, industry, and function. Identify single points of failure and prioritize high-impact relationships.
6. Conduct periodic tabletop exercises to validate your organization’s policies and procedures
Develop and execute periodic tabletop exercises such as the one below to validate your supply chain risk management policies and procedures work in practice, not just in theory or on paper. Below is an example of a tabletop exercise that you can use as a template to get started:
Bridging risk and compliance with the right tools
The right technology can help teams manage risk at scale without burdening suppliers or overstretching internal resources.
Hyperproof’s approach to third-party risk management
Hyperproof helps compliance and risk teams:
By streamlining repetitive tasks and surfacing insights, Hyperproof empowers teams to shift from reactive to proactive risk management.
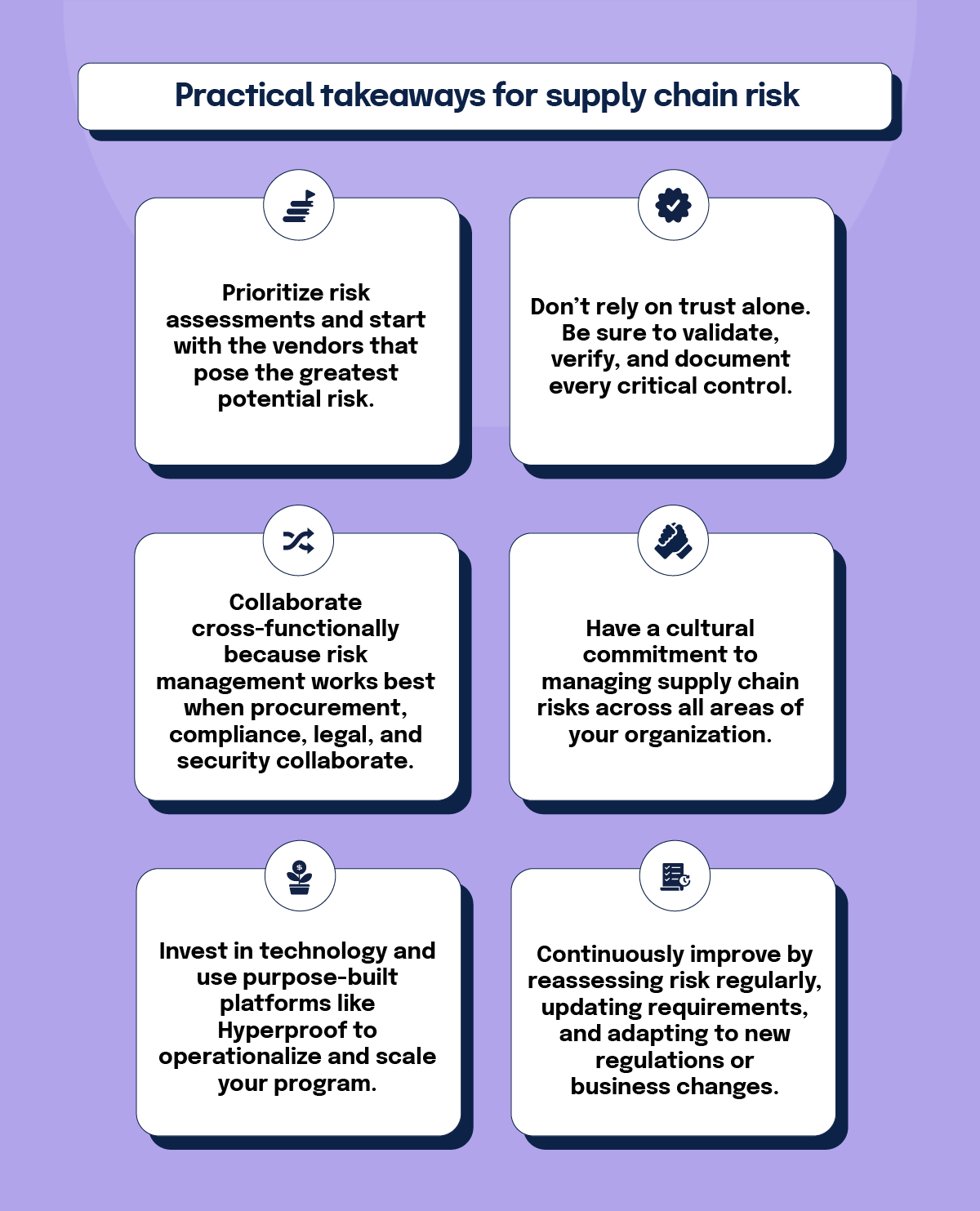
Practical takeaways
The strategic value of supply chain risk management
A strong SCRM program prevents disruption and builds trust. By addressing supply chain risks head-on, you enhance operational resilience, ensure regulatory compliance, reduce financial and reputational damage, and create a competitive advantage through trust and transparency. Strong supply chain risk management can also lead to significant cost savings by minimizing the expenses associated with supply chain disruptions, fines, and emergency response efforts while also reducing inefficiencies and redundancies.
Supply chain ecosystems are only going to become more interconnected and vulnerable. By operationalizing risk management now, you can stay ahead of the threats, satisfy regulators, and build a business that’s ready for whatever comes next.
Hyperproof helps you bring structure, scale, and visibility to your risk management program. Ready to see how?
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












