ISO 27001 Implementation Checklist: 10 Tips to Become Certification Ready

ISO/IEC 27001 is an information security standard designed and regulated by the International Organization for Standardization, and while it isn’t legally mandated, having the certification is essential for securing contracts with large companies, government organizations, and companies in security-conscious industries. In this blog, we will provide an ISO 27001 implementation checklist with 10 tips for becoming certification ready!
ISO 27001 is notable because it is an all-encompassing framework for protecting information assets. Many organizations’ security teams will ask to see an ISO 27001 certification from a potential vendor during the contracting process. They want to know that the potential vendor has invested significant time and resources in protecting information assets and mitigating security risks. An ISO 27001 certification can help reduce audit fatigue by eliminating or reducing the need for spot audits from customers and business partners.
Get detailed guidance on how to achieve an ISO 27001 certification
ISO 27001 certification process

Getting ISO 27001 certified goes beyond ensuring that your Information Security Management System (ISMS) meets the ISO 27001 standard. You must produce adequate evidence (e.g., written policies, systems logs, screenshots from different systems, etc.) that convinces a certified auditor that your ISMS complies with the standard.
Getting the ISO 27001 certification is not a short or easy process. Depending on the amount of work your organization has already put into its information security program, it may take several months to eighteen months or longer for your company to prepare for the ISO 27001 compliance audit. Related: Guide to ISO 27001
Key steps in the ISO 27001 implementation journey
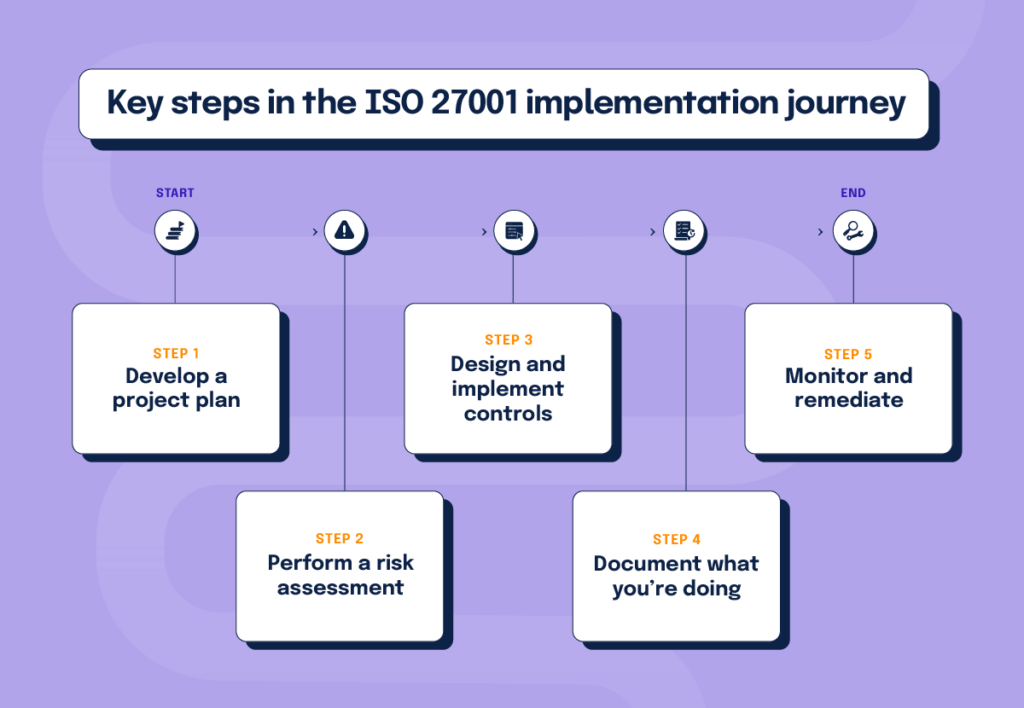
The ISO 27001 compliance journey involves several key steps, including:
- Develop a project plan. Treating your ISO 27001 initiative as a project that needs to be managed diligently is important.
- Perform a risk assessment. The objective of the risk assessment is to identify the report’s scope (including your assets, threats and overall risks), build a hypothesis on whether you’ll pass or fail, and build a security roadmap to fix things that represent significant risks to security.
- Design and implement controls based on your security roadmap.
- Document what you’re doing. During an audit, you will need to provide your auditor documentation on how you’re meeting the requirements of ISO 27001 with your security processes so they can conduct an informed assessment. As such, it’s best to keep detailed documentation of your policies and security ISO 27001 procedures and logs of security activities as those activities happen.
- Monitor and remediate. Monitoring against documented ISO 27001 procedures is especially important because it will reveal deviations that, if significant enough, may cause you to fail your audit. Monitoring allows you to fix things before it’s too late. Consider monitoring your last dress rehearsal: Use this time to finalize your documentation and ensure things are signed off.
Once you’ve completed all these phases, you’ll schedule the certification assessment with a qualified assessor. The assessor will conduct a review of documents regarding your security management system (ISMS) to verify that all of the proper policies and control designs are in place. They’ll also review data generated regarding the practices and activities inside your business to ensure they align with ISO 27001 requirements and written policies.
In this article, we’ll highlight ten practical tips to help you develop a solid ISO 27001 implementation plan and become audit-ready most efficiently.
ISO 27001 compliance checklist: Ten tips for implementation

1. Secure executive buy-in in the beginning
To become ISO 27001 certified, your entire organization must accept and adapt to inevitable changes. To ensure that your ISMS meets the ISO 27001 standard, you’ll likely need to create new policies and processes, change some internal workflows, add new responsibilities to employees’ plates, implement new tools, and train people on security topics. Auditors also expect you to create detailed deliverables, including a Risk treatment plan (RTP) and a Statement of Applicability (SoA). All of this work takes time and commitment from stakeholders across an organization. As such, having senior executives who believe in the importance of this project and set the tone is crucial to its success.
2. Hire an external expert to conduct a ISO 27001 gap analysis
A gap analysis provides a high-level overview of what needs to be done to achieve certification and compares your organization’s existing information security measures against the requirements of ISO 27001. It also helps to clarify the scope of your ISMS, your internal resource requirements, and the potential timeline to achieve certification readiness.
If you don’t have internal expertise on ISO 27001, getting a credible consultant with the requisite experience in ISO 27001 to conduct the gap analysis can be highly beneficial. An experienced expert can help you develop a business case and a realistic timeline to achieve certification readiness — so you can secure the necessary leadership commitment and investment.
3. Appoint a project leader
It is important to identify someone who’s dedicated to driving the project forward. The project leader will convene with senior leaders across the organization to review objectives and set information security goals. This person will develop a project plan and assign roles and responsibilities to other stakeholders. This person will also develop forums (e.g., an ISO 27001 executive committee and an ISO 27001 work committee) to ensure progress is consistently made.
4. Be careful about scoping the ISMS
Scoping is about deciding which information assets to “fence off” and protect. It’s a decision each business has to make for itself. Doing this correctly is critical because defining too broad of a scope will add time and cost to the project, but a too narrow scope will leave your organization vulnerable to risks that weren’t considered.
5. Establish a risk management framework that meets the requirements of ISO 27001
Assessing and managing information security risks is a key component of ISO 27001. Ensure you use a risk assessment method that’s ISO 27001 approved and approved by your senior management. According to ISO 27001, a formal risk assessment methodology needs to address four issues: 1. Baseline security criteria; 2. Risk appetite; 3. Risk scale; 4. Assessments are based on specific scenarios or covering specific assets.
6. Break down control implementation work into smaller pieces with a tool
ISO 27001 requires organizations to apply controls to manage or reduce risks identified in their risk assessment. To keep things manageable, prioritize the controls and mitigate the most significant risks.
Scope out the work and break it out into two- or three-week sprints. List the tasks you (and others) must complete and put them on a calendar. Track your team’s progress easily by putting your functions into a compliance project management tool with good visualization capabilities.
7. Map existing controls to ISO 27001 requirements
If ISO 27001 isn’t your organization’s first security compliance program, you’ll have existing controls that can be leveraged to meet ISO 27001 requirements. For instance, if you’ve done SOC 2 Type 2, you may already have security controls that work for ISO 27001.
By evaluating existing controls and crosswalking them to ISO 27001 requirements, you’ll be able to avoid duplicative work when it’s time to test controls and collect evidence. You’ll also have a smaller set of controls to monitor and review. This type of control mapping exercise can be done manually, but it’s much easier to manage within purpose-built ISO 27001 compliance software.
8. Efficiently prepare risk treatment plan and Statement of Applicability (SoA) by documenting along the way
The risk treatment plan (RTP) and Statement of Applicability (SoA) are vital documents required for an ISO 27001 compliance project. The RTP describes the steps to deal with each risk identified in the risk assessment. The SoA lists all the controls specified in ISO 27001 and outlines whether each control has been applied and why it was included.
If you consistently document the risks and the controls while the actual work is happening, you don’t need to go back and spend a lot of energy putting these two documents together. Further, purpose-built compliance software such as Hyperproof is built to help you consistently manage risks and controls — saving time in producing audit documents.
9. Consider scheduling multiple audits at the same time
Although different customer segments may want to see various certifications and audit reports from you, many security standards (e.g., HITRUST, SOC 2, ISO 27001, etc.) share some core requirements.
If ISO 27001 is one of the multiple security audits you go through each year, see if you can convince your auditors to schedule all the audits within the same timeframe (e.g., two or three-week window). We’ve talked to multiple organizations that have done this so the compliance team can gather and submit one set of evidence to their auditors once a year. Doing it this way is less of a burden than having multiple audits spread across the year.
10. Use a compliance operations platform
A compliance operations platform is a central system for planning, managing, and monitoring all compliance work. It helps compliance professionals drive accountability for security and compliance to stakeholders across an organization.
By using a compliance operations platform such as Hyperproof to operationalize security and IT governance, organizations can create a secure environment where compliance becomes an output of people doing their jobs.
The platform helps organizations improve compliance work, so stakeholders can focus on good operations instead of spending extra time to tick off boxes for compliance. Here are some ways compliance operations software can help with ISO 27001 implementation:
- Understand ISO 27001 requirements in detail
- Document your infosec risk assessment results and risk response plans
- Develop your ISMS by implementing controls, assigning roles and responsibilities, and keeping people on track
- Streamline evidence collection and management
- Know how close you are to being certification-ready
- Monitor your ISMS and make continuous improvements
To learn more about Hyperproof, sign up for a demo.
Want to see how you can achieve and maintain ISO 27001 certification efficiently?

See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











