How to Manage Multiple Cybersecurity Compliance Frameworks Without Being Overwhelmed
Your organization has already achieved its first major compliance milestone: you’ve gotten a SOC 2 Type 2 report. Now, your organization is looking to expand into new markets and you need to pursue additional cybersecurity compliance standards or frameworks (e.g., ISO 27001, PCI DSS or CMMC).
Managing an IT compliance program that encompasses multiple standards comes with a set of challenges you need to be aware of, such as:
- Coordinating people and tasks
As you seek to expand your IT compliance program, you’ll likely need to involve more people from your organization in this effort. They’ll need to understand the value of this undertaking and their respective roles in the initiative.
Keeping everyone on the same page and moving in the same direction will become more difficult. Communication will likely increase, and you’ll need a way to manage communications and collaboration effectively.
- Mapping out overlapping areas between multiple standards and frameworks
Many security compliance frameworks have overlapping requirements. How can you approach work in a way that minimizes duplicate effort when testing controls and collecting evidence to meet multiple frameworks’ requirements? To manage things efficiently, you’ll need to map out how requirements are related and what common controls you can use to satisfy multiple requirements. This is really hard to do in a spreadsheet.
- More ongoing work to manage
To align your security program closer with guidelines within a new standard or framework, you will likely need to create new controls related to governance, identity management and access, supply chain management, etc. Developing new controls may involve creating new policies, procedures, or processes, launching training, or implementing new technical solutions. With a greater number of controls in place, ensuring that all controls are suitable to your current environment and their operating effectiveness will become more challenging.
- Having to spend more money on audits
If you’re looking to achieve a certification for certain standards (e.g., ISO 27001 or CMMC), you’ll need to find a qualified auditor, schedule the audit, and pay for it. Certain audits and certification processes can be quite costly, even in the range of six figures. However, depending on the frameworks you choose, it may be possible to find an auditor who’s able to audit against multiple standards at once to drive down costs and the time involved.
Ebook: You’ve Done SOC 2, What’s Next?
See how to use your SOC 2 work to achieve additional IT compliance standards ›

How to manage multiple IT compliance frameworks without getting overwhelmed
Although scaling up your security compliance program may seem daunting, the process becomes quite manageable if you prioritize standing up good processes, ironing out workflows, and leveraging a dedicated compliance operations software to facilitate the work.
As you try to scale up your IT compliance program and pursue additional standards, having an organized approach and streamlined workflows is critical. When you have a greater number of controls to manage (internal policies, processes, procedures, and technical tools), a greater amount of evidence to collect, and more people to coordinate with, you need tools that help you manage that work efficiently.

Why you shouldn’t be using spreadsheets for your compliance effort
Although you can use spreadsheets and other ad-hoc tools (e.g., Sharepoint, Dropbox, Jira, email) to manage your IT compliance effort, it makes it very difficult to stay organized and maintain solid processes over time. Here are a few reasons why using spreadsheets can be limiting:
- When you scale up a compliance program, there are simply too many moving parts to keep track of manually.
- Spreadsheets don’t allow you to create relationships between data in different files. For instance, how do you associate a piece of evidence to several controls in a spreadsheet? How do you indicate that a control you have can be used to satisfy requirements within two or three different cybersecurity standards/frameworks?
- You can’t collect evidence of security and compliance activities and store them in spreadsheets. If you can’t easily link evidence gathered from control testing back to the documented controls and the compliance requirements, when audit time comes, you’ll spend a lot of time trying to collect that evidence.
- Spreadsheets don’t provide audit trails that are critical for effective risk, compliance, and cybersecurity processes.
- Spreadsheet software has limited security features. Individual files can be password-protected, but different users cannot be assigned different access levels. You can track who opened and saved a spreadsheet file and when, but you cannot tell what changes they made, if any. What happens when someone makes a mistake and you’re left with no way to trace who was responsible or when it occurred?
- You can’t orchestrate workflows with spreadsheets. Your compliance effort most likely involves input from multiple stakeholders. For instance, multiple exchanges are needed before someone can finally sign off and say a particular control has been implemented. A control operator and a compliance professional may need to exchange several messages before the compliance professional is able to receive the correct proof an external auditor expects to see. These types of workflows can’t be managed in spreadsheets, and it’s quite messy to track these exchanges in email threads or Slack messages.
- There are limited data visualization capabilities. To keep everyone on track in your compliance effort and identify what to prioritize next, compliance managers need to be able to see how much progress has been made, what work hasn’t been completed yet, and who is responsible, and they need to have a way to follow-up with individuals regarding specific tasks. Due to the inherent limitations of spreadsheets, including the lack of referential integrity and the inability to create relationships between data in different files, getting actionable insights from your data is nearly impossible.
If you managed your SOC 2 compliance work in spreadsheets, it’s time to migrate your work into a Compliance Operations platform. By doing so, you’ll be able to leverage the work already done for SOC 2 to comply with additional frameworks and standards more easily.
Use a compliance operations platform to stay organized and automate routine tasks

By using a compliance operations platform such as Hyperproof, you can stand up multiple cybersecurity and data privacy programs and frameworks, see the program requirements (or guidelines) within a compliance framework in a clear way, and map internal controls against the program’s requirements (or guidelines).
Controls can be mapped to multiple regulatory requirements in a compliance operations platform. Once controls are mapped, compliance professionals are able to manage a smaller set of controls and collect the same evidence once and re-use it across multiple frameworks.
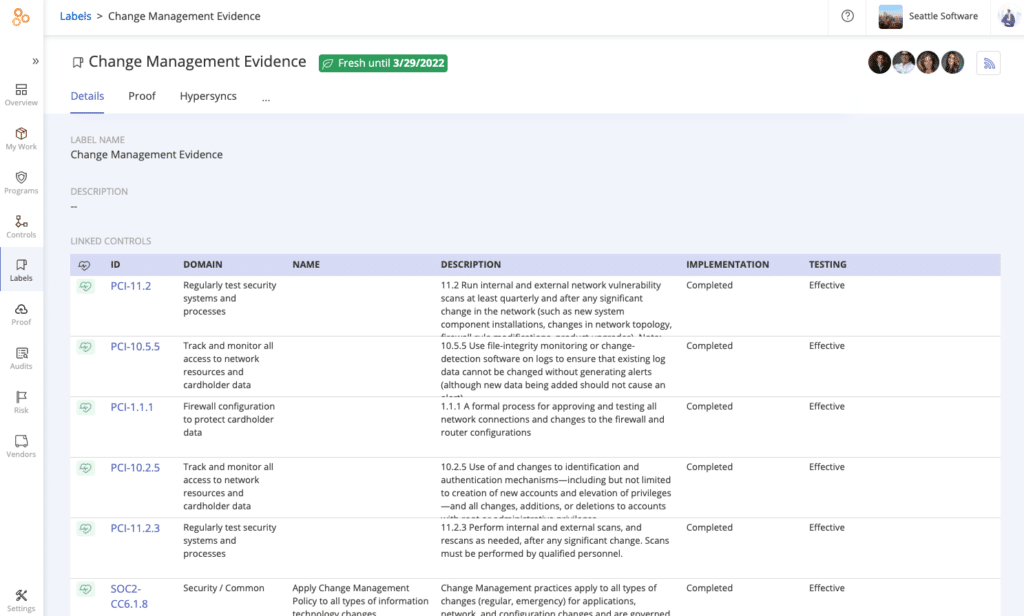
Messages and tasks can be initiated within the platform to people within and outside of your organization (e.g., compliance consultants)—and their responses are tracked centrally. To facilitate seamless collaboration between those in and outside your IT compliance function, Hyperproof integrates natively with multiple communication and project management systems. Messages can be sent out in Hyperproof by compliance professionals and responded to through Slack or Microsoft Teams, or vise versa.
A compliance pro can create tasks for others to complete in Hyperproof and the assignee of the task can complete it in a project management system they’re already familiar with—such as Jira. Any change to a task made in Jira is immediately reflected in Hyperproof—making project management easy.
Hyperproof also comes with dashboards and drill-down reports to give compliance professionals actionable insights about their security posture and compliance gaps.
You can have your SOC 2 program stood up in Hyperproof within a couple of hours. This process is straightforward and simple:
- Create a SOC 2 program in Hyperproof using Hyperproof’s SOC 2 template, which provides all SOC 2 requirements formatted in an accessible way.
- Link your SOC 2 controls to the SOC 2 requirements.
- Upload evidence to specific controls. If you have evidence that you need to gather on a frequent basis (e.g., monthly or weekly), you can configure Hyperproof to automatically sync those documents from your cloud based apps into Hyperproof. Alternately, you can assign tasks to others to submit evidence to attest to controls’ effectiveness.
- In parallel to linking evidence to controls, you can start to add more rigor to your control evaluation effort. For instance, you might assign people to manage specific controls or create a set of tasks around specific controls to ensure they’re evaluated on a cadence and kept up-to-date.
2. Identify SOC 2 controls you can leverage to meet requirements within additional compliance programs, frameworks and standards

Once you’ve stood up a SOC 2 program in Hyperproof, it is time to do a control mapping exercise: figuring out which existing controls can be re-used to satisfy requirements within a new compliance standard or framework. This is tedious to do manually with spreadsheets, but with a compliance operations platform, this exercise is straightforward and requires just a few steps:
- Pick the next framework you want to adopt and create this as a new program in Hyperproof. For instance, you may choose ISO 27001 because your company is looking to expand to Europe. Hyperproof’s ISO 27001 template contains all ISO 27001 requirements out-of-the-box.
- Look through the requirements in ISO 27001. Identify the applicable requirements and delete any that are not applicable to your organization.
- Link existing controls to program requirements or create new controls and link them to the requirements. For each applicable requirement in ISO 27001, Hyperproof automatically assesses if a similar requirement is present within the SOC 2 framework. Where SOC 2 contains a similar requirement to ISO 27001, Hyperproof will surface the SOC 2 controls linked to that requirement and suggest these controls for your consideration in meeting ISO 27001.
- You can choose to accept Hyperproof’s suggested controls or add your own controls to each applicable ISO requirement.
How does Hyperproof know which controls to suggest? Hyperproof has built-in crosswalks based on the Secure Controls Framework (SCF), a comprehensive catalog of controls that enables companies to design, build, and maintain secure processes, systems, and applications. The framework currently incorporates over 850 controls, is baselined across more than 150 regulations and standards, and is updated every few months.
By streamlining your controls set and leveraging common controls to meet the requirements of multiple IT security frameworks, you can create a more efficient approach for managing your IT compliance projects. Now, you can collect evidence for a smaller set of controls and save hours or weeks worth of work. You can focus your energy on more strategic tasks, such as ensuring that those responsible for executing security tasks are doing their part.
Want to learn more about how to build a strategic IT compliance program that’s tailored to your business? Do you want additional tips on how to scale up your IT compliance program and comply with multiple regulations, standards, and frameworks efficiently? Check out our new ebook below.
How to Use Your SOC 2 Work to Achieve Additional IT Security Standards With Less Effort

See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?