What is a PCI Audit? How to Get Your Business Ready
Today, payment card fraud is a booming business with no signs of slowing — out of every $100 in total volume worldwide $6.58 is stolen, according to a 2023 Nilson Report. Losses from fraudulent card transactions are expected to reach $404 billion globally over the next ten years. Ouch – those stats don’t exactly inspire faith in the payment card industry, right?
For modern businesses, offering a card payment option while ensuring the safety of their customers’ most sensitive information is non-negotiable. In finance, PCI stands for the Payment Card Industry – the networks, processors, banks, and merchants involved in issuing and accepting payment cards. It’s become so important that the Payment Card Industry Security Standards Council created the Payment Card Industry Data Security Standard (PCI DSS) as a benchmark for businesses to prove data security competence.
Today, all companies storing, processing, or transmitting sensitive cardholder information must meet PCI DSS requirements. Level 1 merchants (merchants who process over 6 million transactions per year) must demonstrate compliance by passing a PCI audit, which verifies an organization’s ability to safeguard cardholder data and all systems interacting with payment processing based on 12 technical and operational control requirements.
In this article, you will learn about PCI audits and how your team can become audit-ready with our helpful PCI DSS checklist and seven tips for achieving and maintaining PCI compliance.
Ebook: PCI DSS Compliance: Why It Matters and How to Obtain It

What is a PCI compliance audit (PCI audit)?
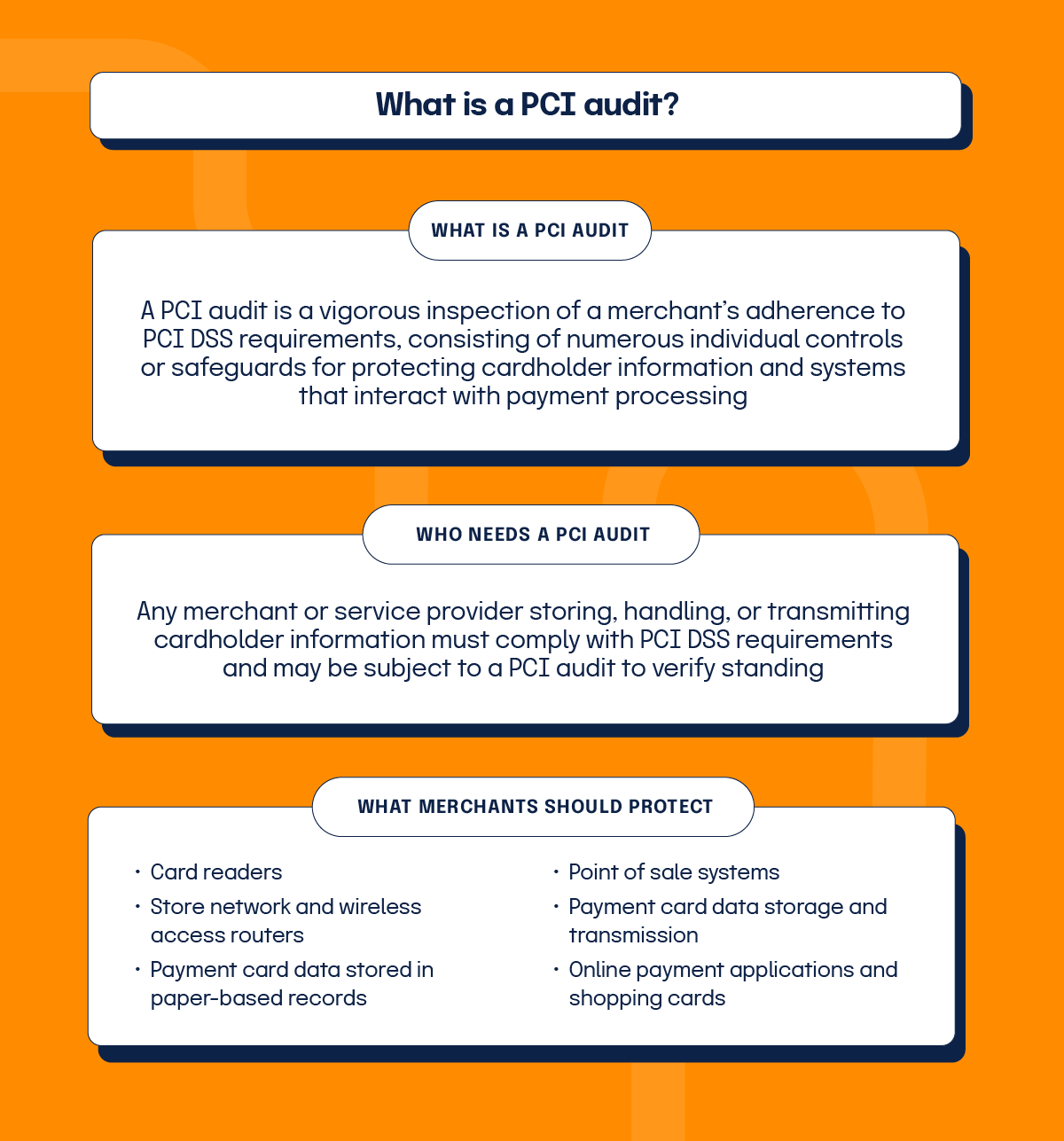
A PCI compliance audit (often shortened to PCI audit) is an independent inspection of a merchant’s adherence to PCI DSS requirements, consisting of numerous individual controls or safeguards for protecting cardholder information (e.g., Primary Account Number, CAV/CID/CVC2/CVV2, etc.) and systems that interact with payment processing.
The Payment Card Industry Security Standard Council defines a merchant as “any entity that accepts payment cards bearing the logos of any PCI SSC Participating Payment Brand as payment for goods and/or services.” PCI DSS provides a baseline of technological and operational requirements designed to safeguard cardholder information. Any merchant or service provider storing, handling, or transmitting cardholder information must comply with PCI DSS requirements and may be subject to a PCI audit to verify compliance.
PCI audits are designed to thoroughly inspect how well your business manages PCI controls, which are safeguards installed to protect all systems interacting with payment card processing.
Merchants and service providers should protect:
PCI DSS requirements
The PCI Security Council set out the following 12 broad technical and operational requirements organizations must meet to be considered PCI compliant:
Build and maintain secure network systems
Requirement 1: Install and maintain a firewall configuration to protect cardholder data
Why this matters: Firewalls and routers are key components of the architecture that control entry to and exit from the network. These devices are software or hardware devices that block unwanted access and manage authorized access into and out of the network. Configuration standards and procedures will help ensure that the organization’s first line of defense in the protection of its data remains strong.
Requirement 2: Do not use vendor-supplied system passwords and other security parameters
Why this matters: Malicious actors (external and internal to an organization) often take advantage of vendor default passwords and other vendor default settings to compromise systems. These passwords and settings are well-known by hacker communities and are easily determined through public information.
Protect cardholder data
Requirement 3: Protect stored cardholder data with methods such as encryption, truncation, masking, and hashing
Why this matters: If an intruder circumvents other security controls and gains access to encrypted data, without the proper cryptographic keys, the data is unreadable and unusable to that person. Other effective methods of protecting stored data should be considered too. For example, methods for minimizing risk include not storing cardholder data unless absolutely necessary, truncating cardholder data if full PAN is not needed, or not sending unprotected PANs using end-user messaging technologies, such as email and instant messaging.
Requirement 4: Encrypt transmission of cardholder data across open, public networks
Why this matters: Sensitive information must be encrypted during transmission over networks that are easily accessed by malicious individuals. Misconfigured wireless networks and vulnerabilities in legacy encryption and authentication protocols continue to be targets of malicious individuals who exploit these vulnerabilities to gain privileged access to cardholder data environments.
Maintain a vulnerability management system
Requirement 5: Use and regularly update anti-virus software or programs
Why this matters: Malicious software, commonly referred to as “malware” — including viruses, worms, and Trojans — enters the network during many business-approved activities, including employee email and use of the internet, smartphones, mobile computers, and storage devices, resulting in the exploitation of system vulnerabilities. Anti-virus software must be used on all systems commonly affected by malware to protect systems from current and evolving malicious software threats. Additional anti-malware solutions may be considered a supplement to the anti-virus software. Additionally, all personnel need to be aware of and follow security policies and procedures to ensure systems are protected from malware continuously.
Requirement 6: Develop and maintain secure systems and applications.
Why this matters: Malicious actors use security vulnerabilities to gain privileged access to systems. Many of these vulnerabilities are fixed by vendor-provided security patches, which must be installed by the entities that manage the systems. To protect against the exploitation and compromise of cardholder data by malicious individuals and software, all systems need to have appropriate software patches — patches that have been evaluated and sufficiently tested to verify that they don’t conflict with existing security configurations. For in-house developed applications, you can often avoid numerous vulnerabilities by using standard software development processes and secure coding techniques.
Implement strong access control measures
Requirement 7: Restrict access to cardholder data to a need-to-know basis
Why this matters: To ensure critical data can only be accessed by authorized personnel, systems and processes need to be in place to limit access on a need-to-know basis and according to job responsibilities. “Need to know” is when access rights are granted to the least amount of data and privileges needed to perform a job duty.
Requirement 8: Assign a unique ID to each person with computer access
Why this matters: Assigning a unique ID to each person with access ensures that each individual is uniquely accountable for their actions. When such accountability is in place, actions taken on critical data and systems can be traced to known and authorized users and processes. Further, the effectiveness of a password is largely determined by the design and implementation of the authentication system, particularly, how frequently password attempts can be made by an attacker, and the security methods to protect user passwords at the point of entry, during transmission, and while in storage.
Requirement 9: Restrict physical access to cardholder data
Why this matters: Any physical access to data or systems that house cardholder data provides an opportunity for individuals to access devices or data and to remove systems or hardcopies and should be appropriately restricted.
Regularly monitor and test networks
Requirement 10: Track and monitor all access to network resources and cardholder data
Why this matters: Logging mechanisms and the ability to track user activities are critical in preventing, detecting, or minimizing the impact of a data compromise. The presence of logs in all environments allow thorough tracking, alerting, and analysis when something goes wrong. It is critical to have a process or system that links user access to system components accessed. Without system activity logs, determining the cause of a compromise is very difficult, if not impossible.
Requirement 11: Regularly test security systems and processes
Why this matters: Vulnerabilities are discovered continually by malicious individuals and researchers, and often introduced by new software. System components, processes, and custom software should be tested frequently to ensure security controls continue to reflect a changing environment.
Maintain an information security policy
Requirement 12: Maintain a policy that addresses the information security for employees and contractors
Why this matters: A strong security policy sets the security tone for the whole company and tells personnel what is expected of them. All employees should be aware of the sensitivity of data and their responsibilities in protecting it.
Each of the 12 broad requirements also contains multiple sub-requirements (not shown here).
During a PCI compliance audit, a QSA will review written, company-provided documents, interview technical staff, and in some cases examine samples of system components (e.g., files and system records) to verify that each of these specific requirements is sufficiently met.
Often the word audit triggers concern and apprehension, but this shouldn’t be the case with a PCI audit. Make no mistake, failing to comply with PCI DSS regulations can result in costly penalties and unpleasant repercussions for your business. However, a PCI audit provides the opportunity to work with a QSA to discover vulnerabilities and areas needing improvement within your data security system. Audits provide a snapshot of the current status and allow the opportunity for learning and growth while helping your business achieve and maintain PCI DSS compliance into the future.
Does my company need to go through a PCI audit to prove compliance?
It depends on your company’s status as a merchant and the requirements of your chosen payment brand. PCI DSS created four levels of PCI compliance determined by merchant type. The four levels including compliance requirements are as follows:
PCI Merchant Level 1
This level includes all merchants with over 6 million transactions a year across all channels or any merchant that has experienced a data breach. Level 1 businesses must undergo annual 3rd-party audits to verify compliance plus annual network scans conducted by an approved scanning vendor. They must also receive two official documents–an Attestation of Compliance (AoC) and a Report on Compliance (RoC).
PCI Merchant Level 2
This level includes merchants with between 1 million and 6 million transactions annually across all channels. All merchants on Levels 2 through 4 must complete a PCI DSS Self Assessment Questionnaire that is signed off by the company’s senior management team in addition to quarterly network scans conducted by approved scanning vendors.
PCI Merchant Level 3
Level 3 includes merchants with between 20,000 and 1 million online transactions annually.
PCI Merchant Level 4
Level 4 includes merchants with fewer than 20,000 online transactions annually or any merchant processing up to 1 million in-person transactions per year.
Due to the sensitive nature of cardholder data, only Qualified Security Assessors (QSAs) approved by the PCI Security Standards Council can conduct PCI audits. Practically speaking, your PCI compliance auditor will be one of these QSAs, engaged to independently validate that you meet PCI DSS requirements for your merchant level.
How does a PCI audit work?
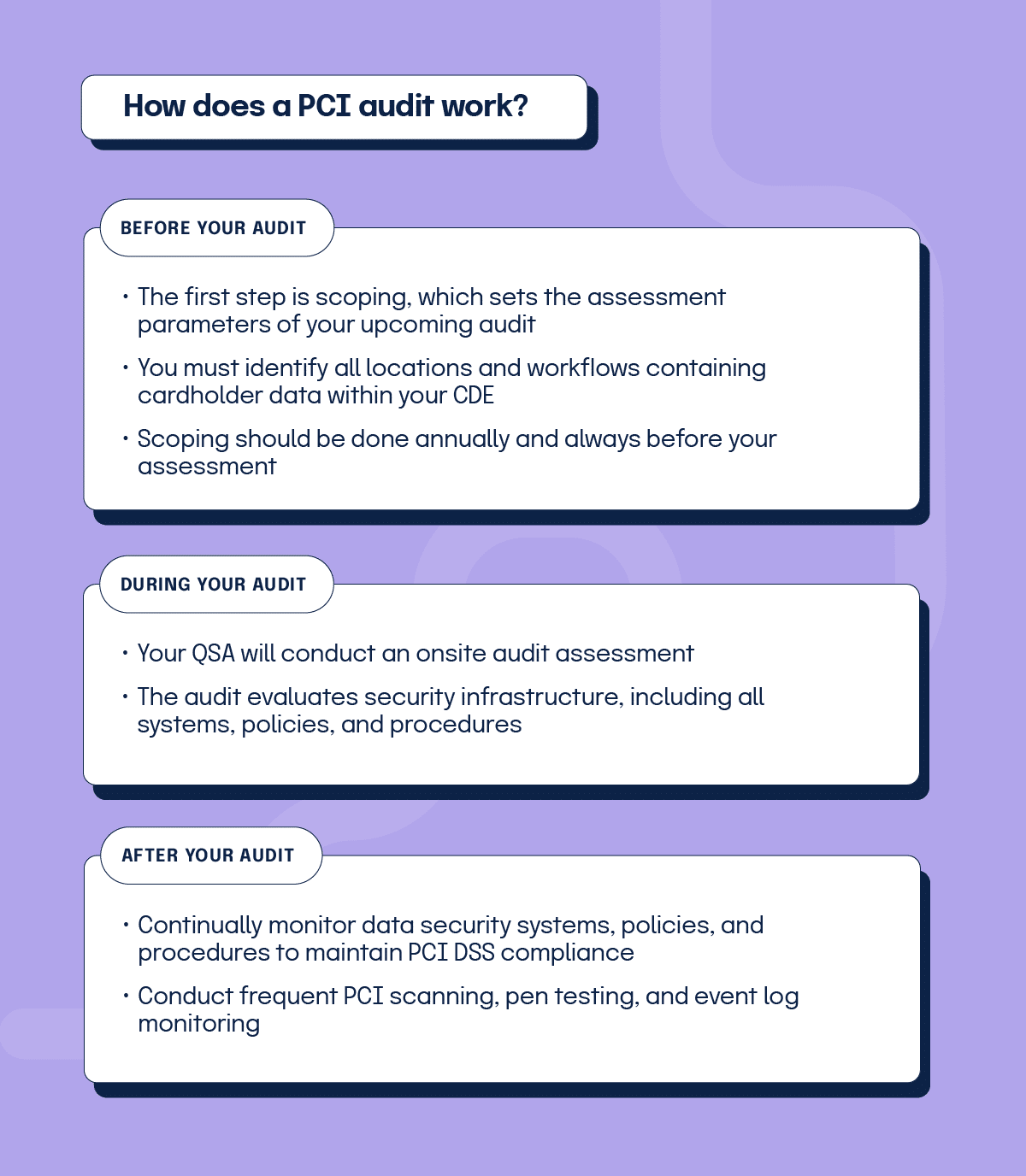
The first step in preparing for your PCI audit is scoping, which sets the assessment parameters, or scope, of your upcoming audit. Your team must identify all locations and workflows containing cardholder data within your cardholder data environment (CDE). Scoping all systems should be done annually and always before your assessment. It falls on you to narrow the scope of your evaluation beforehand, as auditors arrive prepared to include all system processes unless otherwise noted, according to PCI Security Standards Council guidelines.
Next, your QSA will conduct a full onsite audit assessment to evaluate security infrastructure, including all systems, policies, and procedures. It is the QSA’s responsibility to:
The final audit stage is ongoing as all organizations must continually monitor data security systems, policies, and procedures to maintain PCI DSS compliance moving forward. Many businesses conduct frequent PCI scanning, pen testing, and event log monitoring to ensure all PCI data protection controls are meeting the standard.
How often do I need to get a PCI audit?
PCI DSS doesn’t mandate the frequency of PCI audits – it’s really up to the payment card company with whom you choose to work. For example, American Express has its own set of audit frequency requirements, as do Visa and MasterCard. However, it’s important to remember that businesses identified as Level 1 (over six million yearly card transactions) or those who have experienced a breach must pass a minimum of one audit per year to remain PCI compliant.
What happens if I fail my PCI audit?
A PCI audit shouldn’t be viewed as a pass or fail event but as an opportunity to discover what’s needed to better serve your customers’ data security needs. If your QSA discovers a system vulnerability, your organization only fails by not quickly addressing and fixing the issue.
On the other hand, businesses ignoring PCI audit findings, refusing to fix system shortcomings, or deciding PCI DSS regulations don’t apply to them will experience the costly ramifications of non-compliance. Credit card companies can impose fines from $5,000 to $100,000 monthly depending on an infraction’s severity.
Fraudulent purchases can trigger bank reversal charges for which the offending organization may be held responsible.
Most importantly, today’s customers don’t want to do business with companies that don’t take data security seriously. Many choose to file lawsuits when their data is compromised, and once news of such events hits the mainstream, a crippling loss of business and drop in revenue often result for the responsible party. Becoming a publicized PCI DSS offender leads to bad press and a tarnished brand image capable of sinking even the most prosperous enterprise.
How can my business be audit-ready and achieve PCI compliance?

Achieving and maintaining PCI compliance is an ongoing process requiring continued diligence and commitment, but there is help available for organizations willing to put forth the effort. Many organizations formalize this into a PCI compliance audit program – a repeatable set of policies, controls, reviews, and evidence collection activities that keep them continuously ready for their next PCI audit. QSA firms can provide a wealth of information and resources, starting with security awareness training for all employees.
PCI compliance checklists can serve as a helpful guide in preparation for an upcoming audit. Here are some considerations to boost compliance while helping your team become PCI audit-ready:
7 general tips for achieving and maintaining PCI compliance

In addition to PCI compliance checklists, we recommend referencing the following 7 Tips for Achieving and Maintaining PCI Compliance listed below:
Maintain PCI DSS controls over time: PCI compliance isn’t a sprint to pass an annual audit but rather a marathon of continuous monitoring, assessing, and enforcing the use of PCI DSS controls over time. An audit is your business’s checkup — not a substitute for the daily actions necessary to maintain PCI compliance throughout the year.
Limit the cardholder data you store: Only keep essential cardholder data – if you don’t need it, why continue to be responsible for it?
Don’t store sensitive authentication data after authorization: Be sure to eliminate all authentication information after it’s no longer needed–this includes magnetic strip and chip data, card verification codes, and PINS.
Ensure your POS vendor’s security: Be sure to ask your POS vendors how they address common control failures like default settings and passwords. If their POS software stores sensitive authentication data, are they capable of quickly deleting it after use?
Isolate and consolidate essential cardholder data: Remember to store sensitive data in a consolidated, central location and isolate it with network segmentation. Consolidation will simplify access and can also help limit the scope of your PCI DSS assessment.
Use compensating controls: Don’t forget to document and use all compensating controls to substitute for PCI DSS controls whenever possible.
Contact your QSA for assistance and training: The QSA’s role includes providing support and guidance throughout your compliance process, be sure to engage this resource.
FAQ: PCI audits and PCI compliance
What is a PCI compliance audit?
A PCI compliance audit is an independent assessment of whether your organization meets the Payment Card Industry Data Security Standard (PCI DSS). A PCI compliance auditor (typically a QSA) reviews your technical controls, policies, and processes to confirm that systems storing, processing, or transmitting cardholder data are configured and operated securely.
What does PCI mean in finance?
In finance, PCI stands for Payment Card Industry. It refers to the ecosystem of card brands (like Visa, Mastercard, AmEx), issuing banks, acquiring banks, processors, and merchants that issue and accept payment cards, along with the security standards (PCI DSS) that protect cardholder data.
What is a PCI compliance audit program?
A PCI compliance audit program is your internal, repeatable approach to staying PCI DSS compliant year-round. It typically includes ongoing control testing, regular vulnerability scans, documented policies, user access reviews, and structured evidence collection so you’re always ready for your next PCI audit or Self-Assessment Questionnaire (SAQ).
Achieve PCI DSS compliance with Hyperproof
As commerce continues to shift to a virtual world, the ability to secure customer data will become critical to the survival of every business. Achieving PCI DSS compliance is just the first step for organizations looking to compete in a digital economy.
Hyperproof’s compliance operations platform is built to help you meet PCI DSS requirements and protect customer data with confidence. Leverage Hyperproof’s pre-built PCI DSS 4.0.1 template from our library of 100+ frameworks to get started quickly, whether you’re completing a Self-Assessment Questionnaire (SAQ) or preparing for a Report on Compliance (ROC).
Avoid duplicative work by automating evidence collection, streamlining documentation, and ensuring auditor requests are handled consistently and on time. Use Hyperproof’s risk register to track assessment results and empower leaders to prioritize mitigation efforts based on real risk data.
With automated task assignments, control testing on a defined cadence, and real-time alerts when something goes wrong, your team can stay ahead of issues and avoid delays. Hyperproof’s analytics-driven dashboards give you visibility into audit readiness, control health, and team progress, and they can be easily shared with stakeholders.
Plus, with the Jumpstart feature, you can map your PCI DSS 4.0.1 controls across other frameworks like ISO 27001, GDPR, and NIST 800-53 which enables you to add new frameworks quickly.
Learn how Hyperproof can streamline your PCI DSS compliance journey and keep your organization audit-ready, always.

See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?