How to Choose the Right Risk Management Software
The volume and complexity of risks today’s organizations face are growing exponentially due to rapidly advancing technology and business mobility as all enterprises look to make a successful digital transformation. Geopolitical turmoil, economic uncertainty, and natural disasters haven’t taken a break, while attack surfaces continue to grow and threat actors exploit vulnerabilities with increasingly sophisticated cyber weapons.
Many organizations aren’t proactively preparing for the worst-case scenario. In Hyperproof’s 2023 IT Compliance Benchmark Report, 20% of surveyed security/compliance professionals (the largest group) said their organization manages IT risk in an ad-hoc fashion and only when a negative event occurs. Not surprisingly, this reactive approach to risk management isn’t working — and even with a recession looming, security and compliance is one area where spend continues to remain high. The report found that 63% of respondents said they will spend more on IT risk management and compliance in 2023, compared to 45% in 2022.
Reliance on outdated, ad-hoc tools for risk management creates severe limitations for today’s organizations. A December 2020 Hyperproof survey of 1000 risk management, compliance, and security pros revealed that 50% of respondents still use spreadsheets to track risks.
Spreadsheets limit an organization’s ability to manage risks: they don’t allow users to map out relationships between risks, controls, and compliance requirements, nor do they let users collect proof of security/compliance measures. Further, they provide minimal data reporting and analysis capabilities to help risk professionals gain actionable risk insights.
If your organization wants to get better at managing risks, you’ve come to the right place. Below, we’ll show you how to create a risk management strategy, the benefits organizations can reap by implementing risk management software, and how to select suitable risk management software for your organization.
Developing a risk management approach

Does your organization have an approach and methodology in place for addressing risk? It’s important you do because risk management software will act as a tool to help implement your approach but it doesn’t replace having a strategy. Make sure you have a risk management strategy before doing research on specific risk management applications.
Not sure how to develop a risk management strategy? Don’t worry — we got you. Start by identifying your organization’s strategic objectives. They will usually form around important themes like corporate growth objectives, personnel plans, or financial objectives. Once you identify these business objectives, you’ll determine how your technology supports the business processes that support these objectives. Once you have an inventory of the technology that supports strategic initiatives and processes, you’ll identify the biggest threats to your mission-critical technologies and processes.
A successful risk management approach will involve developing the necessary security controls to keep all high-risk threats in check, allowing your most important processes to remain functional.
Risk management frameworks can provide a structured guideline for risk management, which helps many organizations be more consistent in their approach from day one. Here are a few well-known frameworks for consideration:
- NIST Cybersecurity Framework: This list of standards, guidelines, and practices designed by the National Institute of Standards and Technology helps organizations better manage and reduce cyber risk. It was compiled using the industry best practices from various documents and standards like ISO 27001 and COBIT 5. This framework helps teams assess risk levels, align on risk tolerance objectives, set improved security priorities, and set a budget for threat mitigation.
- NIST Privacy Framework: This voluntary tool, created by the National Institute of Standards and Technology, can be used by any organization to develop or improve a privacy program. Effective privacy risk programs can help companies increase trust in their products and services, better communicate about privacy practices, and meet compliance requirements.
- Factor Analysis of Information Risk (FAIR) Model: This framework, billed as the premier “Value at Risk framework for cybersecurity and operational risk,” defines risk management as “the combination of personnel, policies, processes, and technologies that enable an organization to cost-effectively achieve and maintain an acceptable level of loss exposure.” The FAIR book discusses more on how to implement this framework model.
- World Economic Forum Cyber Risk Framework and Maturity Model: This framework model was published in 2015 in collaboration with Deloitte. Like the NIST RMF, this framework relies on subjective judgments and examines risk through a “value-at-risk” lens. This lens asks stakeholders to evaluate three components: existing vulnerabilities and defense maturity of an organization, value of assets, and the attacker’s profile.
Regardless of what risk management framework you choose, the end goal here is effective IT governance. You achieve effective IT governance when you can safeguard IT assets to ensure they’re functioning and supporting the achievement of organizational objectives. The best IT governance and risk management happen when your team can link all risks to mitigating controls already in place.
Related: Cybersecurity Best Practices
How risk management software facilitates effective risk management
Risk management software helps you identify, assess, and document risks associated with running various business processes and IT assets, communicate about risks, and efficiently manage risk mitigation tasks. For teams that are heavily focused on cybersecurity, modern cyber risk management software can also help you operationalize a structured cybersecurity risk management process across your environment. While different tools have different capabilities, at a minimum, risk management software allows you to stand up a risk register — a repository of risk information that contains, at the very least, a description of a particular risk, the likelihood of it happening, its potential impact from a cost standpoint, how it ranks overall in priority relative to all other risks, the response, and who owns the risk.
Benefits of risk management software
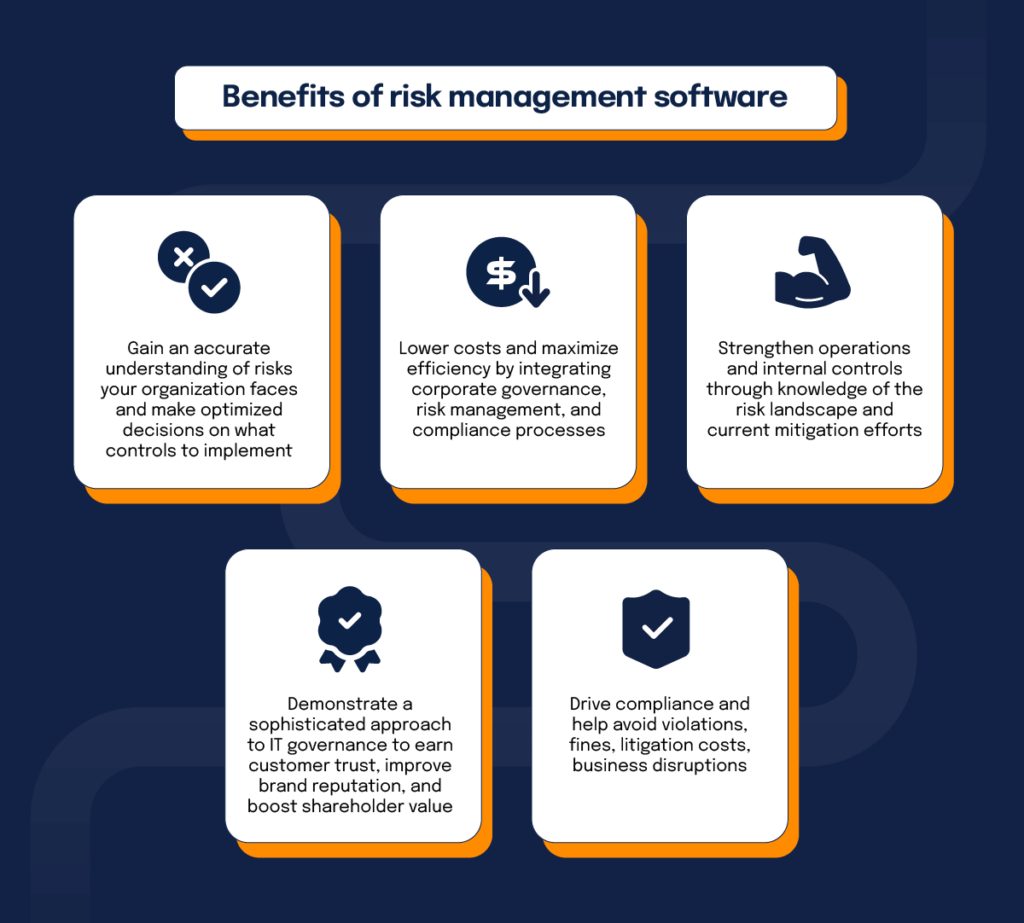
Risk management software provides numerous benefits to organizations looking for help controlling the potential negative impact of risk. If you’re building a business case, our breakdown of the core benefits of risk management software can help you quantify impact and prioritize the right capabilities. Here are some of the more significant benefits risk management software can bring to your business:
- Gain an accurate understanding of risks your organization faces and make optimized decisions on what controls to implement
- Lower costs and maximize efficiency by integrating corporate governance, risk management, and compliance processes
- Strengthen operations and internal controls through knowledge of the risk landscape and current mitigation efforts
- Demonstrate a sophisticated approach to IT governance to earn customer trust, improve brand reputation, and boost shareholder value
- Drive compliance and help avoid violations, fines, litigation costs, business disruptions
Key features of risk management software
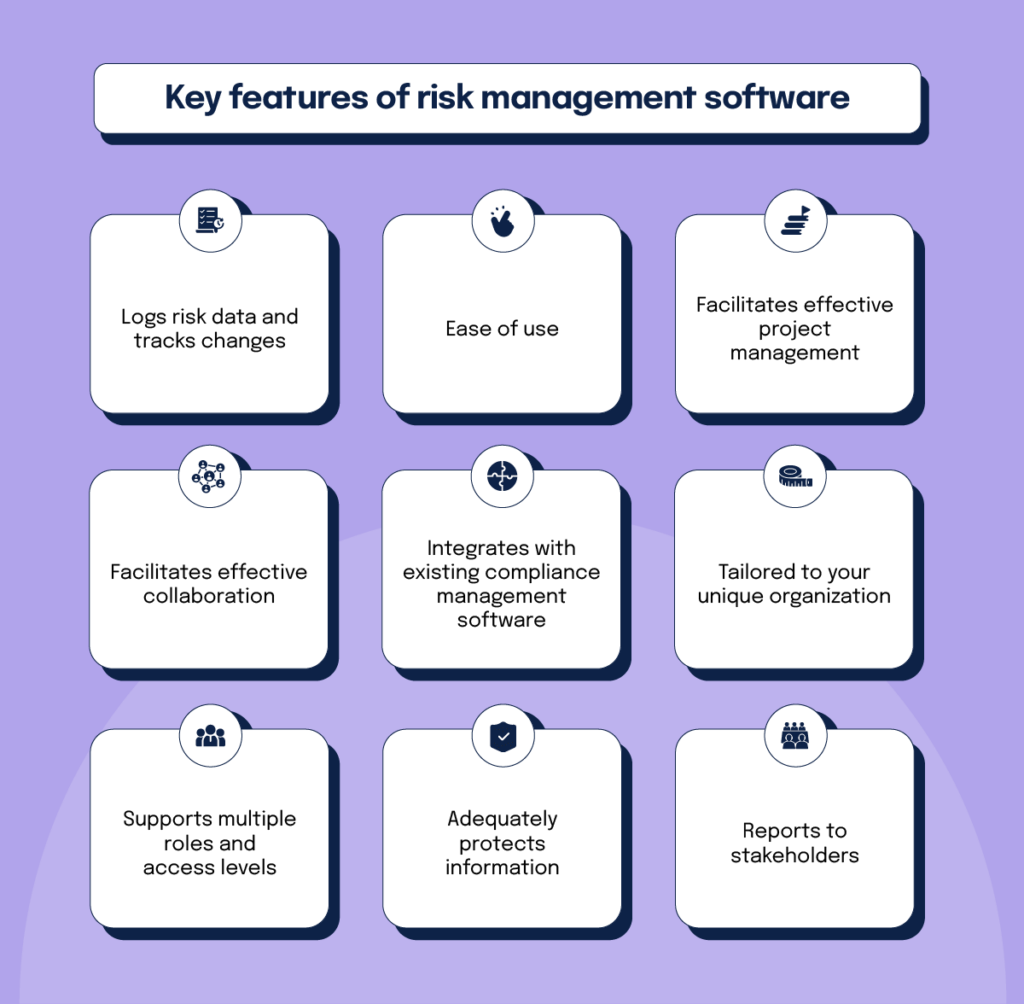
Below is a list of essential features to look for when purchasing risk management software:
Logs risk data and tracks changes: Your software should help document all risks with the appropriate likelihood, tolerance, impact, and response ratings. Your software should also be well equipped to track, record, and display any changes to risk assessment results over time.
Ease of use: The process of creating a risk register should be intuitive and straightforward, starting with the ability to import a list of existing risks in bulk from a spreadsheet or to create new risks one by one.
Facilitates effective project management: Your software should allow you to track and manage risks on a continuous, day-to-day basis and gauge progress over time — something that can’t be done in spreadsheets.
Facilitates effective collaboration: Risk management requires a team effort from stakeholders inside and outside your company. Your software should support this joint effort with collaborative workflows such as reviewing risks and approving the risk treatment plan, issuing tasks to various individuals, and developing questionnaires to assess your vendors’ risk profile.
Integrates with existing compliance management software: It’s crucial to ensure you’re not duplicating your risk management and compliance efforts. Your software should help by linking risks to mitigating controls. Creating a risk register in the same software platform used to track compliance (including activities towards achieving security certifications like ISO 27001) makes gathering evidence of risk management activities much simpler when it’s time for an audit.
Tailored to your unique organization: Your software should allow for easy customization, such as creating specific fields to view risk by different categories, teams, or regions. Also, make sure your software is compatible with the risk management model you want to use and that its risk calculation rules can be adjusted to match your team’s needs.
Supports multiple roles and access levels: Risk information can be confidential, so your software must restrict access to the information included in your risk register. The software you select should support multiple roles and allow you to control access to risk data appropriately.
Adequately protects information: If you’re buying cloud-based risk management software, it’s critical to ensure the vendor has appropriately robust safeguards in place protecting data. Be sure to check whether your third-party software company holds any security compliance certifications like SOC 2 or ISO 27001 for added assurance.
Reports to stakeholders: Boards and senior management need to know your business’s risk profile and how these risks are managed. Your chosen software must facilitate open communication and easy reporting to executive stakeholders. An ideal software solution should provide visual aids to track risks over time, allowing easy identification of trends and drill-down exploration of specific high-risk areas.
3 steps to finding the right risk management software
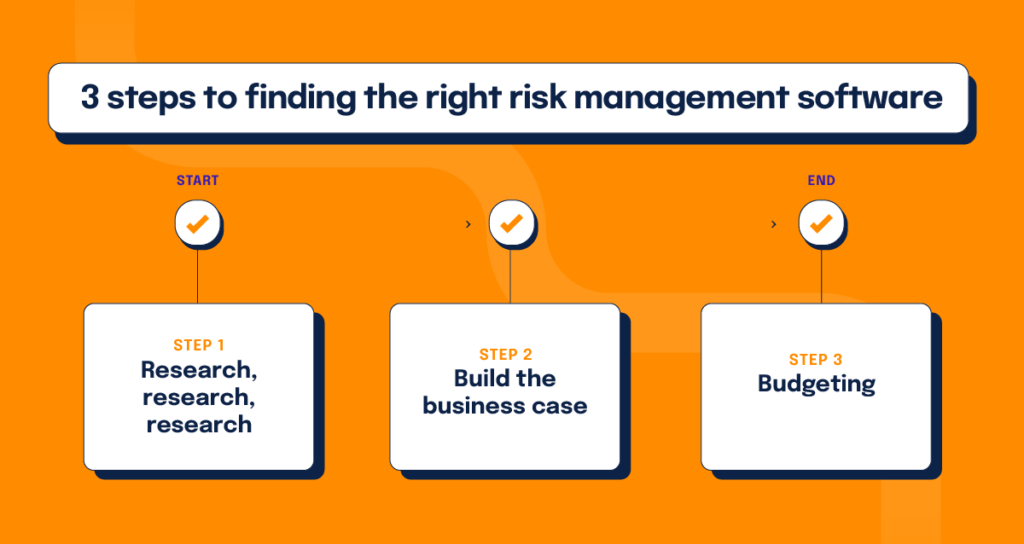
If your team is ready to embrace the many benefits risk management software can provide, it’s time to kick off your evaluation process. Below are the steps we recommend for those looking to make the best decision:
1. Research, research, research: We’ve covered the essential capabilities of risk management. Now it’s time to generate a list of software solutions you want to evaluate based on the capabilities that matter to you and your budget. You’ll also want to identify the key stakeholders who will participate in the evaluation process, such as your CTO, Head of Security, or Head of IT.
2. Build the business case: Your team must build a solid case for the investment by gaining the support and buy-in of upper management. Think about how much time your staff currently spends on manual risk tracking efforts, plus time lost through duplicative risk/compliance efforts due to organizational silos. Then, invite your decision-makers to experience customized demos so they can see the benefits of risk management software firsthand.
3. Budgeting: This last step logically comes after the first two. Research your priorities, check the pricing, then schedule the demo for your top stakeholders. When you select the best choice for your organization’s needs and back it with evidence, the budgeting step becomes much more manageable.
How Hyperproof’s risk management software solution supports your business
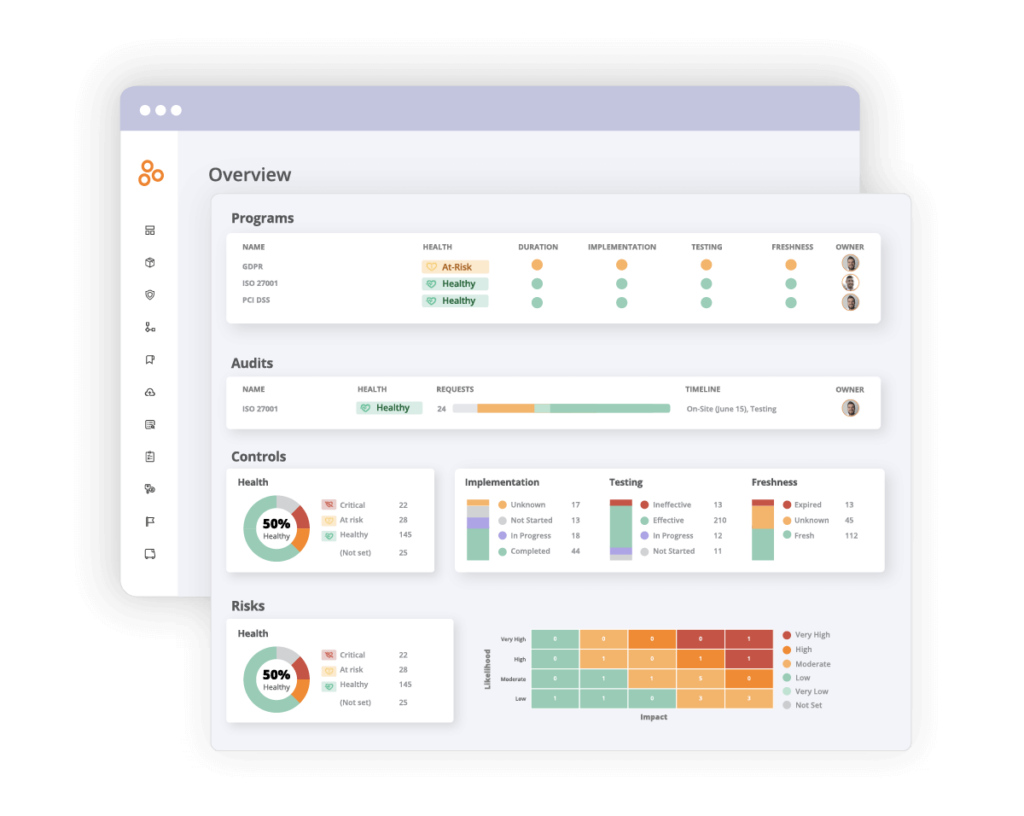
Continually monitoring potential risks, safeguarding data, and remaining compliant in today’s business landscape can prove quite an undertaking even for the most well-heeled organizations. Fortunately, your team doesn’t need to tackle risk management alone. Hyperproof’s risk management software solution can help your business effectively identify, assess, and manage risks on a day-to-day basis in the context of your company’s core mission and objectives. Hyperproof’s platform allows you to maintain a central risk register to track threats and document mitigation plans.
With Hyperproof’s risk management software, no effort or resource is wasted. Users are able to integrate risk management and compliance activities fully, which reduces their workload and prevents repetitive activity. All controls can be mapped to risks and compliance requirements to eliminate the possibility of wasteful redundancy.
With organizations becoming increasingly reliant on third parties to run their business, managing vendor risk has become a significant concern today. Hyperproof’s risk management software gives your team a considerable advantage with a single platform to manage vendor security and compliance posture. The platform provides easy access and control from a central register — holding vendor contracts, customizable risk assessment questionnaires, and documentation of current controls mitigating vendor risk.
Risk management is a topic at the top of everyone’s minds. Take control of your risk management with Hyperproof’s powerful software. Use Hyperproof to identify and prioritize risks, orchestrate and automate risk workflows, create alignment between risk management and compliance activities, and reduce time spent on monitoring risks. Learn more about Hyperproof’s risk management software.
See the benefits of Hyperproof’s Risk Management Solution for yourself

See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











