Risk Management Techniques: Understanding Different Approaches and How to Apply Them
Today, organizations operate in a volatile risk environment with increasing regulations and an uncertain economy. As companies are looking to get serious about risk, more are turning towards risk management techniques and business risk management solutions that explore how technology helps craft a resilient, agile, and strategic risk management program.
Let’s examine what risk management is, the various risk management techniques GRC professionals use, and how technology can help streamline these processes.
The need for risk management techniques
Businesses face a daunting array of challenges, from the volatility of international markets and the unpredictability of political landscapes to the rapid pace of technological change.
Risks cannot be viewed through a narrow lens. Environmental sustainability, cybersecurity, and social governance are just a few broader considerations businesses must incorporate into their risk management techniques. Recognizing and adapting to these evolving risks is essential for organizations aiming to maintain their competitive edge and ensure long-term viability in a world where change is the only constant. Building repeatable documentation and ownership is a best practice in risk management, because it keeps decisions consistent even when teams and tools change. These are all areas of risk management that often overlap, which is why risk programs need shared language and consistent reporting.
Before we dive into risk management techniques, we first need to define risk management.
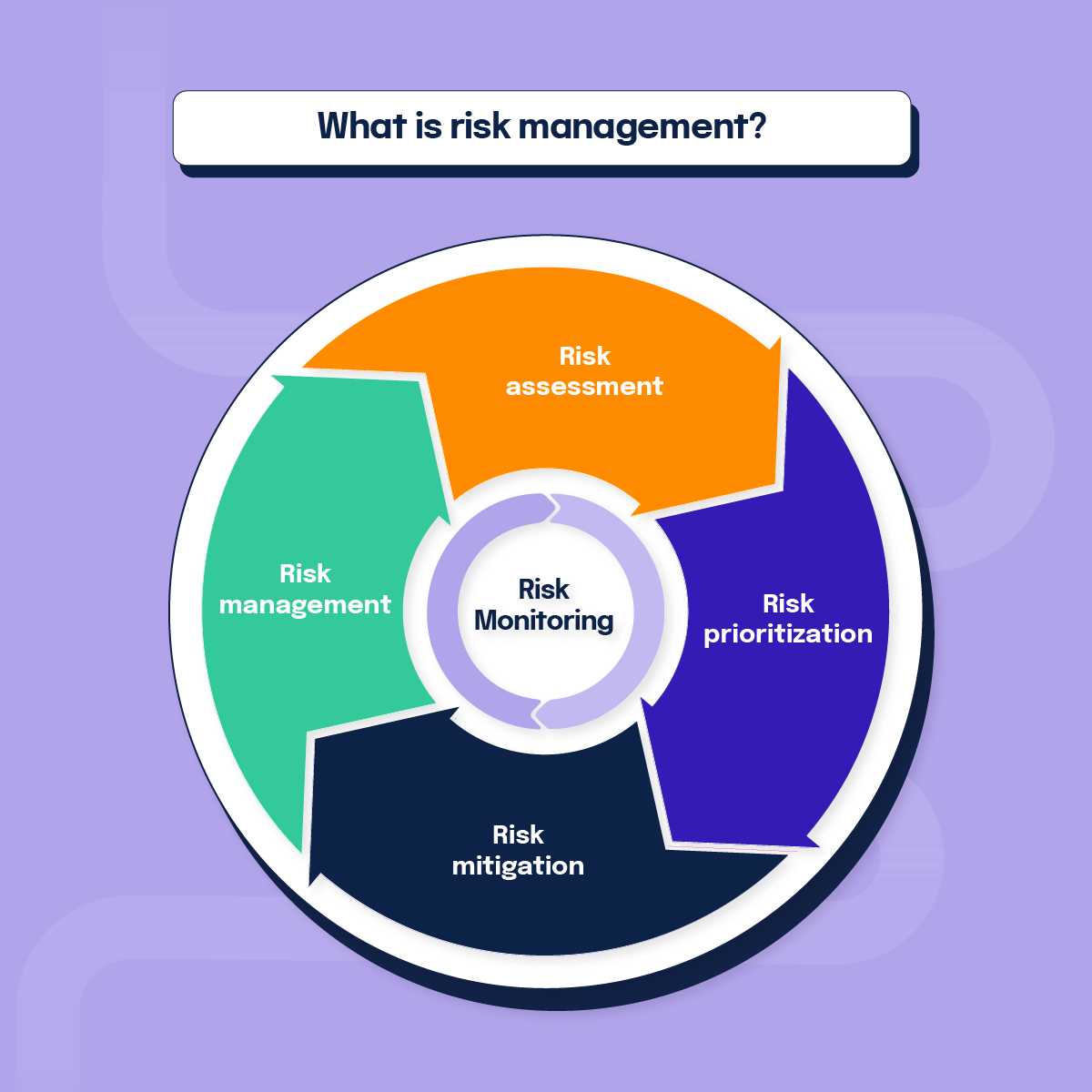
What is risk management?
Risk management is the process of identifying, assessing, and responding to risks that could affect an organization’s objectives. In simple terms, risk management means understanding what might go wrong, how likely it is, and what impact it could have, then deciding how to avoid, reduce, transfer, or accept those risks. It’s a critical part of strategic management because it helps protect assets, support decision-making, and turn uncertainty into opportunity. While definitions are a starting point, true resilience comes from the practical execution of a business risk management process that is integrated into your daily operations. This structured approach helps ensure that every identified threat—from cybersecurity gaps to financial volatility—is documented, assigned an owner, and tracked through to successful remediation. Done well, company risk management turns uncertainty into structured decisions, so leaders can move faster without guessing.
Risk management definition: a systematic approach to identifying, analyzing, prioritizing, and treating risks so an organization can reduce threats and capitalize on opportunities.
Effective risk management is not just about avoiding potential threats; it’s about understanding and embracing risk as an inherent aspect of business, turning potential vulnerabilities into strategic advantages. It is imperative to tie risk to key business KPIs to measure the impact regarding revenue and relevant business decisions.
Defining the different aspects of risk management is vital within your organization. Coming to a consensus on the difference between “high impact financial risk” and “low impact financial risk” and “high probability” versus “medium probability” moves your business forward throughout the risk management process.
What is a risk in risk management?
In risk management, a risk is any uncertain event or condition that, if it occurs, could have a positive or negative effect on your objectives. Most organizations focus on negative risks such as financial loss, operational disruption, regulatory penalties, or damage to reputation, but risk can also represent upside opportunities if managed well.
What is the role of management in risk management?
Management plays a central role in risk management by setting the organization’s risk appetite, aligning risk strategies with business goals, and ensuring adequate resources are available to manage risk. Leaders are responsible for approving policies, assigning ownership for key risks, reviewing risk reports, and making decisions about which risks to avoid, mitigate, transfer, or accept. Their support is critical to embedding risk management into everyday planning and decision-making.
Risk management is a business imperative
Risk management has evolved beyond its traditional defensive role to a strategic function integral to planning and decision-making processes. The strongest programs connect business strategy and risk management so risk conversations happen before major bets, not after incidents.
By aligning risk management strategies with business objectives, organizations can ensure that their risk appetite aligns with their overall vision and goals. This strategic alignment empowers businesses to harness the positive aspects of risk, driving innovation and facilitating growth in an increasingly complex and unpredictable market. Modern corporate risk management strategies aim to enable responsible growth, not just reduce exposure.
Companies should improve their risk management, especially as it becomes more closely tied to top-line revenue acquisition and bottom-line revenue defense. Proper risk management can help unlock these avenues and allow for a more streamlined experience, whether that’s cheaper cyber insurance, fewer lawsuits, or landing and expanding into new markets.
See how you can use Hyperproof to make risk management easier.
What is a risk management technique?
Risk management techniques are systematic approaches or methods used to identify, assess, and mitigate risks associated with various activities, processes, or business decisions. These techniques minimize potential losses and maximize opportunities while ensuring safety, compliance, and operational efficiency.
The multifaceted nature of risks today requires a diverse set of risk management techniques, each tailored to address specific risks and their potential impacts on the organization.
The importance of thorough documentation
Effective risk management means having a well-defined, documented process for the business owner of the risk to avoid situations like:
- Finger-pointing or workplace conflict
- Unnecessary vulnerabilities that lead to breaches
- Confusion about who is responsible for what
Documentation helps us better understand the who, what, where, when, and why of risk management processes, which is essential to risk operations. In other words, clear documentation is the backbone of business risk management procedures, because it defines how risks are logged, escalated, treated, and reviewed. This is where consistent business risk management procedures matter most—without them, your register becomes a list instead of a system.
Key risk management practices
Common risk management practices include creating a formal risk management framework, documenting roles and responsibilities, maintaining a risk register, and regularly reviewing controls. Practical risk reduction examples include improving security controls, training employees to avoid phishing attacks, adding redundancy for critical systems, and buying insurance to transfer high-impact risks. Together, these practices help organizations systematically handle risk instead of reacting ad hoc.
The 4 risk management techniques (with examples)
To keep it practical, we’ll focus on the different kinds of risk management decisions most teams make: avoid, mitigate, accept, or transfer. An example of a risk management strategy is deciding upfront which risks you will avoid entirely, which you’ll reduce with controls, and which you’ll transfer or accept based on tolerance. The four main risk management techniques are:
- Risk avoidance
- Risk mitigation
- Risk acceptance
- Risk transference
“In larger organizations, these decisions need to be standardized across teams, which is why the best risk handling strategies for enterprises usually combine clear ownership, consistent scoring, and repeatable reporting.
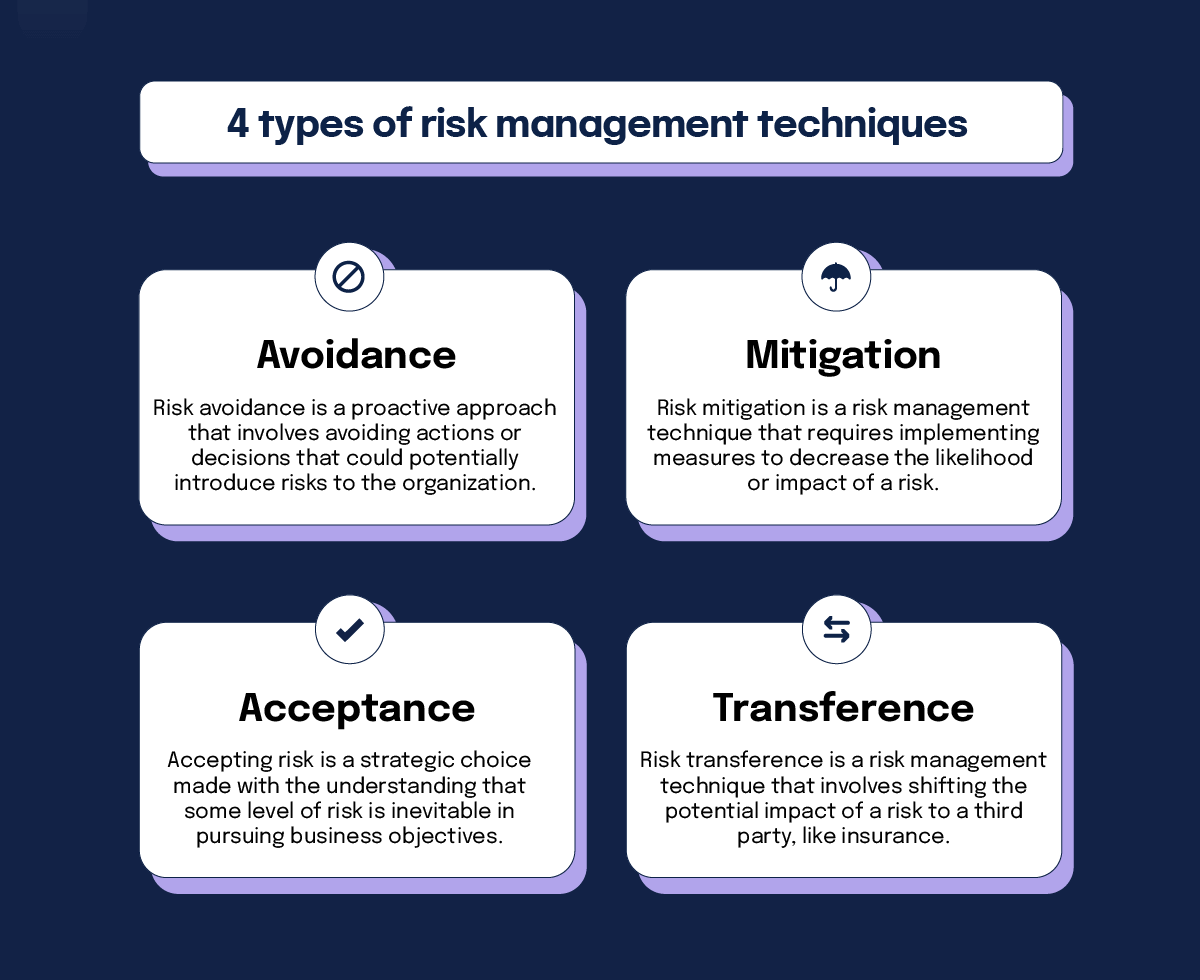
1. Avoidance
Risk avoidance is a risk management strategy where you completely avoid activities that create certain risks. Instead of trying to reduce or transfer the risk, you decide not to engage in the risky activity at all. While this “avoid risk” approach can be effective, it must be balanced against lost opportunities for growth and innovation. Deciding when to avoid risk and engage thoughtfully is a delicate balancing act.
Organizations often employ thorough risk assessments and scenario planning to weigh the costs and benefits of risk avoidance against other risk management techniques. This helps to determine whether risk avoidance aligns with the company’s long-term strategic goals and vision, ensuring that overly conservative approaches do not stifle innovation and progress.
Example of risk avoidance
A multinational technology company is evaluating the introduction of a new data analytics service that would store and process large amounts of personal data from users across many jurisdictions. Early in the planning phase, the legal and compliance teams raise concerns about the complexity and cost of adhering to stringent data protection regulations such as GDPR in Europe, CCPA in California, and similar laws in other regions.
Faced with potential financial penalties, reputational damage from noncompliance, and the high costs of implementing compliant systems globally, the company’s leadership decided to avoid this risk entirely. Instead of launching this new service, they choose to expand their existing services that already have compliance structures in place.
By opting not to proceed with the new service, the company avoids the intricate web of compliance challenges and potential legal troubles, safeguarding its operations and reputation. This strategic choice reflects a conservative approach to risk management, prioritizing the stability and reliability of the company’s services over the uncertain benefits of a new, risky venture.
2. Mitigation
Risk mitigation is a risk management technique that requires implementing measures to decrease the likelihood or impact of a risk. This technique strikes a balance between minimizing risk and maximizing potential gains, ensuring the organization remains resilient and adaptable.
This concept is a core aspect of risk management, which involves identifying potential risks, assessing their magnitude, and taking appropriate actions to mitigate them. Risk mitigation aims to minimize the probability of an adverse event occurring and the severity of its consequences should it occur.
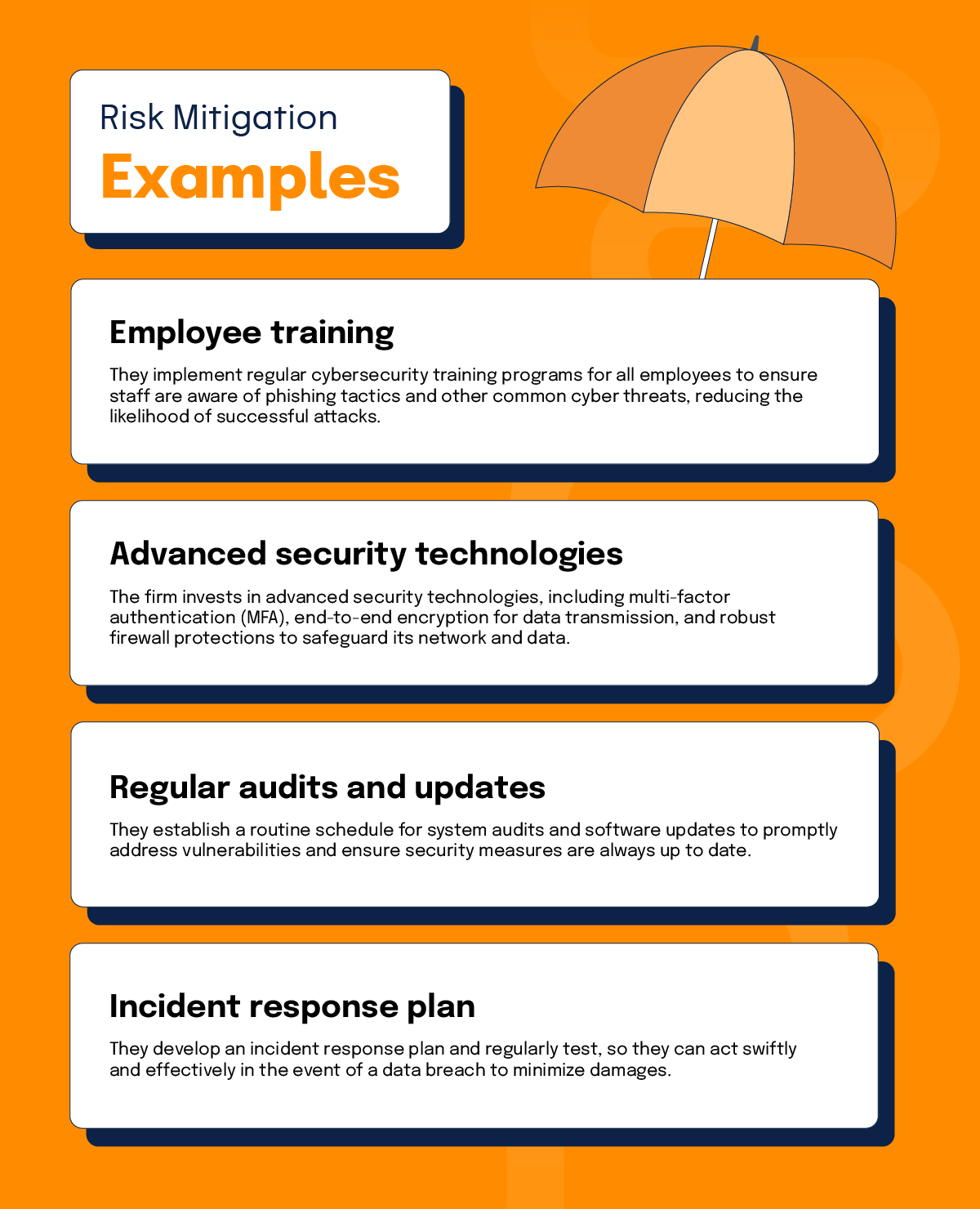
Examples of risk mitigation
Imagine a large financial services firm that handles sensitive client data and transactions daily. Aware of the increasing frequency and sophistication of cyberattacks, the firm identifies cybersecurity as a critical risk area that requires stringent controls.
To mitigate these risks, the company undertakes several initiatives, including:
1. Employee training: They implement regular cybersecurity training programs for all employees to ensure staff are aware of phishing tactics and other common cyber threats, reducing the likelihood of successful attacks.
2. Advanced security technologies: The firm invests in advanced security technologies, including multi-factor authentication (MFA), end-to-end encryption for data transmission, and robust firewall protections to safeguard its network and data.
3. Regular audits and updates: They establish a routine schedule for system audits and software updates to promptly address vulnerabilities and ensure security measures are always up to date.
4. Incident response plan: They develop an incident response plan and regularly test, so they can act swiftly and effectively in the event of a data breach to minimize damages.
By implementing these measures, the firm not only reduces the likelihood of a cybersecurity incident but also diminishes the potential impact on its operations and reputation, should one occur. This comprehensive risk management technique helps maintain client trust and ensures compliance with regulatory requirements.
3. Acceptance
Accepting risk is a strategic choice made with the understanding that some level of risk is inevitable in pursuing business objectives. This approach demonstrates an organization’s confidence in its risk management capabilities and readiness to tackle challenges head-on.
Companies can — and often need — to accept low-probability risks above their risk tolerance. This is especially true when these risks are out of their control; organizations should plan to address them even though the chances of them happening are low.
By consciously accepting certain risks, organizations can harness opportunities that may not have been previously accessible. This allows for potentially greater reward and innovation that can drive competitive advantage. However, this decision typically involves preparations like establishing contingency plans or setting aside financial reserves to manage potential outcomes effectively.
Example of risk acceptance
Take, for example, an enterprise business that uses a specific legacy software system critical to their operations. This system may have known security vulnerabilities that may not be eliminated without a costly and disruptive system overhaul.
After evaluating the risks and benefits, leadership may decide to accept the risk associated with these vulnerabilities. The probability of a security breach may be low, and the cost of maintaining current operations with the existing system is more favorable than upgrading. They continue using the legacy system while increasing monitoring or other compensatory controls.
In this case, accepting the residual risk of a potential security incident outweighs the business costs of upgrading to a new software system, as this would disrupt operations and could lead to revenue loss. This approach allows the company to allocate resources more efficiently according to its risk management priorities and business strategy.
4. Transference
Risk transference is a risk management technique that involves shifting the potential impact of a risk to a third party, like insurance. Another option is to transfer the risk to a vendor or supplier in the company’s supply chain as a contractual vehicle for transferring risk. This risk management technique does not eliminate the risk, but redistributes its potential consequences, allowing the organization to focus on its core competencies.
Effective risk transference typically requires careful contract negotiation and management to ensure the third parties involved are capable and willing to assume the specified risks. Additionally, organizations must continuously monitor and assess the relationships and performance of these third parties to mitigate any new risks that may arise from the transference strategy, like non-compliance or financial instability of the partner.
Example of risk transference
Consider a multinational corporation that operates a complex supply chain with multiple vendors across various countries. Due to its operations’ complexity and global nature, the company faces significant risks related to supply chain disruptions.
The company’s leadership decides that while they can accept minor delivery delays, any disruption that threatens to delay production for more than a month is beyond their risk tolerance. To manage this risk, the company chooses to transfer a portion of the risk to a third party by purchasing a comprehensive supply chain disruption insurance policy. This insurance is designed to cover substantial losses from extended delays, providing financial compensation and support for alternative sourcing strategies if major disruptions occur.
By transferring the risk to an insurer, the company can mitigate potential financial losses exceeding its tolerance threshold while still accepting the day-to-day operational risks of minor supply chain hiccups. This strategic decision allows them to maintain operational resilience and financial stability, aligning with their overall risk management strategy.
Key components of using risk management techniques
In practice, managing risk means following a clear cycle: identify, assess, streamline, prioritize, centralize, mitigate, and monitor your risks.
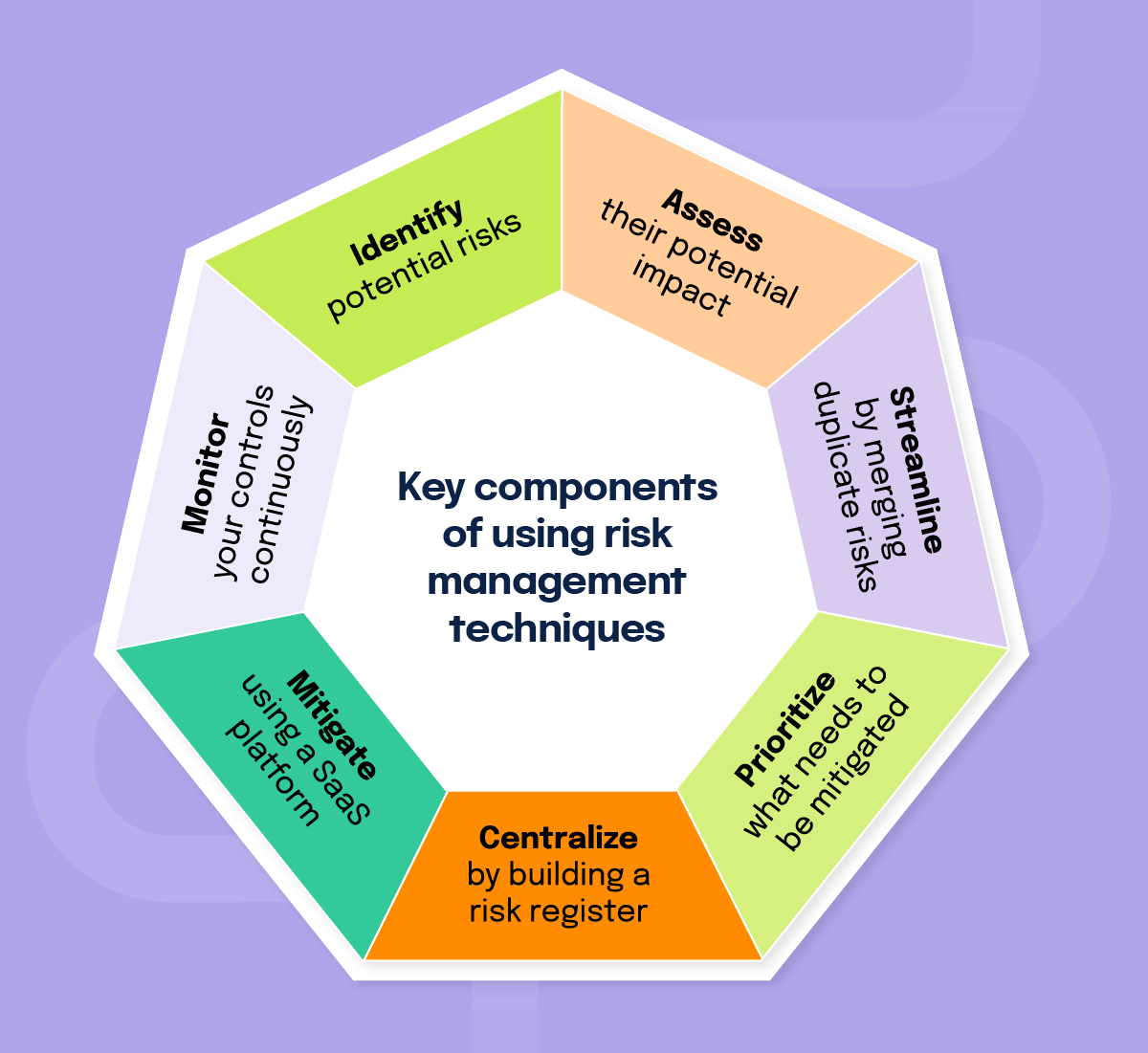
1. Identify
The first step in managing risk is identifying potential risks. One method of doing this is by sending a risk questionnaire to various stakeholders throughout the organization. From there, risk managers can supplement the identified risks with input from third parties — such as experts, consultants, and managed service providers — or simply their own experiences.
Technological advancements have enhanced risk identification. Businesses can better predict and identify risks they may have overlooked by using data analytics, artificial intelligence, and machine learning.
There are tried-and-tested methods for identifying risks, including questionnaires, brainstorming sessions, and interviews with industry subject matter experts. These allow for a better look at what risks exist and need mitigation.
Questionnaires
Questionnaires are essential for identifying risk. Because they can be shared widely across the organization and with various stakeholders, questionnaires allow for more diversified perspectives on the many risks facing a business. This helps the risk management team better understand and identify their risks and how to mitigate them effectively.
Brainstorming
By having your stakeholders map out and brainstorm potential risks, you can supplement your other risk identification processes by enhancing them with first-hand experiences and new ideas. Brainstorming allows you to better understand how various stakeholders perceive your business risks so you can align more strategically with your organization’s objectives.
However, brainstorming only works if there is a structured way of capturing this data. Make sure to create a document and process that centralizes the ideas and captures the crux of what is discussed in the session. Otherwise, this activity can quickly be rendered useless.
Get expert opinions
Expert opinions can be indispensable when it comes to identifying risks. There may be bias or gaps in your identification process, and outside resources allow for diverse perspectives to better prepare you for the next steps in the risk management process.
2. Assess
Once risks have been identified, assessing their potential impact and likelihood is crucial to success. Modern technology offers sophisticated tools for risk assessment, including simulation models and risk matrices, which provide detailed insights into the nature and magnitude of identified risks. To perform a successful IT risk assessment, you will need to assess the impact and likelihood and analyze your internal controls. Your internal controls may be technical and non-technical, so your assessment must be multifaceted.
3. Streamline
During this part of the process, you will merge duplicate risks and remove improbable risks. Once these risks are analyzed, you’ll have a cleaner, more effective risk management process.
4. Prioritize
Additionally, you will need to come to a consensus on what needs to be mitigated. Whether that’s everyone in alignment or a percentage of a certain cohort agreeing on the risks and documentation of them depends on the organization. Most risk management frameworks include this as a formal step to avoid workplace conflict and get stakeholders in agreement on priorities.
5. Centralize
At this step, you will want to build a risk register. Risk registers allow for more streamlined mitigation because everything is held in one central place. This process can be automated and streamlined using software solutions that monitor assessments and provide snapshots of progress, helping you and your team the ability to tackle risks more efficiently.
6. Mitigate
Based on qualitative and/or qualitative assessment of the risks, teams can identify which risks need to be mitigated first and work from there to build a strategy for mitigation. This is made easier with the implementation of certain technologies that offer rich dashboards and risk registers to track risks that need to be mitigated.
The essence of risk mitigation is determining the most appropriate response to each identified risk. Technology plays a pivotal role here by offering solutions that streamline the implementation of mitigation strategies and enhance their effectiveness through real-time monitoring and adjustment. With automatic control testing, you can rest assured that your controls are operating as they should, so you can spend more time testing the manual controls and focus on more strategic work.
7. Monitor
With certain tools, you can implement continuous control monitoring to help give you peace of mind regarding your risk management program. This type of real-time monitoring allows you to rest assured that certain controls are operating as intended so you can better spend your time mitigating risks that require hands-on, manual work.
By monitoring your risks, you enable your organization to stay on top of potential threats to your company’s operations by being proactive. Solutions like Hyperproof offer 24/7 monitoring, with built-in alerts when your controls get off track.
Risk management techniques help expand your company’s horizons
With the right risk management techniques, your organization can continue to unlock new markets and opportunities in your country and worldwide. By bringing efforts together under specific techniques — avoidance, mitigation, acceptance, and transference – you can better focus your efforts and strategically align with your leadership team.
Integrating these techniques into the right software is also an efficiency play, allowing you to save time and resources to tackle risk management and compliance head-on. Expanding your company goes hand-in-hand with risk management, and these techniques and examples can help guide you, your team, and your leadership so the organization can stay secure and prosperous.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












