Understanding the Change Healthcare Breach and Its Impact on Security Compliance
Editor’s note: This post was updated in August 2025
Healthcare ransomware incidents are far too common, but none have wreaked as much havoc as the recent Change Healthcare attack. Rick Pollack, President and CEO of the American Hospital Association stated that “the Change Healthcare cyberattack is the most significant and consequential incident of its kind against the U.S. healthcare system in history.” And congress members have said that “the breach of Change was tantamount to targeting the health care system in its entirety.”
In late February, the ALPHV/BlackCat ransomware gang claimed responsibility for hacking Change Healthcare, a subsidiary of UnitedHealth Group. The intruders disrupted operations and stole up to 6TB of data. The data included personal information, payment details, insurance records, and other sensitive information. This led to a non-verified ransom payment of $22 million.
Change Healthcare plays a pivotal role in managing clinical criteria for pre-authorization, verifying coverage, and processing patient claims to third parties. After the attack, Change Healthcare took key operations offline, but they have rebooted their systems only inconsistently.
The incident jeopardizes the very survival of countless healthcare providers nationwide due to delays in patient care and reimbursement. The hack generated massive economic and legal shockwaves across the U.S. healthcare industry. Everyone from major industry players to small town rural physician practices was impacted.
To make matters worse, reports in April 2024 revealed that another ransomware group called RansomHub was extorting Change Healthcare. They claimed to own sensitive data stolen from the breach.
How has this unprecedented cyber attack impacted security compliance? Let’s find out.
Who is Change Healthcare and what do they do?
For patients and providers suddenly caught up in this incident, a common question has been, “who is Change Healthcare and what do they do?” and “Change Healthcare – what is it?” Change Healthcare is a large healthcare technology and payments company (now a subsidiary of UnitedHealth Group) that sits in the middle of the U.S. healthcare system. It routes eligibility checks, prior authorizations, claims, and payments between providers, payers, and pharmacies.
Because of that central role, when there is a Change Healthcare issue or outage, it doesn’t just affect one hospital or insurer – it can ripple across the entire ecosystem, delaying prescriptions, claims processing, and reimbursements nationwide.
A timeline of the Change Healthcare attack

February 21, 2024
Change Healthcare detects a cyber attack. The company makes an announcement, disconnects networks, and takes operations offline.
February 22, 2024
Hospitals, health systems, and pharmacies report disruptions from the attack.
February 26, 2024
Ransomware group BlackCat claims responsibility for the attack.
February 27, 2024
The Department of Health and Human Services (HHS) warns hospitals to be wary of BlackCat hackers.
February 29, 2024
Change Healthcare confirms BlackCat is behind the attack. BlackCat claims to have stolen 6TB of data from Change Healthcare. The data included patient Social Security numbers, medical records, and information on active military personnel.
March 1, 2024
Optum introduces a temporary assistance program for providers without adequate cash flow due to the attack.
March 3, 2024
BlackCat receives an unconfirmed bitcoin payment worth $22M.
March 4, 2024
The AHA deems Change Healthcare’s temporary funding program for affected providers inadequate. US Senate Majority Leader Chuck Schumer asks Change Healthcare to speed up payments to hospitals. Large health systems lose more than $100M a day due to interruptions.
March 6, 2024
At least five federal lawsuits are filed against Change Healthcare’s parent company, UnitedHealth Group, over the cyberattack.
March 8, 2024
The AHA says it will take several weeks (or months) before hospitals and other healthcare organizations can fully recover from the attack.
March 13, 2024
The federal government initiates an investigation into UnitedHealth and Change Healthcare regarding HIPAA compliance in light of the cyberattack.
March 15, 2024
Change Healthcare’s electronic payments platform resumes operations, with payer implementations in progress. A survey conducted by the AHA reveals that nearly 94% of hospitals have experienced financial repercussions from the cyberattack.
March 18, 2024
UnitedHealth Group discloses that it has disbursed over $2B to healthcare providers and is rolling out new software to streamline medical claims preparation. The company successfully reinstates 99% of its pharmacy network services.
March 22, 2024
Senator Mark Warner (D-Va.) introduces a bill proposing cybersecurity-related conditions for Medicare accelerated and advance payments during cyberattacks.
April 4, 2024
Change Healthcare asks a U.S. court panel to consolidate at least 24 class actions accusing the payment processor of failing to protect personal data from February’s cyber hack.
April 8, 2024
Senators Josh Hawley (R-MO) and Richard Blumenthal (D-CT), send a letter to UnitedHealth Group Chief Executive Officer Andrew Witty demanding answers about the attack.
April 16, 2024
Reports surface that a relatively new ransomware group – RansomHub – issued a demand stating it had acquired the stolen data from a former ALPHV affiliate. RansomHub demands payment to stop the data leak, and leaked screenshots which appear to include Change Healthcare data and patient files. The group claims it will sell the stolen data to the highest bidder if Change Healthcare and UnitedHeath refuse to negotiate payment.
June 2024
A judicial panel consolidated over 50 lawsuits related to the breach into one case in Minnesota, emphasizing the widespread legal consequences of this breach.
June 11, 2024
HITRUST sends a letter to U.S. Congress and Regulatory members to express their support for the efforts to address the attack. The letter lobbies Congress to “view the problem as a matter of risk management with a focus on selecting and using relevant controls that are threat-adaptive, and ensuring that compliance outcomes, where needed, are earned through robust and reliable assurance programs.”
Read the full letter from HITRUST
July 2024
The total response cost of the breach rises to $2.3-2.45 billion, including over $9 billion in advanced payments to providers.
July 19, 2024
Change Healthcare files a breach report with OCR identifying approximately 500 individuals affected. Affected individuals started to be notified.
July 31, 2024
Change Healthcare reports the breach to HHS.
September 19, 2024
Numerous lawsuits are filed as a response to the Change Healthcare cyberattack and data breach. Facing the challenge of defending multiple cases across various districts, Change Healthcare submitted a motion to the U.S. Judicial Panel on Multidistrict Litigation (JPML), seeking to transfer and centralize all related actions.
October 17, 2024
The cost of the Change Healthcare ransomware attack has risen to $2.457 billion, according to UnitedHealth Group’s Q3, 2024 earnings report.
October 30, 2024
Change Healthcare hires a new CISO, Tim McKnight, as their former CISO, Steve Martin, steps into a new role as Chief Restoration Officer.
January 24, 2025
OCR is notified by Change Healthcare that 130 million notices were sent to individuals regarding this breach and 190 million individuals have been impacted.
July 31, 2025
Change Healthcare notifies OCR that 192.7 million individuals have been impacted by the breach.
Taken together, this timeline answers a few of the most common questions people still search for: “when did the Change Healthcare breach happen?” and “when did Change Healthcare go down?” The initial Change Healthcare cyber attack was detected on February 21, 2024, and core systems were taken offline that same day. While many services were brought back online over the following weeks and months, the financial, legal, and compliance fallout has continued well into 2025 – so for anyone asking “Change Healthcare cyber attack, when will it be fixed?”, the technical outage window was relatively short, but the downstream impact has been anything but.
Unprecedented collateral damage
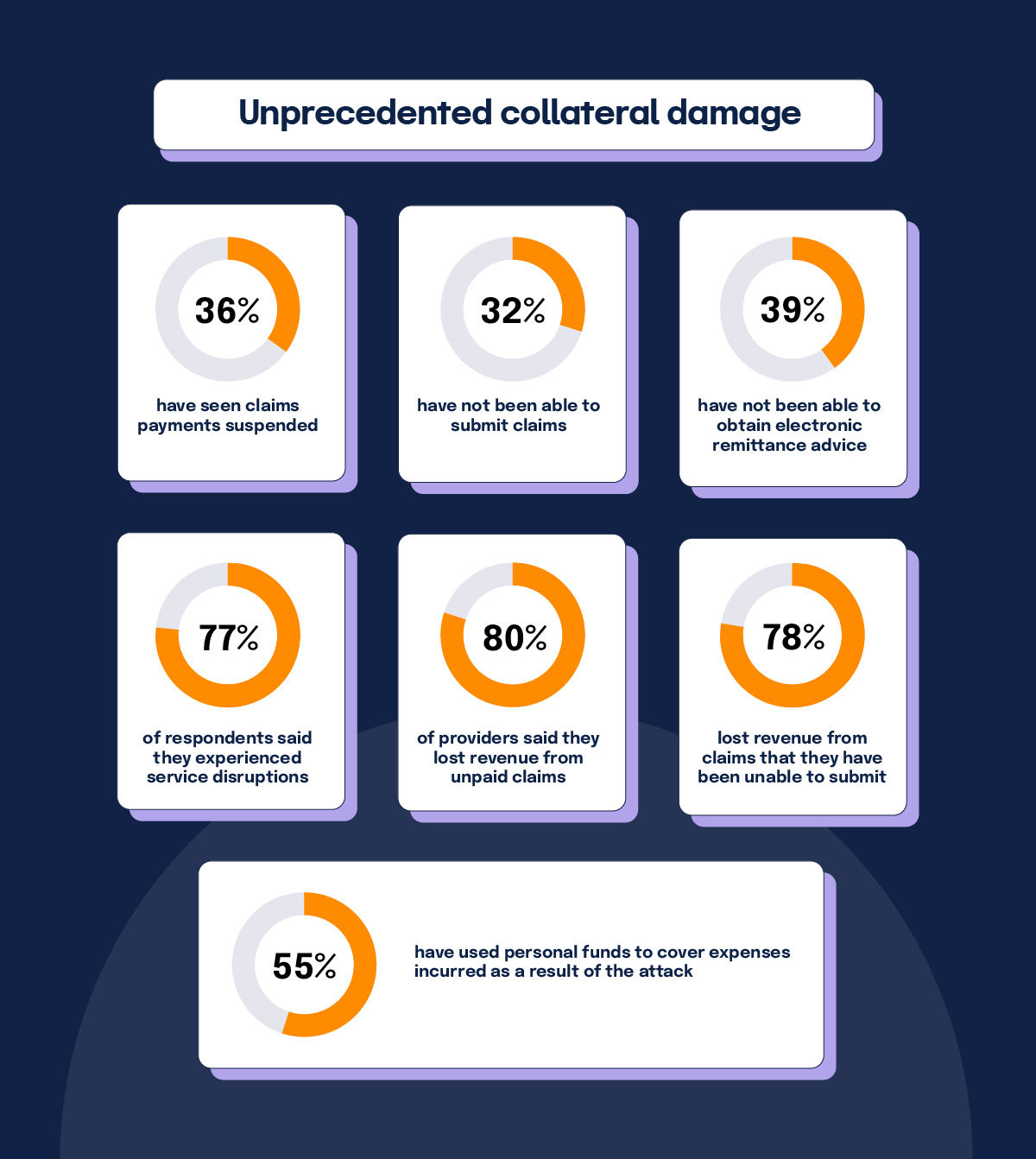
A survey conducted by the American Medical Association (AMA) revealed a wide blast radius due to the Change Healthcare breach. The numbers speak for themselves in percentage of surveyed practices affected:
- 36% have seen claims payments suspended
- 32% have not been able to submit claims
- 39% have not been able to obtain electronic remittance advice
- 77% of respondents said they experienced service disruptions
- 80% of providers said they lost revenue from unpaid claims
- 78% lost revenue from claims that they have been unable to submit
- 55% have used personal funds to cover expenses incurred as a result of the attack
Nearly half of respondents said they’ve been forced to enter new (and potentially costly) arrangements with alternative clearinghouses to conduct electronic transactions. While some practices have received advance payments, temporary funding assistance, and loans, issues persist with all of those measures. Meanwhile, UnitedHealth Group said it’s paid out more than $2B to help health-care providers who have been affected by the cyberattack.
The survey also quoted affected physician practices. Their words reveal the pain being felt across the country:
- “This cyberattack is leading me to bankruptcy, and I am just about out of cash”
- “SOOOO much overtime dealing with this. Cost me an additional $50,000 in payroll.”
- “…estimated $100,000 in unexpected costs.”
- “This crippled our brand new practice. I am keeping the lights on using personal funds.”
- “I have not taken a salary for a month and am borrowing from personal funds to keep practice going.”
- “…may bankrupt our practice of 50 years in this rural community…”
For many patients, the Change Healthcare data breach surfaced less visibly – in the form of confusing billing delays, unexpected balances, or letters explaining that their information may have been exposed. Those downstream experiences are a big part of why so many people are now searching “Change Healthcare data breach what to do” and trying to understand the real-world impacts of this event.
OCR investigation underway
The widespread damage of the ransomware attack prompted the Office for Civil Rights (OCR) at the Department of Health and Human Services to open a HIPAA compliance investigation of Change Healthcare.
In a “Dear Colleagues” letter, OCR Director Melanie Fontes Rainer said, “[W]e are reminding entities that have partnered with Change Healthcare and UHG of their regulatory obligations and responsibilities, including ensuring that business associate agreements are in place and that timely breach notification to HHS and affected individuals occurs as required by the HIPAA Rules.”
This is an usual move by the OCR, but “the breach warrants swift investigation to determine if Change Healthcare and its parent company were fully compliant with the HIPAA Rules,” commented Steve Alder, Editor-in-Chief, The HIPAA Journal.
As of July 2024, OCR has intensified its investigations and has been issuing substantial HIPAA penalties across the healthcare sector. OCR has reminded healthcare entities to ensure Business Associate Agreements (BAAs) are updated and compliant and to provide timely breach notification to HHS and affected individuals as required by HIPAA.
What about HITRUST?

Long before the recent attack, Change Healthcare had earned HITRUST certification status for its enterprise infrastructure and Change Healthcare Platform. The company’s website says, “HITRUST Risk-based, 2-year (r2) Certified status demonstrates that the organization’s major implemented systems and platforms have met key regulations and industry-defined requirements and is appropriately managing risk. This achievement places Change Healthcare in an elite group of organizations worldwide that have earned this certification.”
HITRUST not only provides comprehensive security controls and data security improvement, it’s not only guaranteed way to achieve HIPAA compliance, but also viewed by many as the most robust path to demonstrating HIPAA compliance – which is a key reason organizations affected by the Change Healthcare issue are re-evaluating their own assurance programs.
HITRUST not only provides comprehensive security controls and data security improvement, it’s also the only guaranteed way to achieve HIPAA compliance. In the wake of the Change Healthcare incident, many organizations are scrambling to adopt the HITRUST framework, and for good reason. The HITRUST 2024 Trust Report revealed the HITRUST Assurance Program™ dramatically reduces information breaches, resulting in incredibly low occurrence of breaches — just 0.64%.
The HITRUST framework is widely accepted as a gold standard for compliance, and it’s currently unclear how Change Healthcare may not have fully complied with HITRUST procedures and recommendations. All this has lawmakers posing serious questions to the healthcare service provider.
Need to get HITRUST certified? Whether it’s r2, i1, or e1, Hyperproof can help.

Lawmakers want to know how and why the Change Healthcare breach happened
On April 1, Senators Josh Hawley (R-MO), ranking member of the Senate Judiciary Subcommittee on Privacy, Technology and the Law, and Subcommittee Chair, Richard Blumenthal (D-CT), wrote a scathing letter to UnitedHealth Group Chief Executive Officer Andrew Witty demanding information about the attack. Lawmakers have also signaled continued interest in the role of UnitedHealth’s leadership and the CEO Change Healthcare in overseeing cyber risk at such a critical piece of national infrastructure.
The letter states that, “While we recognize that UHG was indeed the victim of an outside attack, the entire sector is now the victim of UHG’s lack of preparedness and built in redundancies, which could have potentially mitigated the widespread impact of the breach.”
The senators stated that Change Healthcare was part of U.S. healthcare critical infrastructure processing 15 billion transactions and $1.5T in healthcare claims annually. The company handled as many as one of every three patient records in the country. From the senators’ point of view, “The result of UnitedHealth Group’s failure to properly safeguard against cyber threats and the subsequent, extended outage of its services has been dire.”
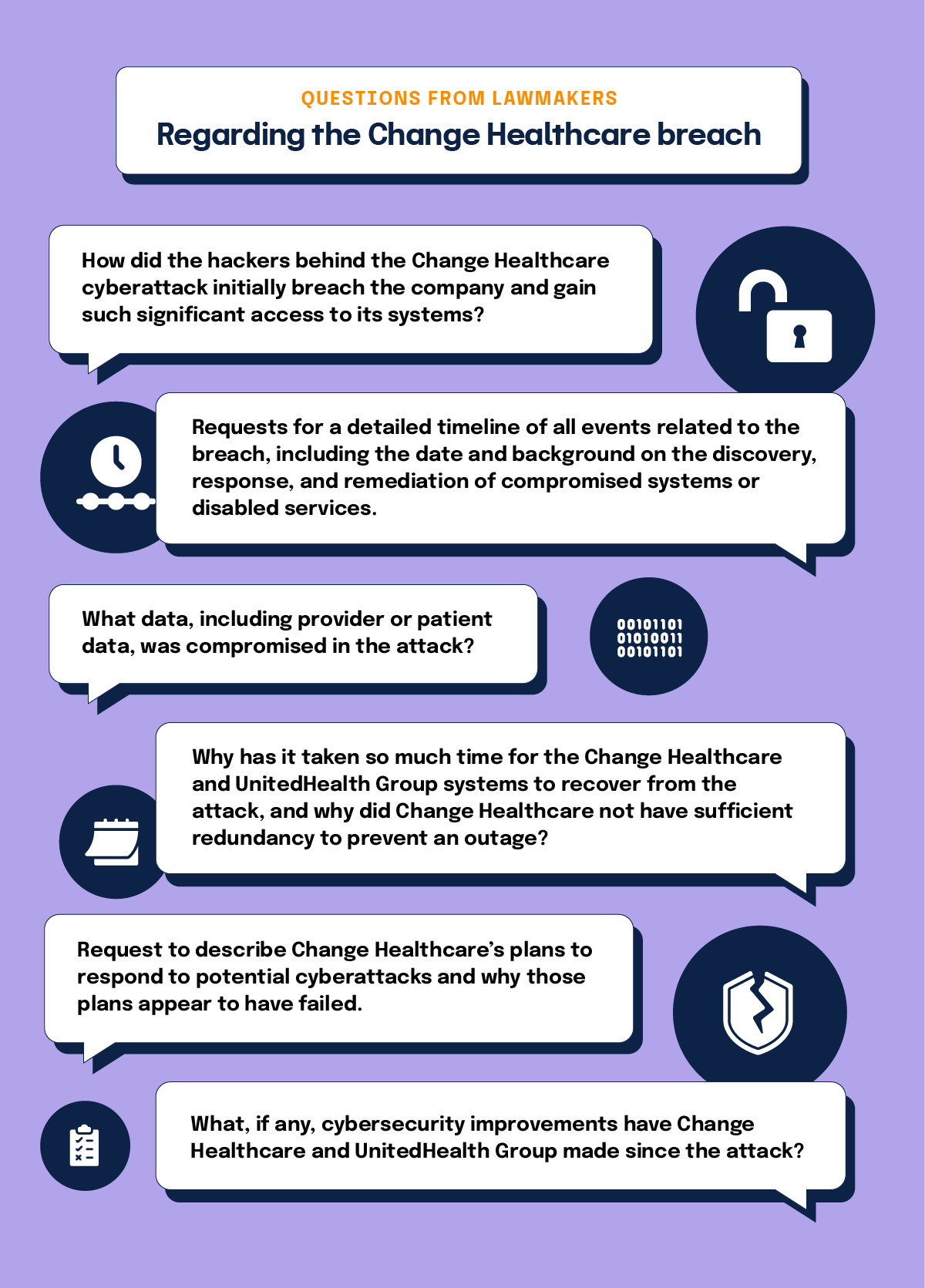
Some questions being posed to the company by the lawmakers include:
- How did the hackers behind the Change Healthcare cyberattack initially breach the company and gain such significant access to its systems?
- Requests for a detailed timeline of all events related to the breach, including the date and background on the discovery, response, and remediation of compromised systems or disabled services.
- What data, including provider or patient data, was compromised in the attack?
- Why has it taken so much time for the Change Healthcare and UnitedHealth Group systems to recover from the attack, and why did Change Healthcare not have sufficient redundancy to prevent an outage?
- Request to describe Change Healthcare’s plans to respond to potential cyberattacks and why those plans appear to have failed.
- What, if any, cybersecurity improvements have Change Healthcare and UnitedHealth Group made since the attack?
The larger security compliance backdrop

As the fallout from the Change Healthcare breach continues, coincidentally, the Cybersecurity and Infrastructure Security Agency (CISA) recently published a draft of landmark regulation outlining how organizations will be required to report cyber incidents to the federal government.
CISA’s 447-page Notice of Proposed Rulemaking (NPRM) is now open for public feedback through the Federal Register. According to the NPRM, covered critical infrastructure organizations, such as healthcare, will be required to report incidents within 72 hours after a cyberattack has occurred. Ransomware payments must be reported within 24 hours of being made. However, if payment is accompanied by an incident, the organization has 72 hours to comply with reporting.
CISA was tasked to develop the NPRM by the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA). With this document, CISA aims to enhance the government’s capacity to monitor incidents and ransomware payments. CIRCIA intends to enable a coordinated, informed U.S. response to the foreign governments and criminal organizations conducting these attacks.
Common Questions about the Change Healthcare breach (for patients and providers)
Although this article focuses on security compliance, patients and providers are asking very practical questions about the incident as well. Here are brief, high-level answers to some of the most common queries.
Is Change Healthcare a scam? Is Change Healthcare a legitimate business / legit company?
Change Healthcare itself is not a scam; it is a large, long-standing healthcare technology and claims-processing company that now operates under UnitedHealth Group. That said, major incidents like this often attract scammers who impersonate well-known brands. If you see messages claiming to be from Change Healthcare and you’re wondering “is Change Healthcare legitimate?” or “is Change Healthcare a legitimate business?”, always verify through official channels (your health plan portal, your provider’s office, or the company’s official website) before sharing any personal information.
Is the Change Healthcare data breach legitimate? Is my Change Healthcare data breach letter legit?
The Change Healthcare data breach is real and has been reported to the U.S. Department of Health and Human Services. However, scammers may send fake notifications that look similar to the real thing. If you receive a Change Healthcare data breach letter and you’re unsure whether the Change Healthcare data breach letter is legit, don’t use the phone numbers or links printed in the letter. Instead, go to your health plan’s official site or member portal, or call the customer service number on your insurance card to confirm whether you were affected.
Change Healthcare data breach: what to do now?
If you believe your data may have been involved and you’re wondering “Change Healthcare data breach, what do I do?”, typical best practices after any healthcare or financial breach include:
- Watching your explanation of benefits (EOBs) and medical bills for services you don’t recognize.
- Monitoring bank and credit-card statements for unusual charges.
- Taking advantage of any free credit monitoring or identity-protection services offered in official notices.
- Considering a fraud alert or credit freeze with the major credit bureaus if you see suspicious activity.
- Contacting your providers or insurer if you spot claims you didn’t authorize.
Is there a class action lawsuit against Change Healthcare?
Multiple lawsuits – including class actions – have already been filed and, as noted earlier, many have been consolidated into multidistrict litigation. If you’ve received notice about a case and are asking “is there a class action lawsuit against Change Healthcare?”, the answer is yes; but whether you should participate is a legal question. Individuals should consult their own attorney or legal aid resources for advice tailored to their situation.
How do I contact Change Healthcare? What is the Change Healthcare contact number or address?
For safety, avoid relying on contact details you find in random emails, texts, or social posts. If you’re asking “how do I contact Change Healthcare?”, “Change Healthcare contact number,” or “Change Healthcare address,” the safest approach is to:
- Use the contact information listed on your health plan’s member portal or insurance card, or
- Visit the official UnitedHealth Group or Change Healthcare website by typing the URL directly into your browser (not by clicking through ads or unsolicited links).
That way, you’re sure you’re using a legitimate Change Healthcare contact channel or Change Healthcare number, rather than calling a spoofed line set up by a scammer.I
Is Change Healthcare a scam if I get a call out of the blue?
Unsolicited calls, emails, or texts asking you to “confirm” Social Security numbers, payment card details, or login credentials should always be treated with suspicion – even if the caller claims to be from a well-known company. If someone contacts you unexpectedly and you’re asking “is Change Healthcare a scam in this situation?”, hang up and call back using a trusted number you looked up yourself. This simple step dramatically reduces your exposure to phishing and social-engineering attacks.
Where does healthcare security compliance go from here?
As the saga of the Change Healthcare cyber attack continues, the overall impact on the industry remains to be seen. Undoubtedly, the company will conduct damage control for some time as well as in-depth forensic investigation into the exact vulnerability that was exploited in the attack. Meanwhile, the healthcare industry will likely increase its reliance on certifications like HITRUST.
The massive scale of the Change Healthcare incident invites the entire sector to do some serious soul searching. If an organization with such a large footprint was hacked, leading to historical levels of damage, what measures should be implemented to prevent future incidents? Perhaps Red Team testing — where cyber teams act as attackers to find vulnerabilities — will rise in demand. One can only imagine how this would impact the cost of security. Either way, faithfulness towards compliance will undoubtedly become even more of a priority.
Security has increasingly become a central player in business decision making. Still, many CEOs seem to have been hedging their bets, either through cyber insurance plans or simply minimizing the problem to their peril. But due to the damage resulting from the Change Healthcare incident, cyber might catapult to become the most important issue in the hearts and minds of business leaders today.
In the aftermath of the Change Healthcare cyber attack, the government campaign for stricter compliance will take on even more importance. We can expect more stringent regulation, tighter controls, and stiffer penalties for non-compliance, which comes as no surprise as the stakes have never been higher – for regulators trying to oversee systemic risk, for providers struggling to stay open, and for individual patients simply trying to verify whether a Change Healthcare contact or Change Healthcare number in front of them is truly safe to trust.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?