ISO 27001 Certification: A Detailed Guide on How to Get Certified
Editor’s note: This blog post is an excerpt from our eBook, Getting to Know the ISO 27001 Standard: Practical Guidance for Achieving ISO 27001 Certification.
What makes ISO 27001 certification compelling and desirable? A business that is ISO 27001 certified has invested significant time and resources in information security, and their clients and partners can be certain they’re doing business with an organization that takes security seriously.
ISO/IEC 27001 is an information security standard designed and regulated by the International Organization for Standardization, and while it isn’t a legally mandated framework, it is the price of admission for many B2B businesses and is key to securing contracts with large companies, government organizations, and companies in data-heavy industries.
This standard is notable because it is an all-encompassing framework. It’s not restricted to one type of personal data or even to electronic data; it includes standards for everything from HR data security to client data to physical entry controls and security of loading and delivery areas.
Related: Guide to ISO 27001
Becoming ISO 27001 certified
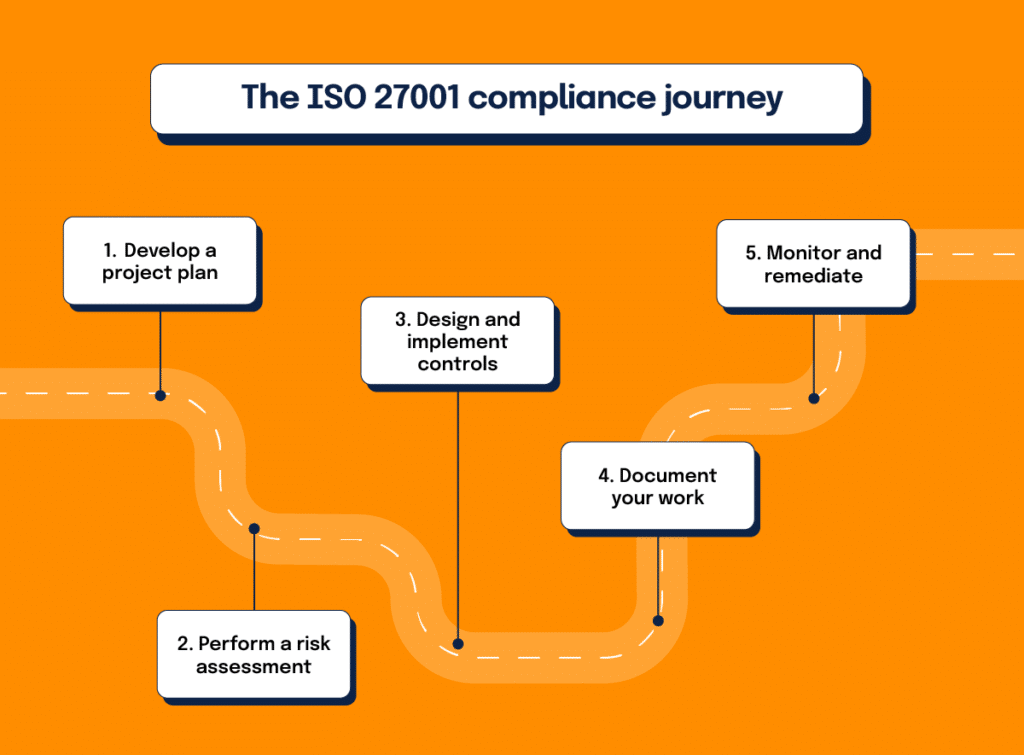
Becoming ISO 27001 certified isn’t quick or easy; the length of time it takes varies from organization to organization and depends on a lot of different factors. Conservatively, businesses should plan on spending around a year to become compliant and certified. The compliance journey involves several key steps, including:
1. Develop a project plan
It’s important to treat your ISO 27001 initiative as a project that needs to be managed diligently.
2. Perform a risk assessment
The objective of the risk assessment is to identify the scope of the report (including your assets, threats and overall risks), build a hypothesis on whether you’ll pass or fail, and build a security roadmap to fix things that represent significant risks to security.
3. Design and implement controls
These controls should be based on your security roadmap.
4. Document what you’re doing
During an audit, you will need to provide your auditor documentation on how you’re meeting the requirements of ISO 27001 with your security processes, so he or she can conduct an informed assessment.
5. Monitor and remediate
Monitoring against documented procedures is especially important because it will reveal deviations that, if significant enough, may cause you to fail your audit. Monitoring gives you the opportunity to fix things before it’s too late. Consider monitoring your last dress rehearsal: Use this time to finalize your documentation and make sure things are signed off.
Additional resource: How to Perform a Successful IT Risk Assessment
What to expect in an ISO 27001 compliance audit

Once you have gone through these key steps, it is time to go through the audit itself. There are three parts to an ISO 27001 compliance audit:
Stage 1
A review of the information security management system (ISMS) that makes sure all of the proper policies and controls are in place.
Stage 2
A review of the actual practices and activities happening inside your business that ensures they’re in-line with the requirements and the written policies.
Stage 3
Ongoing compliance efforts, which include periodic reviews and audits to ensure the compliance program is still in force.
In this guide, we will help you understand the requirements within ISO 27001 as well as the controls you need to implement to satisfy those requirements. You can use this guide as a tool to understand what controls you already have within your organization and identify the additional controls you’ll need to create and implement to become fully compliant and achieve the certification.
Download your copy here.
Determining the scope
Before you begin putting controls into place, you need to determine which areas of your business will be within the scope of your Information Security Management System (ISMS). Each business is unique and houses different types and amounts of data, so before building out your ISO compliance program, you need to know exactly what information you need to protect.
Information security should be about doing business more securely, not simply ticking boxes. You want to understand the internal and external issues that affect the intended outcome of the information security management system and what the people invested in your ISMS want and need from ISO 27001 compliance. The first control domains in ISO 27001—4.1 and 4.2—outlines your ISMS’ scope, which we’ll discuss more in the next section.
Once you’ve determined the relevant issues and interested parties, you have the building blocks to address clauses 4.3a-c: recording the scope of your ISMS. This is a crucial first step, because it will tell you exactly what you need to spend time on and what isn’t necessary for your business.
Understanding the ISO 27001 control families
4. Context of the organization
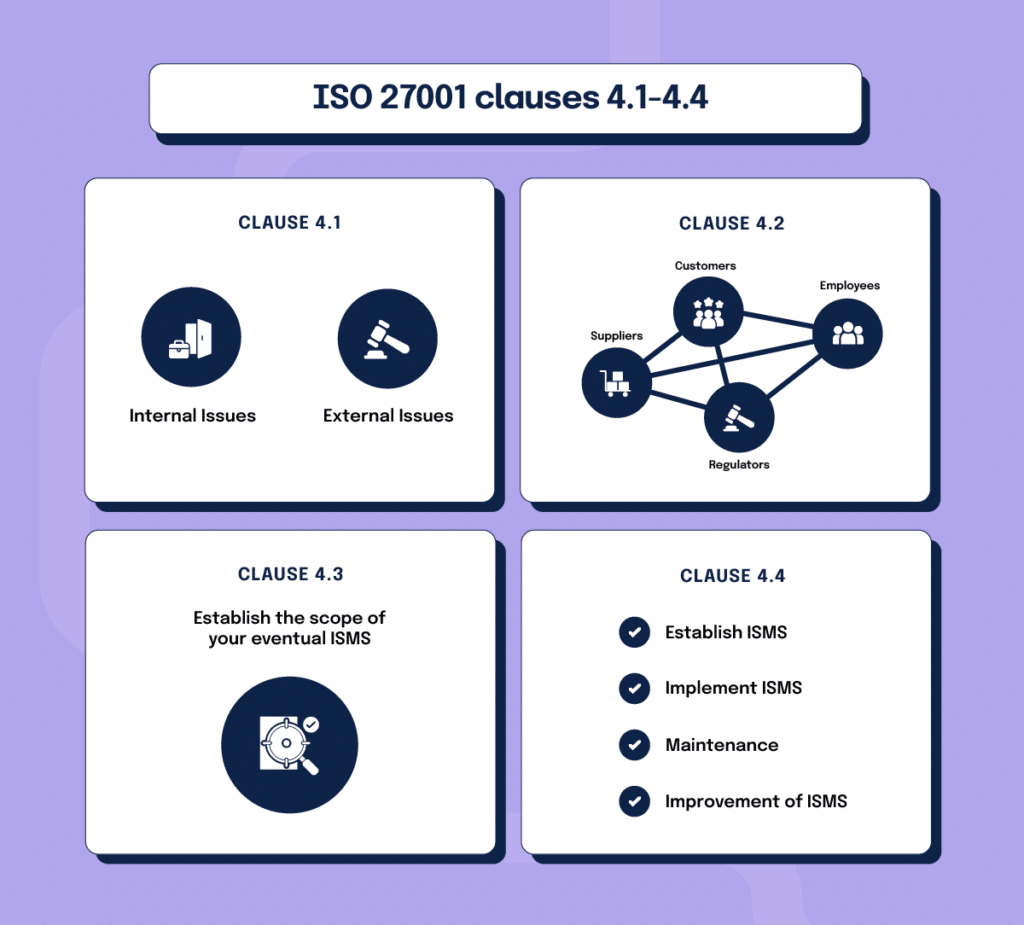
The first requirements you will encounter when reading are in clause 4. Context of the Organization.
Clause 4.1 is about relevant internal and external issues. Because ISO 27001 doesn’t offer a lot of information about what exactly constitutes an internal or external issue, this can be a tricky first step for businesses that are totally new to compliance.
Some examples of internal issues might include things such as internally stored or managed information assets, personnel issues such as high turnover rates or difficulty recruiting qualified individuals, or current compliance processes that are causing issues.
- What are the issues, both internal and external, that will affect the success of your ISMS?
Clause 4.2 has to do with the “interested parties,” and their requirements. These interested parties do include customers and partners, but they also include employees, management, suppliers, and regulators. Anyone who has a say or an interest in your data security should be considered here. Once you’ve identified all of the stakeholders, you can identify which of those parties has the most influence on your compliance program and begin to pare down that list to the most inclusive and realistic list of requirements.
- Who are the stakeholders who will have input into or benefit from your ISMS?
- What do stakeholders need from your ISMS, and how do those requirements overlap and intersect?
Clause 4.3 requires the establishment of the scope of your eventual ISMS and states that you must consider the issues and interested parties you identified and the interfaces and dependencies between those issues and interested parties while developing this scope.
- What issues will be specifically addressed within the scope of your ISMS?
- What requirements of your stakeholders will you address with your ISMS?
- How do these requirements intersect with each other, and how will that affect how your ISMS operates?
Finally, clause 4.4 requires the establishment, implementation, and maintenance and improvement of an ISMS. Ultimately, the evidence you use to prove compliance with this clause will be the culmination of the rest of the controls that you will develop, which will all be informed by clauses 4.1 through 4.3.
- Is your ISMS fully established and implemented, and are you continually working to improve it?
5. Leadership

Control family 5 addresses your business’s leadership and management. Senior management’s support of your company’s culture of compliance is critical to its success, so much so that ISO has dedicated three clauses and 17 sub-clauses to ensuring your business is hitting every part of leadership involvement needed to make a compliance program successful.
5.1 Leadership and Commitment: These requirements comprise almost half of control family 5, and they lay out the steps that leadership needs to take to ensure compliance is a company-wide priority. For example, the leadership needs to establish information security objectives, make the resources needed for ISMS creating and maintenance available, and promote continual improvement.
Finally, 5.1.h dictates that leadership must “support other relevant management roles to demonstrate their leadership as it applies to their areas of responsibility.” Depending on the size of your company and what kinds of information security and compliance staff you have, this might include your Chief Information Security Officer, IT Director, HR Director, and more.
One of the most difficult parts of proving compliance with clause 5.1 is collecting evidence. While you might see evidence every day of your CISO or CEO providing support to other managers or promoting continual improvement of your information security program, how do you document that? Part of your ISMS’ function will be to find and collect this kind of evidence so that you can show during your audit that your senior leadership is taking these responsibilities seriously.
- Do you have a documented set of information security objectives developed by your leadership team?
- Has the ISMS been integrated into your organization’s processes that touch on any sensitive information?
- Has leadership made the resources your team needs to manage the ISMS available to you?
- Does your leadership regularly communicate the importance of your company’s ISMS to people at all levels of the business?
- Is your leadership checking on the outcomes of your ISMS to make sure they’re the outcomes they intended?
- Is your leadership team hiring and supporting the team members needed to make sure the ISMS is operating properly?
- Is your leadership team invested in and working towards continual improvement of your ISMS?
- Are the executives in your business supporting all of the lower-level managers in their unique area of responsibility?
5.2 Policy: This clause requires that leadership establish an information security policy, ensure that it’s tailored to your organization, and make sure that it includes some key features, like information security objectives and a commitment to continual improvement of the ISMS. They also have to make the policy available to interested parties when it’s necessary and communicate the policy throughout the organization.
The final leadership responsibilities, stated in clause 5.3, are assigning responsibility and authority for 1) ensuring the ISMS conforms to the information security standard they’ve developed and 2) reporting on the performance of the ISMS.
- Is your information security policy tailored to the purpose of your company?
- Does your information security policy include specific objectives?
- Does your information security policy state that your business is committed to compliance with any information security requirements applicable to your business?
- Does your information security policy explicitly state that your company is committed to continually improving the ISMS?
- Is your information security policy available to anyone in your company who wants or needs to see it?
6. Planning

This control family broadly addresses what your business needs to plan in terms of recognizing and addressing risks and opportunities. Clause 6 is broken down into four smaller sections:
6.1.1: General risk planning: This clause covers identifying risks and opportunities to 1) make sure your ISMS can achieve its intended outcome, 2) reduce or prevent undesired effects, and 3) ensure your ISMS is continually improving. This section also requires planning specific actions to address the risks and opportunities determined above as well as defining and implementing a process for assessing information security risks.
In short, your business needs a documented process for identifying, assessing, and treating information security risks that are integrated into your ISMS.
- Do you understand the risks your ISMS faces and the opportunities you can take advantage of to make it successful?
- Have you determined which of those risks you need to address to make sure there aren’t any negative outcomes from your ISMS implementation?
- Do you know specifically which risks and opportunities you have to address in the future to make sure you are continually improving your ISMS?
- Do you have an actionable plan for those risks and opportunities?
- Have you worked out how you implement those plans into your ISMS process and make sure they’re working out as they should?
6.1.2: Information security risk assessment: This clause covers, in more detail, ISO 27001’s requirements for an information security risk assessment process that meets some specific criteria, such as including risk acceptance and assessment criteria and producing consistent, valid, and comparable results.
It also includes requirements for applying this risk assessment process to identify the risks to your business in the face of a possible loss of confidentiality, integrity, and availability, assessing the consequences and the likelihood of those risks, and using the process to evaluate the risks and see how they compare to the risk acceptance and assessment criteria you developed earlier.
Essentially, this section requires you to develop a process to identify and evaluate risks to your information that produces consistent and actionable results.
- Do you have a process in place for assessing new risks to your ISMS?
- Does the process have risk assessment criteria and criteria for which risks you’re willing to accept?
- Does the process produce consistent results that are compatible with your ISMS process and goals?
- Have you used that risk assessment process to identify any risks related to a loss of confidentiality, integrity, and availability of sensitive information?
- Have you figured out what would happen if those risks were to come to fruition and how likely that is to happen?
- Have you compared those results to the risk assessment criteria you established and determined how you will address them?
6.1.3: Information security risk treatment: Once you’ve developed a process for identifying and evaluating risk, clause 6.1.3 requires that you develop a process for risk treatment.
Ultimately, this process will help you determine whether your organization will tolerate the risk, take steps to terminate it, or transfer the risk to another party; how to implement the treatment option you choose; and how to develop a risk treatment plan. Finally, this risk treatment plan and any residual information security risks that come along with it have to be approved by the risk owner.
- Do you have an established process for treating risks to your information security?
- Have you used that process to select risk treatment options for the various risks your company is facing?
- Have you further used that process to determine what controls you need in place to implement those risk treatment options?
- Have you utilized the risk treatment process to produce a Statement of Applicability?
- Have you used the process to develop a risk treatment plan for future information security risks?
- Do the risk owners approve of the risk treatment plan and accept any additional risks that come along with the plan’s implementation?
6.2: Information security objectives and how to plan to achieve them: The final clause in the Planning control family lays out requirements for information security objectives that your business must develop. Among other things, these objectives have to be consistent with your company’s information security policy, measurable, communicated, and updated when needed.
To be ISO 27001 compliant, your business also must determine what resources will be required to meet the objectives, who will be responsible for each objective, when they will be completed, and how the results will be evaluated. You’ll also have to maintain documentation on all the information security objectives.
The Planning control family requires a lot of work, because even in an organization that has some of these elements in place, they usually aren’t as thoroughly documented as ISO 27001 requires. But that documentation is critical for these risk assessment and treatment plans to work. People have to be able to access and carry out these plans consistently, and that can’t happen if they aren’t documented and readily available.
- Do you have established information security objectives in the departments that need to have them and at all levels, not just upper management?
- Are all of those objectives in line with your overall information security policy?
- Are the objectives measurable?
- Do those objectives take compliance requirements, risks, and risk treatment into account?
- Do the right people understand these objectives?
- Are the objectives updated when they need to be?
- What are the actionable outcomes of these objectives?
- What resources will people need to meet these objectives?
- Who are the people responsible for each objective?
- When will these objectives be completed?
- How will you evaluate the success of each objective?
- Have you documented all of the above information for each information security objective?
Get to know ISO 27001 better

Want to learn more about ISO 27001’s requirements and what it takes to be prepared for a formal audit? Download our guide Getting to Know the ISO 27001 Standard: Practical Guidance for Achieving ISO 27001 Certification to get the information you need to jumpstart your certification process.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











