How to Perform an IT Compliance Audit: A Comprehensive Checklist

Maintaining IT compliance is a crucial priority for organizations, yet the IT compliance audit process can be a daunting task. IT compliance audits often involve time-consuming manual processes, making them error-prone and hindering operational efficiency.
Let’s dive into how organizations can use automation tools to streamline key audit tasks — from data collection and analysis to reporting and remediation actions. We’ll even provide a comprehensive checklist outlining how to perform an IT compliance audit to get you started.
What is an IT compliance audit?
An IT compliance audit is an independent assessment of an organization’s adherence to cybersecurity tools, practices, and policies. It evaluates whether the organization meets specific requirements and complies with regulations and laws established by certification bodies or standard-setting organizations. Some common compliance frameworks include:
- ISO 27001, which focuses on information security management systems
- SOC 2®, which assesses controls relevant to data security, availability, processing integrity, confidentiality, and privacy
- GDPR, which ensures protection of personal data and privacy for individuals within the European Union (EU)
- HIPAA, which sets standards for the protection of sensitive patient health information
- PCI DSS, which ensures secure handling of credit card information
Compliance audits are important because regulations and laws are constantly evolving and being updated. An audit ensures your organization is adhering to new or updated regulations and laws and identifies opportunities for improvement.
Ready to start the audit process? Assess your audit preparedness ->
Primary objectives of an IT compliance audit
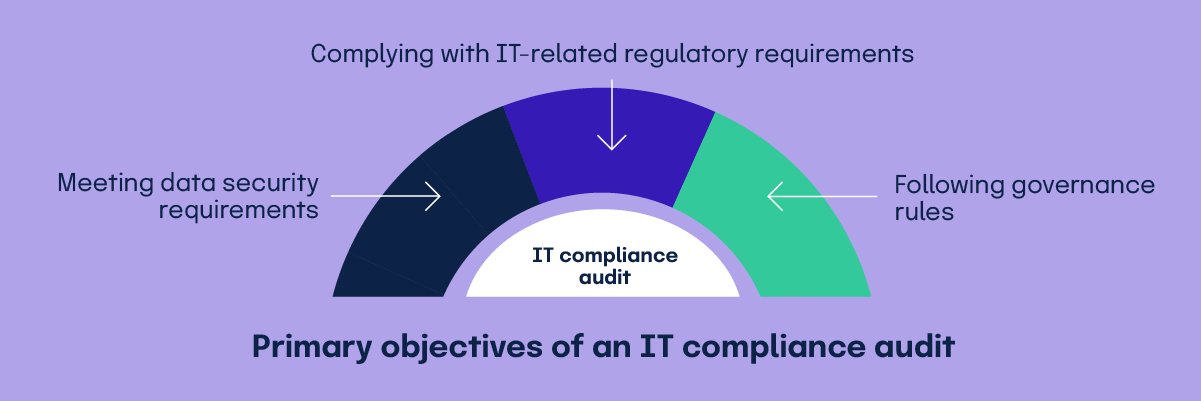
The main objectives of an IT compliance audit include ensuring data security requirements are met, following governance rules, and complying with IT-related regulatory requirements.
Meeting data security requirements
This involves evaluating the organization’s data protection measures, encryption protocols, and access controls to ensure that sensitive information is safeguarded against unauthorized access and breaches. Compliance with data security standards like GDPR, CCPA, and HIPAA is critical to protecting customer and employee information, preventing data leaks, and maintaining the organization’s reputation.
Following governance rules
This is essential for maintaining the integrity and accountability of an organization’s IT processes. An IT compliance audit assesses how well an organization adheres to established governance frameworks, such as COBIT or ITIL, which provide guidelines for IT management and control. Ensuring proper governance helps organizations streamline their operations, align IT strategies with business goals, and demonstrate compliance to regulators and stakeholders.
Complying with IT-related regulatory requirements
Compliance with IT-related regulatory requirements ensures organizations securely manage their IT infrastructure. These regulations vary depending on industry and location but generally include standards for data privacy, cybersecurity, and operational processes.
For example, regulations such as GDPR, HIPAA, and PCI DSS impose strict requirements on how organizations manage, store, and protect sensitive data while frameworks like NIST CSF offer guidelines to help organizations navigate IT governance and risk management.
During an IT compliance audit, an organization is evaluated on how well it meets these regulatory requirements. This involves assessing security controls, reviewing data privacy practices, and ensuring proper documentation.
Key benefits of regular IT compliance audits
Regular IT compliance audits offer proactive risk management by identifying and assessing risks before they become significant issues. They provide continuous improvement opportunities to enhance processes and controls, and they strengthen your organization’s reputation and credibility through consistent compliance. Additional benefits of regular IT compliance audits include:
- Helping you stay ahead of changes to your organization
- Allowing leadership to get an accurate view of an organization’s compliance posture
- Uncovering hidden security risks
- Proactively preventing data breaches and other vulnerabilities
- Increasing efficiency and cost-savings by reducing the probability of costly compliance failures
- Establishing trust with key stakeholders like the board
The importance of staying proactive
Staying proactive in IT compliance is not just about avoiding penalties. It’s about creating a robust security posture that protects your organization’s data, enhances operational efficiency, and builds trust with customers and stakeholders. Continuous monitoring, regular updates to compliance strategies, and leveraging technology are key to maintaining an effective compliance program.
Read more about the importance of maintaining IT compliance ->
Conducting an IT compliance audit
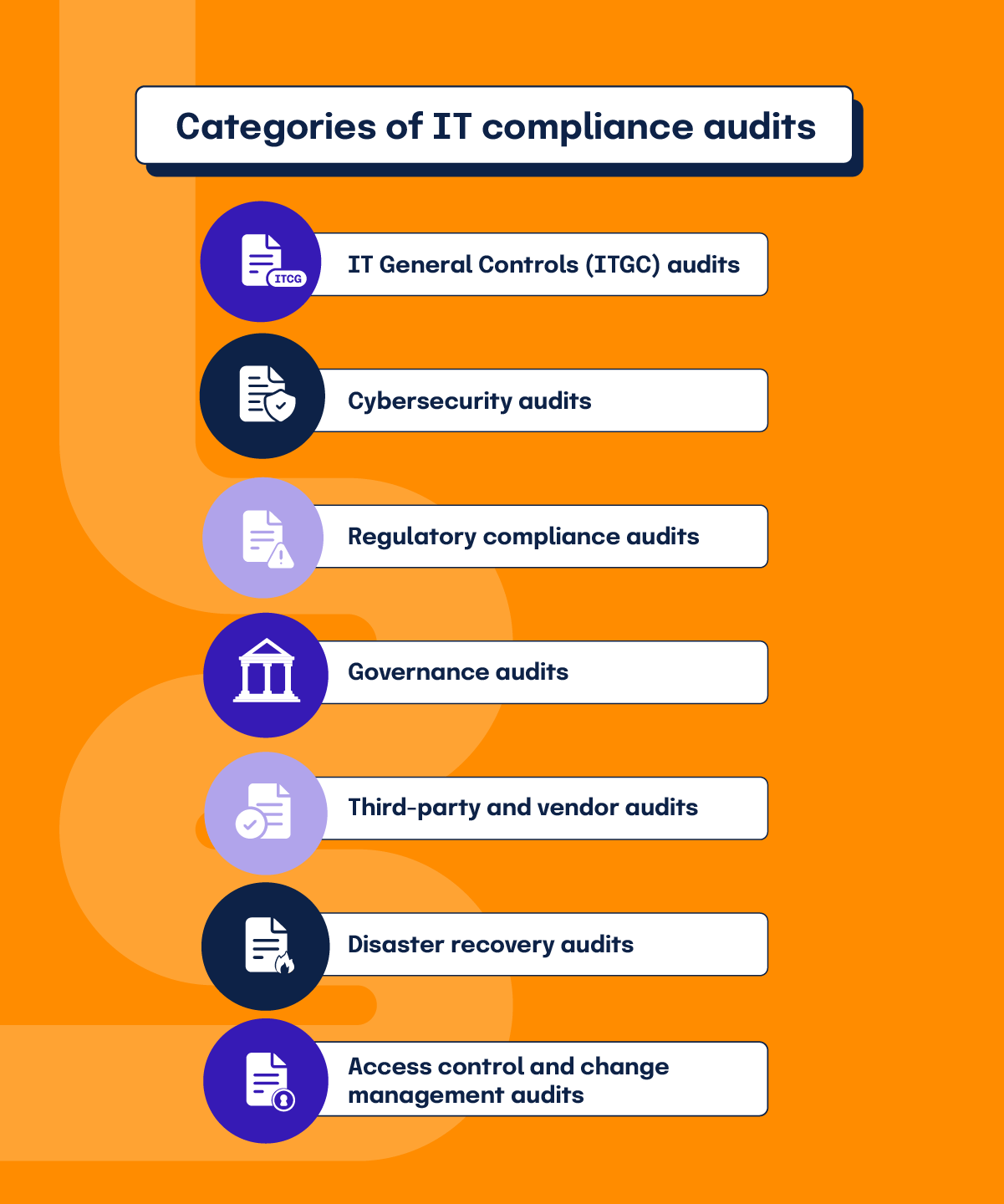
IT compliance audits cover many areas of your business. These audits can be broken down into the following categories:
IT General Controls (ITGC) audits
IT general controls (ITGC) audits focus on the core aspects of an organization’s IT infrastructure. These audits examine controls related to IT operations, access to programs and data, program development, and program changes. Ensuring these controls are in place and functioning correctly is vital for maintaining the financial integrity and security of the IT environment, particularly in regulated industries. This includes reviewing policies and procedures, monitoring user access, and verifying the effectiveness of backup and recovery processes.
Cybersecurity audits
Cybersecurity audits evaluate an organization’s defenses against cyber threats. This involves assessing the effectiveness of firewalls, intrusion detection systems, antivirus software, and encryption protocols. The audit identifies vulnerabilities, ensures that incident response plans are robust and current, and verifies compliance with cybersecurity frameworks such as NIST CSF, ISO 27001, and the CIS Security ControlsⓇ.
Regulatory compliance audits
Regulatory compliance audits ensure that an organization is adhering to industry-specific laws and regulations. These audits review compliance with standards such as GDPR (for data privacy), HIPAA (for healthcare information), SOX (for financial reporting), and PCI DSS (for payment card information). The focus is on data privacy, financial reporting, and the handling of sensitive information. Regulatory compliance audits help organizations avoid legal penalties, enhance transparency, and demonstrate their commitment to ethical practices.
Governance audits
Governance audits assess the alignment of IT processes and strategies with the organization’s overall goals and objectives. This involves reviewing governance frameworks like COBIT, which guides control objectives, or ITIL, which focuses on IT service management. Governance audits ensure that IT investments are managed effectively, risks are mitigated, and there is accountability at all levels. These audits promote better decision-making and strategic planning.
Third-party and vendor audits
Third-party and vendor audits evaluate the compliance and security practices of external partners and suppliers. These audits ensure that vendors meet the organization’s standards for data protection and regulatory compliance. By assessing the risk posed by third-party relationships, organizations can prevent data breaches, ensure continuity of services, and maintain trust with their clients and stakeholders.
Disaster recovery audits
Disaster recovery audits review and test the organization’s plans and procedures for responding to and recovering from IT disruptions. This includes assessing the adequacy of backup systems, recovery time objectives (RTO), and recovery point objectives (RPO). Disaster recovery audits ensure that the organization can quickly restore operations after an incident, minimizing downtime and data loss, and maintaining business continuity.
Access control and change management audits
Access control and change management audits focus on the management of user access and changes to IT systems. These audits evaluate how access rights are granted, modified, and revoked, ensuring that only authorized personnel have access to sensitive information. Change management audits assess the procedures for implementing, documenting, and reviewing changes to IT systems. Proper access control and change management are essential for preventing unauthorized access and ensuring system integrity. They are often integrated into broader security or ITGC audits.
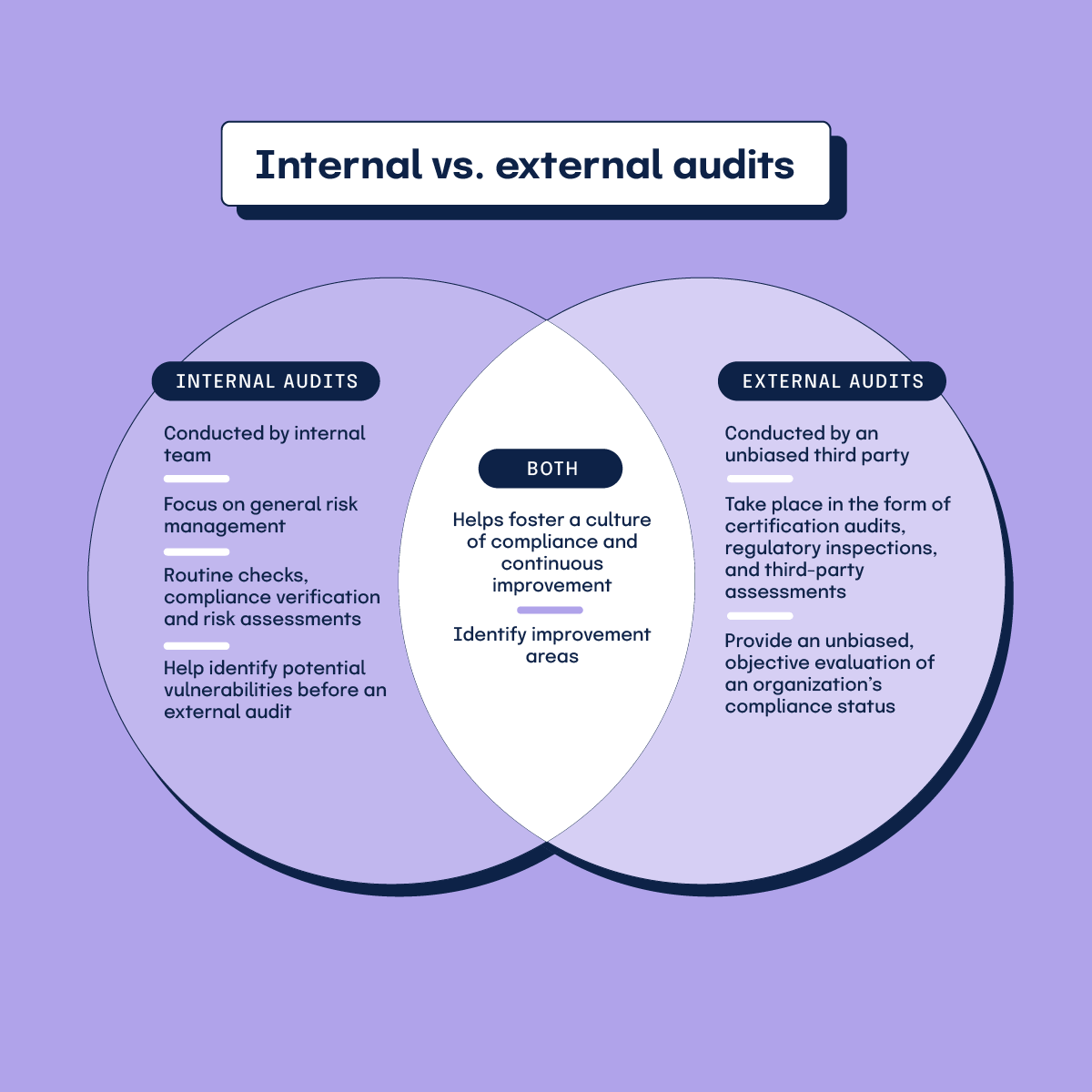
Internal vs. external audits
Internal audits are conducted by an organization’s internal team to focus on general risk management and compliance with internal policies. These audits often include routine checks, compliance verifications, and risk assessments. Internal audits are valuable as they help identify potential vulnerabilities and improvement areas before external auditors or regulatory reviews. This gives the organization time to address issues proactively. In addition to this, regular internal audits contribute to fostering a culture of continuous improvement and compliance.
External audits are conducted by an unbiased third party to ensure adherence to regulatory standards. These audits can take the form of certification audits, regulatory inspections, and third-party assessments. External audits are particularly important as they provide an unbiased, objective evaluation of an organization’s compliance status, which offers credibility and additional assurance to stakeholders, clients, and regulatory bodies.
Learn more about conducting internal audits in this comprehensive guide to internal audits ->
Why conduct IT compliance audits?
IT compliance audits primarily focus on evaluating adherence to regulatory requirements and standards rather than directly identifying vulnerabilities or implementing stronger security measures. These audits provide a comprehensive evaluation of IT controls and processes, ensuring they meet regulatory requirements and best practices.
When an organization regularly conducts IT compliance audits, they are able to proactively address potential issues, which ultimately reduces the overall risk of costly breaches. In addition to this, regular audits enhance an organization’s credibility and trust since they show clients, partners, and stakeholders that security and compliance are a priority. The insights IT compliance audits provide help drive continuous improvement for an organization, allowing it to stay ahead in the evolving regulatory landscape.
How to conduct an IT compliance audit

IT compliance audits can vary extensively by which framework(s) your organization uses. The NIST Cybersecurity Framework (CSF) is a flexible, commonly used framework that can guide your IT compliance audit process. For the purposes of this article, we have used NIST CSF as a baseline to outline the steps needed to conduct an IT compliance audit. Please note that this is just an example and there are various ways an organization can conduct an IT compliance audit.
Step 1: Identify the scope
First, begin by identifying the scope of the audit. This involves defining the systems, processes, and assets to be evaluated. The scope of conducting an audit to assess compliance with NIST CSF might include evaluating network infrastructure, user access controls, incident response protocols, and risk management processes. It is important to clearly outline which parts of your organization will be included to ensure a comprehensive assessment.
For example, HR should evaluate current and former employees who may still have access to sensitive company data, each department (such as Marketing, Customer Success, and Product) needs to conduct user access reviews, and the accounting department must review the security of payment platforms. This step sets the foundation for the entire process, making it essential to be thorough and precise.
Step 2: Understand NIST CSF categories and subcategories
Next, you should review the NIST CSF categories and subcategories to familiarize yourself with the framework’s requirements and how they apply to your organization. Understanding these categories helps when mapping out your necessary controls and security measures.
Step 3: Evaluate your existing controls
Evaluate your organization’s existing controls against each NIST CSF subcategory. This assessment involves a detailed examination of your current practices and controls to determine their effectiveness. Identify areas where your organization is compliant and areas that may require improvement.
For example, if evaluating the “Access Control” subcategory, you would review current processes for managing access to critical systems and data. This would include assessing user authentication methods, access provisioning and de-provisioning processes, and the use of multi-factor authentication (MFA). You would then compare these controls against the NIST CSF standards to identify areas of compliance and areas needing improvement. Oftentimes, you will see maturity measured in this step as well. If current controls lack stringent access logging or regular access reviews, then those would be marked as an opportunity area to align with NIST CSF best practices.
Step 4: Select your organization’s tier:
For each NIST CSF function, the practitioner of the audit will work with their organization’s leadership team to select the tier your organization wants to be at. This step will help you determine where you need to be so you can work backward to outline what steps should be taken to reach the desired tier for each function.
NIST CSF has identified four tiers:
- Partial (Tier 1)
- Risk informed (Tier 2)
- Repeatable (Tier 3)
- Adaptive (Tier 4)
Learn more in this quick start guide from NIST that provides a roadmap for how to use the CSF tiers ->
To apply a tier to NIST CSF functions, start by rating your organization’s current state for each function. For instance, if assessing the “Governance” function, you would evaluate how well your organization establishes and monitors your company’s cybersecurity risk management strategy, expectations, and policy. Here is an example of what governance looks like at each tier:
Tier 1: Partial
Governance is minimal or non-existent. There is little to no formal cybersecurity risk management strategy in place, and leadership may not be aware of or engaged in cybersecurity activities. Policies, if they exist, are not consistently enforced or aligned with broader organizational goals.
Tier 2: Risk informed
Governance is somewhat established but not fully integrated across the organization. Leadership recognizes the importance of cybersecurity risk management, and there are basic policies and strategies in place. However, these efforts may be reactive, with limited alignment to the organization’s broader risk management practices.
Tier 3: Repeatable
Governance processes are well-established and consistently applied across the organization. Leadership is actively engaged in cybersecurity risk management, ensuring that policies and strategies are regularly reviewed and aligned with organizational objectives. Governance is proactive, with a strong emphasis on continuous improvement and adaptation to emerging threats.
Tier 4: Adaptive
Governance is highly mature and integrated into every aspect of the organization’s operations. Leadership not only actively manages cybersecurity risk but also anticipates future challenges and adapts strategies accordingly. The governance function is dynamic, with policies and practices continuously evolving based on real-time data, threat intelligence, and organizational changes, ensuring alignment with long-term strategic goals.
Assessing what governance looks like at each tier allows your organization to conduct a gap analysis to identify the steps that should be taken to get to your desired tier. Our extensive, peer-reviewed GRC maturity model provides an excellent roadmap for organizations looking to improve their GRC maturity.
Want to assess which tier your organization aligns with?
Get started by taking the GRC maturity evaluation quiz ->
Step 5: Identify and remediate gaps
Identify gaps between your current practices and the NIST CSF control requirements. Highlight areas needing improvement and develop an action plan to address these gaps. This plan should include specific steps, timelines, and responsible parties to create a roadmap for enhancing your cybersecurity posture. If your audit reveals that the Protect function’s subcategory, managing access permissions and authorizations, is at a low maturity level, then you would need to assess why this gap exists and what specific improvements are required,
Suppose your current system lacks a robust process for regularly reviewing and updating access permissions. In this case, an action plan could include the following steps:
1. Implement a user access review process
- Establish a policy for periodic user access reviews
- Develop a procedure for conducting access reviews
- Integrate this process with your existing IT systems
- Define a schedule for regular access reviews
- Assign responsibility to the IT security team to develop and implement the policy with department managers responsible for executing reviews in their specific area
2. Enhance user access controls
- Implement MFA for critical systems
- Ensure all access requests require manager approval
- Roll out MFA within six months
- Update the request approval workflow within the next two months
- Assign responsibility to the IT department to lead the implementation with HR and department heads supporting the updates of access request workflows
Step 6: Regularly assess with continuous monitoring
Regularly reassess and adjust your strategies as needed. Continuous monitoring and updating your cybersecurity practices are crucial to staying ahead of evolving threats and maintaining compliance. Schedule periodic reviews to ensure your organization remains aligned with the NIST CSF and other relevant standards.
Who should be involved?
Several teams and individuals should be involved in the IT compliance audit process, including the information security/cybersecurity team, risk management team, internal audit team, audit committee, executives, and IT operations and systems administrators.
Each group plays a specific role: the internal audit team conducts the audit, the information security/cybersecurity team implements and maintains security controls, the risk management team identifies and assesses risks, the audit committee oversees the audit process, executives set the tone and priorities, and IT operations manage technical infrastructure and controls.
It is important to note leadership plays a pivotal role in the overall success of IT compliance programs. Executives must prioritize compliance by allocating necessary resources, setting clear expectations, and actively participating in compliance initiatives. A strong tone from the top can drive the entire organization towards achieving and maintaining compliance.
IT compliance audit checklist: a practical guide for beginners
Below is a checklist to help you get started on an IT compliance audit. We’ve outlined the key steps you should take to get started to help expedite the process.
IT Compliance Audit Checklist: A Practical Guide for Beginners

Overcoming IT compliance audit challenges
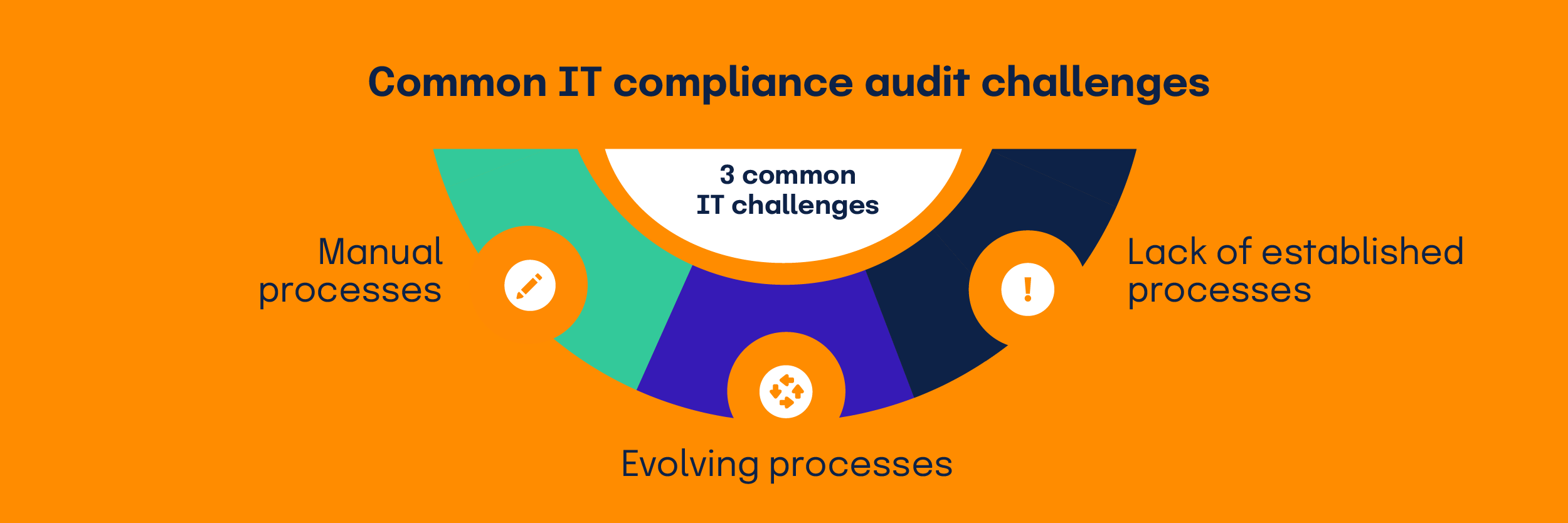
Common challenges in IT compliance audits include time-consuming and error-prone manual processes, evolving regulations that require constant updates, and a lack of established processes that make it difficult to maintain consistent compliance practices.
Manual processes
To overcome the challenge of manual processes, organizations can leverage technology to streamline processes and reduce errors.
With Hyperproof, organizations can:
- Use Hypersyncs to automate evidence collection
- Automate control testing and escalation
- Map controls across frameworks with built-in control crosswalks
Evolving regulations
To overcome evolving regulations, organizations must stay informed about regulation changes and educate their team regularly through continuous education and monitoring of regulatory updates.
Lack of established processes
To overcome a lack of established processes, organizations should develop and enforce internal policies to ensure consistent compliance.
Read more about conducting shorter, efficient audits – known as agile auditing ->
How can technology accelerate the audit process?
Integrating technology into IT compliance audits not only enhances accuracy and efficiency but also enables IT teams to redirect their focus toward strategic initiatives that drive business growth and innovation. These platforms provide a seamless connection between controls and audit requests, ensuring easy access to necessary information and streamlining audit workflows. They enhance communication and coordination with internal and external auditors and allow you to monitor status regularly to keep track of progress and address issues promptly, helping you stay on schedule.
Customer story: How DigiCert uses Hyperproof to save 80 hours per month
One of our customers, DigiCert, uses Hyperproof to streamline evidence organization and record keeping for audits, saving their compliance team 80 hours per month. Aaron Poulsen, Director of Product Security and Compliance says “With Hyperproof, we finally know where we stand with an audit.”
Dive into the case study ->
How Hyperproof’s Audit Module streamlines the audit process
Hyperproof’s audit management platform revolutionizes how organizations prepare for audits by centralizing all audit-related tasks and automating the manual work you dread, like evidence collection and file management. This ensures that evidence is always current and accurate, taking the guesswork out of audit preparation.
Hyperproof enhances collaboration with external auditors by providing them with controlled access to only the necessary information. External auditors can see specific documents and data relevant to the audit without having access to sensitive or unrelated information.
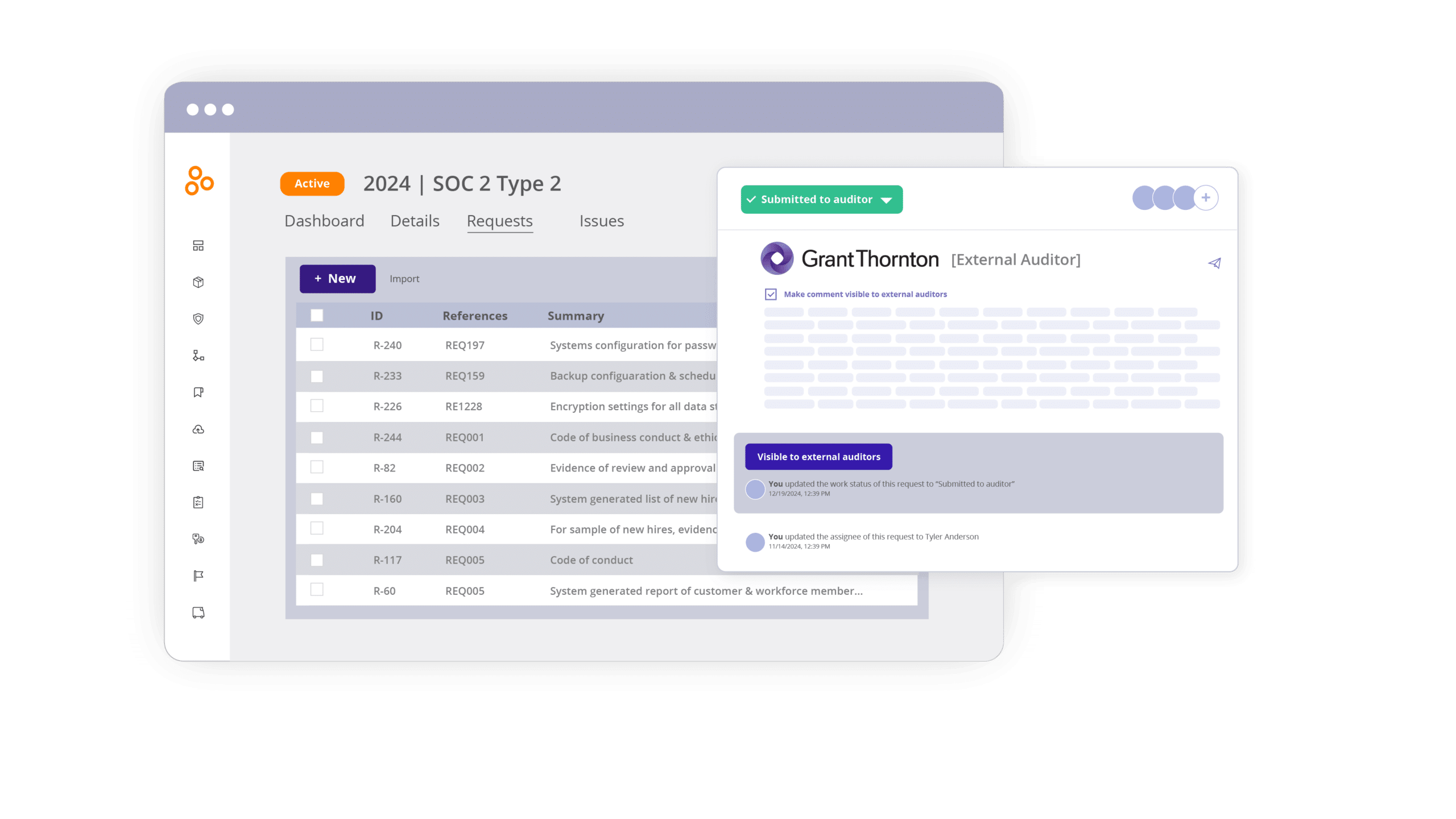
You can also connect audit requests to controls and their associated evidence in Hyperproof. This speeds up the audit readiness process and enables users to reuse the work they have already done for their next audit.
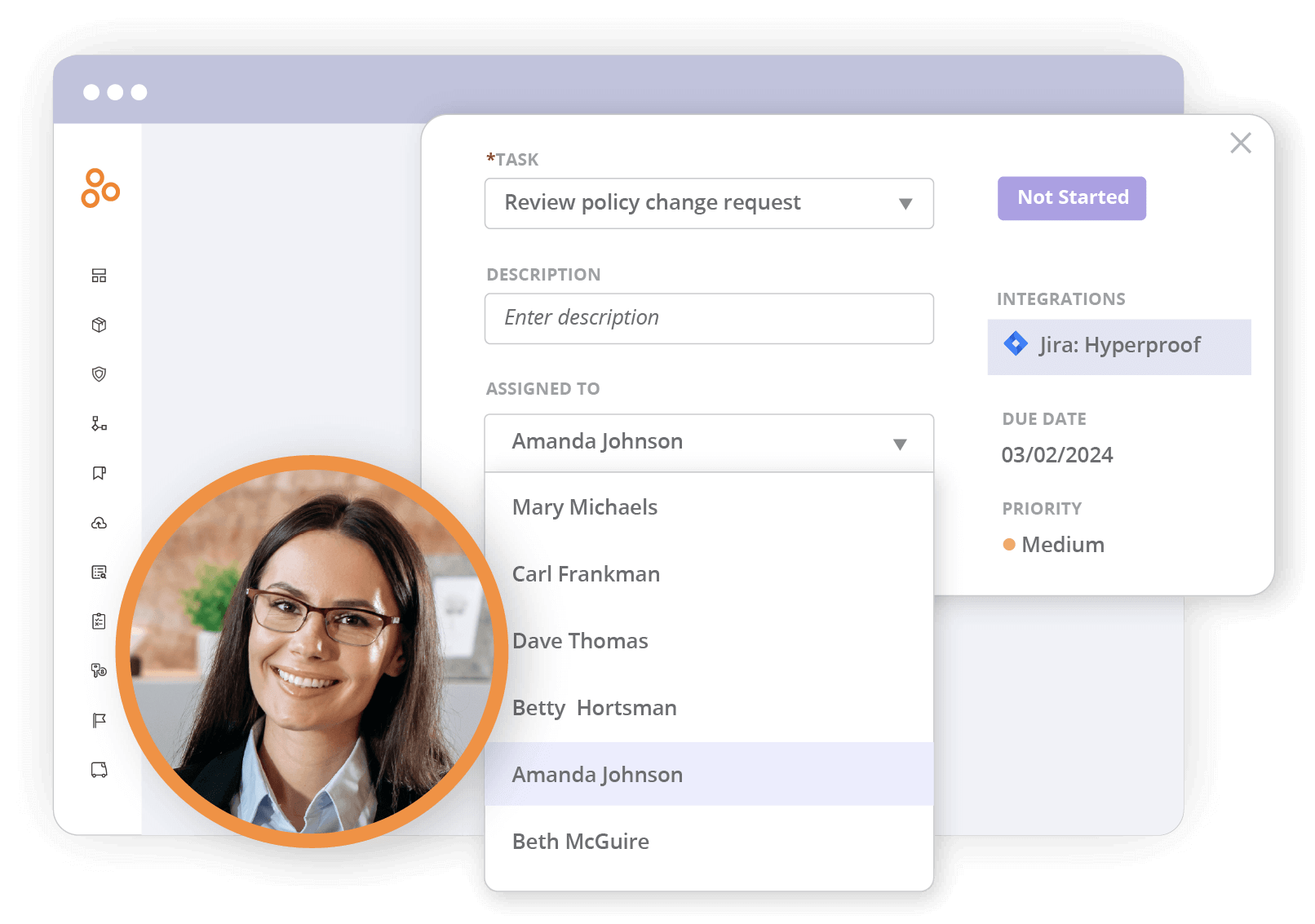
Hyperproof also simplifies the process of requesting evidence across the organization. Audit managers can create and assign tasks to team members, specifying exactly what information is needed and when it’s due. These tasks come with built-in notifications, ensuring that assignees are promptly informed of their responsibilities. This proactive communication helps maintain the momentum of the audit process.
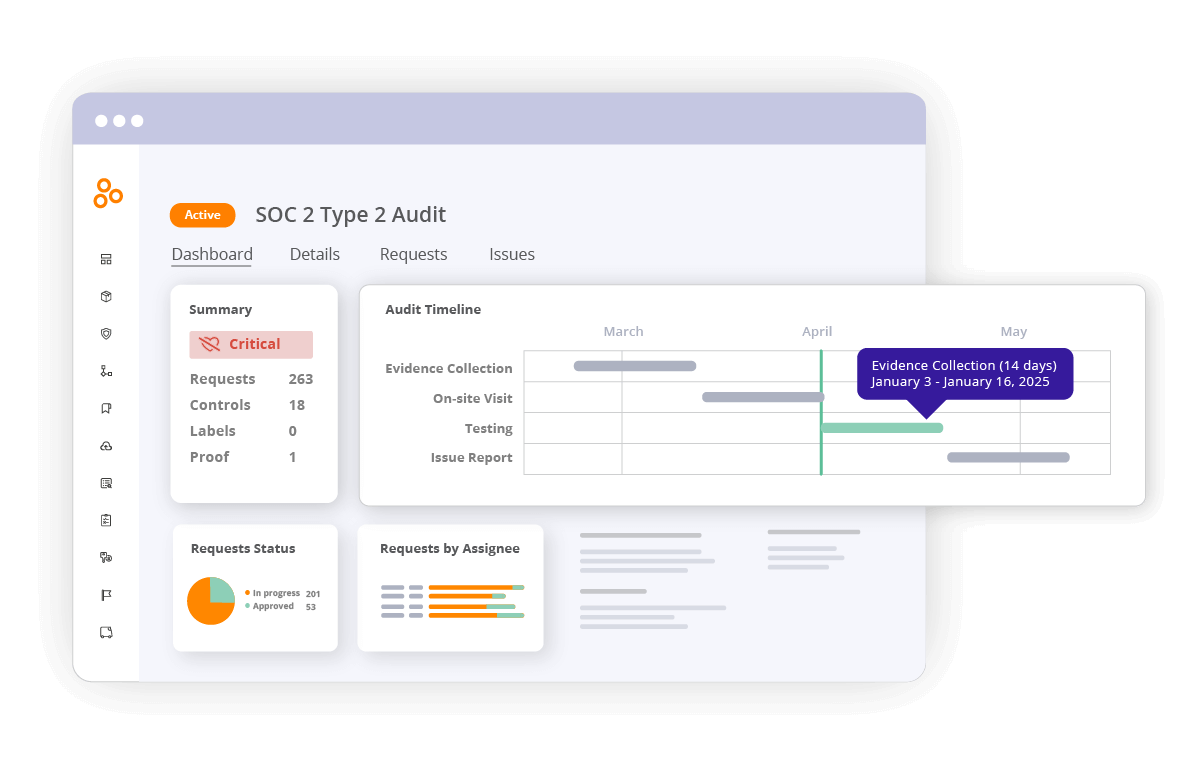
The audit dashboard provides clear visibility into the status of audit requests, ensuring that organizations can efficiently track progress and address any outstanding issues. At a glance, you can understand your progress toward completing the audit, what is in review, and what is completed so you can easily report your status to stakeholders.
Ready to learn more?
Our team would love to help you solve your IT compliance audit challenges.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












