
The Ultimate Guide to
NIST CSF: A Practical Guide to Cybersecurity Risk Management
Introduction
Today, many companies turn to security guidelines like the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) when they need help creating a rigorous approach to cybersecurity risk management. Cybersecurity risk management is more critical today than ever. Global cybercrime costs businesses 16.4 billion every day, with a ransomware attack occurring every eleven seconds. Yet, managing risk is a challenging, ongoing, iterative process for all organizations.
Despite many advantages, the adoption of NIST CSF can be challenging for many organizations. However, there is a way to implement this framework faster while ensuring it will provide all desired security benefits.
What is NIST CSF?
NIST CSF is voluntary guidance designed to help organizations better understand, assess, prioritize, and communicate their cybersecurity efforts to manage and reduce cyber risk of all types, including malware, password theft, phishing attacks, DDoS, traffic interception, social engineering, and others. The National Institute of Standards and Technology (NIST) created the framework by collaborating with government and industry groups, and the framework was designed to complement existing organizational cybersecurity operations. NIST CSF is designed to complement existing organizational cybersecurity operations and can be integrated with other risk management programs and standards like ISO 27001 and COBIT 5.
The framework provides a common language and methodology for managing cybersecurity risk and helps guide key decisions about risk management activities through the various levels of an organization, from senior executives to business and process level and implementation teams as well.
The framework provides a common language and methodology for managing cybersecurity risk and helps guide key decisions about risk management activities through the various levels of an organization, from senior executives to business and process level and implementation teams as well.
Because the framework is designed to be outcome-driven (as opposed to prescriptive), it works for organizations of all sizes, industries, and maturities. Thus, whether you’re just starting to establish a cybersecurity program or already running a mature program, the framework can provide value by acting as a top-level security management tool that helps assess cybersecurity risk across the organization.
Blog
Want to learn more about NIST CSF 2.0, the latest update to the NIST CSF framework?
What are the 3 key components of NIST CSF?
The framework is composed of three components:
1 Implementation tiers
2 Framework core
3 Framework profiles
1 Implementation Tiers
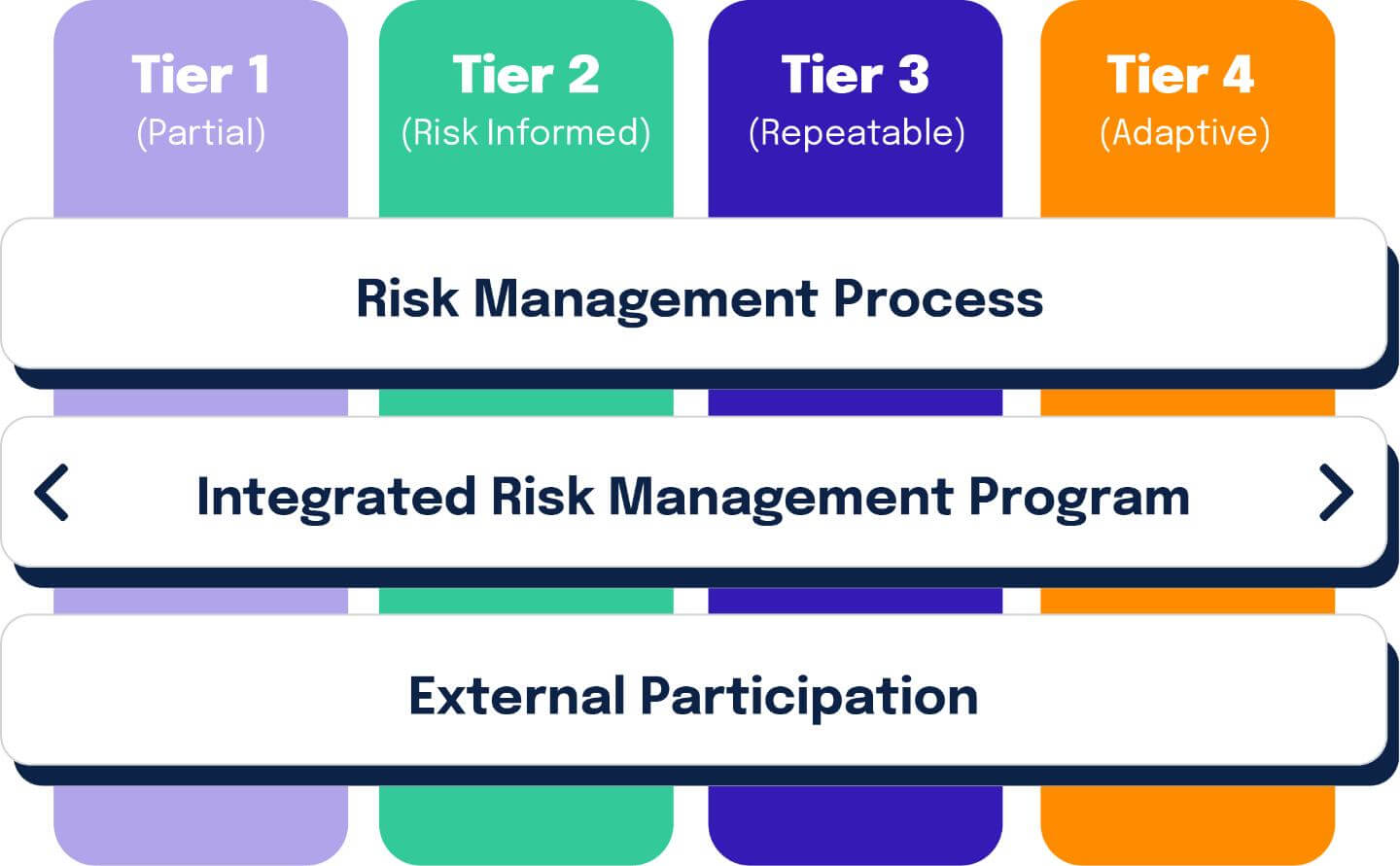
Implementation tiers provide context for cybersecurity risk management and guide organizations to the appropriate level of rigor for cybersecurity programs.
The framework tiers are categorized on a scale of 1 (lowest) to 4 (highest):
Tier 1: Partial
A tier 1 categorization means cybersecurity risk management practices lack formalization, and awareness of cybersecurity risks at the organization is limited.
Tier 2: Risk Informed
A tier 2 categorization means there is awareness of cybersecurity risks at the organizational level, but an organization-wide approach to managing cybersecurity risks has not been established. Cybersecurity information sharing within the organization remains informal.
Tier 3: Repeatable
A tier 3 categorization means management endorses the organization’s cybersecurity practices and formalizes them into an enterprise-wide policy covering both cybersecurity risk governance and risk management across all organizational functions. These practices are updated regularly based on risk assessments and changes to the business, technology, and threat landscapes.
Tier 4: Adaptable
A tier 4 categorization means organizations recognize the interplay between cybersecurity risk and organizational objectives and integrate this into their decision-making processes. The organization demonstrates agility in adapting to evolving threats and technology landscapes and is able to quickly respond to sophisticated threats.
2 Framework Core
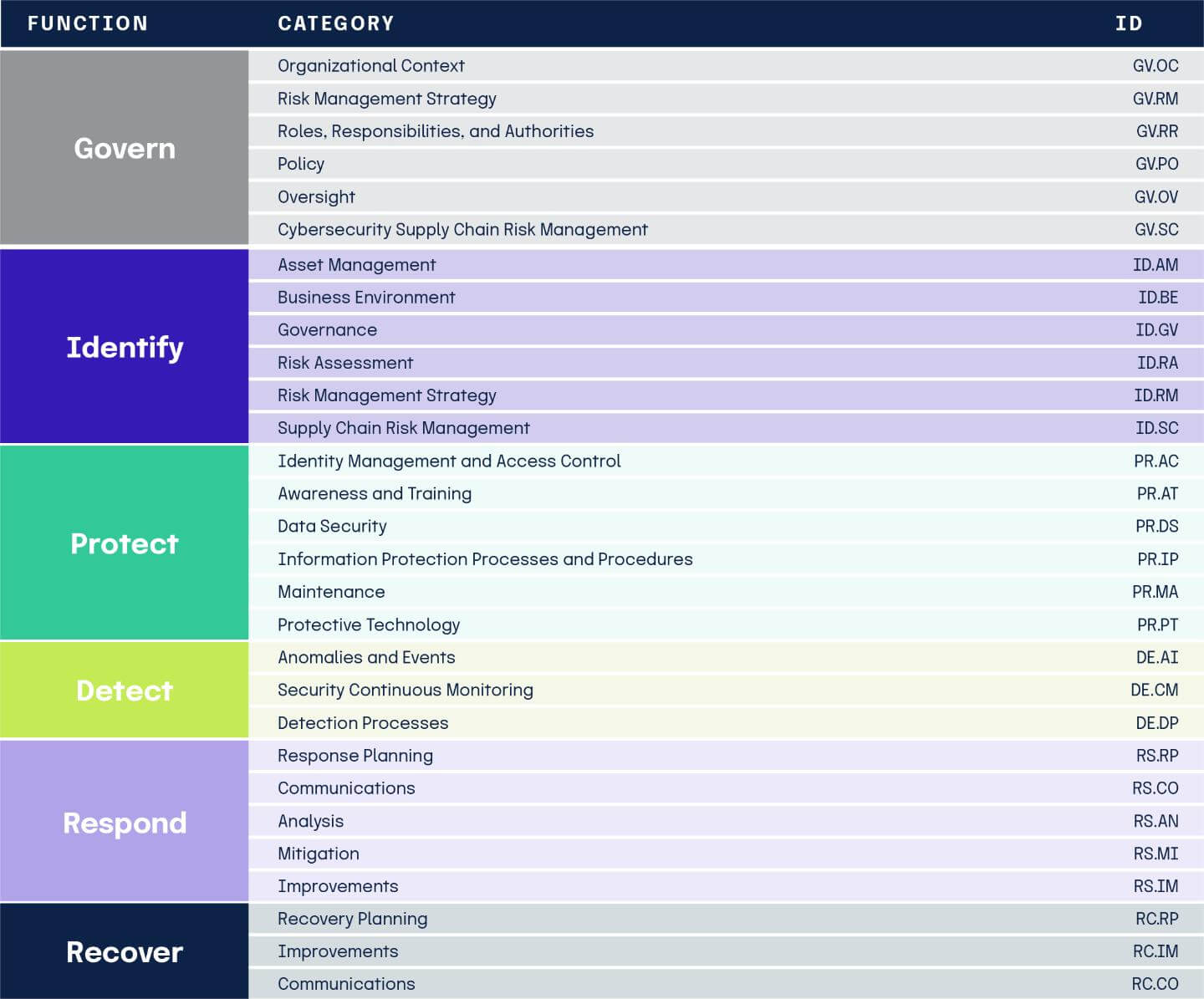
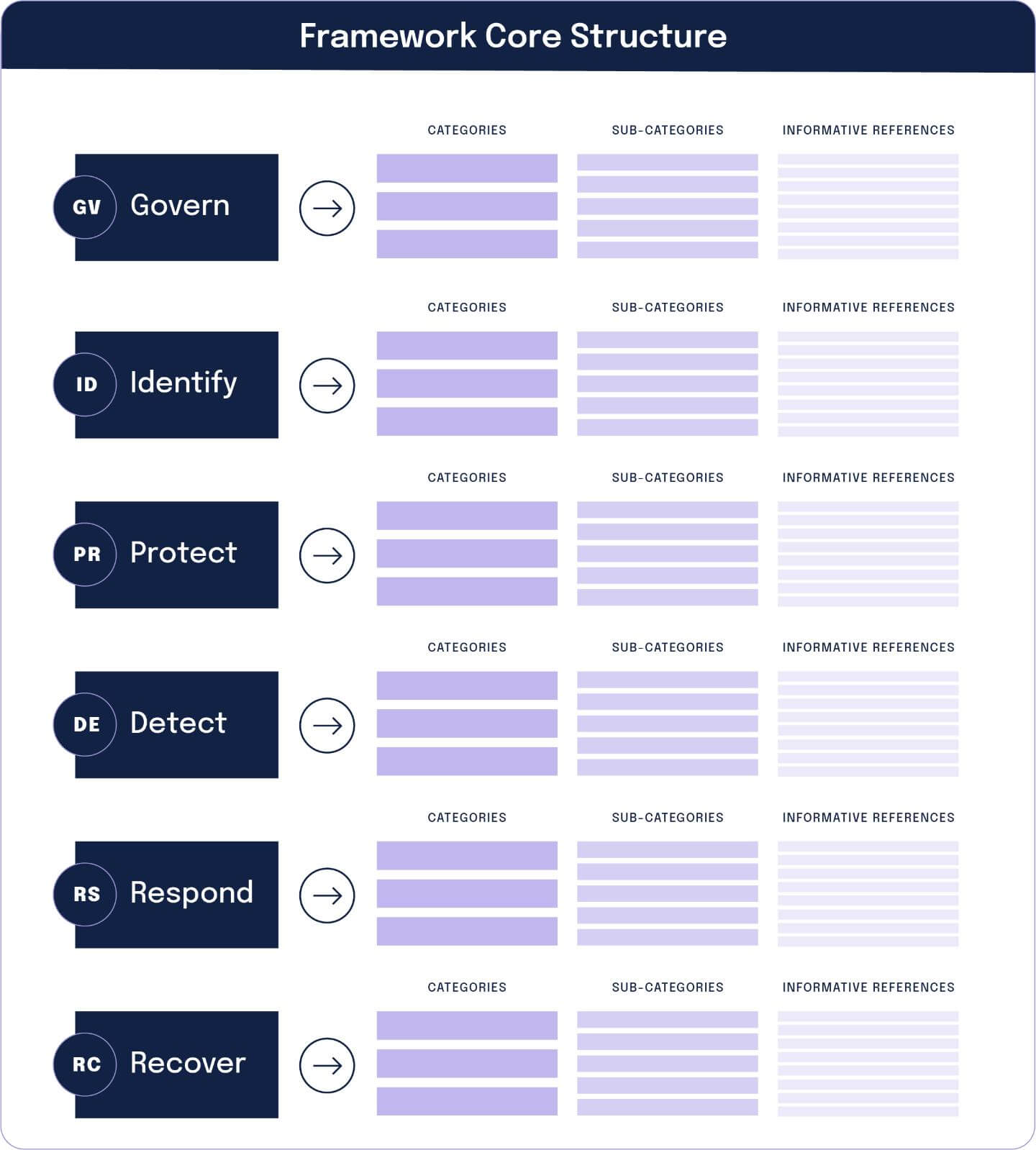
The framework core is the heart of NIST CSF and is an essential matrix designed to guide cybersecurity risk management programs. The framework core discusses activities incorporated in cybersecurity programs, which can be tailored to an organization’s unique needs. These critical security activities are detailed in a hierarchy of three components – functions, categories, and subcategories.
The 6 NIST CSF Functions
Functions represent the overarching cybersecurity activities. There are six functions – Govern, Identify, Protect, Detect, Respond, and Recover. Together, these functions form a comprehensive cybersecurity risk framework that helps organizations manage cyber risk consistently across governance, operations, and recovery.
Govern
Establish and monitor your company’s cybersecurity risk management strategy, expectations, and policy.
Identify
Have a clear understanding of cybersecurity risks and how to prioritize actions effectively.
Protect
Implement safeguards to prevent or reduce cyber threats. These could include educating staff to recognize risks, establishing procedures to improve network security, and considering liability insurance for financial protection.
Detect
Develop strategies to quickly identify cyber attacks and cybersecurity incidents through monitoring. This involves implementing data classification, asset management, and risk management protocols.
Respond
Have the steps for what should happen after identifying a cybersecurity incident documented. This should include clear communication with staff, shareholders, partners, and customers, as well as law enforcement and legal counsel.
Recover
Plan the restoration of any impaired capabilities or services following a cyber attack, ensuring the organization can swiftly recover.
Categories
Categories break down each function into clusters of highly detailed cybersecurity objectives. Category examples include asset management, identity management and access control, and detection processes.
Subcategories
Subcategories further refine each category into specific outcomes, such as cataloging external information systems and protecting data at rest.
3 Framework profiles
Framework profiles illustrate how NIST CSF can be tailored to suit specific organizational needs. The profiles describe an organization’s current cybersecurity posture and desired target outcomes based on business objectives, risk appetite, and resources. Comparing current profiles with target profiles helps teams identify opportunities for improvement.
How to use NIST CSF
As the NIST CSF allows flexibility for all organizations, its usage varies greatly depending on individual business needs. However, some common patterns of use exist, which include:
1 Examine current state
This stage includes identifying security priorities/vulnerabilities/risks, determining compliance requirements, and reviewing existing security policies and practices.
2 Conduct an assessment
This stage includes reviewing vulnerabilities, identifying threats while defining probability and likelihood, categorizing risks, and creating a risk heat map.
3 Identify your target state
This stage includes identifying mitigation options, translating mitigation into desired outcomes while defining goals for the outcomes and managing security priorities.
4 Plan your roadmap
This final stage involves quantifying and grading the current state, establishing a budget and identifying resources, defining targets within the budget, and sharing the results with stakeholders.
5 Implement and update
This final stage involves implementing the action plan through management, programmatic, and technical controls, and continuously updating the profile based on monitoring results and changing risk conditions.
A brief history of NIST CSF
With its trusted reputation as an unbiased source of cybersecurity best practices, the National Institute of Standards and Technology (NIST) was selected to develop a cybersecurity framework in response to Executive Order 13636.
Executive Order 13636 aimed to improve the overall security and resilience of the nation’s critical infrastructure and was signed by President Obama on February 12th, 2013 – kicking off the development of NIST CSF.
To successfully develop NIST CSF, NIST collaborated with stakeholders from the federal government, security industry, and academia. Collecting all of the required information, identifying any gaps, making necessary edits, and putting together an action plan took the organization a little over a year.

How do I implement NIST CSF?
To implement the framework, an organization must follow the guidelines outlined in the framework and maintain these practices over time. NIST does not have a formal audit process or attestation for NIST CSF. Instead, NIST encourages organizations to determine their conformity needs and develop their own assessment programs. Implementing NIST CSF protects not only your organization but your customers, partners, and third-party vendors as well.
Blog
To learn more about implementing NIST CSF, check out our step-by-step guide on NIST CSF compliance.
What are the benefits of implementing NIST CSF?
NIST CSF is an excellent framework to help your organization govern, identify, detect, protect, respond to, and recover from cyber risk, as well as deliver valuable business benefits, which include:

How to prepare for implementing NIST CSF
To best prepare for implementing NIST CSF, you can take the following five steps:
Step 1
Understand the three key components of the framework: Implementation tiers, framework core, and framework profiles.
Step 2
Evaluate your organization’s current cybersecurity practices.
Step 3
Outline your current cybersecurity controls and practices.
Step 4
Identify areas of improvement by comparing where your organization currently is against the NIST CSF requirements.
Step 5
Develop an action plan for implementing the framework.
An outline of the assessment process
Although NIST CSF does not have a formal attestation process, you can still assess your organization’s security posture using NIST CSF. Through internal or external control assessments, NIST CSF serves as a framework for organizations to assess their resilience goals, including incident response, risk management, and business continuity.
While there’s an industry standard for assessing the maturity of these goals, the benchmarks used vary among organizations and assessors.
An assessment doesn’t determine compliance with NIST CSF; rather, it gauges the maturity of an organization’s readiness to handle and respond to incidents. Typically, this assessment is followed by recommendations for improvement.
Unlike standards like SOC 2® or ISO 27001, NIST CSF assessments don’t yield a binary compliance judgment. Instead, they categorize organizations into various maturity levels within the NIST CSF criteria.
NIST CSF: Frequently Asked Questions
Hyperproof makes implementing NIST CSF easy

Ready to see how Hyperproof can help with NIST CSF?












