A Buyer’s Guide to Modern Third-Party Risk Management
A decade ago, “vendor management” primarily meant maintaining a spreadsheet of suppliers, signing a contract, and revisiting it at renewal time. That approach is now dangerously outdated.
Third parties now sit at the center of your digital operations: cloud providers, AI services, outsourced developers, payment processors, logistics partners, and more. When one of them is compromised, you make the headlines, and you face the regulators.
Recent research shows why buyers are rethinking their approach. IBM’s 2024 Cost of a Data Breach Report found the average breach now costs $4.88 million globally. Meanwhile, multiple analyses of the Verizon Data Breach Investigations Report and other sources indicate that around 30% of data breaches now involve a third-party vendor or supplier, roughly double the prior year.
Another study from SecurityScorecard estimates that at least 35.5% of all breaches in 2024 originated from third-party compromises.
If you’re evaluating modern third-party risk management (TPRM) platforms, you’re not just buying software, but also buying resilience for your entire ecosystem. This guide walks through what has changed, what to look for in a modern solution, and how Hyperproof can help you operationalize a smarter, AI-enabled TPRM program.
From traditional to modern TPRM
Traditional vendor management was largely reactive, with one-time due diligence at onboarding, annual questionnaires (at best), static contracts with limited security clauses, and manual tracking in spreadsheets, email, or generic ticketing systems.
This model no longer works in an environment where vendors push code multiple times a day, AI systems constantly change models and data flows, and fourth and nth parties (your vendors’ vendors) quietly expand your attack surface.
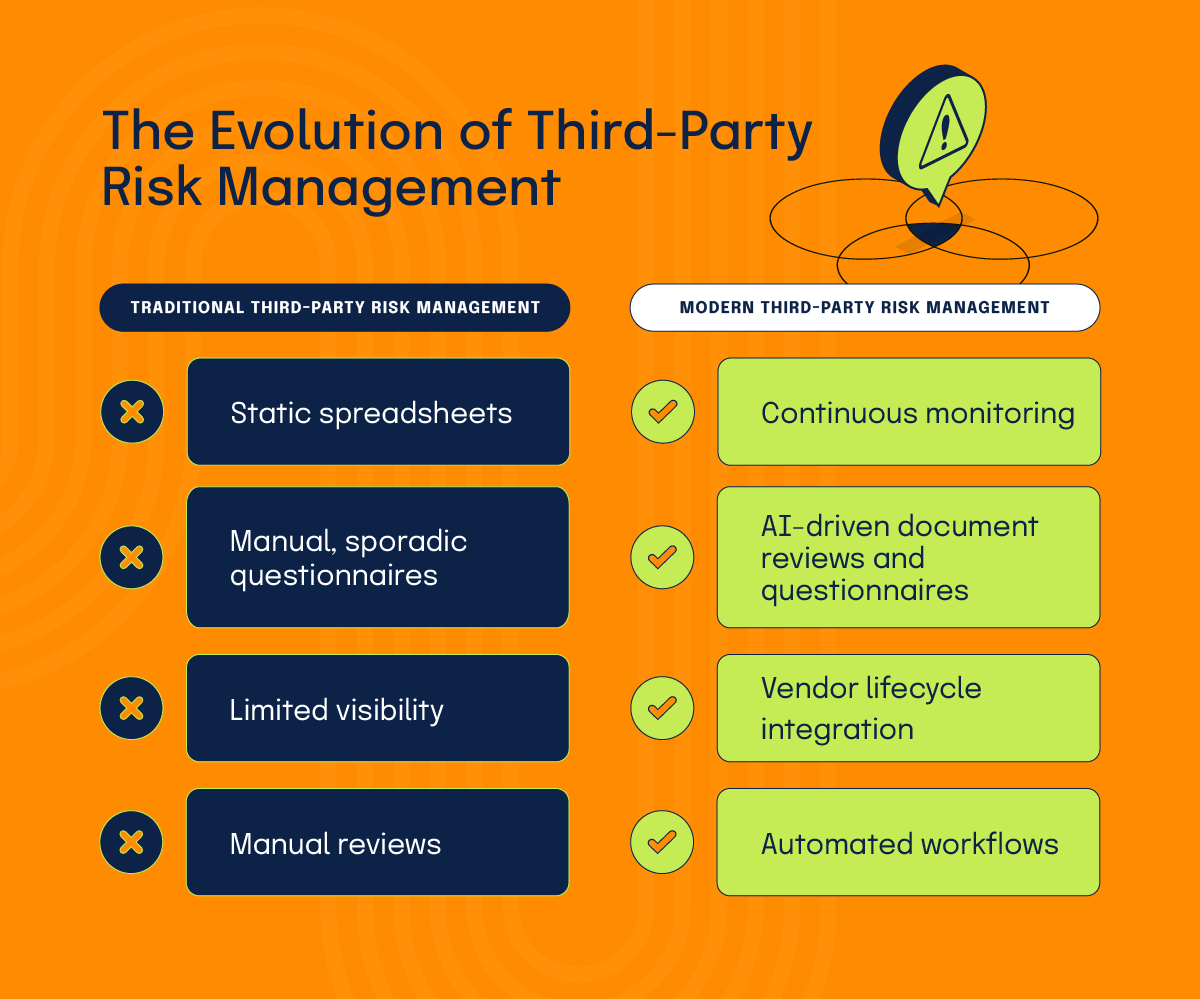
Modern TPRM has evolved into comprehensive ecosystem risk management. That shift involves:
1. A transformation from vendor oversight to ecosystem visibility
Instead of treating each supplier in isolation, leading programs maintain:
2. Moving beyond point-in-time reviews to continuous assurance
Modern programs don’t assume a vendor that passed last year’s assessment is still safe today. They:
3. Transitioning from check-the-box compliance to risk-informed business enablement
Mature teams use TPRM to:
In other words, TPRM has moved from being a compliance tax to a strategic capability.
Why is TPRM changing so quickly?
A few key drivers shaping the third-party risk management landscape:
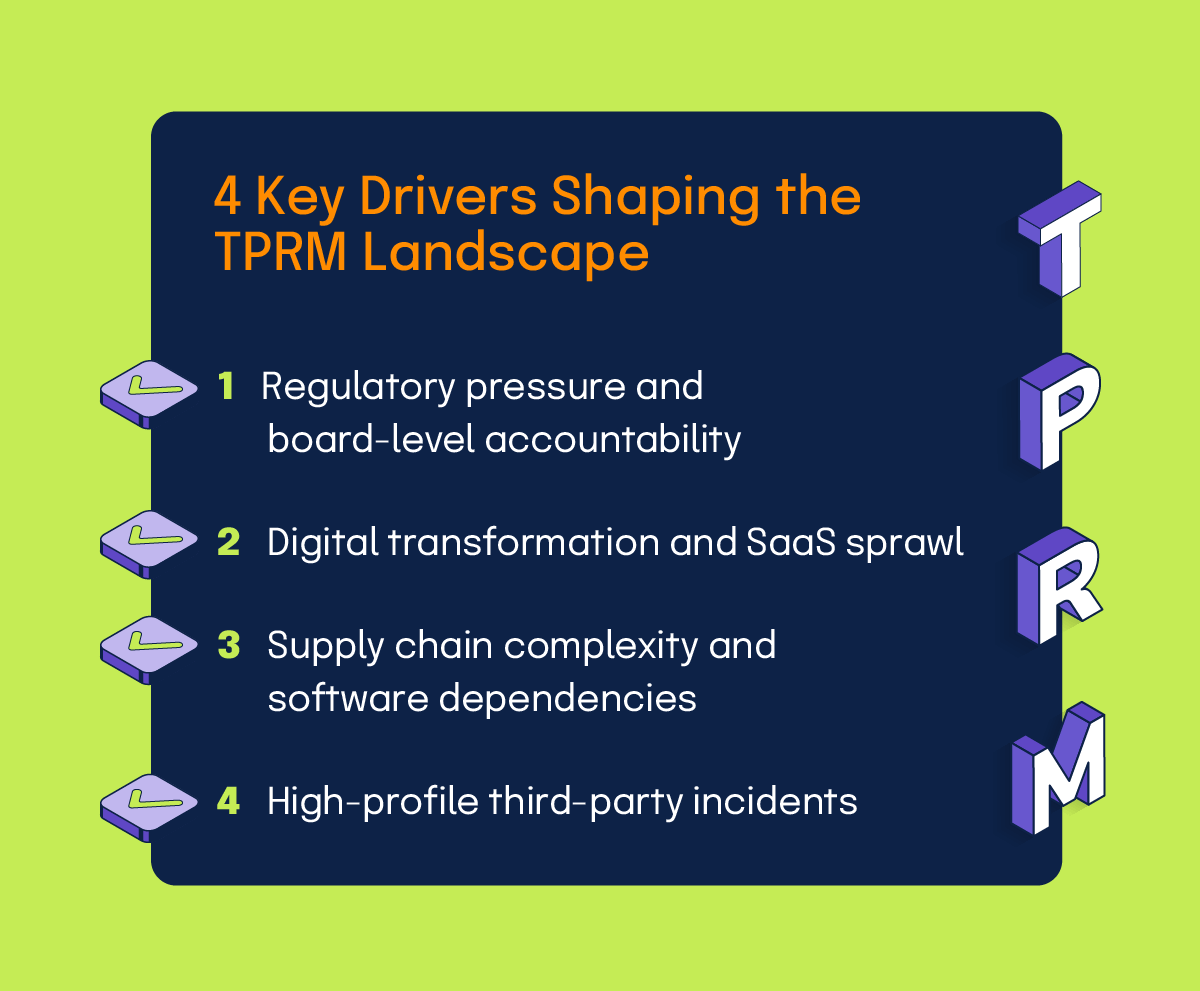
1. Regulatory pressure and board-level accountability
Regulators around the world have made third-party and supply chain risk explicitly your problem. NIS2 requires “comprehensive supply chain risk management” and makes boards directly accountable for third-party security. Non-compliance can mean fines up to €10 million or 2% of global annual turnover. DORA treats ICT third-party risk as an integral part of operational resilience and mandates detailed contractual provisions, ongoing monitoring, and registers of all ICT service providers.
The SEC’s new public disclosure rules require public companies to promptly disclose material cyber incidents, even if they originate in third-party systems, and describe their cyber risk management and governance practices. Add GDPR-sized penalties (up to €20M or 4% of global turnover) for mishandling personal data, and the message is clear: “We didn’t own that system” is not a defense.
2. Digital transformation and SaaS sprawl
Organizations now rely on hundreds — or thousands — of external services, often procured by teams outside of IT. Shadow SaaS and shadow AI introduce unmanaged data flows and permissions that expand your risk surface faster than traditional processes can track.
3. Supply chain complexity and software dependencies
Software supply chain attacks are surging, as attackers exploit weaker controls at smaller vendors to reach bigger targets. Recent coverage shows supply-chain breaches doubling and becoming “unmanageable” for many businesses.
4. High-profile third-party incidents
From outsourced service providers to payroll systems and marketing platforms, third-party incidents repeatedly show that your security is only as strong as your least mature vendor. These breaches bring not just technical cleanup, but multi-million-dollar fines, lawsuits, and brand damage.
The true cost of inadequate third-party risk management
Underinvesting in TPRM shows up across two key dimensions:
Regulatory fines and legal exposure
Regulators have made it unmistakably clear: organizations are accountable not only for their own cybersecurity posture but also for the security practices of every vendor, supplier, and outsourced service provider they rely on. This shift means that even if a breach originates from a third party’s system, the organization that entrusted data to that vendor often bears significant regulatory and legal consequences.
Across major regulatory frameworks — including privacy, operational resilience, financial services, and critical infrastructure —regulators now explicitly spell out third-party risk oversight as a requirement. Many jurisdictions mandate continuous monitoring, detailed contractual controls, and demonstrable due diligence over third parties, not just point-in-time reviews. Failing to meet these standards can result in:
Multi-million-dollar fines tied to global revenue
Modern regulations increasingly scale penalties based on global annual turnover, not local business impact. This dramatically increases the stakes for multinational organizations. Even a single third-party incident involving mishandled personal data, operational disruption, or failure to implement “appropriate technical and organizational measures” can trigger penalties that materially affect financial performance.
Expanded disclosure obligations
Organizations are now required to promptly disclose material cyber incidents, whether the incident originated internally or through a vendor. When vendor-related incidents lead to delayed or incomplete disclosure, regulators may pursue enforcement actions for failing to provide accurate and timely information to investors, customers, or supervisory authorities.
Civil litigation and shareholder action
After a third-party breach, organizations may face:
These legal battles often extend months or years beyond the breach itself, compounding costs and reputational damage.
2024’s Change Healthcare breach was a prime example of the cost of underinvesting in third-party risk management.

Contractual and commercial penalties
Many customer contracts now include strict data protection, uptime, and security clauses. A vendor-caused outage or data leak can trigger:
In regulated industries, these contractual failures may also prompt supervisory reviews or audits into the organization’s TPRM practices.
In short: inadequate third-party oversight doesn’t just create operational risk—it invites regulatory scrutiny, legal exposure, and financial penalties that can eclipse the cost of a robust TPRM program many times over.
2. Business disruption and lost growth
Third-party incidents rarely stay contained to the vendor. They often ripple across your entire business, halting operations, disrupting product development, delaying revenue, and straining customer trust. When an external partner experiences a security failure, your team inherits both the downstream consequences and the responsibility to respond quickly and transparently.
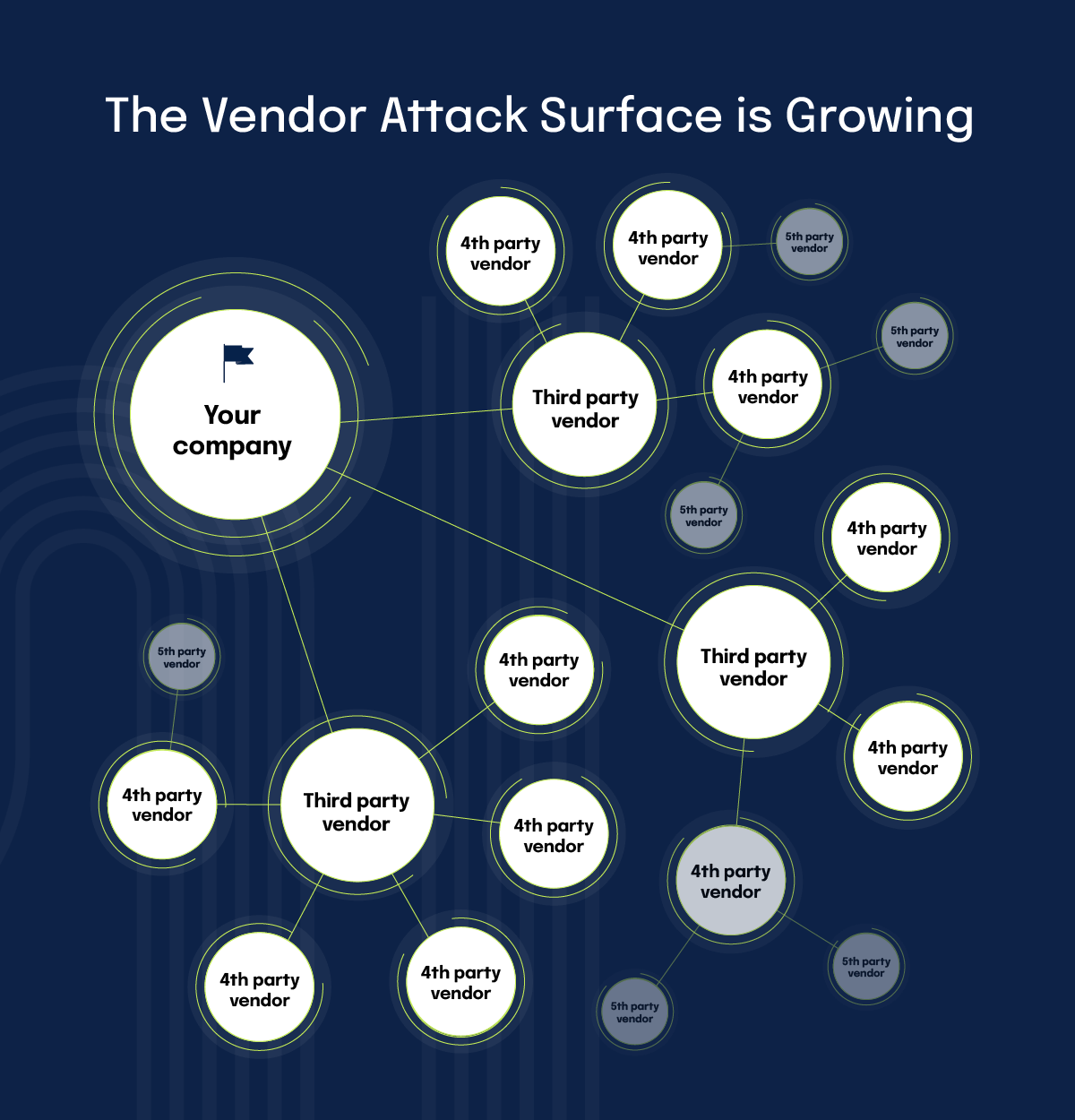
Operational downtime and cascading disruption
Many organizations depend on vendors for mission-critical services such as authentication, payments, hosting, logistics, analytics, or AI infrastructure. When these services go offline due to an incident, the impact can be immediate and severe:
Even short outages can compound into missed SLAs, shipping delays, service credits, or production backlogs.
Delayed product launches and halted innovation
Vendor failures can derail strategic initiatives, especially when they involve outsourced development, infrastructure providers, or specialized technology. Organizations often must:
When this happens, competitors with more resilient vendor ecosystems can move faster, leaving your organization at a strategic disadvantage.
Lost deals and customer churn
Customers increasingly scrutinize their partners’ supply chain security. Following a third-party incident, prospects may:
Existing customers may reassess whether you remain a “safe bet,” particularly if the incident resulted in downtime or exposed data.
Internal productivity loss and resource strain
Vendor-related incidents often trigger cross-functional emergency response involving:
This resource drain can last weeks or months and pull focus away from strategic projects.
Reputational damage and long-term trust erosion
Even if the breach originates with a vendor, your customers and stakeholders often perceive it as your security failure. Public trust is fragile: once shaken, it becomes harder to win new business, maintain renewals, or assure partners that your risk management program is robust.
What to look for in a modern TPRM platform
When you evaluate TPRM solutions, you’re really asking: Can this platform keep pace with my vendors, my regulators, and my business? Modern platforms use AI and automation to move beyond manual, questionnaire-only workflows:
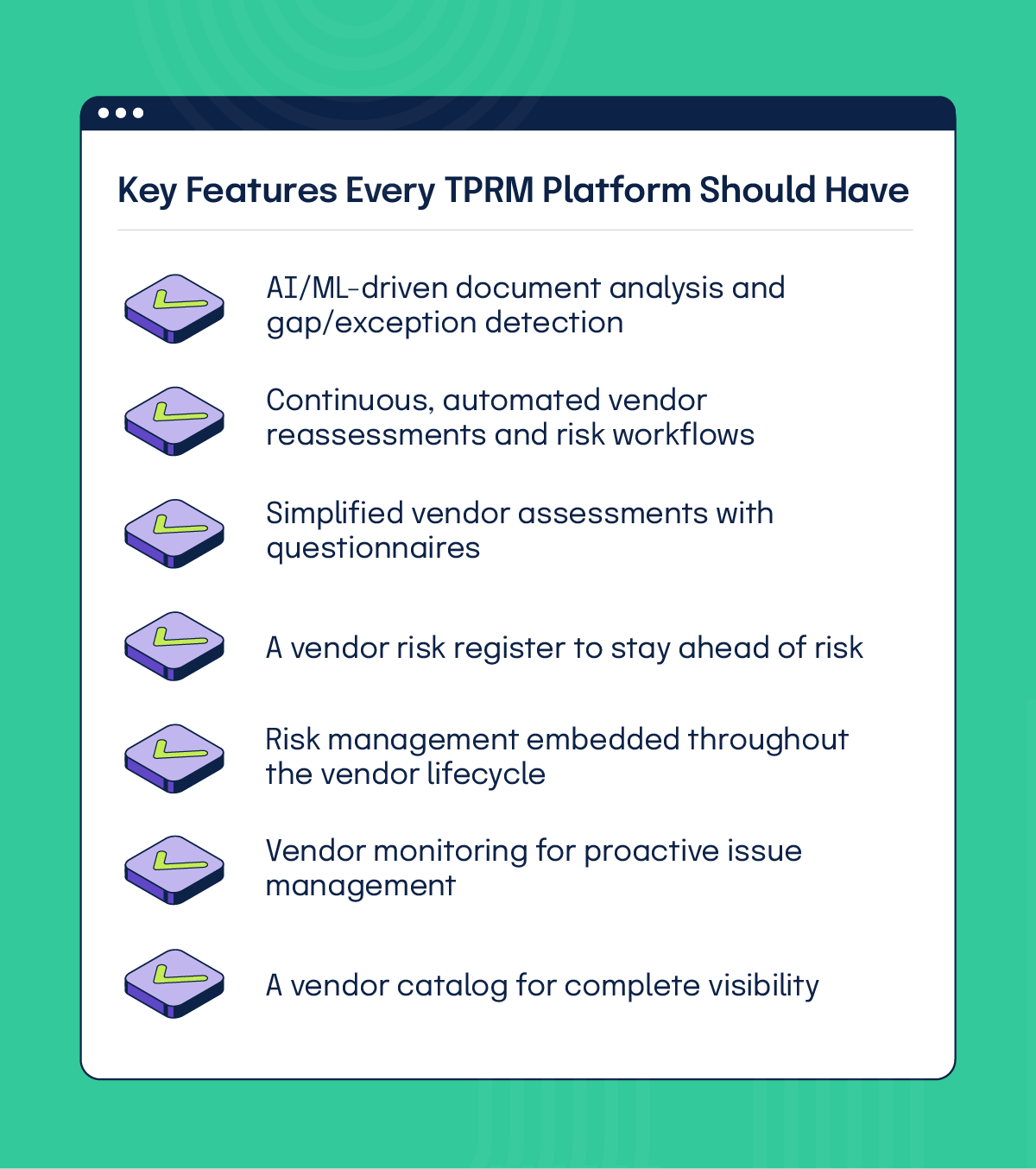
AI/ML-driven document analysis and gap/exception detection
Modern solutions automatically ingest and analyze vendor-provided artifacts like security reports, policy documents, and compliance certificates. They then detect gaps and exceptions, map controls to frameworks, and reduce manual review effort, helping teams assess vendor risk with accuracy and consistency.
Continuous, automated vendor reassessments and risk workflows
Your third-party risk management platform should trigger vendor reassessments automatically based on thresholds or timeframes. It should also prioritize vendors by tier and route tasks through pre-built workflows, keeping reviews consistent, efficient, and fully auditable.
Simplified vendor assessments with questionnaires
The right platform should enable you to create, distribute, and track questionnaires across any framework — like ISO 27001, SOC 2®, PCI DSS, and more — or assessment type. It should allow you to build from templates or customize per vendor with configurable sections, conditional logic, and scoring models to ensure complete, standardized evaluations.
A vendor risk register to stay ahead of risk
Every third-party risk management system needs a unified, dynamic view of vendor risks across your ecosystem. You should be able to automatically identify, categorize, and prioritize issues by severity and likelihood, and collaborate with vendors and stakeholders through remediation.
Risk management embedded throughout the vendor lifecycle
From intake and sourcing to contract renewal, risk management should be built into your third-party risk management system, not bolted on. Your TPRM solution should connect procurement, legal, and security workflows, ensuring that current risk data informs every vendor decision.
Vendor monitoring for proactive issue management
A quality solution should continuously scan public sources for breach disclosures, security incidents, and compliance lapses to surface real-time external risk indicators. This way, your teams can act before small issues become major exposures.
A vendor catalog for complete visibility
Every vendor, assessment, and contract should be visible in one connected catalog. The right TPRM solution will let you filter by risk tier, framework, or lifecycle stage to streamline governance, accelerate audits, and drive informed sourcing decisions.
Questions to ask when evaluating a third-party risk management solution:
Implementation planning: data migration and change management
Even the best TPRM platform won’t deliver value if implementation stalls. Two areas deserve special attention.
1. Data migration and system integration planning
You’ll need a clear plan to move from your current state (spreadsheets, shared drives, legacy tools) to a centralized system:
Vendor inventory rationalization
Consolidate and dedupe vendors from across IT, procurement, finance, and business units. Then, map each vendor to owners, data types, and criticality.
Risk category and framework mapping
Align existing risk ratings, questionnaires, and findings to standard categories and map to internal risk taxonomy and external frameworks (NIST, ISO, DORA, NIS2, etc.).
Data quality integration
Clean up inconsistent vendor names, IDs, and contact data, and decide which system of record “owns” which data elements. Validate API connections early using real vendor records.
2. Change management and user adoption strategies
TPRM is inherently cross-functional. To drive adoption:
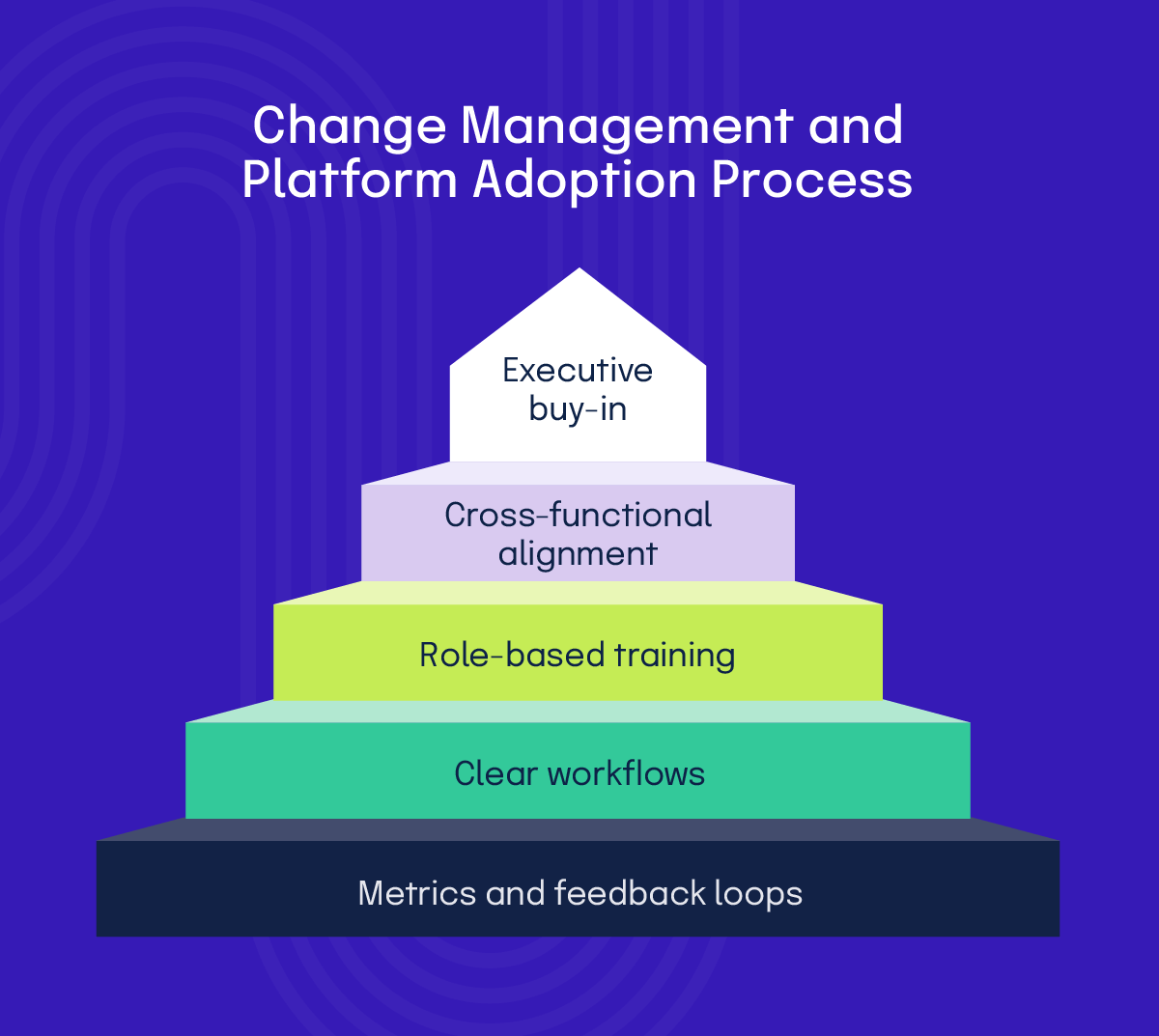
1. Engage stakeholders early
Involve security, privacy, procurement, legal, finance, and key business units in design decisions. One way to boost engagement is to identify executive sponsors who can champion the program and loop them in before implementation has even started.
2. Design intuitive workflows
Make it easy for risk owners to review and approve vendors. Give procurement simple ways to trigger risk workflows during intake using a consolidated, seamless platform.
3. Train and communicate
Your new TPRM program is only as successful as its people. Offer role-based training for analysts, requestors, approvers, and executives and share before-and-after metrics (e.g., time to onboard vendors) to reinforce value throughout the training process.
Measuring success and optimizing ROI
To prove the value of your TPRM investment and continuously improve, define metrics in three areas:

Identify key KPIs
Knowing how to measure success will set your TPRM program up for success. Examples include:
Understand your cost-benefit analysis
Third-party risk is a classic example where you may never get credit for disasters that didn’t happen, so having a clear baseline and tracking improvements over time is critical. Quantify the following:
Review total cost of ownership (TCO) and licensing models
When comparing platforms, look beyond the subscription price. There are several common models: per vendor, per assessment, and flat platform fees, often combined with implementation and support packages.
When evaluating third-party risk management solutions, factor in:
What to ask during the evaluation process
How Hyperproof can help
Hyperproof is built to help modern GRC and security teams transform third-party risk from a painfully manual process into a continuously managed, AI-assisted program.
At the core of Hyperproof’s approach is RiskAI, our modern third-party risk engine, to help you automate vendor assessments and centralize risk data while streamlining collaboration across security, procurement, and compliance teams. Hyperproof helps you automate the most time-consuming parts of vendor risk management and generate defensible, audit-ready outcomes.
Leverage a modern third-party risk engine with RiskAI
RiskAI automates the analysis of vendor-provided artifacts — like security reports, policy documents, and compliance certificates — so your team isn’t manually combing through PDFs.
With RiskAI, you can:
Instead of spending hours interpreting each document, your analysts review structured findings, validate RiskAI’s recommendations, and focus on decision-making.
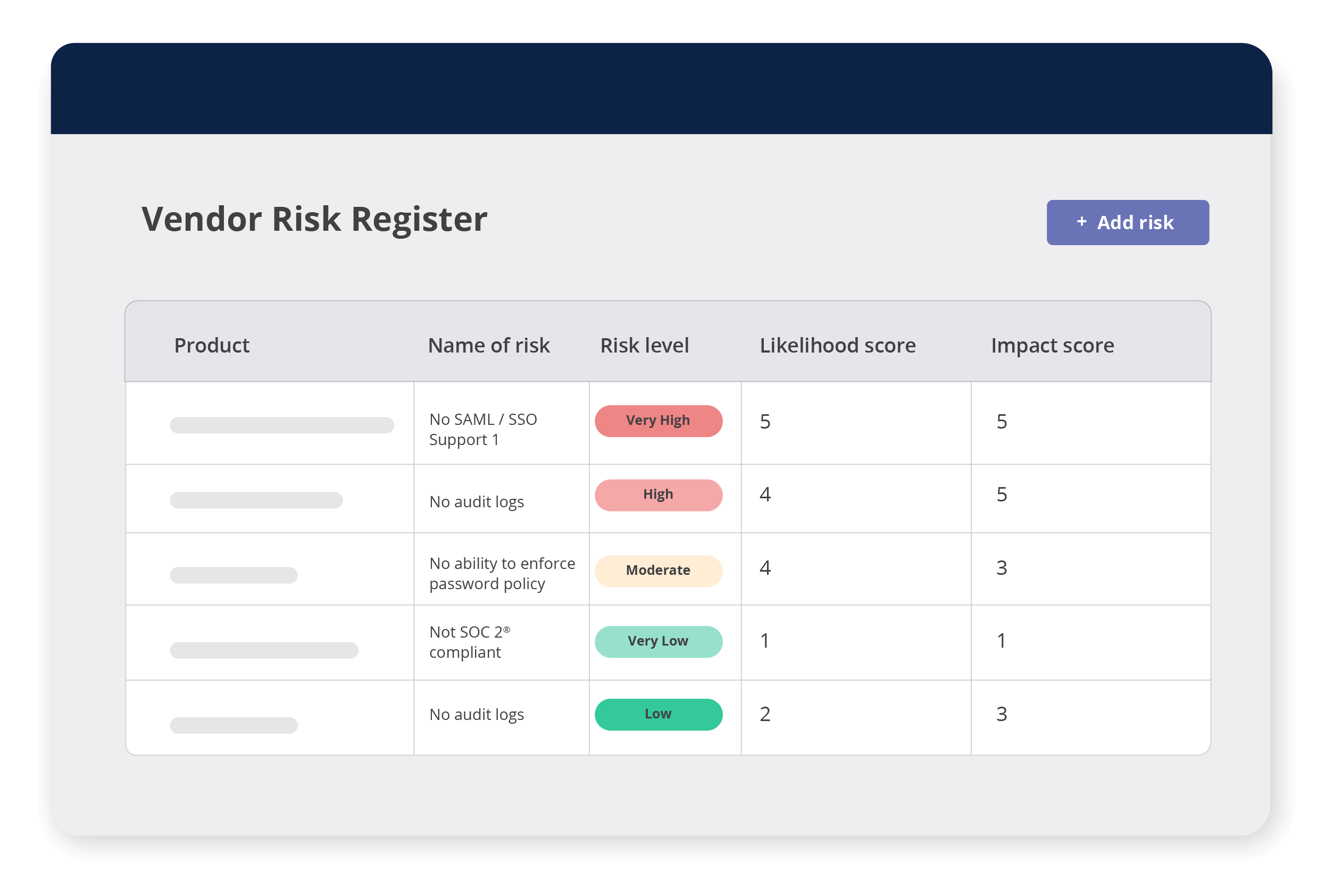
Stay ahead of risk with the vendor risk register
Hyperproof’s vendor risk register gives you a unified, dynamic view of risk across your entire ecosystem:
Security, procurement, and business owners work from the same source of truth, so there’s no debate about which spreadsheet is correct when the board or regulators start asking questions.
Automate continuous assessments and risk workflows
With Hyperproof, you can stop chasing dates in calendars and inboxes:
This automation keeps your program moving, even as your vendor landscape grows.
Embed risk into every stage of the vendor lifecycle
Hyperproof is designed so risk isn’t a bolt-on step after procurement—it’s woven into the entire lifecycle:
By connecting procurement, legal, and security workflows, Hyperproof ensures every vendor decision is informed by current risk data, not last year’s assumption.
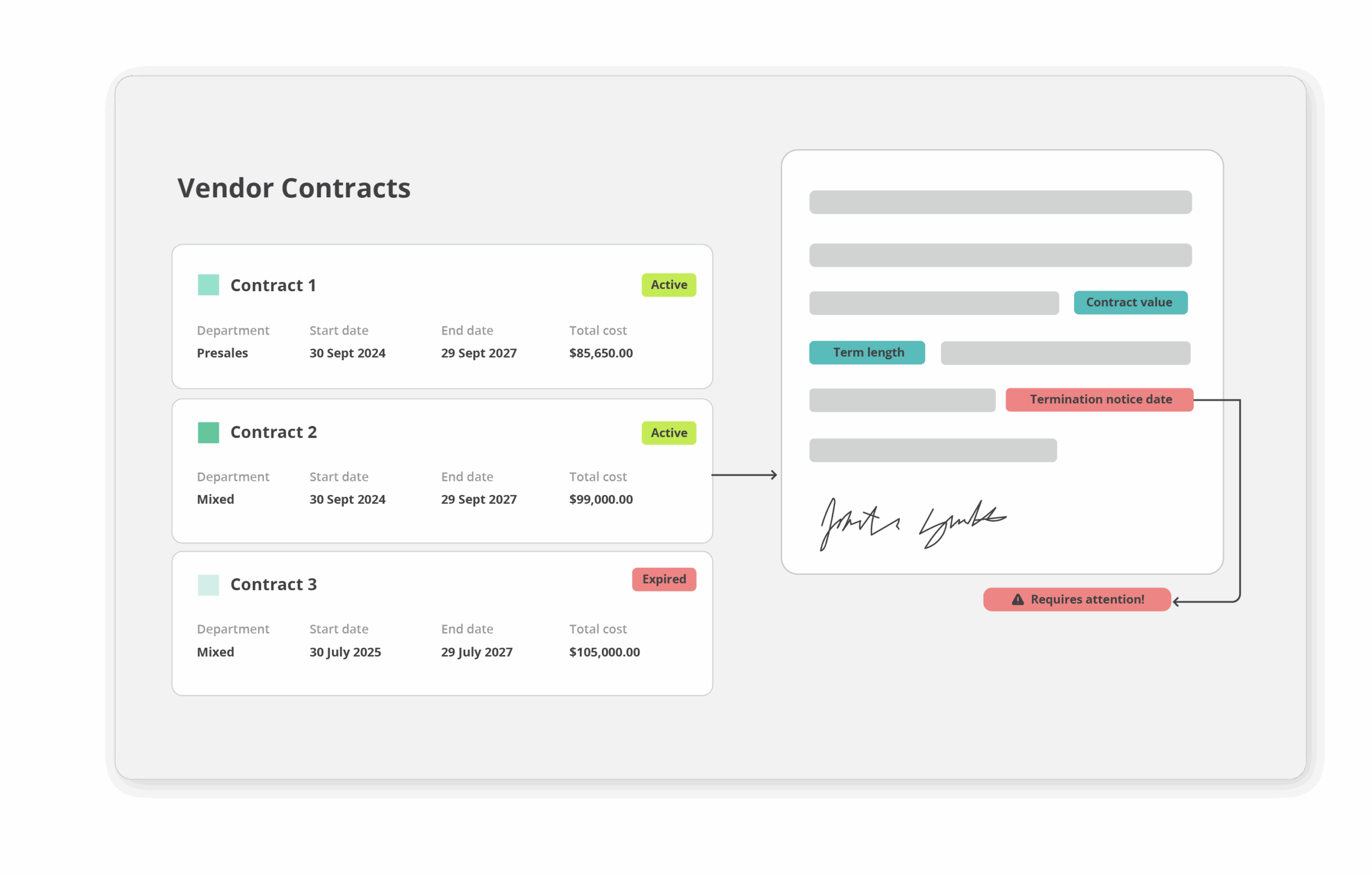
Monitor vendors beyond questionnaires
Questionnaires capture what vendors say they do. Hyperproof helps you align that with what’s happening in the real world.
Our monitoring capabilities continuously scan public sources for:
When something changes, Hyperproof surfaces real-time external risk indicators so your team can:
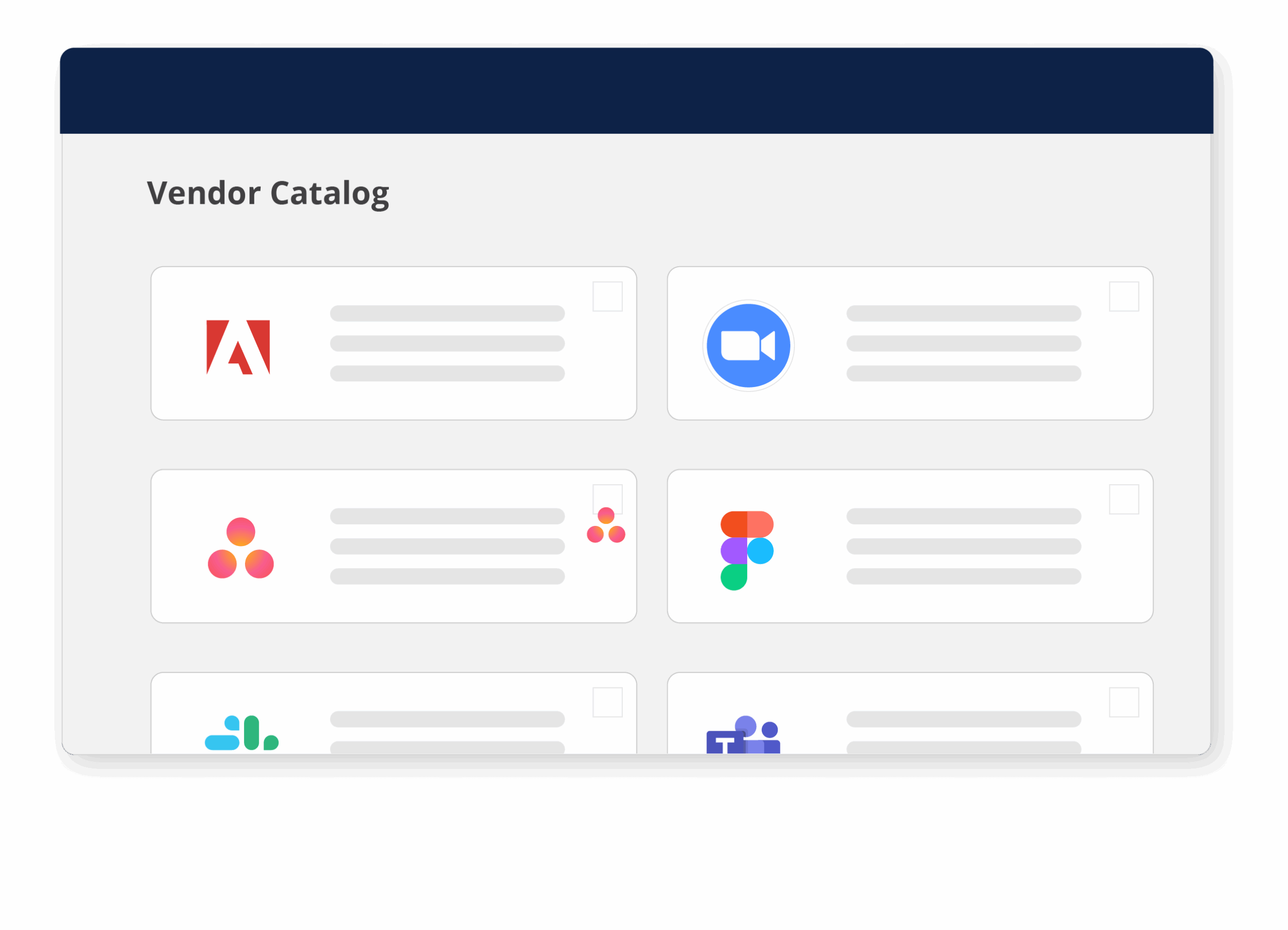
Gain total visibility with the vendor catalog
Finally, Hyperproof’s vendor catalog gives you a single pane of glass across your entire TPRM ecosystem:
For GRC leaders, the vendor catalog becomes the control center for all third-party risk decisions.
Choosing a TPRM platform that can grow with you
As third-party risk becomes a board-level and regulatory priority, spreadsheets and ad-hoc workflows simply can’t keep up. Modern TPRM requires:
Hyperproof is built to help you make that leap, combining our intelligent third-party risk engine (RiskAI), robust workflows, continuous monitoring, and a unified vendor catalog so you can scale TPRM with confidence.
If you’re evaluating TPRM platforms now, your next step is simple: define your critical use cases, map them to the capabilities in this guide, and pressure-test vendors on how they’ll help you operationalize them in your environment.
Your vendors aren’t slowing down. Your TPRM program shouldn’t either.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












