Compliance Automation: How to Get Started
Compliance is about building trust, resilience, and bringing more efficiency to your business. As emerging risks force cybersecurity to evolve, manual compliance processes can no longer keep up with the growing list of regulatory requirements.
Compliance automation helps organizations streamline their compliance programs, reduce manual work, and stay audit-ready. By using modern, AI-powered compliance automation software, you can simplify evidence collection, track controls across multiple frameworks, and manage compliance at scale.
This blog will help you:
The growing compliance challenge
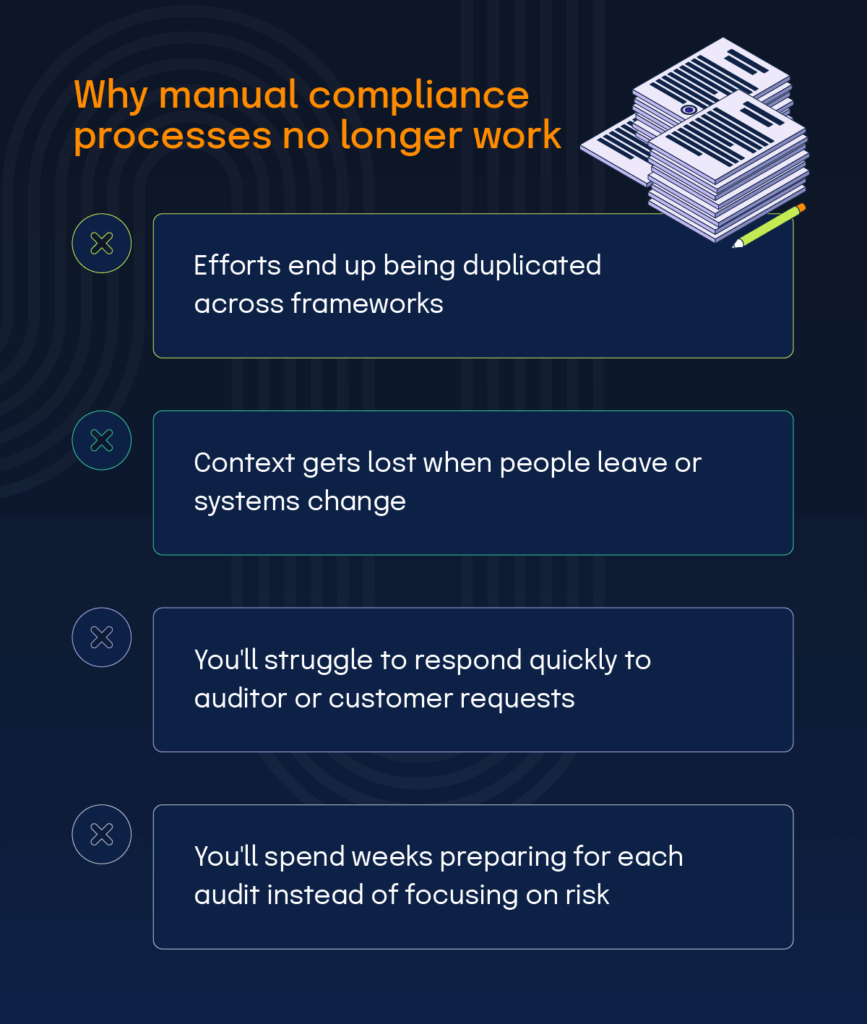
Why does traditional compliance management no longer work?
Compliance programs were previously designed around annual audit reviews, where teams would scramble to collect evidence before a deadline. This approach is no longer practical.
Emerging regulations and customer expectations demand continuous compliance. Continuous compliance is a state where controls are continuously monitored, risks are tracked, and evidence is automatically updated in real-time.
Manual compliance processes simply can’t support this level of responsiveness. Organizations that still rely on spreadsheets and manual checklists often:
To gain a competitive edge, businesses need a smarter, more efficient way to manage compliance from end to end.
Why proactive compliance is no longer optional
Organizations are juggling more regulatory requirements, audits, and risks than ever. Staying compliant with standards like SOC 2®, ISO 27001, and GDPR now requires continuous monitoring, not just periodic checkups.
At the same time, security threats and regulatory scrutiny have intensified. The IBM Cost of a Data Breach Report 2025 found that the global average cost of a data breach is nearly $4.4 million. And now, with new global AI and data privacy regulations, compliance has become a continuous, business-critical process.
Data from Hyperproof’s 2025 IT Risk and Compliance Benchmark Report highlights just how high the stakes have become. Among organizations that manage risk reactively, meaning they address issues only after an incident, 60% experienced a data breach in 2024. In contrast, companies that use integrated and automated GRC tools were far better protected, with just 41% reporting a breach.
This gap highlights the value of automation and proactive, continuous compliance management. Organizations that rely on manual, ad-hoc processes are far more exposed to risk. This is not because they care less about compliance, but because they lack the tools and visibility to manage it effectively.
Unfortunately, most compliance teams are still buried in spreadsheets, email threads, and manual evidence collection. Budgets remain flat while workloads grow, and that’s where automation comes in to help.
There’s a better way to handle security and compliance.

What is compliance automation?
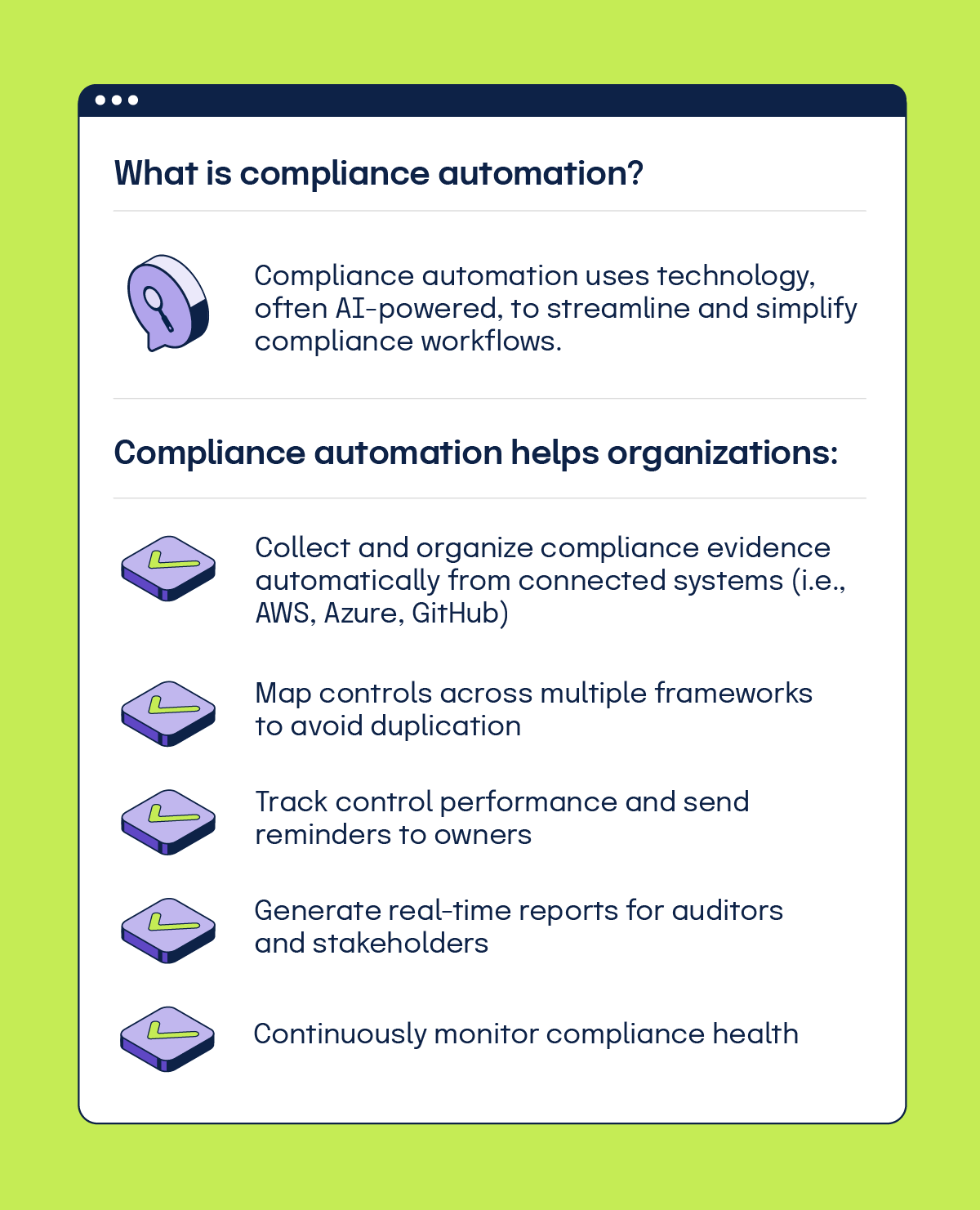
Compliance automation uses technology, often AI-powered,to streamline and simplify compliance workflows. This empowers organizations to scale its activities and resources to meet the demands of an increasing compliance scope. Instead of manually tracking every task, automation handles repetitive work so compliance teams can focus on proactive risk management and strategy. Automation helps organizations:
Artemis Health used Hyperproof to operationalize their compliance program and saw a 50% reduction in time spent on manual processes. These savings come from increased efficiency with automations, leading to a stronger compliance posture.
The business case for compliance automation

Compliance automation makes compliance efforts easier, but it also delivers tangible business benefits across operations, security, and revenue growth. Here are a few benefits of compliance automation:
1. Save time and reduce costs
By automating evidence collection and control monitoring, organizations free up hundreds of hours per audit cycle. That means less time spent chasing documentation and more time focused on improving processes.
Wondering how much an AI-powered GRC platform can save you?

2. Improve accuracy and reduce risk
Manual processes can lead to missing or outdated evidence. Automation ensures that controls are consistently tested, evidence is always current, and audit trails are complete. This can drastically reduce the risk of non-compliance or failed audits.
3. Support business growth
A healthy compliance posture gives organizations a competitive edge. More and more prospective customers are asking for security documentation during procurement. When your compliance posture is strong, you can quickly share verified reports and questionnaires, accelerating deals and strengthening trust.
4. Empower teams and prevent burnout
Automation eliminates repetitive manual work, allowing compliance professionals to focus on higher-value tasks like assessing risks, improving policies, and aligning security strategy with business goals.
5. Enable continuous compliance
Instead of scrambling for evidence once a year, automation keeps your organization compliant all the time. With real-time dashboards and alerts, you can identify and address issues before they become audit findings or security incidents.
How to get started with compliance automation
Implementing compliance automation is easier when you follow a structured approach. Whether you are just beginning to formalize your compliance program or looking to scale what you already have, this practical checklist will help guide your efforts:

Diagnose your compliance and security challenges
Many CISOs and compliance leaders today are facing the same issue: compliance workloads keep growing while resources stay flat. The explosion of new data privacy, cybersecurity, and AI regulations around the world has made compliance an ongoing process.
These rules require continuous monitoring of data protection and internal controls, and they hold organizations accountable not only for their own practices but also for those of their vendors. That means your company’s compliance success is directly tied to your ability to manage vendor risk effectively.
This complexity helps explain why compliance often consumes such a large portion of security budgets. Research from Hyperproof’s 2025 IT Risk and Compliance Benchmark Report reinforces this trend:
74% of respondents reported annual security budgets exceeding $1 million, and 52% said they spend 30–50% of their time on administrative tasks like manual data entry. Even as 63% plan to increase GRC budgets and 72% expect to grow their compliance teams in 2025, organizations continue to grapple with the resource burden of managing compliance complexity at scale.
A big reason is duplication. Large organizations may have to comply with multiple frameworks (i.e. SOC 2Ⓡ, ISO 27001, NIST, GDPR, HIPAA, PCI-DSS) each with slightly different requirements. Without automation, teams end up redoing similar work for each standard.
Meanwhile, customers and sales prospects continue to demand proof that their data is safe. Security questionnaires, audit requests, and risk assessments aren’t slowing down. To keep up, organizations must evolve beyond reactive compliance practices and toward proactive, automated compliance operations.
When you diagnose where your compliance program struggles, whether it’s evidence collection, control tracking, or reporting, you’ll have a clear picture of where automation can create the most impact.
Use strategic compliance automation solutions
Once you understand your compliance challenges, the next step is to apply the right tools and technology to address them.
This is where compliance automation software becomes invaluable. It helps organizations integrate compliance into their daily operations so they can manage risk continuously, not reactively.
Modern, AI-powered compliance automation tools should allow you to:
When compliance automation is strategically implemented, it connects your governance, risk, and compliance functions into one cohesive system. You can prove compliance to customers and regulators more efficiently. It will also free your risk and compliance teams to focus on protecting the business instead of preparing for audits.
Ultimately, automation allows you to align compliance with your broader business goals. By continuously monitoring controls and demonstrating compliance on demand, you strengthen your organization’s credibility, improve vendor trust, and create a competitive advantage.
Address challenges and ensure long-term success
Even with the right tools, successful compliance automation requires thoughtful implementation and ongoing management.
Start by assigning clear ownership of the project. In smaller organizations, this might fall to the CISO or security director. Larger companies may need a cross-functional compliance team that includes representatives from security, legal, IT, and operations. The key is to ensure that someone has both the authority and the time to drive progress.
Next, identify and document your controls so you can map them to regulatory requirements. This is when you can perform a gap assessment to show where controls don’t meet standards and to plan remediation effectively.
As your organization grows or processes change, review your controls regularly. Automation can help flag when controls are outdated, missing, or untested, but human oversight ensures they still align with current operations.
Finally, frame automation as an investment in risk management, not just a compliance task. When you can demonstrate that automation reduces risk exposure, cuts costs, and improves security outcomes, you’ll have an easier time gaining and maintaining executive support.
Hyperproof can help you automate compliance tasks
Hyperproof’s AI-powered compliance operations platform helps organizations reduce manual work, improve visibility, and achieve continuous compliance. Our platform is built to simplify and scale compliance programs across frameworks like SOC 2Ⓡ, ISO 27001, NIST, PCI-DSS, and more.
Here’s how Hyperproof helps:
Reduce time spent tracking down information
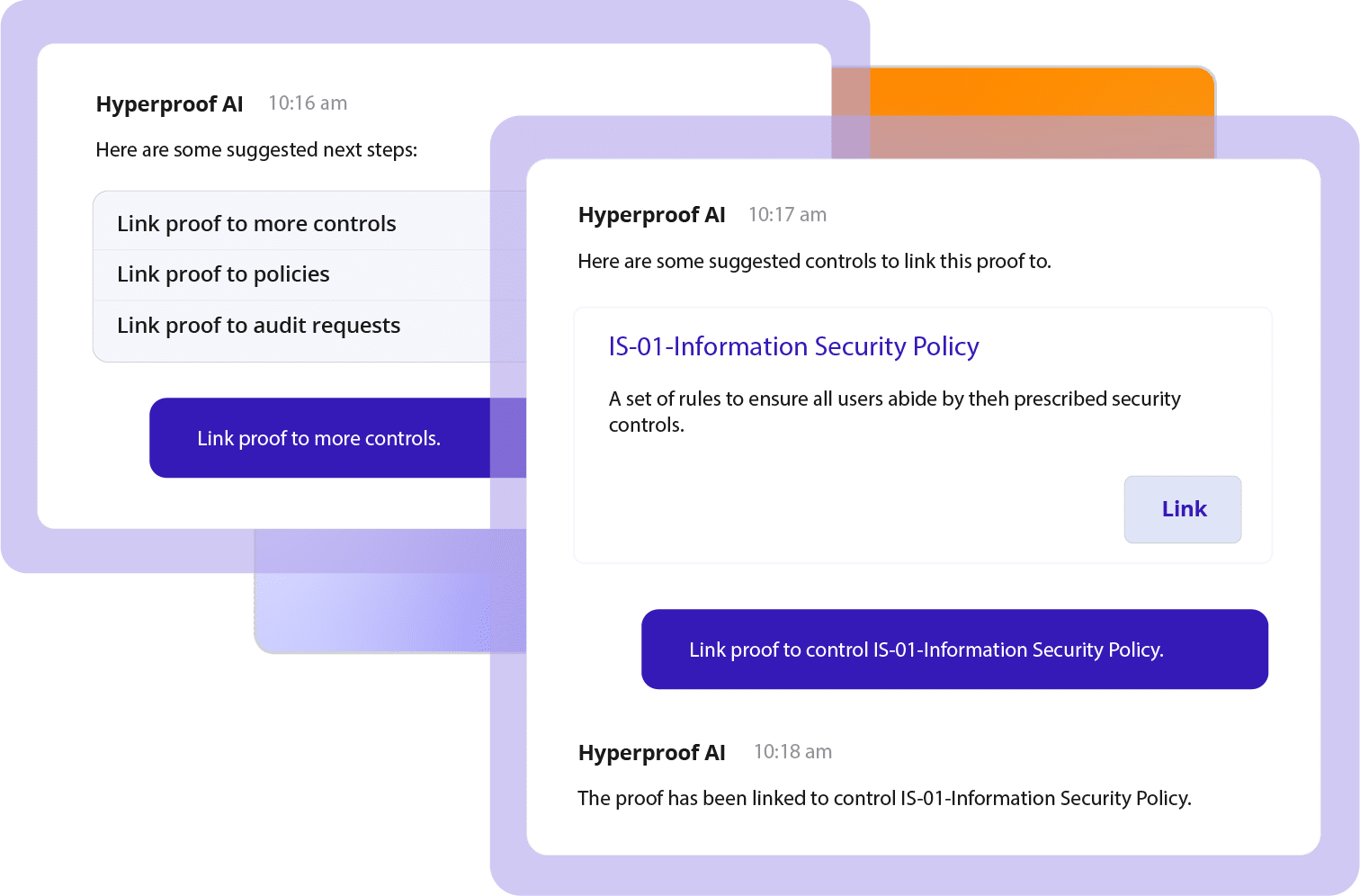
Manage all compliance tasks, controls, and evidence in one place. Document controls, map them to multiple frameworks, and assign owners. All evidence stays organized and audit-ready, no more lost context or redundant work. Plus, with Hyperproof AI’s Discover agent you can easily research, monitor, and locate compliance data across your systems.
Minimize duplicative effort
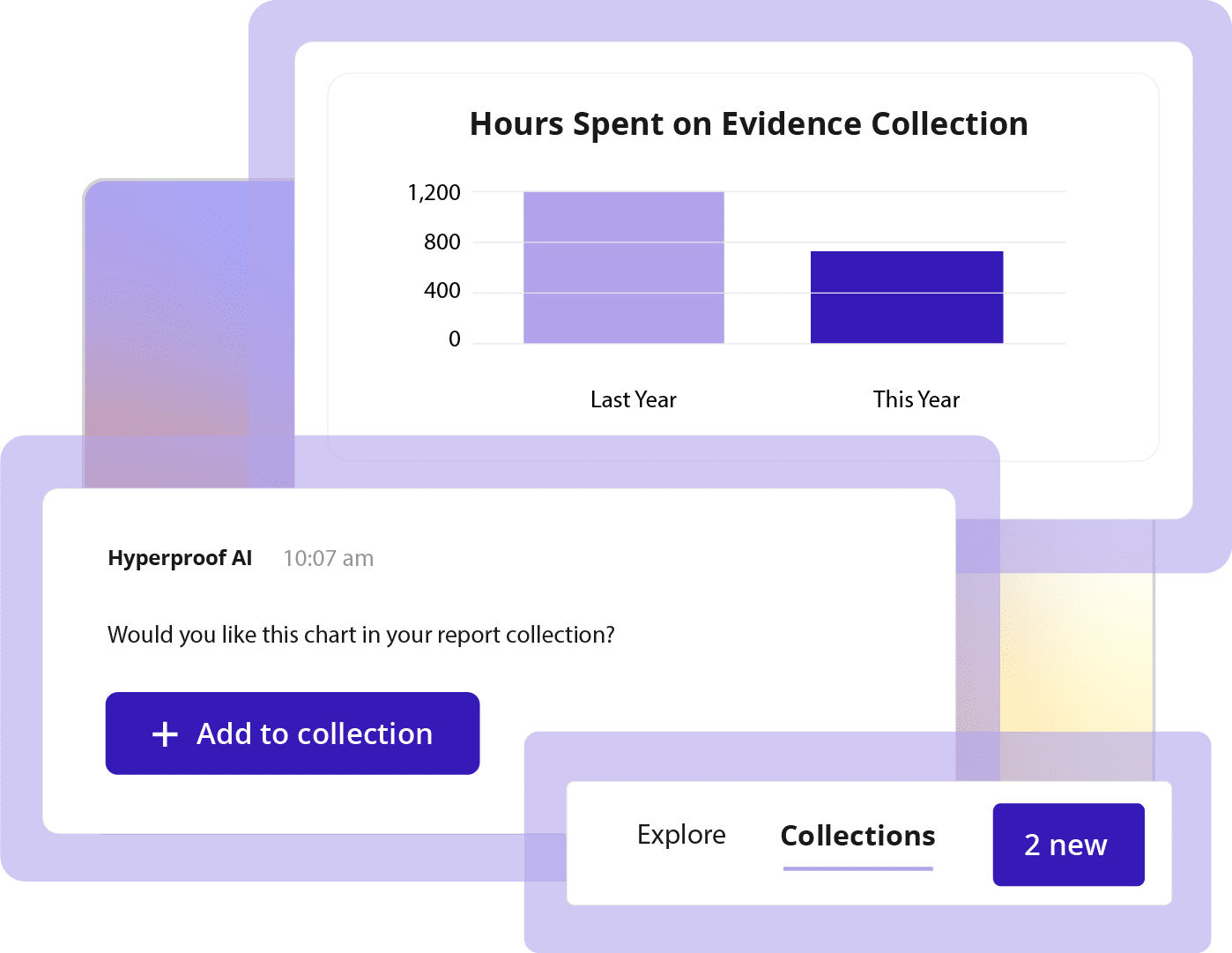
Hyperproof identifies overlapping requirements between frameworks so you can reuse controls and evidence. You collect proof once and apply it across multiple audits, saving weeks of prep time. Hyperproof AI’s Act agent can automate this work further by streamlining workflows and automatically mapping risks, controls, and tasks on your behalf.
Automate evidence collection

Use Hypersyncs to automatically gather proof from cloud storage systems (Google Drive, SharePoint, Dropbox) and cloud platforms (AWS, Azure). Hyperproof pulls in fresh data daily and attaches metadata like timestamps and file sources so auditors can verify authenticity.
Collaborate seamlessly
Hyperproof integrates with Jira, Slack, and Microsoft Teams, enabling compliance teams and control owners to work together without leaving their preferred tools. Automated reminders keep everyone on schedule and prevent missed reviews or tests.
Simplify audits
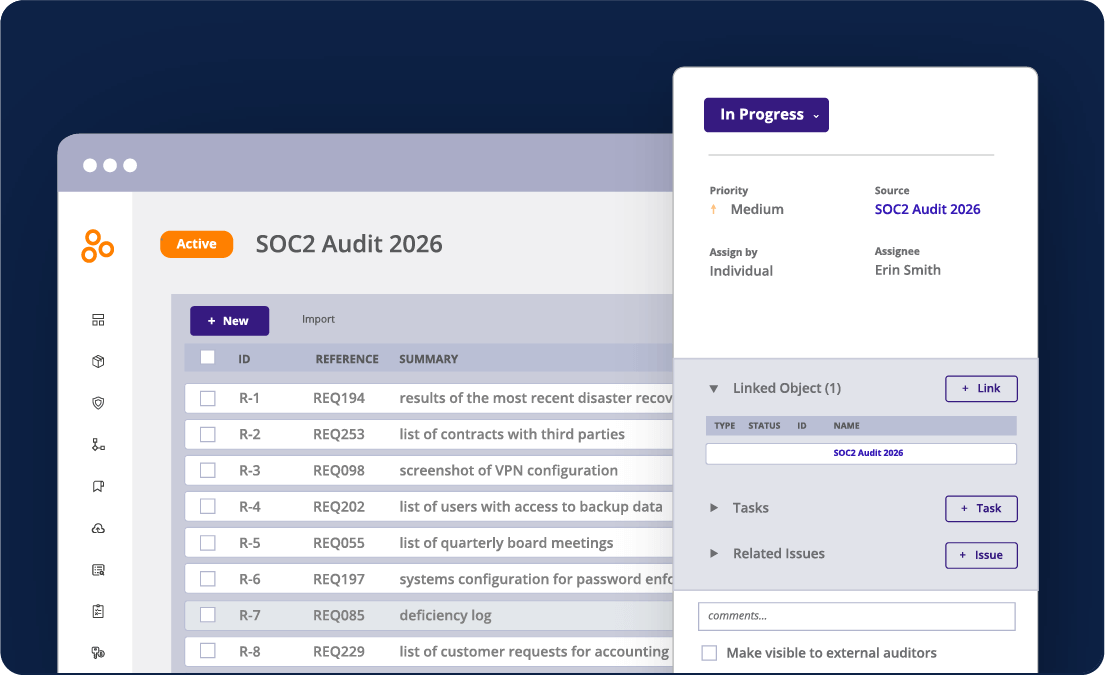
Invite auditors directly into Hyperproof’s Comply Module and share only the documents you choose. This secure, streamlined process eliminates the back-and-forth of sending files manually.
Gain real-time visibility
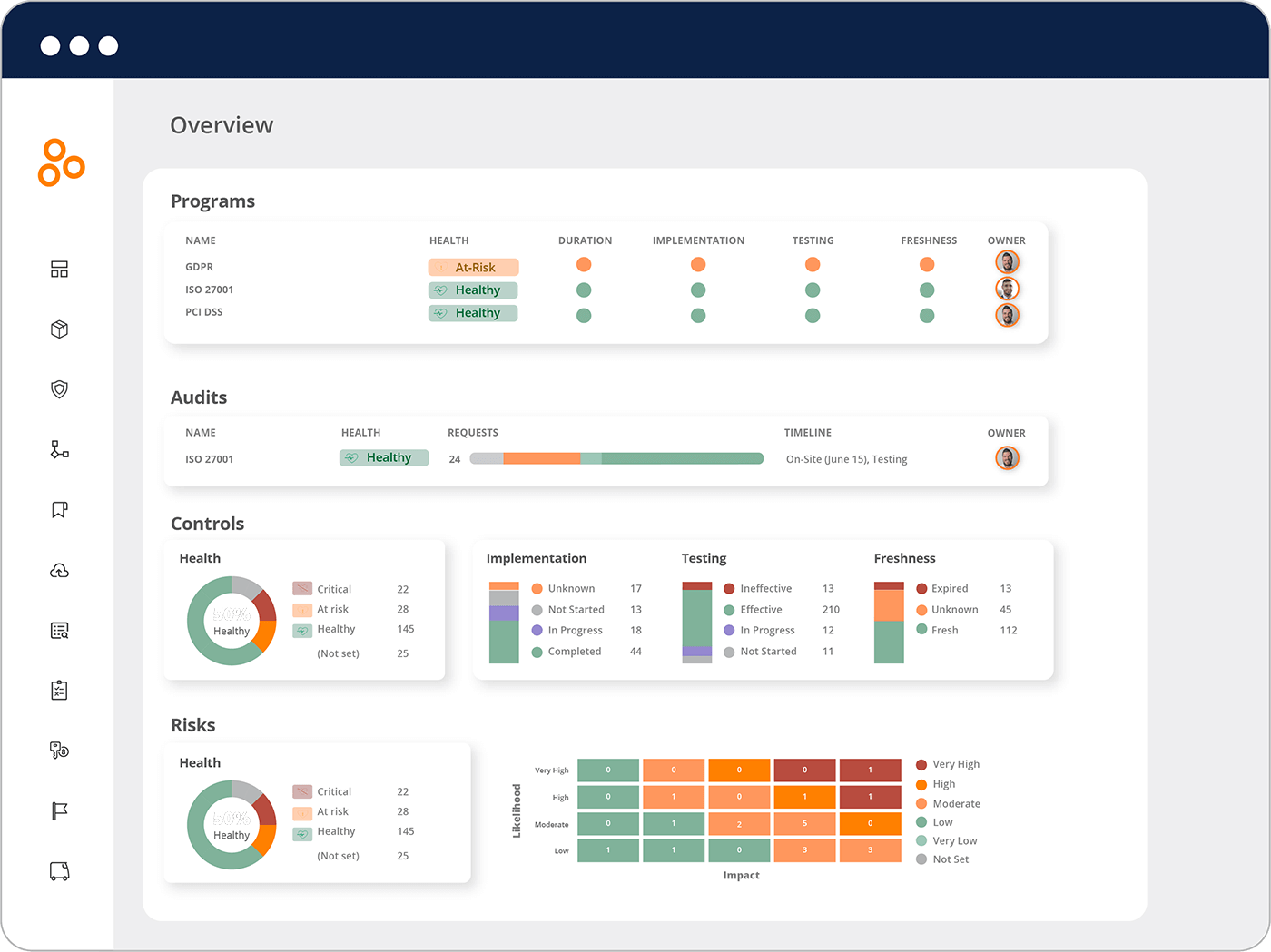
Dashboards and reports show exactly where your compliance stands. You can track progress, identify gaps, and communicate your compliance posture to executives, auditors, and customers with confidence. Hyperproof AI’s Advise agent can automate this work further by automatically generating reports based on your input.
Transform GRC from a cost center to a growth engine
With AI-powered compliance automation, GRC transforms from a cost center to a strategic growth driver. By automating framework adoption and reusing evidence across standards, Hyperproof helps organizations jumpstart new frameworks and enter markets faster. AI-powered automation reduces manual effort, accelerates time-to-market, and empowers teams to focus on innovation instead of administration, turning GRC into a true competitive advantage.
If you’re ready to see how compliance automation software can save your team time and reduce risk, we’d love to show you how Hyperproof works.
See Hyperproof in action
TL;DR: Getting started with compliance automation
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












