Compliance Audits: What to Know to Pass Audits

It’s an exciting time for your growing company. Your product is launched, a your sales team is educated, you’re starting to build a predictable pipeline of prospects, and your early customers are enthusiastic about the product. With all this momentum built up, you’re hopeful about being able to land a really prestigious account — a Fortune 500 company — that would help your sales team open doors that weren’t open before. You’ve had some promising conversations with a couple of decision-makers. But suddenly, you’ve hit unexpected turbulence: have you passed a compliance audit? For many buyers, an audit for compliance is the proof point that turns “we take security seriously” into something procurement can actually approve.
If not, don’t worry – a repeatable compliance audit process can help you gather the right evidence, align stakeholders, and move fast without scrambling. If your next step is a compliance IT audit, start with a checklist you can adapt to your scope and framework.
This prospective organization’s security team asks to see your organization’s latest SOC 2® Type 2 report. They need to know when the latest opinion letter was issued and which CPA firm had conducted the audit. They’re also asking you a set of security questions you haven’t seen before.
At this point, you’re trying not to panic. You’ve heard a little bit about SOC 2® before and know that this is a compliance hurdle your company will need to jump over at some point in the next few years. But this moment has arrived much sooner than you’d expected.
Now, you must quickly get up to speed on SOC 2®, learn about this compliance audit and determine what’s required to pass the audit – so you can give this prospective organization the assurance they need to trust you as their vendor. In this article, we’ll talk about compliance audits, some common compliance (and IT security) audits your business may need to go through as your company grows, and some tips on how to prepare for and pass these audits (such as SOC 2®). We’ll focus on compliance audits for businesses that handle customer or regulated data, and walk through a practical approach to preparing for audits so you can turn them into a sales enabler rather than a blocker.
Here’s what we’ll cover:
- What is a compliance audit?
- What’s the purpose of a compliance audit?
- What’s typically involved in a compliance audit?
- How do you prepare for a compliance audit (and do so efficiently)?
- Tips for passing compliance audits
- Hyperproof’s capabilities to help you prepare for compliance audits
What is a compliance audit?

A compliance audit is a comprehensive review and evaluation of a business or organization’s compliance with a voluntary compliance framework (e.g., SOC 2, ISO 27001) or a set of regulatory requirements (e.g., GDPR or HIPAA). Audit reports are like report cards that tell someone (e.g., your customers) about the health of your compliance program, based on whether you’ve implemented effective controls needed to meet specific requirements and/or guidelines laid out in a particular compliance framework. Put simply, compliance auditing is the process of independently evaluating whether your business is following the laws, regulations, and voluntary frameworks it has committed to (for example, SOC 2®, ISO 27001, HIPAA, or GDPR).
These days, most businesses care about their data, and they know that they’re taking on a level of risk when they entrust third parties with their business data (and their customers’ data). To help businesses understand the best ways to keep data safe, standard-setting associations (e.g., the American Institute of Certified Public Accountants and the Payment Card Industry Security Standards Council) have developed different standards and requirements.
Organizations can abide by those to maintain a reasonable level of security, information integrity, availability, and confidentiality. These standard-setting associations have issued detailed guidelines showing auditors exactly what to evaluate and include in their written reports.
For instance, the American Institute of Certified Public Accountants (AICPA) developed the SOC 2® audit. This tests a service organization’s internal controls to provide a report that can serve as a form of security assurance for the client, customers, employees, any third-party stakeholders, and the service organization itself. The Payment Card Industry Security Standards Council, founded by Visa, Mastercard, American Express, Discover, and JCB International, developed its own security standards to ensure a safe digital payment ecosystem for all participants.
The scope of a compliance audit depends on which framework or regulation the auditor is evaluating against and, for some frameworks, it also depends on what type of information your organization stores and how the information is utilized.
But let’s ignore the specifics of each framework for a moment. Generally speaking, an auditor’s job is to evaluate the strength and thoroughness of your company’s policies, user access controls, and risk management procedures – either at a point in time or, more likely, over a specific period (6 or 12 months).
What is the purpose of a compliance audit?

The top reason to go through compliance audits for businesses is to give your customers the assurance that you are protecting their information to the fullest extent possible. In getting a reputable third party to say “yes, XYZ company is compliant,” you’ll earn trust more quickly and acquire customers more easily.
Here are the primary reasons why organizations go through IT compliance audits:
Customers need verification to trust you
At this time, when it comes to matters of data security and data privacy, many organizations will not simply take your words at face value. Instead, IT and procurement departments within organizations will ask to see proof of audit findings from a certified public accounting firm before they’ll consider doing business with your firm.
Some of the most commonly required or requested data security frameworks require organizations to complete an audit before they can call themselves compliant (e.g., SOC 2®, ISO 27001).
Meet industry-specific standards to legally conduct business
Your organization may be subject to industry-specific standards. For instance, your organization would be required to be compliant with the Health Insurance Portability and Accountability Act if you process individuals’ medical records and other protected health information). HIPAA requires health care providers, health plans, health care clearinghouses, and their business associates — to protect individuals’ medical records and personal health information (PHI) and alert individuals, the media, and the government under certain circumstances if a breach occurs.
Improve your security to prevent costly data breaches
Preparing for a compliance audit is the best way to find gaps or holes in your data security program. The process of implementing a security compliance framework such as ISO 27001 or the NIST Cybersecurity Framework gives you the chance to see where your organization is falling short and where you can shore up your processes and policies. Then you can implement new measures or update existing security policies and procedures better to protect your organization and your customers’ data.
Competitive differentiation
You want your organization’s approach to security and compliance to be your competitive edge (e.g., B2B buyers, particularly those working for enterprises, may choose you over competitors if you convey a sense of security that others cannot).
What are the requirements for compliance audit?
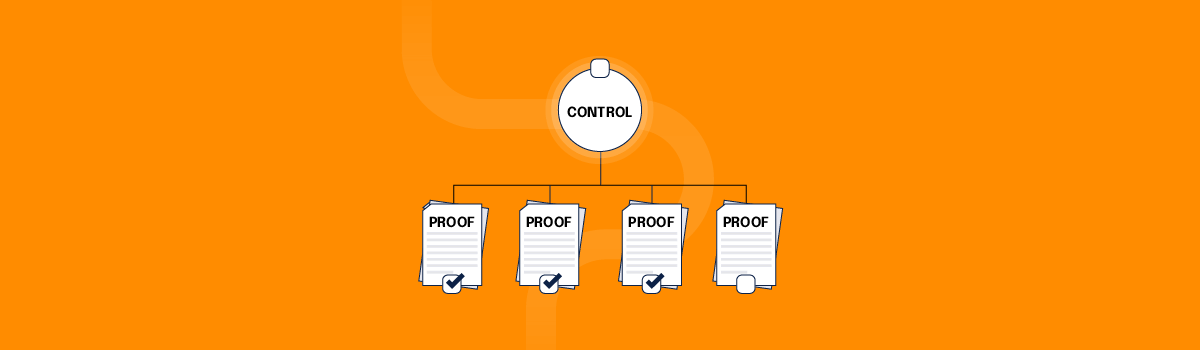
Compliance audits typically involve providing documentation of your internal controls to an outside auditor. Internal control is any process, procedure, policy, or technology component your organization has chosen in place to mitigate the risk of experiencing an unwanted outcome or to ensure a specific outcome can be achieved.
During an audit, the auditor evaluates the evidence you provide to assess whether your internal controls are designed effectively, operating as intended, and adequately protecting your organization from a specific set of risk outcomes (e.g., a data breach, a lawsuit resulting from a user privacy violation, etc.).
Documents or evidence that auditors may request from your organization include:
- Internal policies, such as Acceptable Encryption and Key Management Policy, Acceptable Use Policy, Data Backup Policy, Data Breach Response Policy, Personnel Security Policy, Disaster Recovery Plan Policy
- Documentation of specific procedures such as your procedure around removing employees’ access to key systems immediately upon their departure from the company
- Meeting notes, such as notes taken from monthly security review meetings
- Emails such as a thread that shows that a specific approval process was followed
- Screenshots showing statuses generated by systems you’ve put in place as part of an information security program (e.g., vulnerability scan reports from your vulnerability scanner)
As your business grows, you’ll naturally implement new business applications and processes and hire for new roles. With that, you’ll need to create and document new security measures to counter the risks of change and growth. When you think about all the departments and types of work within each team, it’s easy to see how time-consuming formal audits can be, both to prepare for and complete.
Related: Internal Controls and Data Security: How to Develop Controls That Meet Your Needs
What do you need to pass an audit?

When preparing for audits, taking the following steps can help you have a smooth journey and successful outcome:
1. Develop a project plan
Implementing a new data security framework is like a project, and it must be managed closely. Develop a timeline, make sure the right people are involved, and ensure everyone understands the importance of successfully completing this project. Strong compliance audit management means treating the audit like a cross-functional project: clear owners, tracked deliverables, and visible progress against deadlines.
2. Perform a risk assessment
Risk assessments are foundational to an effective compliance program. After all, your compliance and security measures should be tailored to minimize the material risks to your organization. To correctly identify risks to your information systems, you’ll need to inventory your data assets to gain a clear view of where all data resides and who has access to what.
3. Design and implement controls
Once you know your risks, you can develop internal controls to mitigate them. Controls are processes or activities designed to assure that your business is meeting its objectives in security, data privacy, and the effectiveness of your operations.
4. Document your work
One of the main ways you will show compliance during an audit is through documentation. You should keep detailed records on your processes, policies, training, implementation, internal and external audits, and any other activities related to your compliance efforts because auditors will need them to verify the efficacy of your internal controls. Compliance audit documentation should be organized so an auditor can quickly answer three questions: what the control is, who owns it, and what evidence proves it operated during the audit period.
5. Conduct an audit-readiness assessment
To mitigate the risk of failing an audit, your organization should work with your auditor to have them conduct a compliance audit readiness assessment before the formal audit. Although this is a voluntary exercise, it can be a highly beneficial exercise, especially if you’re going through an audit for the first time.
These steps apply across most compliance audits for businesses, whether you’re facing your first SOC 2® assessment or recurring ISO 27001 surveillance audits.
What is a compliance readiness assessment (and how it helps in preparing for audits)?

An audit readiness assessment can be thought of as a “preparatory test” before the real test or as your dress rehearsal before a performance in front of a live paying audience. It’s an opportunity to discover weaknesses in your internal control environment and fix those issues before the formal audit happens.
During an audit readiness assessment, which should ideally happen a couple of months before the formal audit, the auditor will seek to understand the business processes that are in the scope of the audit, how the various systems are set up to support these business processes, and the controls you’ve put in place. Their job is to evaluate whether those controls sufficiently meet the audit standard and surface gaps you still need to address to get a clear opinion letter (which is what you want).
To conduct an audit readiness assessment, the auditor will ask to see documentation of your controls (e.g., policies, documentation of various procedures, meeting notes, screenshots from different systems). They’ll also talk to key personnel in your compliance program — to understand your key policies and compliance processes. They may ask clarification questions. Once these steps are complete, your auditor will write a report outlining the gaps in your program or areas where your organization’s compliance efforts need more work.
Conduct a formal audit
At this point, you should have completed an audit readiness assessment, seen what wasn’t working, and taken the time to shore up any aspects of your compliance program that needed work. If you’ve done all of this work beforehand and know what to expect from the auditors, this process should be relatively smooth and hopefully won’t uncover any hidden gaps in your program.
A caveat about formal audits
It’s important to remember that a formal audit will not catch all of the potential vulnerabilities in your security or compliance programs. They are a point-in-time exercise and only give you a snapshot of how your compliance program works when the audit is conducted. To adequately mitigate security risk, it’s crucial to test your controls and remediate identified weaknesses continuously.
Why preparing for compliance audits is challenging
While compliance audits are crucial for gaining your customers’ trust and protecting their data, they can be time-consuming, expensive, and frustrating to prepare for – especially if it’s your first time.
For one, you may not know that certain controls haven’t been documented until your auditor asks for them. Meanwhile, pulling and reviewing the right information to understand how close you are to being ready for the formal audit will likely be quite tedious if you using tools like spreadsheets, email, and file storage systems. When you have to cross-reference things manually, it’s tough to answer the critical questions you’ll need to answer to get a clear report:
- Do we have working controls for every requirement, or are we missing a few controls? Getting these answers will likely require many interactions with team members in engineering, IT, and business units and digging through different document repositories.
- Do we have up-to-date evidence for demonstrating the presence and efficacy of each control?
- Do we have backup controls for our high-risk assets?
- What documents or proof of compliance do I still need to collect?
- Which stakeholders haven’t yet completed the tasks they were supposed to complete?
- Which controls and pieces of proof do I need to review or update by the end of this week?
Fortunately, preparing for an audit doesn’t have to be a burden. By dedicating enough resources to the endeavor, planning upfront, and leveraging technology to automate manual processes, you can avoid much of the pain others had to endure.
Tips for passing compliance audits

Dedicated resources and people
Implementing a compliance framework and completing an audit will require time, money, and knowledge. Going through the process of identifying your risks, selecting the right compliance framework, meeting with auditors, and reviewing your controls will take time away from other valuable work (e.g., product development). You can also expect to spend anywhere between $10,000 to $100,000 on a single audit.
If you’re going through an audit for the first time (or even the second or third time), getting expert support is imperative. There are many professional service firms that specialize in various cybersecurity and data privacy frameworks; they can help you better understand the requirements of the law and work with you to develop tailored controls for your environment.
Get leadership support
Getting leadership support up-front is crucial for a few reasons:
- First, a compliance officer needs to have some authority to change, develop, and implement operational processes and enforce disciplinary actions for noncompliance. They can’t exercise that authority without the support of management and the C-suite.
- Second, security and compliance are things that need to be woven into your company culture. If it’s not a priority for executives, it won’t be a priority for anyone else. When executives are bought in, they make decisions that center on compliance, show their employees that it’s a priority, and create an environment where everyone understands the importance of data security and privacy.
Use compliance operations software
You can use software like Hyperproof to cut down the amount of administrative work from your compliance processes (e.g., tracking the status of each control, mapping controls to requirements, gathering evidence, and sharing the evidence with your auditor) — so your team can focus their energy on the tasks that truly make your organization stronger. If you want a deeper breakdown of how audits and controls fit together, see our guide on audit compliance procedures. Hyperproof allows you to easily see the requirements for different compliance frameworks (e.g., SOC 2®, ISO 27001, GDPR), create or update internal controls, store, tag, and organize compliance evidence, and automate many repetitive administrative tasks associated with the audit process.
Hyperproof’s compliance audit preparedness tools in action

Let’s say you’re in the middle of preparing for an upcoming SOC 2® audit; you’ve created controls for some requirements. You have uploaded documentation to verify the effectiveness of certain controls but not all controls.
In Hyperproof, you can pull up the SOC 2® program dashboard and in a matter of seconds, understand the status of the entire program, the work that needs attention, and when it has to be completed.
Understand how well-defined a program is at a high-level
You can see the current state of program definition, drill into specific categories (like “In Progress” vs. “Not Started”) and start working on specific requirements or controls.
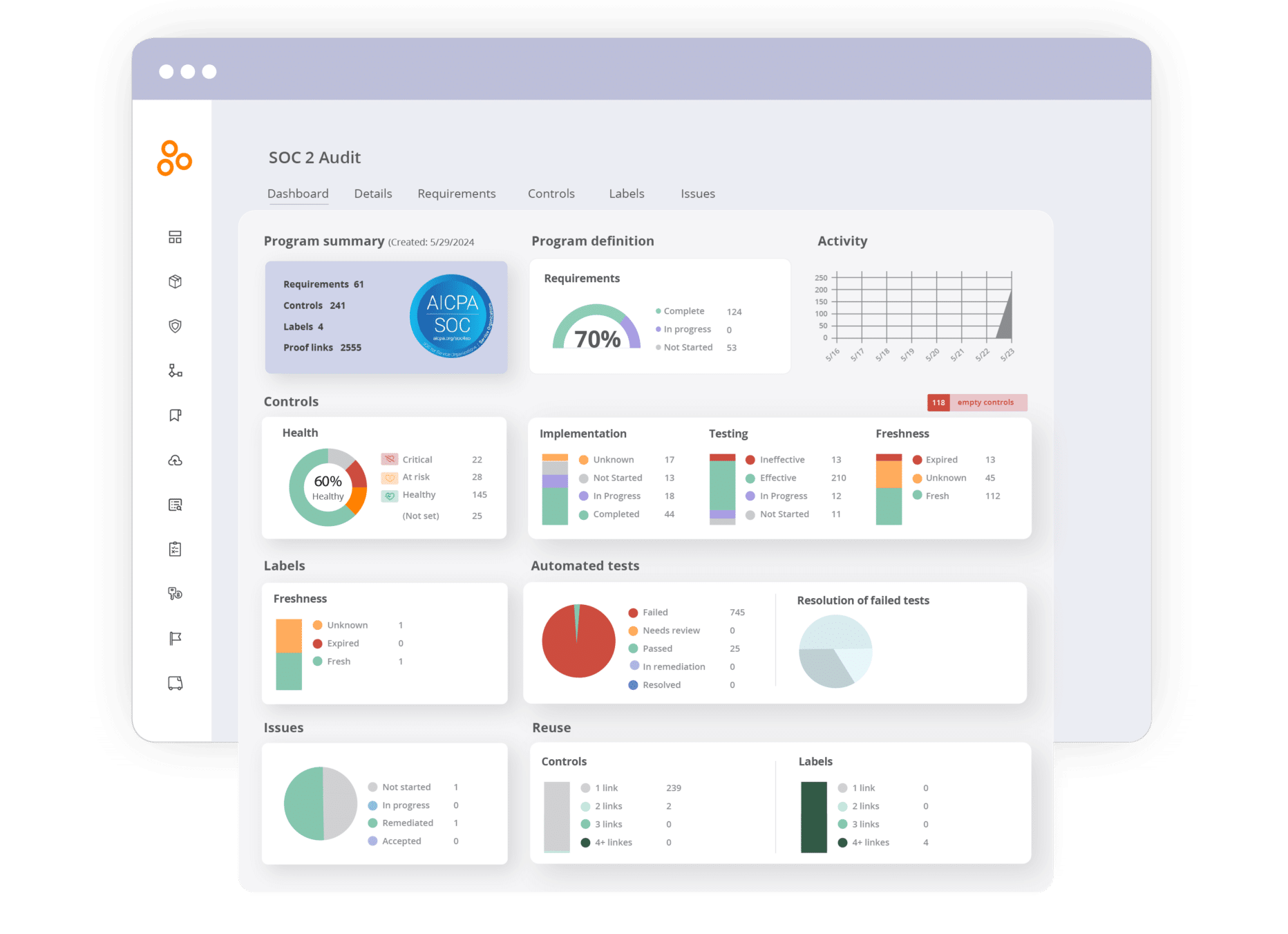
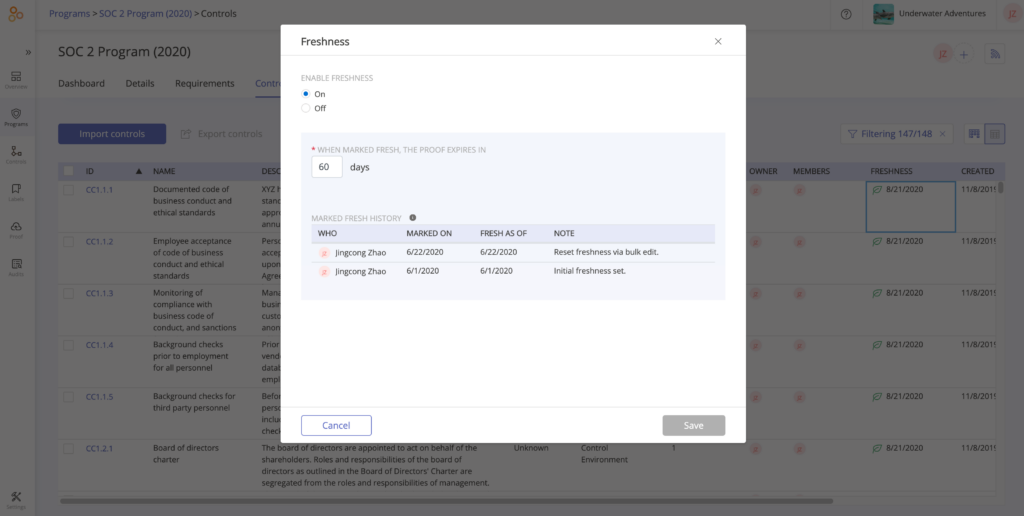
Set cadences to re-evaluate controls and keep them current
You can take a look at the “Freshness” chart, drill in to see the status of each control, and ensure you set a review policy on each control to re-evaluate its efficacy (e.g. in 30, 90, or 120 days).
Understand the efficiency of your compliance efforts
By reusing evidence across controls and reusing “common” controls across multiple requirements, you can bring efficiency to the management of your compliance efforts. Hyperproof helps you gauge how you’re doing in terms of efficiency.
Common controls are controls that can satisfy multiple compliance requirements. For instance, many cybersecurity frameworks have requirements around change management. They ask organizations to govern change sustainably and continuously, involving active participation from technology and business stakeholders to ensure that only authorized changes occur. You could make one control to satisfy multiple requirements around change management.
Head over to the “Reuse” section of a Program Dashboard to see how efficiently your team manages your compliance efforts. Have you created any common controls that satisfy two or more requirements?
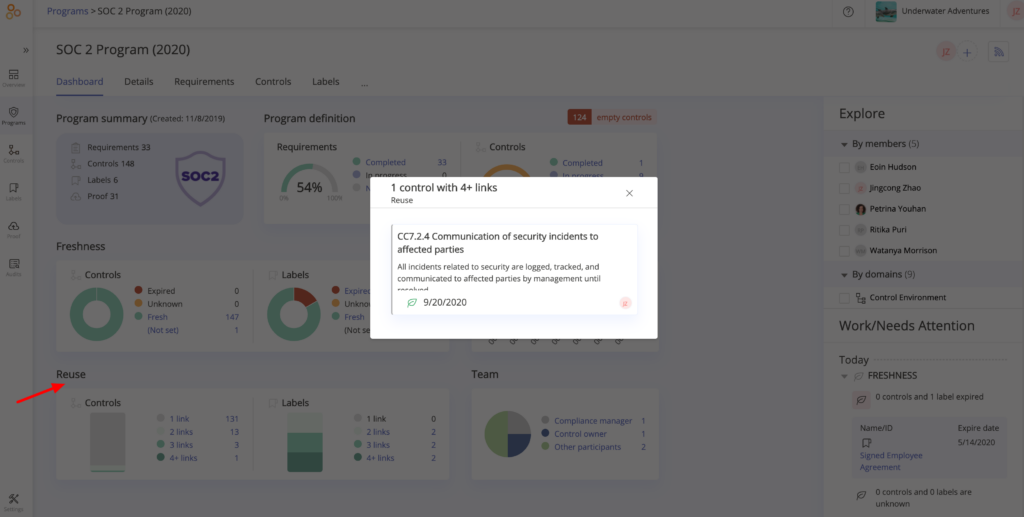
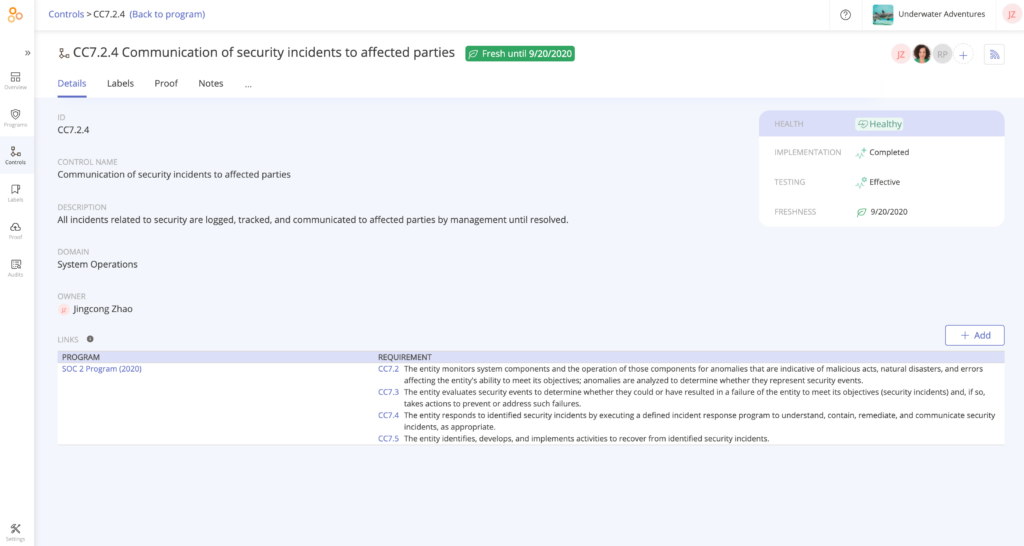
In this example, we clicked through the Reuse chart and found one control –CC7.2.4– that satisfies four different requirements within the SOC 2® framework. That’s a good thing because it means that we can collect evidence once for this control, and the evidence will satisfy four different requirements.
Complete all audit requests in one place
When your team has checked that all necessary controls are in place, tested, and documented, it’s quite easy to provide that evidence to your auditor for the formal assessment. You can invite your auditor to access the Audit space within their Hyperproof account by sending an email invitation. The auditor will upload all of their client evidence requests in the Audit space. Once this is done, these requests are visible in your Hyperproof account.
From there, you can assign each request to a team member and set a due date for completing the request.
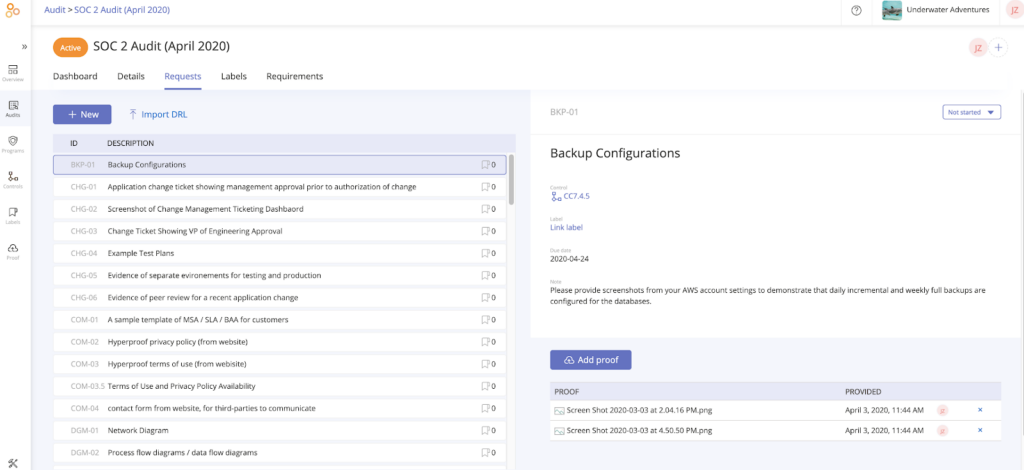
You can see progress on evidence requests in real time as team members complete their assignments.
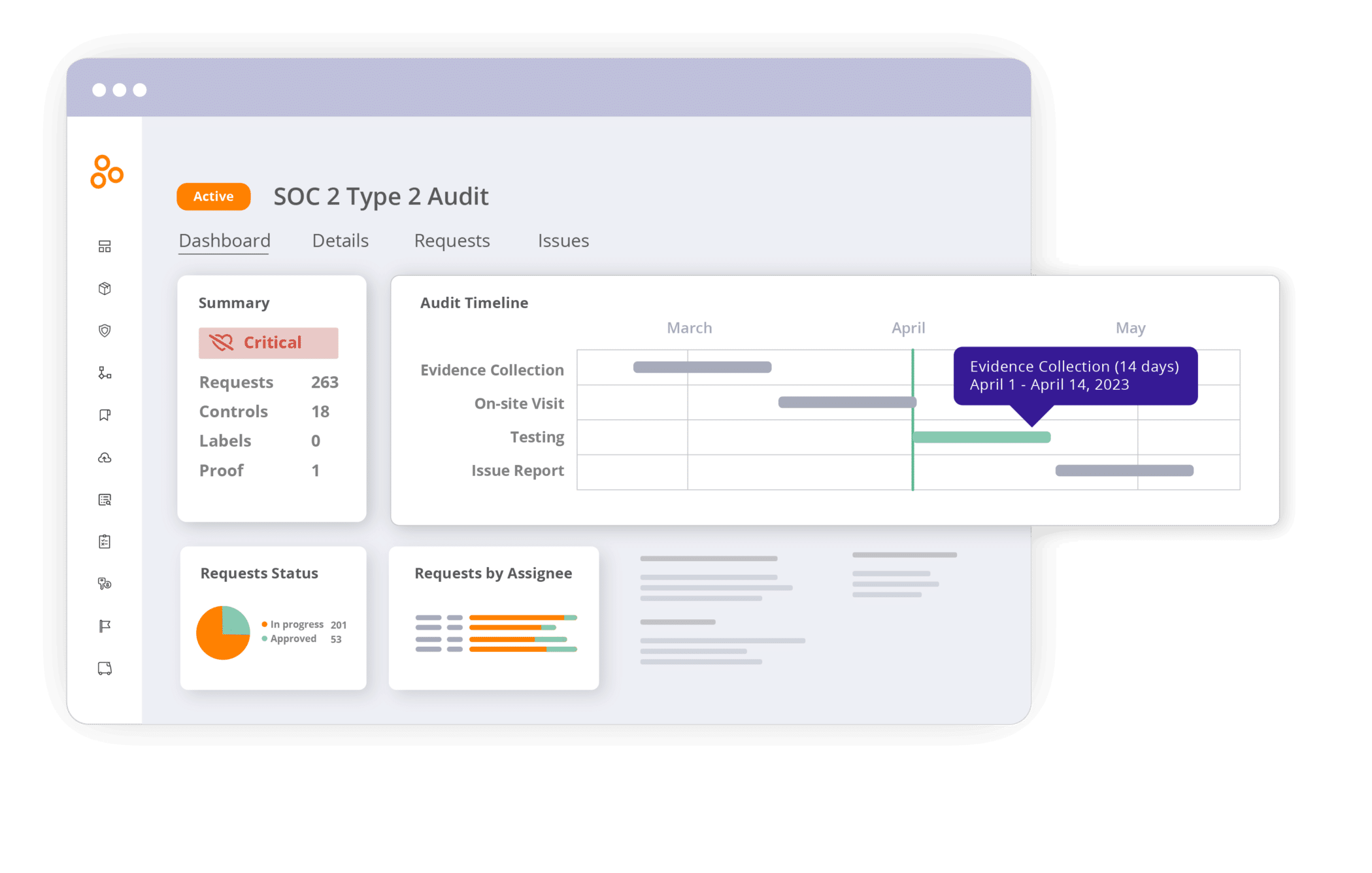
Suppose someone hasn’t provided evidence for an audit, due to illness or other reasons. In that case, Hyperproof allows other people within the compliance team to step in and provide the requested evidence to the auditor.
Does this article apply to an in-store compliance audit for retail locations?
Yes. While this guide focuses on technology and security frameworks such as SOC 2® and ISO 27001, the same principles apply to an in store compliance audit. Retailers still need internal controls (for example, POS access controls, cash-handling procedures, inventory checks, signage/labeling rules), documentation of those controls, and evidence that they’re being followed. The steps we outline for performing risk assessments, documenting controls, and preparing for audits can be adapted to physical store environments as well as cloud-based systems.
Discover how Hyperproof can support successful compliance audits
Check out our customer case studies to learn more about how businesses are using Hyperproof to advance their compliance programs.
If you’re an existing customer, you already have access to these dashboards and will see these features the next time you log into your Hyperproof instance.
If you are not using Hyperproof yet, you can sign up for a personalized demo to learn more about how the app can be used to improve the consistency, quality, and efficiency of your compliance program and make preparing for audits dramatically easier.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?