
The Ultimate Guide to
NIST SP 800-53
What is NIST SP 800-53?
Developed by the Joint Task Force Interagency Working Group, which includes representatives from the civil, defense, and intelligence communities, including the National Institute of Standards and Technology (NIST), Department of Defense, Office of the Director of National Intelligence, and the Committee on National Security Systems, NIST Special Publication (SP) 800-53, Security and Privacy Controls for Information Systems and Organizations is a collection of specific safeguarding measures that can be used to protect an organization’s operations and data and the privacy of individuals. In fact, NIST SP 800-53 is considered the gold standard for information security and is cross-referenced by many other industry-accepted security standards.
Any organization, regardless of its size, sector, or technology environment, can use NIST SP 800-53 security and privacy controls to maintain the security of its information systems and mitigate privacy risks. The controls can be customized and implemented as part of a firm-wide process to manage risks such as hostile attacks, human errors, natural disasters, structural failures, foreign intelligence entities, and privacy risks.
Can NIST SP 800-53 improve my security system?
Yes. Although NIST SP 800-53 was originally designed for use by U.S. federal government agencies, it can help organizations in all industries improve the security of their information systems. NIST SP 800-53 contains a set of security and privacy safeguarding measures for all types of computing platforms, including general purpose computing systems, cyber-physical systems, cloud systems, mobile systems, industrial control systems, and Internet of Things (IoT) devices.
The consolidated control catalog addresses security and privacy from a functionality perspective and an assurance perspective. Addressing functionality and assurance helps an organization gain confidence that its information technology products and the systems that rely on those products are sufficiently trustworthy.
In many cases, implementing NIST SP 800-53 rev 5 will help organizations ensure NIST 800-53 compliance with other regulations that deal with cyber risk and information security, such as HIPAA, FISMA, or SOX, because many other frameworks use NIST as the reference framework.
NIST SP 800-53 control families
According to NIST SP 800-53 rev 5, controls can be viewed as “descriptions of the safeguards and protection capabilities appropriate for achieving the particular security and privacy objectives of the organization and reflecting the protection needs of organizational stakeholders. Controls are selected and implemented by the organization in order to satisfy the system requirements.”
NIST SP 800-53 rev 5 lists 20 families of controls that provide operational and technical safeguards to ensure the privacy, integrity, and security of information systems.
Each family holds controls that are related to the specific topic of the family. Security and privacy controls may involve aspects of policy, oversight, supervision, manual processes, and automated mechanisms that are implemented by systems. Below is a table that lists the security and privacy control families and their associated family identifiers.
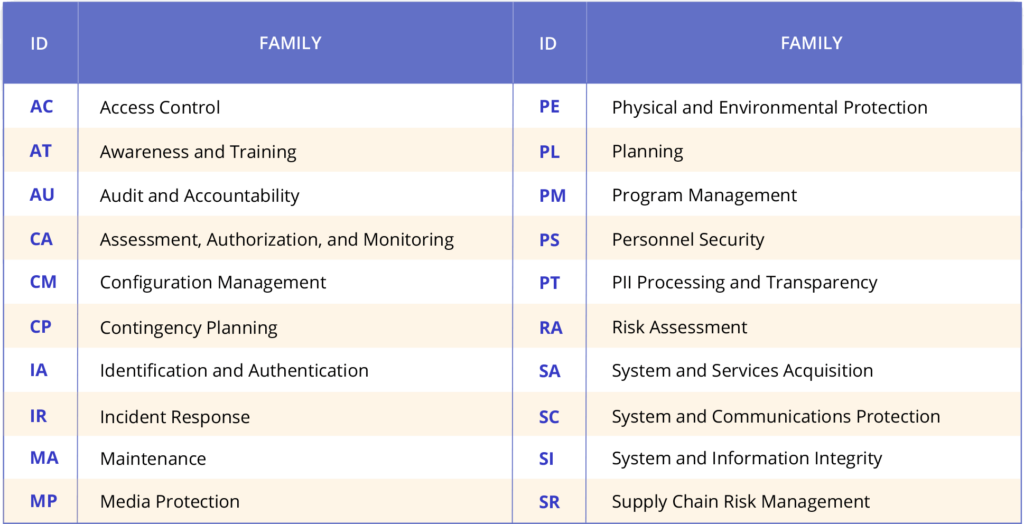
Families of controls contain base controls and control enhancements, which are directly related to their base controls. Control enhancements either add functionality or specificity to a base control or increase the strength of a base control. Control enhancements should be used in systems and environments of operation that require greater protection than the protection provided by the base control.
SP 800-53 rev 5 security and privacy controls follow a standardized structure: a base control section, a discussion section, a related controls section, a control enhancements section, and a references section. Figure 1 illustrates the structure of a typical control.
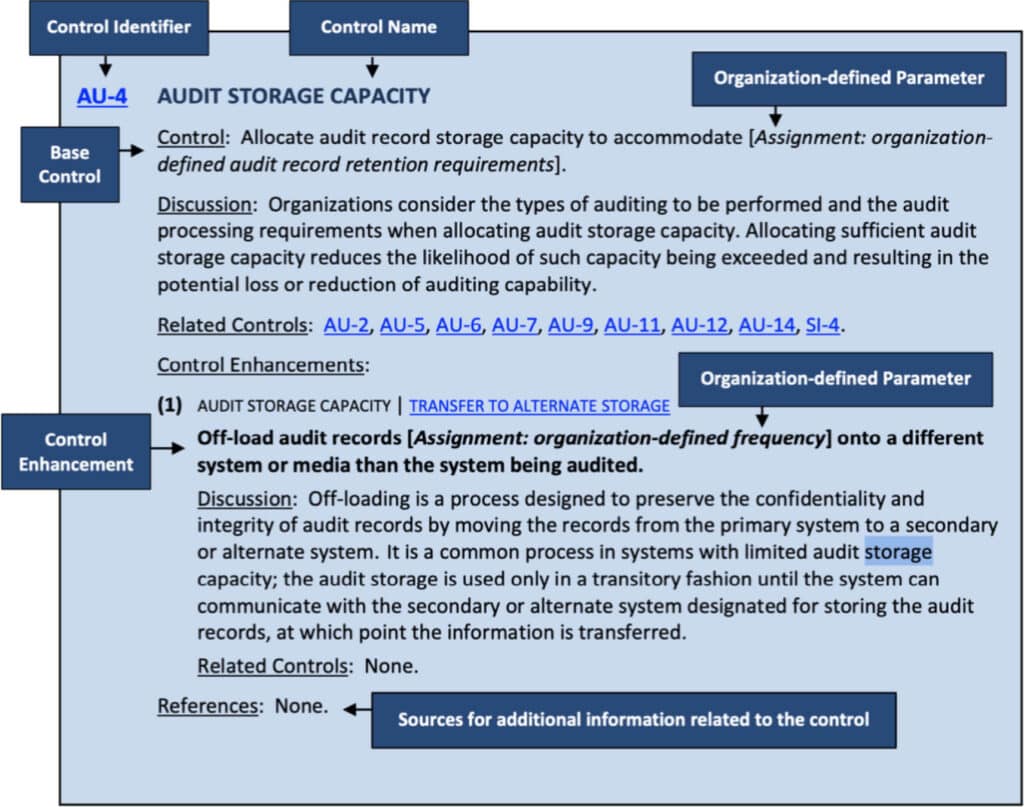
Many organizations have chosen to use NIST SP 800-53 controls as the baseline for their security and privacy controls because the controls in the catalog, with a few exceptions, are policy-, technology-, and sector-neutral; they focus on the fundamental measures necessary to protect information and the privacy of individuals across the information lifecycle.
However, It is up to each organization to analyze each security and privacy control for its applicability to their specific technologies, environments of operation, mission, and business functions as well as tailor the controls that have variable parameters. To access the entire SP 800-53 controls catalog, you can visit the NIST SP 800-53 rev 5 publication or sign up for a demo of Hyperproof.
To help organizations figure out which specific controls from the SP 800-53 rev 5 catalog they should implement to suit their unique situation, NIST has published a companion publication, titled SP 800-53B. SP 800-53B. This publication contains control baselines that serve as starting points for protection and can be tailored appropriately based on organizational missions, business functions, threat information, and operational environment.
5 control families to pay attention to
Since SP 800-53 rev 5 has 20 control families, it’s important that you prioritize your efforts based on the areas that will have the highest impact. In today’s environment, where many people are now working from home, potentially using unauthorized networks and applications and their personal devices, organizations may want to consider focusing on five control families to ensure adequate protection of your systems: Access Control, Configuration Management, Assessment, Authorization, and Monitoring (CA), Audit and Accountability (AU), and Awareness and Training (AT).
1. Access control family
The Access Control (AC) family includes a range of security and privacy controls aimed at regulating who or what can view or use resources in a computing environment. This family covers specific controls such as Policy and Procedures (AC-1), Account Management (AC-2), Access Enforcement (AC-3), and Information Flow Enforcement (AC-4). It incorporates mechanisms like Mandatory Access Control (MAC), Discretionary Access Control (DAC), Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC), as well as principles such as Least Privilege to ensure that access rights are appropriately assigned and managed based on organizational policies and security requirements.
2. Awareness and training family
Organizations should establish a comprehensive Awareness and Training (AT) program to ensure that all system users, including those with significant security and privacy responsibilities, receive appropriate training. This includes providing foundational and advanced levels of security and privacy literacy training to all users, role-based training tailored to specific duties for privileged users and executives, and measures to test users’ knowledge level.
3. Audit and accountability family
The Audit and Accountability (AU) family encompasses controls designed to create, protect, and retain audit records to enable monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity. This includes establishing policies and procedures to ensure accountability and traceability of user actions. To balance monitoring and auditing requirements with other system needs, organizations must identify and log a specific subset of event types at any given time, ensuring that audit processes are effective without unduly impacting system performance.
4. Control assessment (authorization and monitoring) family
The Control Assessment (Authorization and Monitoring) family focuses on ensuring security and privacy assurance through comprehensive policies and procedures. This family includes controls for assessing the effectiveness of implemented security and privacy measures, authorizing the operation of systems based on acceptable risk levels, and continuously monitoring controls to detect changes or deficiencies that could impact system security. These activities help organizations ensure that security and privacy protections remain effective over time and align with organizational risk management strategies.
5. Configuration management family
The Configuration Management (CM) family encompasses controls designed to establish and maintain the integrity of systems through structured configuration management processes. This includes developing and documenting baseline configurations that serve as a basis for future builds, releases, or changes to systems, incorporating security and privacy control implementations, operational procedures, information about system components, network topology, and the logical placement of components within the system architecture. Additionally, it involves establishing policies and procedures for managing changes, monitoring configurations, and ensuring that unauthorized changes are prevented or detected, thereby maintaining system security and operational stability.
Those control families cover the basics and provide a minimal level of protection. From there, you can work on the other areas.
What are control baselines in NIST SP 800-53B?
NIST SP 800-53B, Control Baselines for Information Systems and Organizations, provides security and privacy control baselines for the Federal Government and private sector organizations. SP 800-53B is a companion publication to SP 800-53, revision 5, Security and Privacy Controls for Information Systems and Organizations.
SP 800-53B includes three security control baselines (one for each system impact level: low-impact, moderate-impact, and high-impact), as well as a privacy control baseline that is applied to systems irrespective of impact level. The privacy control baseline supports federal agencies in addressing privacy requirements and managing privacy risks that arise from processing PII based on privacy program responsibilities under OMB Circular A-130.
Baselines are there to help organizations select a set of controls for their systems that is commensurate with their security and privacy risk. According to NIST guidance, the security baseline selected for systems should be “commensurate with the potential adverse impact on an organization’s operations, organizational assets, individuals, other organizations, or the Nation if there is a loss of confidentiality, availability, or integrity.”
Here’s what the three levels mean:
- A low-impact system is defined as a system in which all three of the security objectives (i.e., confidentiality, integrity, and availability) are assigned a FIPS Publication 199 potential impact value of low.
- A moderate-impact system is a system in which at least one of the security objectives is assigned a FIPS Publication 199 potential impact value of moderate and no security objective is assigned a potential impact value of high.
- A high-impact system is a system in which at least one security objective is assigned a FIPS Publication 199 potential impact value of high.
Once an organization has selected an appropriate security baseline, they would tailor the controls to align them more closely with the specific security and privacy requirements identified by the organization. Control baselines are tailored based on a variety of factors, including threat information, mission or business requirements, types of systems, sector-specific requirements, specific technologies, operating environments, organizational assumptions and constraints, individuals’ privacy interests, laws, executives, orders, policies, regulations, or industry best practices.
Here are some ways in which controls can be tailored:
- Identify and designate common controls
- Apply scoping considerations
- Select compensating controls
- Assign values to organization-defined control parameters via assignment and selection operations
- Supplement baselines with additional controls and control enhancements
What’s the difference between NIST CSF and NIST 800-53?
NIST Cybersecurity Framework (CSF) is a subset of NIST SP 800-53 rev 5. Given that NIST CSF is more limited in scope, starting with NIST CSF is a reasonable choice for most companies that need a set of best practices to align with, particularly if they are not prime contractors for the US Federal Government.
Does NIST SP 800-53 overlap with other security frameworks?
Nearly all other frameworks and certification programs use NIST SP 800-53 or ISO 27001 as a baseline reference. In fact, NIST SP 800-53 has broad overlap with most security and privacy frameworks. For instance, the security controls from NIST SP 800-53 rev 5 map to the ISO 27001, a standard that specifies requirements for establishing, implementing, operating, monitoring, reviewing, maintaining, and improving a documented information security management system (ISMS) within the context of business risks.
However, similar topics may be addressed in two security control sets that may be of different context, perspective, or scope. Each organization still needs to assess whether a control taken from NIST SP 800-53 would fully satisfy requirements of ISO 27001 without modification.
What are the best practices for NIST SP 800-53 compliance?
To work your way towards full compliance, you’ll need to understand and work through some key steps:
Start by locating and securing all your sensitive data and then conduct security categorization as an organization-wide activity involving key stakeholders including chief information officers, senior agency information security officers, and other designated personnel to classify data based on potential adverse impacts to organizational operations, assets, and individuals. You want to conclude this phase of discovery with comprehensive risk assessments that identify threats and vulnerabilities in systems, determine the likelihood and magnitude of harm from unauthorized access, and assess the likelihood and impact of adverse effects on individuals from processing personally identifiable information.
Develop and document a comprehensive map of system data actions that process personally identifiable information throughout the full information lifecycle, including collection, generation, transformation, use, disclosure, retention, and disposal. The critical action step is creating data maps that include discrete data actions, elements of personally identifiable information being processed, system components involved in the data actions, and the owners or operators of system components.
Managing access starts with creating rules to govern who can access what information. These rules must be well-known and strictly enforced. Action steps for improved access control involve inactivating stale user accounts, proactively managing user and group memberships, and working from a “least privilege” model, which involves giving users the least amount of access they need to do their job.
Start by keeping records of how users access systems and data files. Use these records to create a baseline of regular activity to help identify anomalies such as weird access locations, rapid access upgrades, and sudden mass movements of data. Be sure to install a set of controls designed to monitor and detect insider threats, malware, and misconfigurations. Any vulnerabilities, anomalies, or attempted breaches should be discovered and remediated quickly.
It’s important to educate your employees on what they need to do (and what to avoid) to keep networks and company data secure. Management should provide employees with tactical knowledge on how to deal with the cyber threats organizations are most likely to face, such as email scams, malware, insecure passwords, unsafe internet browsing habits, removable media, etc.
NIST SP 800-53A recommends organizations deploy security assessment tools to gauge their real-time security posture. These software tools, created by security experts, measure the effectiveness of all organizational security measures and suggest system improvements based on empirical evidence.
But once your team has installed the appropriate controls and implemented NIST SP 800-53 security and privacy controls, you’ll need to make sure that your controls are implemented correctly and produce the desired outcome for meeting your organization’s security requirements.
NIST Special Publication 800-53A establishes standard assessment procedures to assess security controls’ effectiveness in information systems, specifically those controls listed in NIST SP 800-53. These recommended assessment procedures provide a starting point for developing more specific procedures and can be supplemented by your organization if it’s deemed necessary according to your risk assessment. Keep in mind that your organization may create additional assessment procedures for those security controls not contained in NIST Special Publication 800-53.
NIST 800-53 : Frequently Asked Questions
Hyperproof for NIST SP 800-53
Organizations can reap significant benefits when they align their security and compliance programs with a recognized framework like NIST SP 800-53, but the comprehensive nature of the guidelines poses adoption challenges.
Hyperproof’s compliance operations software makes it much easier for organizations to adopt NIST SP 800-53 as their cybersecurity framework, along with other industry-leading frameworks. Sign up for a personalized demo to see how we can help you utilize NIST SP 800-53 controls to create an effective and efficiently-managed security program:

Hyperproof partners with professional service firms with proven track records and deep expertise in helping organizations get NIST SP 800-53 ready. Our partners help customers design their compliance programs, build them out, and conduct readiness assessments to ensure there are no surprises when the audit occurs. If you need a referral, we’d love to talk.
Ready to see
Hyperproof in action?









