Streamlining Third-Party Risk Management: The Top Findings from the 2024 Benchmark Survey Report
As businesses grow and expand their operations, their third-party risk management program grows with them. This growth leads to increased complexity that makes it challenging for GRC and IT professionals to effectively identify and mitigate third-party risks.
Manual processes and the sheer volume of work can overwhelm even the most experienced risk managers. That’s why the market is shifting toward integrated solutions that can streamline these processes and provide comprehensive reporting on compliance and risk postures in addition to managing third-party risk.
Each year, Hyperproof surveys 1,000+ GRC professionals across multiple industries to learn what’s top of mind for them. This year, we found there was a greater need for a unified solution that provides a holistic view of risk and compliance data.
This blog is a high-level summary of our findings from chapter 4 of the report, covering third-party risk. To dive deeper — and check out other chapters — download the full report.
The state of supply chain risk management
In our 5th annual IT Risk and Compliance Benchmark Report, we found several changes to third-party risk management: supply chain disruptions are on the rise, and the state of supply chain risk management needs to shift to meet these challenges.
Supply chain risk management is continuing to evolve. In recent years, there have been changes at the federal level: in 2021, President Biden issued Executive Order 14028 to improve the nation’s cybersecurity, particularly around third-party risk and supply chain management.
EO 14028 provides a defined structure for collaboration between the government and the private sector. It outlines the parameters of critical software and establishes a process for sharing information to assist organizations with safeguarding against cyber threats.
Section 4 of the executive order outlines that “the Federal Government must take action to rapidly improve the security and integrity of the software supply chain, with a priority on addressing critical software.” It further states the obligations of the National Institute of Standards and Technology (NIST) to support the executive order by implementing various solicitations of feedback, issuing of specific guidelines, and more.
As regulatory bodies make changes to their approaches to cybersecurity, they need to make adjustments to current and new frameworks to meet changing standards for supply chain risk management.
What does this mean for third-party risk? There are more eyes than ever examining how software companies are operating, resulting in higher pressure to keep organizations safe from supply chain disruptions, especially those stemming from third parties.
Third-party incidents are on the rise
Our 2024 IT Risk and Compliance Benchmark Report unveiled that third-party incidents are on the rise — an unsurprising finding since cloud security has become more vital to business operations. This year, 62% of respondents reported experiencing a supply chain disruption related to cybersecurity, an increase of 13% year-over-year. Third-party and supply chain risks are becoming increasingly difficult to manage, particularly in the realm of cybersecurity risk management.
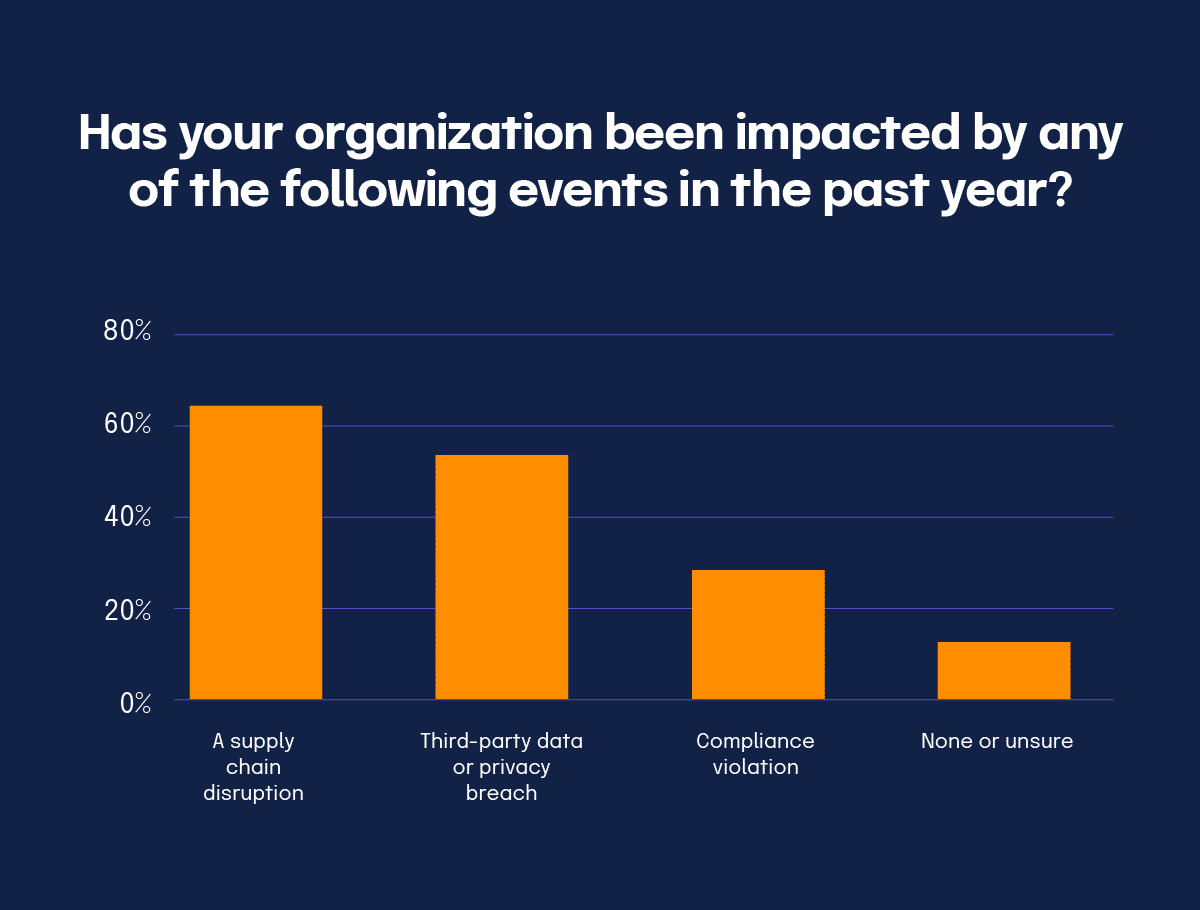
Another concerning finding is that 89% of respondents have experienced or expect an audit finding related to third-party risk management that they cannot promptly resolve. This represents an 18% increase from the previous year, underscoring the growing importance and complexity of third-party risk.
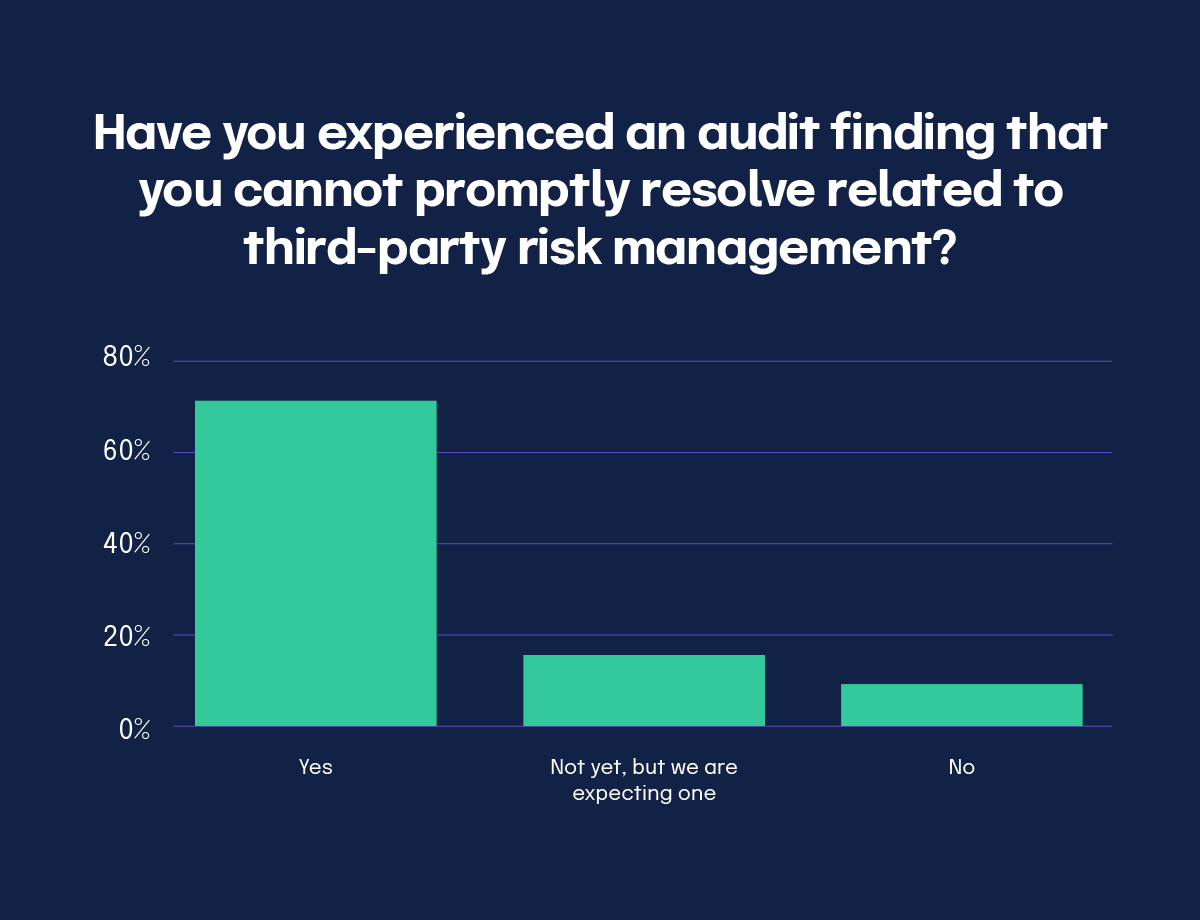
To this point, third-party risk has emerged as a priority, and organizations must proactively address this accelerating threat. However, the manual process of answering more vendor security questionnaires can be overwhelming for GRC and IT professionals, especially as the number of vendors accessing sensitive data grows exponentially.
While compliance violations related to third-party oversight have reduced by 42% this year, the number of data or privacy breaches caused by third-party vendors has increased by 22%. This discrepancy suggests that the focus has shifted towards preventing breaches, while compliance violations may still pose a significant risk.
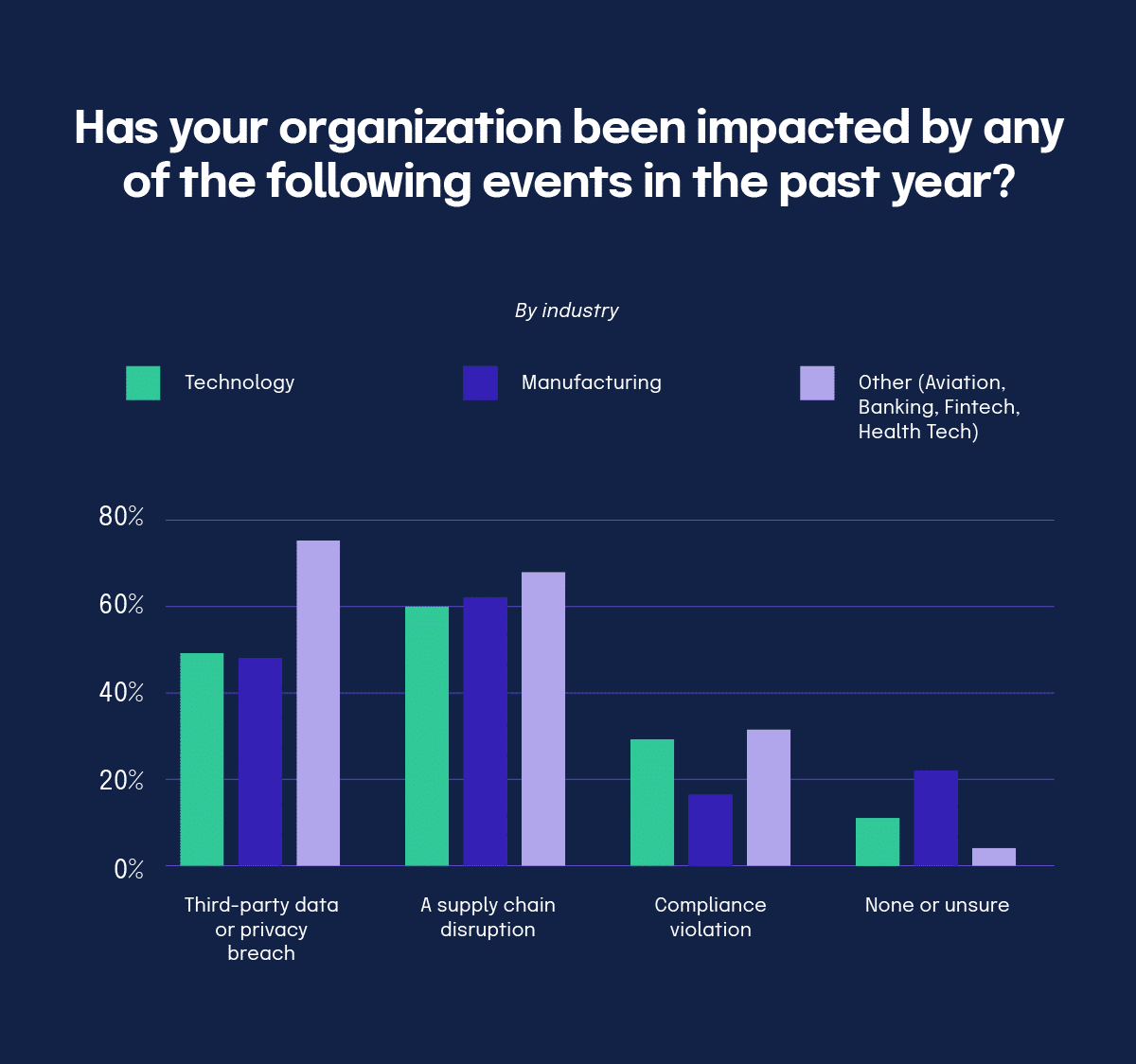
To better manage third-party risk, many are turning to software to improve executing day-to-day tasks, managing vendors, answering security questionnaires, and getting visibility into their compliance and risk postures. Getting this visibility and improved efficiency helps GRC professionals better focus their efforts on preventing breaches and supply chain disruptions.
Third-party risk (and GRC) software usage is increasing

Our survey data indicated that 85% of respondents are already using a platform to manage risk and compliance operations. However, only 25% of these professionals are leveraging third-party modules within their GRC platform. Instead of using integrated solutions, practitioners are forced to use single point solutions to manage third-party risk — or, rather, they are stuck using outdated tech stacks that do not allow for much automation.
Single point solutions can lead to fatigue, especially if many are in place inside one organization. Switching between tools and completing work manually increases the risk of human error, meaning that the very tools used for third-party risk could be posing a danger to the businesses they aim to protect.
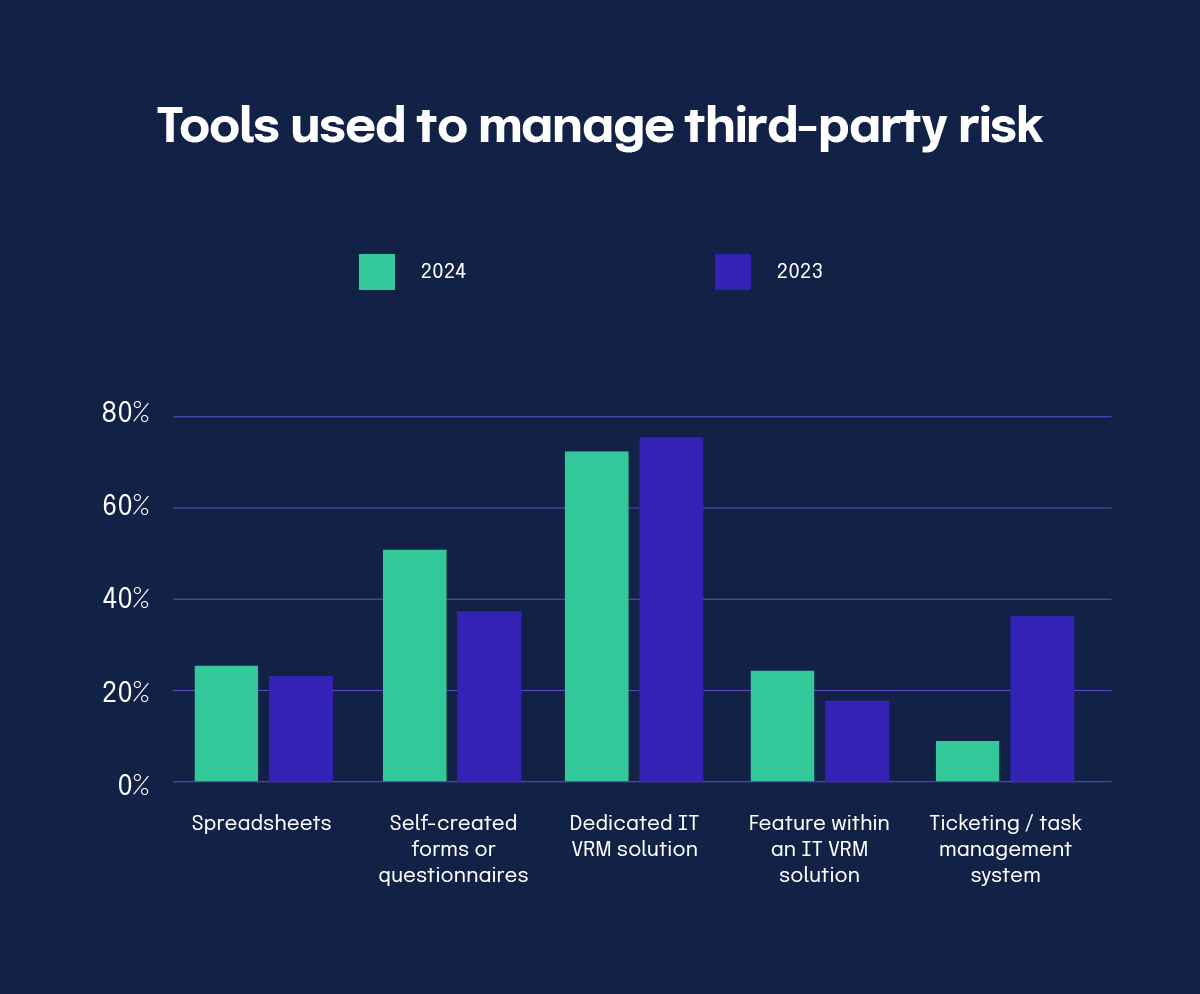
Surprisingly, respondents have also shifted toward using manual tools like forms and questionnaires created in Microsoft Office and Google Suite tools. This may be due to the fact that teams are being asked to do more with less, resulting in existing tools and outdated practices being used.
26% of respondents are still using spreadsheets to manage their third-party risks. This is up 13% from last year’s survey, a surprising finding as the manual work associated with third-party risk continues to overwhelm GRC teams. Meanwhile, those using ticketing and task management tools fell 63%, coming in at just 14% of respondents. The only tools that grew in adoption in our 2024 report were third-party risk modules within GRC platforms, growing 32% year-over-year to account for a quarter of respondents.
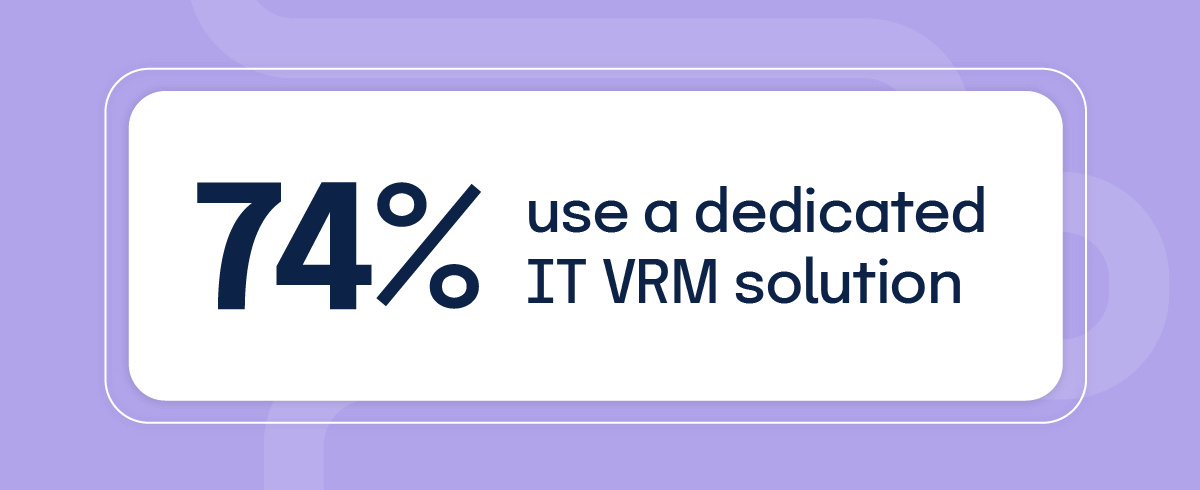
These various platforms suffer from a lack of integration and connection, making third-party risk management more challenging. Respondents are less satisfied with point solutions and are now seeking integrated platforms that include vendor risk management alongside their other GRC work.
Integrated platforms allow for streamlined workflows and operations, resulting in more peace of mind for GRC professionals. With risk and compliance data all in one place, they can get better visibility into the work they’ve done and more easily identify areas of weakness. By bringing everything together, these professionals can better tackle third-party risk management inside their integrated GRC platform, eliminating the need for multiple single point solutions.
Efficient compliance operations are becoming a brand differentiator, and it’s more important than ever to adhere to regulatory standards and bodies. Likewise, the importance of a proactive vendor risk management program is only increasing year-over-year, as the amount of supply chain disruptions continues to grow.
Third-party risk is a challenge, but not unconquerable
Third-party risk management is a complex challenge for organizations, often posing significant regulatory and legal threats. To overcome these hurdles, it is imperative to invest in a comprehensive platform that integrates vendor risk management within a broader GRC framework. By streamlining and automating workflows, organizations can effectively mitigate third-party risks and ensure compliance with regulatory standards.
Vendor risk management is not unconquerable. With the right resources, staffing, and solutions, it’s possible to build out a third-party risk management program that properly protects your organization.
To learn more about our third-party risk insights and other trends we found, including budgeting, staffing, and risk management best practices, download the full IT Risk and Compliance Benchmark Report.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












