Third Party Security Assessment: How to Do It Right
Organizations today rely heavily on third-party vendors and service providers to support critical business functions. While this interconnectedness creates efficiency, it also introduces significant security risks. A comprehensive third-party security assessment program is essential for identifying, evaluating, and mitigating these risks before they lead to data breaches, operational disruptions, or compliance violations.
This article provides a practical guide to conducting effective third-party security assessments, from establishing a foundational framework to implementing continuous monitoring practices. By following these guidelines, security and GRC professionals can build a sustainable program that protects their organization while fostering productive vendor relationships.
Understanding the fundamentals of third-party security risk
Defining third-party security risk assessments
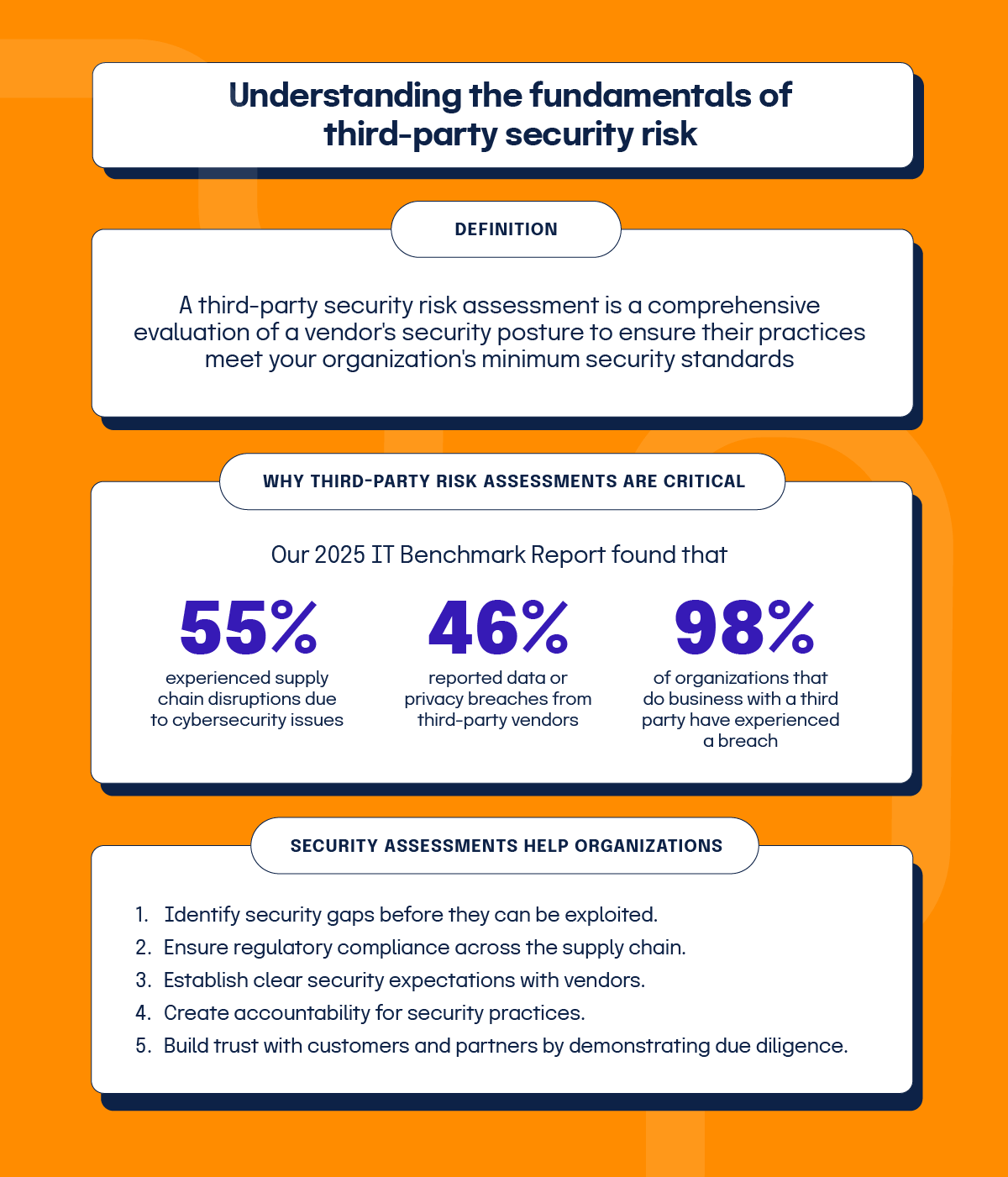
A third-party security risk assessment is a comprehensive evaluation of a vendor’s security posture to ensure their practices meet your organization’s minimum security standards. These assessments examine vendors, partners, clients, contractors, consultants, or any intermediaries that have access to your systems or data.
The assessment process involves inventorying third parties and conducting various risk identification activities, including specialized security questionnaires, real-time risk intelligence feeds, penetration tests, vulnerability scans, certification reviews, and detailed internal policy examinations. The goal is to identify security deficiencies and verify compliance with security standards and regulatory requirements.
These evaluations serve as due diligence exercises that facilitate open communication among stakeholders, enabling transparent conversations about findings and determining appropriate actions when risks are identified. Risk owners must decide whether to accept identified risks, create contractual addendums with the third party, or reject the vendor relationship entirely.
The importance of third-party security assessments
Third-party security assessments are critical due to the increasing interconnectedness of business ecosystems. Our 2025 IT Benchmark Report found that 55% experienced supply chain disruptions due to cybersecurity issues, and a further 46% reported data or privacy breaches from third-party vendors. A statistic from another report further highlights this issue: 98% of organizations do business with a third party that has experienced a security breach. This reality makes these assessments not just a best practice but a necessity in modern information security strategy.
The question for most organizations is not if but when a security incident will occur. Even if your organization has implemented strong internal security controls, those protections may be undermined by vulnerabilities in your vendor ecosystem.
Security assessments provide a critical line of defense against third-party risks in today’s landscape of cyber threats, data breaches, regulatory demands, and interconnected business operations. They help organizations:
Identify security gaps before they can be exploited
Ensure regulatory compliance across the supply chain
Establish clear security expectations with vendors
Create accountability for security practices
Build trust with customers and partners by demonstrating due diligence
Essential components of effective assessment programs
Effective assessment programs integrate several key components to create a comprehensive approach to third-party risk management.
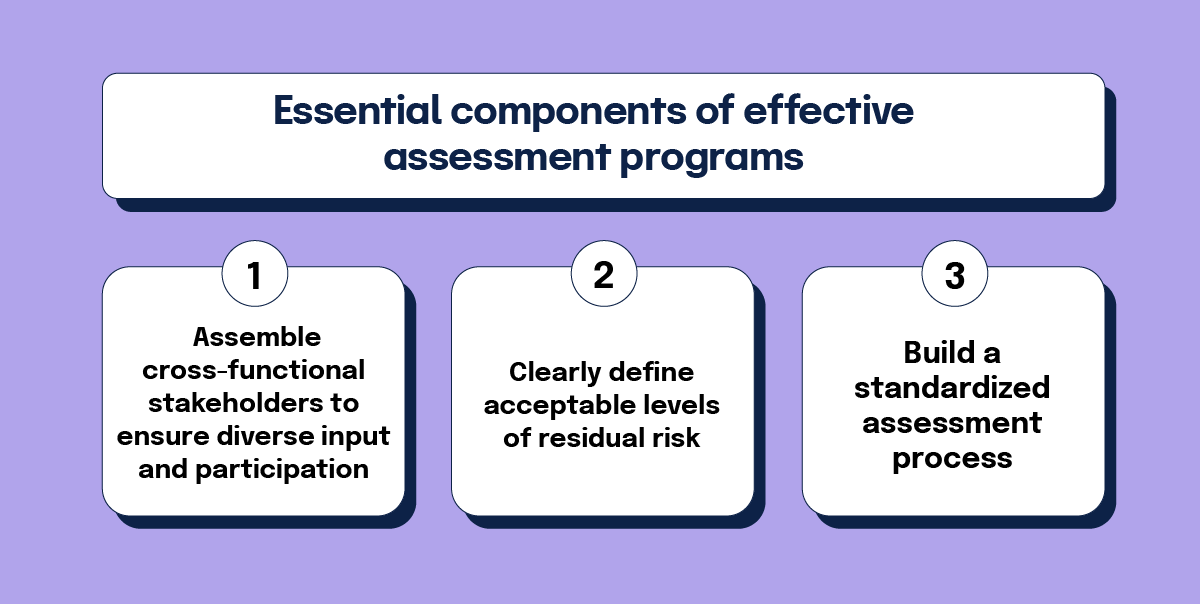
First, assembling cross-functional stakeholders ensures diverse input and participation. These stakeholders bring different priorities and perspectives to the table, and understanding these varied viewpoints helps streamline the program and prevent critical steps from being overlooked. By creating a cross-functional team to guide the assessment program, organizations drive broader adoption and sustainable long-term success.
Second, organizations must clearly define acceptable levels of residual risk. Even with rigorous controls, some risk inevitably remains when working with third parties. Establishing risk tolerance thresholds before evaluating potential partners makes vendor selection more efficient and consistent. This approach quickly identifies third parties that may not align with your business objectives or risk tolerance levels.
Third, building a standardized assessment process is key. This process should vary based on factors like the third party’s criticality to your supply chain, their access to sensitive data, and their vulnerability to continuity events. Third parties with high criticality and potential risk deserve more thorough due diligence than those presenting lower risk. A well-structured process enables more efficient operations and supports better risk-based decisions about your third-party relationships.
Building your third-party security assessment framework
Developing a rigorous 3rd party security risk assessment is the primary way to safeguard your organization’s data in an interconnected world. By formalizing this framework, you ensure that 3rd party security standards are applied consistently across all vendors, from high-criticality cloud providers to low-risk professional service firms.
Regulatory requirements and compliance considerations
Organizations must verify third-party compliance with relevant regulations, as primary organizations are often held accountable for vendor non-compliance. This verification is particularly important for organizations handling sensitive data, such as government contractors and healthcare providers.
For example, regulations like HIPAA hold the primary organization accountable for non-compliance by their vendors. If a healthcare provider’s billing vendor fails to implement required security controls and experiences a breach of patient data, both the vendor and the healthcare provider could face significant penalties. The likelihood of regulators discovering such non-compliance would be high, representing an unacceptable risk that could result in contract termination.Compliance verification should cover industry-specific regulations like HIPAA for healthcare, PCI DSS for payment processing, and GDPR or CCPA for personal data protection. Organizations should also consider broader frameworks like NIST CSF, ISO 27001, and SOC 2® when evaluating vendor security practices.
The assessment process should include reviewing compliance certificates, evaluating security controls, and examining audit reports to proactively assess the risk posed to your organization. Based on these findings, you can decide whether to proceed with the business relationship or take steps to mitigate identified risks.
Establishing roles and responsibilities
Clearly defining duties for all parties involved in the assessment process is essential for accountability and effectiveness. From internal teams to external vendors, each participant should understand their responsibilities and how they contribute to the overall assessment.
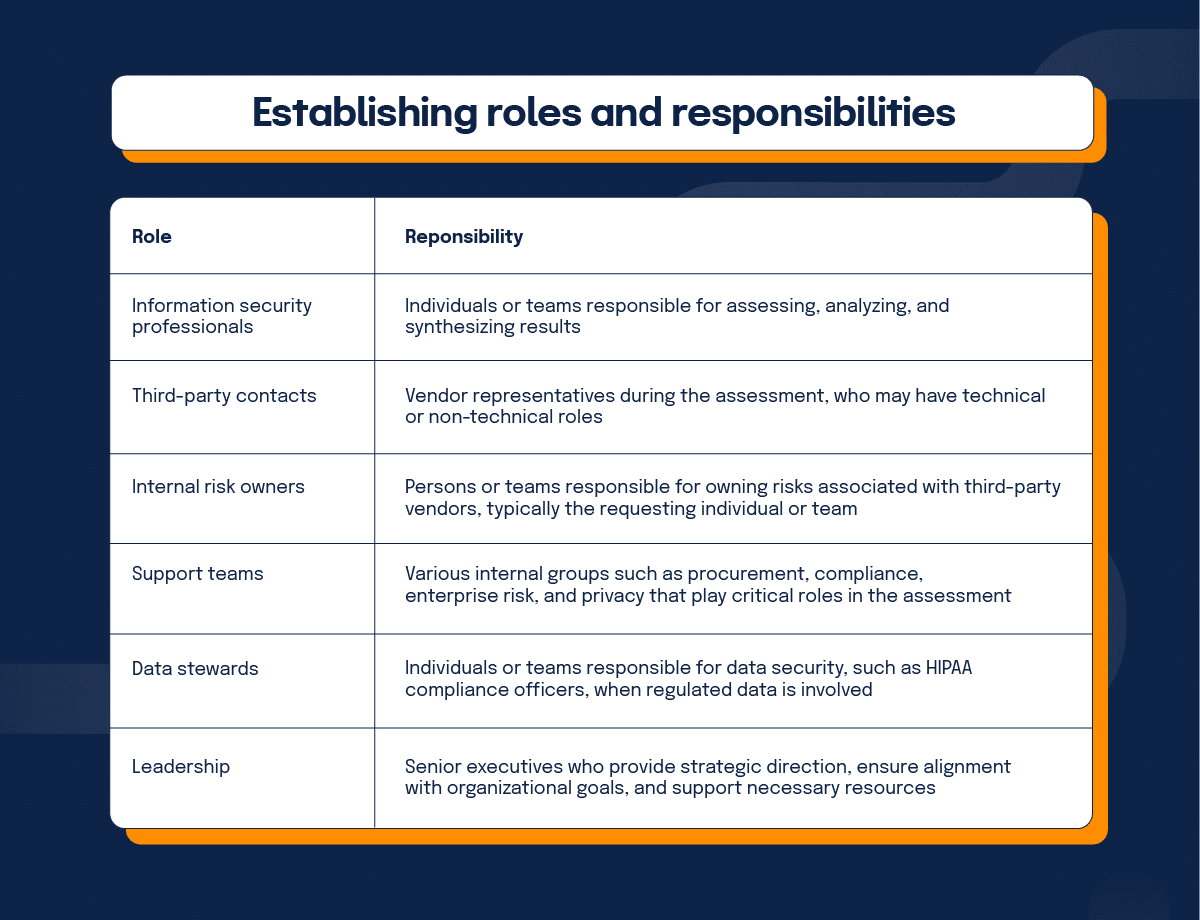
Establishing a clear reporting hierarchy aligned with organizational goals ensures focused accountability and strategic cohesion. This structure clarifies who makes final decisions about risk acceptance, who implements mitigation measures, and who monitors ongoing compliance.
Creating assessment policies and procedures
Developing formal policies establishes clear guidelines and standardized approaches for all assessments, preventing the need to start from scratch each time. These policies should be documented, approved by leadership, and accessible to all stakeholders involved in the assessment process.
Effective assessment policies should address:
Assessment triggers: When assessments are required (new vendors, contract renewals, significant changes)
Assessment frequency: How often reassessments should occur based on risk tier
Methodology standards: Approved assessment techniques and tools
Documentation requirements: What evidence must be collected and how it should be stored
Escalation procedures: How to handle identified risks or vendor non-compliance
Exceptions management: Process for reviewing and approving exceptions to security requirements
These policies embed a structured methodology into your team’s practices, creating consistency across assessments and ensuring that institutional knowledge is preserved even as team members change.
Procedures should provide step-by-step guidance for executing the policies, including detailed instructions for using assessment tools, templates for documentation, and workflows for the entire assessment lifecycle.
Developing a risk assessment rubric
A risk assessment rubric provides a cohesive set of criteria that blends data classification controls with regulatory obligations and internal security standards. This framework guides and measures the effectiveness of your assessments, ensuring consistency and comprehensiveness.
The rubric should include:
Data classification categories: Definitions of data sensitivity levels (e.g., public, internal, confidential, restricted)
Control requirements by classification: Security controls required for each data classification
Evidence standards: Types of documentation accepted as proof of control implementation
Scoring methodology: How to evaluate and rate vendor responses and evidence
Risk calculation formula: How to combine various factors to determine overall risk levels
For example, a simple rubric might tie data classifications to specific evidentiary requirements. A vendor handling public data might only need to provide a security policy overview, while one processing restricted data would need to submit detailed documentation, third-party certifications, and possibly undergo penetration testing.
This structured approach ensures that assessment effort is proportional to risk and that all assessors apply consistent standards when evaluating vendor security.
Setting acceptable risk thresholds
Establishing what level of risk is acceptable for your organization before assessing potential partners makes vendor selection and risk management more efficient and uniform. This approach helps quickly identify third parties that may not align with business objectives and risk tolerance.
If your organization already has defined risk thresholds and tolerances as part of enterprise risk management (ERM), these same definitions can be reviewed and incorporated into third-party risk management. This alignment creates consistency across your risk programs and leverages existing governance structures. Rather than creating separate standards, review your enterprise risk framework and adapt those established thresholds to the third-party context, ensuring leadership has already approved these risk parameters.
Risk thresholds should be defined for different categories of risk, such as:
Data security risks: Acceptable levels of risk for different data classifications
Operational risks: Tolerance for service disruptions based on criticality
Compliance risks: Zero tolerance for certain regulatory requirements versus flexibility for others
Financial risks: Acceptable levels of financial exposure from third-party relationships
Reputational risks: Thresholds for public perception impacts
These thresholds should be documented and approved by senior leadership, with input from legal, compliance, and business stakeholders. They provide clear guidance for decision-making when assessment results reveal security gaps or concerns.
For critical services or sensitive data, thresholds will typically be lower, requiring more stringent security controls and less tolerance for identified risks. For less critical functions, organizations may accept higher risk levels if business benefits outweigh potential security concerns.
Planning and preparing for the assessment
Identifying and categorizing third parties
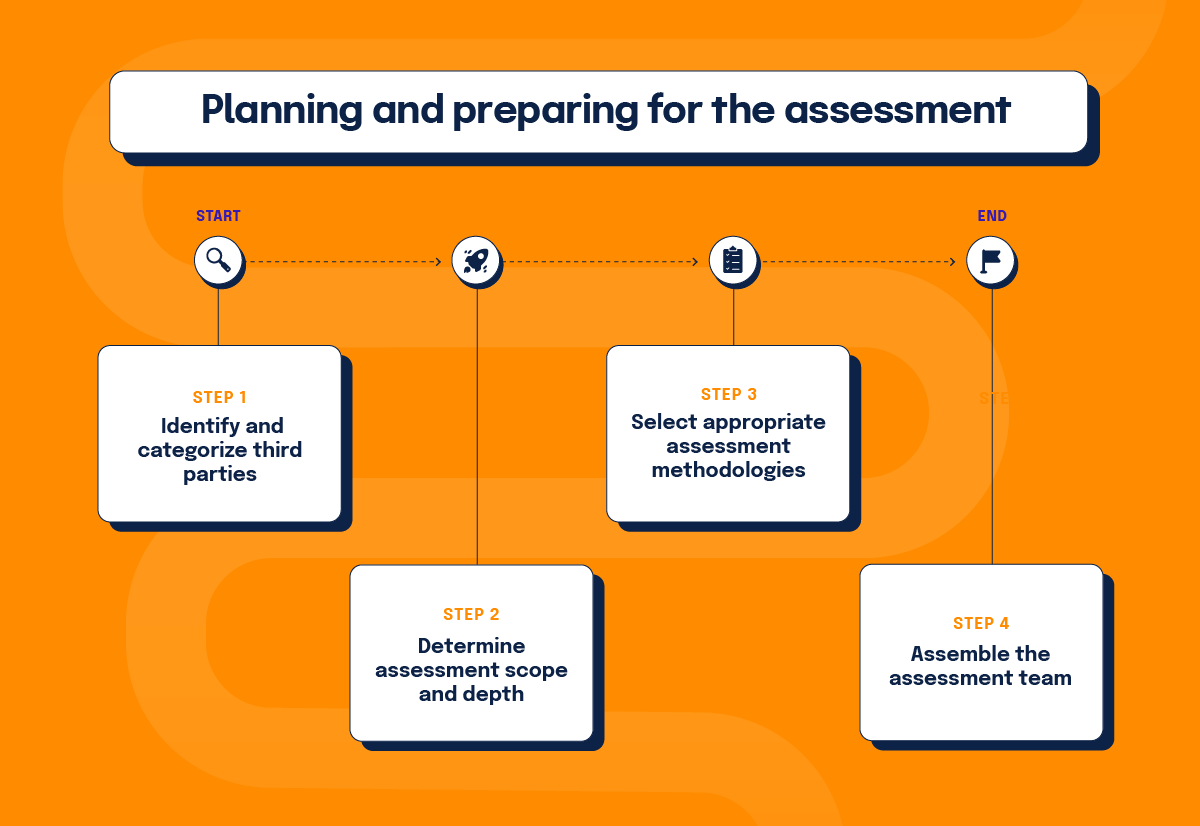
Creating an inventory of all third-party relationships is the foundation of an effective assessment program. This inventory should categorize vendors based on criticality, data access, and potential risk to prioritize assessment efforts.
Start by listing all third parties that require risk assessments, focusing first on those that present the highest risk to your organization. Then, establish supplier risk criteria that include the third-party risks most detrimental to your organization. For example, companies that manage or outsource sensitive data must include specific information security risks in their vendor risk criteria.
These risk criteria will:
To anticipate and avoid possible risks, create detailed diagrams outlining your relationships with third parties. This visualization helps establish standard risk management processes throughout the company and provides insight into the interconnections between vendors and your systems or data.
A tiered approach to categorization often works well:
Tier 1: Critical vendors with access to sensitive data or supporting essential functions
Tier 2: Important vendors with limited access to sensitive data or supporting significant functions
Tier 3: Vendors with minimal access to sensitive data or supporting non-critical functions
This categorization determines the depth, frequency, and rigor of security assessments for each vendor.
Determining asset scope and length
Tailoring the assessment scope based on the vendor’s risk tier is essential for efficient resource allocation. High-risk vendors require more thorough due diligence than those with lower risk profiles.
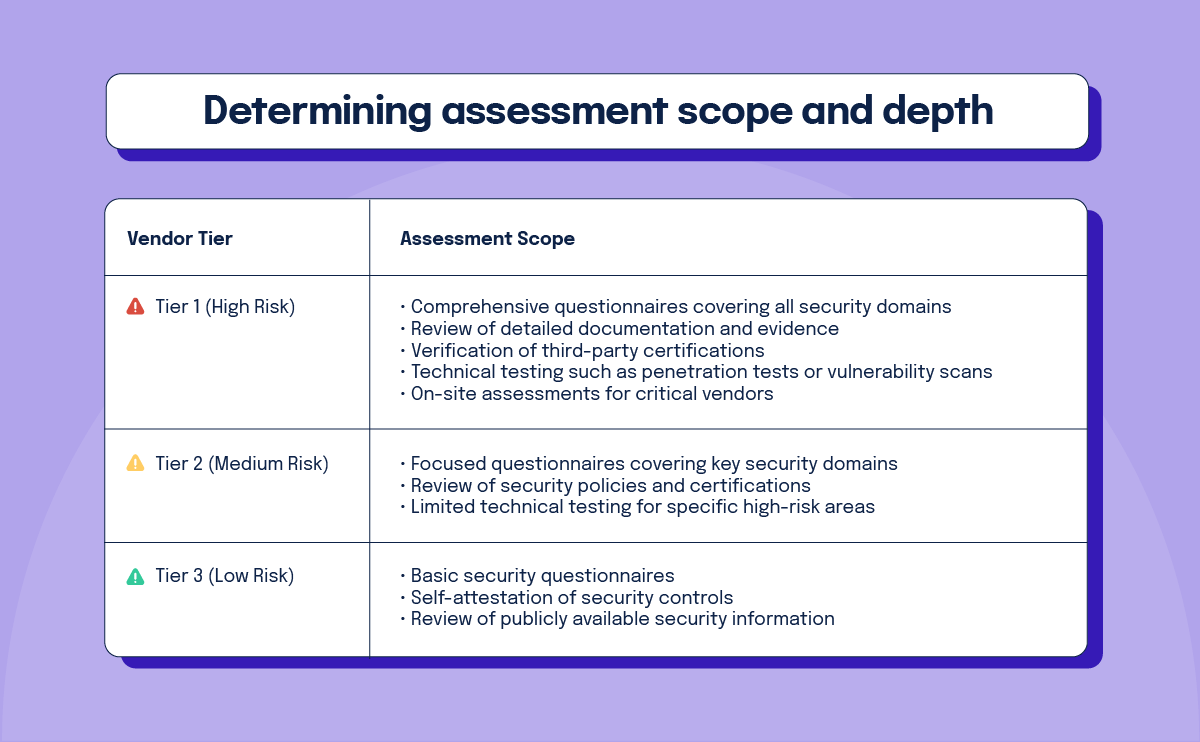
The depth of the assessment should also consider the specific services provided and data accessed. A vendor processing financial data requires deeper scrutiny of encryption and access controls, while a marketing agency needs more focus on data handling and retention practices.
By aligning assessment scope with risk, organizations can concentrate resources where they provide the greatest security benefit.
Selecting appropriate assessment methodologies
Choosing the right assessment methodology is crucial for gathering relevant information efficiently. Organizations must decide whether to use industry-standard questionnaires or create custom templates based on specific risk criteria and requirements.
Industry-standard questionnaires offer several advantages:
Popular standardized questionnaires include:
Custom questionnaires may be preferable when:
Many organizations use a hybrid approach, starting with an industry-standard questionnaire and adding custom sections to address specific concerns or requirements.
Beyond questionnaires, assessment methodologies may include:
The selected methodology should align with the vendor’s risk tier and the nature of the services provided.
Assembling the assessment team
Forming a cross-functional team with representatives from various departments ensures comprehensive assessment coverage and diverse perspectives. The team should include members from information security, procurement, compliance, enterprise risk, and relevant business units.
Key team members and their responsibilities might include:
Assessment lead: Coordinates the overall assessment process, communicates with stakeholders, and ensures timely completion.
Security analyst: Evaluates technical security controls and identifies potential vulnerabilities.
Compliance specialist: Verifies regulatory requirements and contractual obligations.
Business representative: Provides context about the business relationship and operational requirements.
Legal counsel: Reviews contracts and advises on the legal implications of identified risks.
Procurement specialist: Manages vendor relationships and contract negotiations.
For smaller organizations, individuals may fulfill multiple roles, but all perspectives should be represented in the assessment process.
The team should receive training on the assessment methodology, tools, and evaluation criteria to ensure consistent application of standards. Regular calibration sessions help maintain consistency across different assessments and assessors.
Clear communication channels and decision-making authority should be established before beginning the assessment to avoid delays or confusion during the process.
Conducting the third-party security assessment
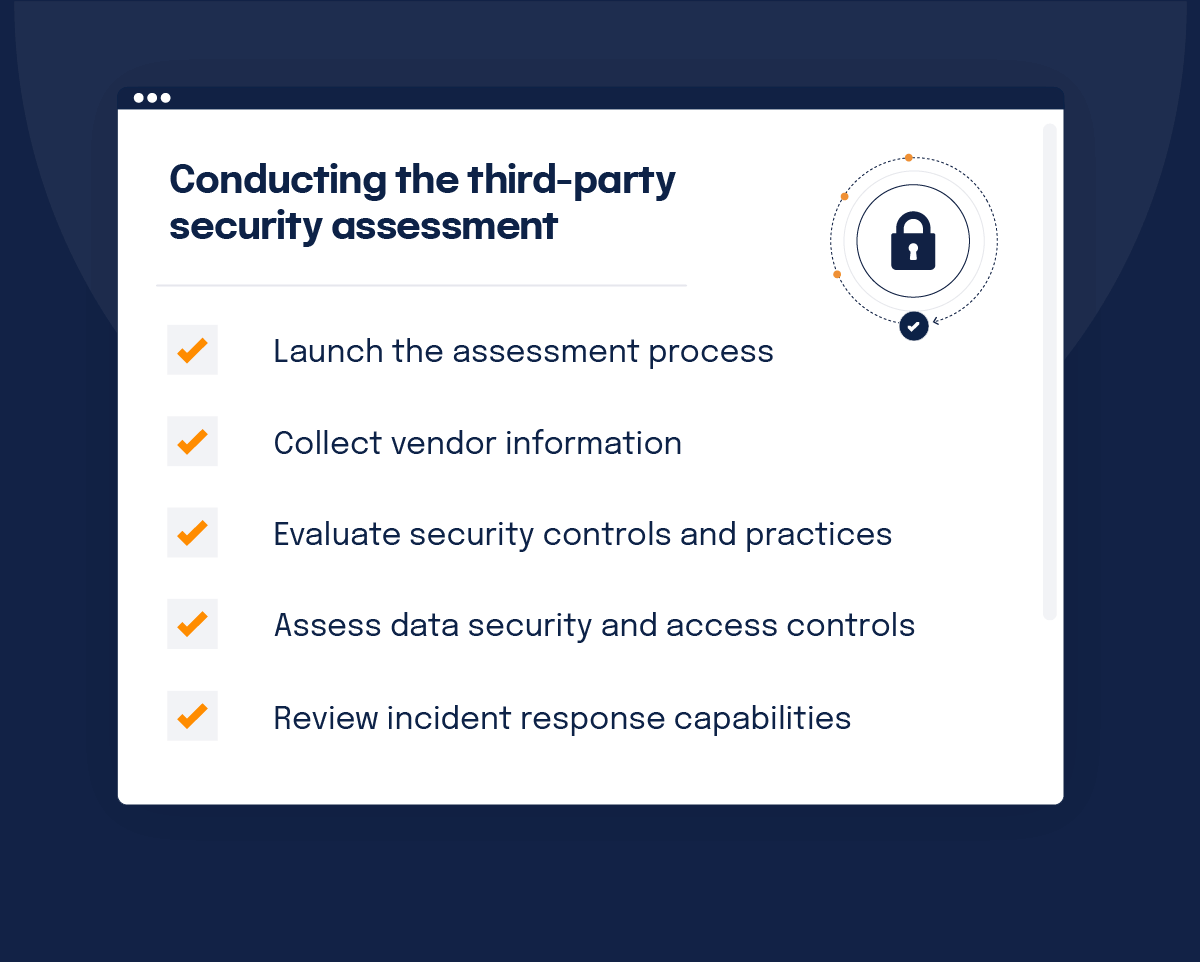
Launching the assessment process
The first step in conducting a third-party security assessment is setting clear objectives, defining necessary evidence requirements, establishing timelines with due dates, and providing structured instructions to participants.
Begin by clearly communicating the assessment purpose to all stakeholders, including the vendor. This communication should explain:
When using assessment management tools like Hyperproof, the process typically starts with a vendor assessment wizard that helps organize assessment details into an interactive survey. This includes entering vendor and product information, assigning responsible business units and teams, and giving the assessment a descriptive name.
Setting due dates and configuring automated email reminders ensures timely responses. Providing clear, structured instructions to participants improves engagement and clarity. These instructions should explain how to complete the assessment, what supporting documentation is required, and how to submit responses.
The launch phase should also include selecting an appropriate questionnaire template that aligns with security frameworks relevant to your organization and the vendor relationship.
Conducting vendor information and evidence
Gathering detailed information and supporting documentation from vendor contacts is a critical phase of the assessment. This evidence provides verification of security controls and practices beyond simple questionnaire responses.
Types of evidence to collect may include:
When requesting evidence, be specific about what you need and why it’s important. Provide clear instructions for secure document submission, especially for sensitive information. Consider using secure portals or encrypted file transfers rather than email for document collection.
Establish a systematic approach to organizing and storing collected evidence. This organization facilitates analysis and creates an audit trail for future reference. Each piece of evidence should be linked to specific assessment questions or control requirements for easy cross-reference.
If vendors are reluctant to share certain documents, consider alternatives such as reviewing documents during virtual meetings, accepting redacted versions, or accepting certifications as proxy evidence of controls.
Evaluating security controls and practices
Assessing the vendor’s approach to cybersecurity, operational controls, disaster recovery, and compliance adherence requires a systematic evaluation methodology. This evaluation should examine both the design and operating effectiveness of security controls.
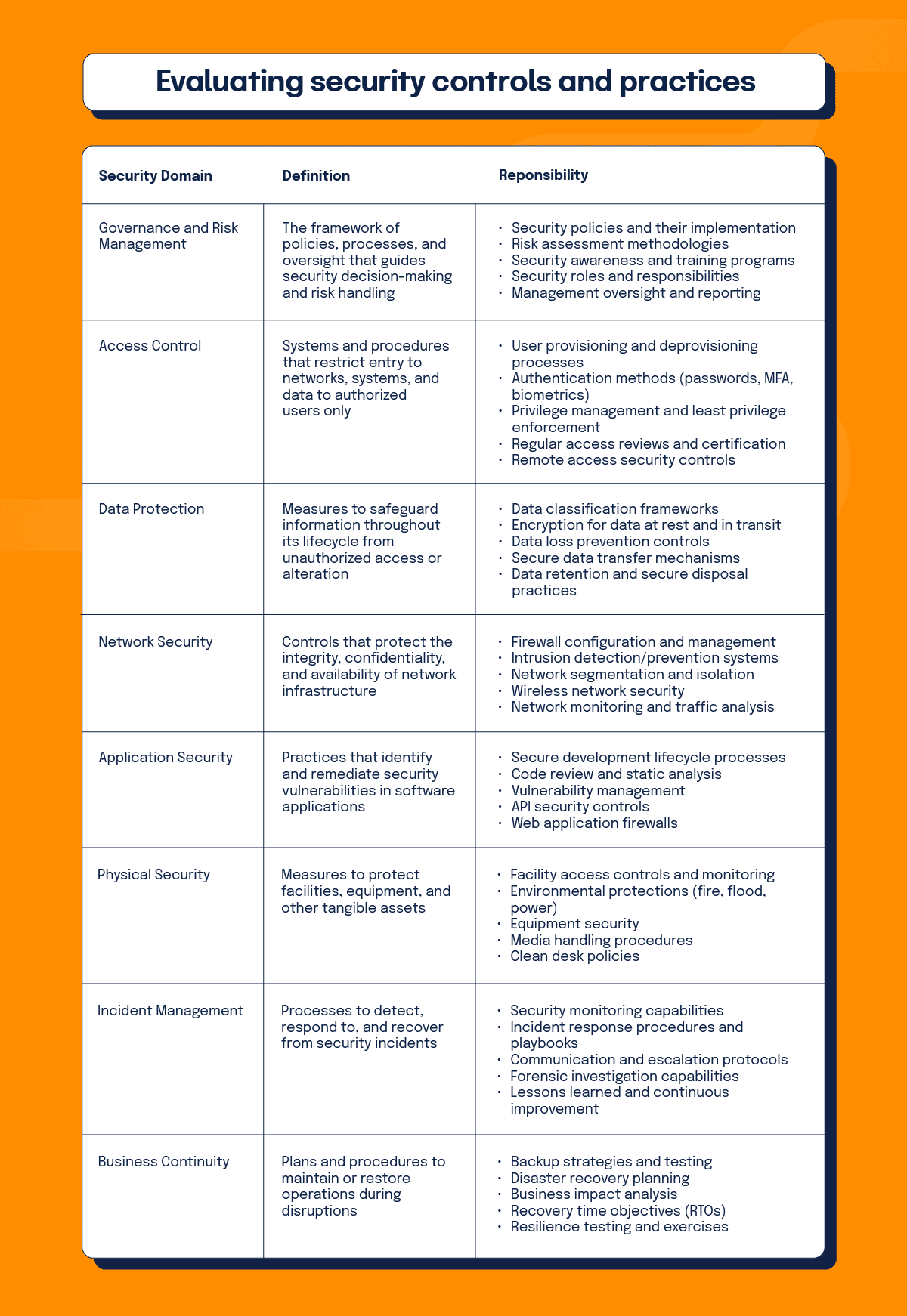
For each domain, assess whether controls are:
Compare the vendor’s practices against industry standards, regulatory requirements, and your organization’s security expectations. Identify gaps where controls are missing, inadequate, or inconsistently applied.
Document your findings with specific references to evidence reviewed and standards applied. This documentation creates a defensible assessment that can withstand scrutiny from auditors or regulators.
Assessing data security and access controls
Verifying that third parties implement proper access controls is particularly important when sharing sensitive data. This verification is critical because 70% of data breaches originate from granting third parties excessive access.
Key aspects of data security and access control to evaluate include:
Data classification: How the vendor identifies and categorizes sensitive data
Access management: Processes for granting, reviewing, and revoking access
Authentication controls: Password policies, multi-factor authentication, and single sign-on
Privileged access: Management of administrative accounts and privileged credentials
Data segregation: How customer data is separated in multi-tenant environments
Data encryption: Encryption methods for data at rest, in transit, and in use
Data retention: Policies for data storage duration and secure disposal
Access monitoring: Logging and alerting for access attempts and anomalies
Many organizations make the mistake of relying solely on contractual terms or vendor reputation rather than verifying access controls directly. This verification should include reviewing access control policies, examining evidence of implementation, and testing controls where possible.
For vendors handling particularly sensitive data, consider requesting additional evidence such as:
Document any gaps in access controls and assess their potential impact on your data security. These findings will inform risk mitigation strategies and contractual requirements.
Reviewing incident response capabilities
Evaluating the third party’s incident detection mechanisms, reporting procedures, and recovery plans determines how quickly they can resolve and recover from security incidents. This evaluation is crucial because the speed and effectiveness of incident response directly impact the potential damage from security breaches.
Key elements of incident response to assess include:
Detection capabilities: Tools and processes for identifying security incidents
Response team: Structure, roles, and training of the incident response team
Response procedures: Documented processes for different types of incidents
Communication plans: Procedures for notifying customers and stakeholders
Containment strategies: Methods for limiting the impact of security incidents
Forensic capabilities: Tools and expertise for investigating incidents
Recovery procedures: Processes for restoring normal operations
Post-incident analysis: Approaches for learning from incidents and improving security
Request evidence of incident response testing, such as tabletop exercises or simulations, to verify that plans work in practice, not just on paper. Review documentation of past incidents (if available) to assess how effectively the vendor handled real situations.
Pay particular attention to notification timeframes and procedures. Your contracts should specify required notification periods, but the assessment should verify that the vendor can meet these requirements through established processes and tools.
Evaluate whether the vendor’s incident response capabilities align with the criticality of the services they provide and the sensitivity of the data they handle. Critical vendors should demonstrate more mature and comprehensive incident response capabilities than those providing less essential services.
Analyzing and managing assessment results
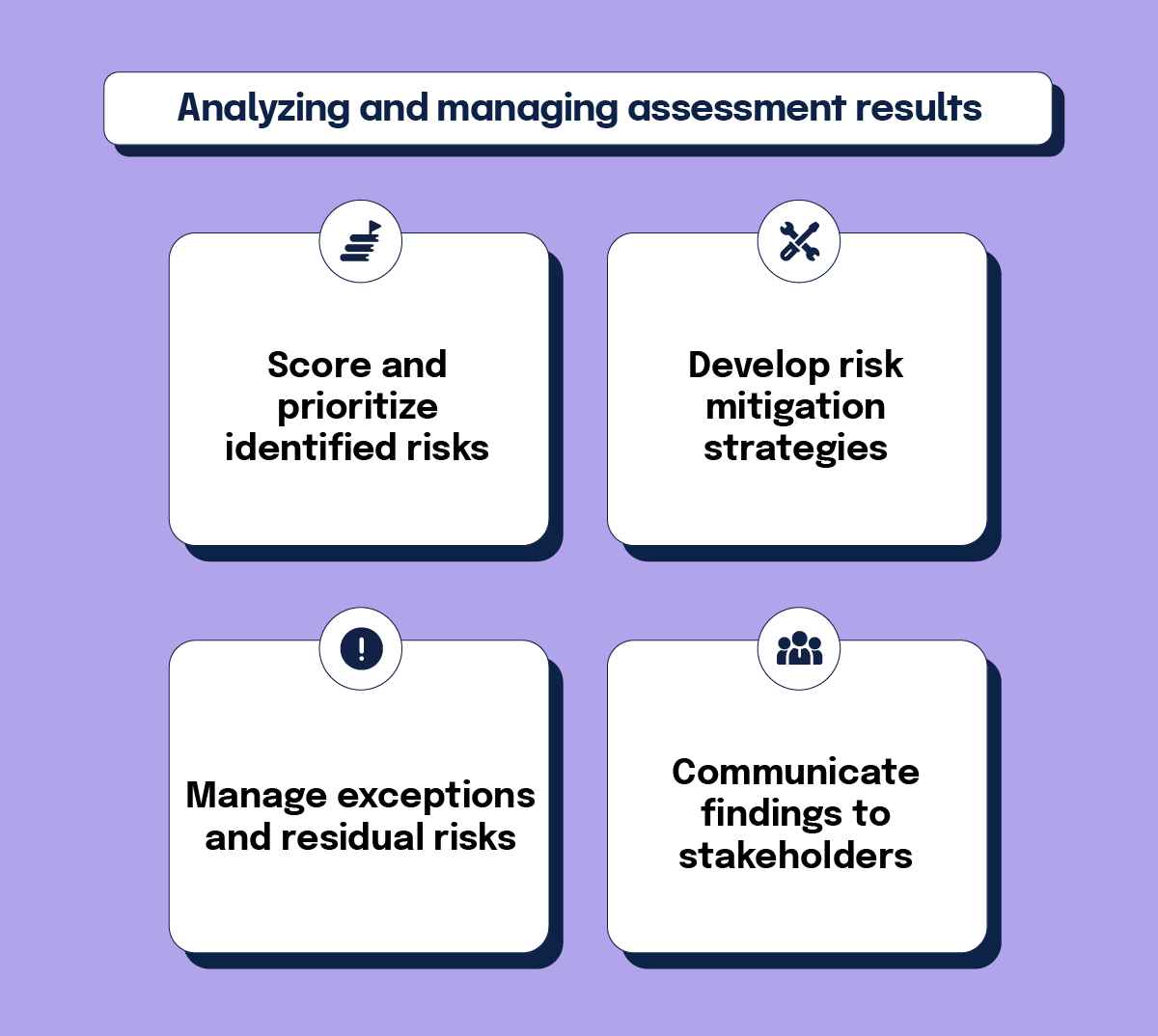
Scoring and prioritizing identified risks
Quantifying each risk on a defined scale and categorizing threats based on potential impact focuses remediation efforts effectively. A systematic scoring approach provides consistency across assessments and facilitates comparison between vendors.
A typical risk scoring methodology includes:
Likelihood assessment: Probability of the risk occurring (1-5 scale)
Impact assessment: Potential damage if the risk materializes (1-5 scale)
Risk calculation: Likelihood × Impact = Risk Score
Risk categorization: Grouping risks as Critical, High, Medium, or Low based on scores
For example, a vulnerability with high likelihood (5) and high impact (6) would receive a risk score of 30, categorizing it as Critical. This scoring helps prioritize which risks require immediate attention and which can be addressed over time.
Beyond numerical scoring, consider categorizing risks by type:
This categorization helps direct risks to appropriate teams for remediation and provides a more nuanced view of the vendor’s risk profile.
Document the scoring methodology and ensure consistent application across all assessments. This consistency enables meaningful comparison between vendors and tracking of risk trends over time.
Developing risk mitigation strategies
Creating plans to address identified security issues according to criticality may include developing better security controls or adjusting third-party policies. Effective mitigation strategies balance security requirements with practical implementation considerations.
Common risk mitigation approaches include:
Risk reduction: Implementing additional controls to lower the likelihood or impact of the risk
Risk transfer: Using insurance or contractual provisions to shift some risk to another party
Risk avoidance: Changing processes or requirements to eliminate the risk entirely
Risk acceptance: Formally acknowledging and accepting risks that cannot be mitigated
For each identified risk, develop specific mitigation actions with clear ownership and timelines. These actions should be:
Mitigation strategies might include:
Document these strategies in a risk treatment plan that is reviewed and approved by appropriate stakeholders, including business owners and security leadership.
Managing exceptions and residual risks
Documenting and managing cases where vendors fall short of minimum security requirements in a central risk register maintains visibility and accountability. Not all identified risks can be fully mitigated, and some exceptions to security requirements may be necessary for business reasons.
An effective exception management process includes:
Exception request: Formal documentation of the security requirement that cannot be met
Business justification: Clear explanation of why the exception is necessary
Risk assessment: Analysis of the security impact of granting the exception
Compensating controls: Alternative measures to reduce the risk
Approval process: Review and sign-off by appropriate authorities
Time limitation: Expiration date requiring reassessment
Documentation: Recording of all exceptions in a central register
Residual risks, those that remain after mitigation efforts, should be formally accepted by business owners with appropriate authority. This acceptance should be documented and include:
Regular reviews of the exception and risk acceptance register ensure that temporary exceptions don’t become permanent and that accepted risks are periodically reassessed as business needs and threat landscapes change.
Communicating findings to stakeholders
Sharing assessment results with all relevant parties facilitates transparent conversations about findings and determines appropriate courses of action. Effective communication ensures that security concerns are understood by business stakeholders and that decisions about vendor relationships are made with full awareness of risks.
Key stakeholders typically include:
Communication should be tailored to each audience:
For high-risk findings, consider face-to-face meetings or video conferences to ensure understanding and alignment on next steps. These discussions should include:
All communications should be documented for future reference, creating an audit trail of risk-based decisions and agreed-upon actions.
Implementing continuous monitoring and reassessment
Establishing ongoing monitoring processes
Implementing continuous monitoring of third parties using risk intelligence tools tracks emerging threats and changes in vendor security posture. Point-in-time assessments provide valuable insights but may quickly become outdated as threats evolve and vendor environments change.
Continuous monitoring approaches include:
Security rating services: Subscription services that provide external security ratings based on observable security practices; however, these results are limited as they do not scan internal infrastructure
Threat intelligence feeds: Information about new vulnerabilities or threats affecting vendor technologies
News and breach monitoring: Alerts about security incidents or breaches involving your vendors
Financial monitoring: Tracking vendor financial stability for early warning of business issues
Compliance changes: Monitoring regulatory changes that might affect vendor compliance
Automated security scanning: Regular vulnerability scans of vendor-exposed assets
These monitoring activities supplement formal assessments by providing early warning of potential issues between assessment cycles. They allow for more timely risk identification and mitigation, reducing the window of exposure to emerging threats.
Establish clear procedures for how monitoring information will be evaluated and what triggers additional investigation or action. Not all monitoring alerts require an immediate response, so defining thresholds and escalation procedures helps focus attention on significant issues.
Setting reassessment schedules and triggers
Developing schedules for periodic reassessments based on vendor risk tier, with additional triggers for reassessment such as security incidents or significant changes, ensures that security evaluations remain current and relevant.
Typical reassessment schedules by risk tier might include:
Tier 1 (High Risk): Annual comprehensive reassessment
Tier 2 (Medium Risk): Biennial comprehensive reassessment
Tier 3 (Low Risk): Triennial comprehensive reassessment
Beyond scheduled reassessments, establish triggers that prompt out-of-cycle evaluations:
These event-based triggers ensure that assessments reflect current realities rather than historical conditions. They provide flexibility to respond to changing circumstances while maintaining a structured assessment program.
Document reassessment schedules and triggers in your third-party risk management policies, and communicate these requirements to vendors during the onboarding process so they understand the ongoing nature of security assessments.
Measuring assessment program effectiveness
Developing clear indicators of success that reflect assessment scope and align with company goals continuously improves the accuracy and value of your assessments. An effective third-party risk program requires ongoing monitoring of assessment accuracy and impact.
Key performance indicators (KPIs) for assessment effectiveness might include:
Annual program reviews help determine whether risks are being effectively identified and addressed. These reviews should examine whether appropriate actions have been taken when risks are identified and whether those actions have been effective in reducing risk.
Gather feedback from various stakeholders, including business owners, vendors, and security teams, to identify improvement opportunities. This feedback can highlight process inefficiencies, communication gaps, or areas where assessment scope could be better aligned with business needs.
Use this information to refine your assessment methodology, update questionnaires, adjust risk scoring, and improve communication processes. Continuous improvement of the assessment program ensures it remains relevant and valuable as threats, technologies, and business needs evolve.
Leveraging technology for assessment management
Using third-party security risk management software streamlines the process of inventorying vendors, managing assessments, collecting evidence, producing scorecards, and tracking risks. These tools enhance efficiency and effectiveness while providing better visibility into the vendor security landscape.
Key features to look for in assessment management technology include:
Vendor inventory management: Centralized repository of all third-party relationships
Questionnaire management: Library of templates and customization capabilities
Workflow automation: Assignment of tasks and tracking of completion
Evidence collection: Secure document upload and storage
Risk register: Documentation and tracking of identified risks
Reporting and dashboards: Visualization of assessment results and program metrics
Integration capabilities: Connection with other security and compliance tools
Platforms like Hyperproof offer solutions specifically designed for third-party security risk management. These platforms provide collaborative environments where teams can work together on assessments, share information, and track progress.
When implementing technology solutions, focus on user experience for both internal teams and vendors. Complex or difficult-to-use systems can create resistance and reduce the quality of assessment data. Look for intuitive interfaces, clear instructions, and streamlined workflows that minimize the burden on all participants.
Technology should support, not replace, human judgment in the assessment process. While automation can improve efficiency, security professionals still need to analyze results, identify nuanced risks, and make contextual decisions based on business needs and security requirements.
Building a sustainable third-party security program
Creating an effective third-party security assessment program requires more than just implementing a set of tools or procedures. It demands a strategic approach that balances security requirements with business needs, establishes clear processes while maintaining flexibility, and builds a culture of risk awareness throughout the organization.
The key elements of a sustainable program include:
By following the guidance in this article, from understanding fundamental concepts to implementing continuous monitoring, security and GRC professionals can build assessment programs that effectively identify and mitigate third-party risks while supporting productive business relationships.
Remember that a third-party security assessment is not a one-time project but an ongoing program that requires sustained attention and resources. The effort invested in building a comprehensive assessment capability pays dividends through reduced security incidents, improved regulatory compliance, and greater confidence in your extended enterprise.
As organizations continue to expand their third-party ecosystems, the ability to effectively assess and manage vendor security becomes increasingly critical to overall security posture. Those who excel at this discipline gain a competitive advantage through more secure operations, better vendor relationships, and the ability to make risk-informed business decisions.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?











