The Zero Trust Security Model: What You Need to Know
Remember the days when security was simple – or so we thought. You locked your valuable data deep inside corporate strongholds. With fortified, high-tech perimeters to lock out the bad guys, security teams rested easy. Threats came from the outside, while everyone and everything inside the fortress received unquestioned trust.
Those days are a distant memory. With the rise of mobile business environments, cloud service, IoT, and bring-your-own-device policies, the nature of security has changed dramatically. Perimeters are extinct, and our data is everywhere. Opportunities to exploit abound and attackers take full advantage.
The time has come to embrace a different security model. In today’s wide-open landscape, with threats coming from all directions, trust equals vulnerability. We must remove trust from the modern environment, verifying everyone and everything regardless of location. Welcome to the age of Zero Trust.
In this article, we will discuss all you need to know about the Zero Trust security model. We will discuss the history, values and principles, technology and strategy, and why Zero Trust is so important right now. Hint: think COVID-19. Most importantly, we will also leave you with helpful tips for implementing Zero Trust in your environment. Let’s get started, shall we?
Zero Trust security: What is it?

Zero Trust is a cybersecurity strategy based on eliminating any trust within an environment regardless of location. Everyone and everything is read as a threat until proven otherwise. All users and devices must be authenticated and authorized before being allowed access to valuable resources.
Traditional castle and moat models live by a “trust but verify” creed. They begin with a de facto trust of all within a network. This model is ineffective today because traditional perimeters no longer exist. Keep in mind everything is mobile, data isn’t confined, and the number of attack surfaces is vast. Additionally, once inside, an attacker can open the door for his friends and move laterally to access vulnerable assets.
Zero Trust challenges the castle and moat premise of allowing any trust to exist in your environment. Zero Trust lives by a “never trust, always verify” mantra based on the assumption all network activity is malicious until proven otherwise. This guilty until innocent mindset may seem harsh, but it’s become mandatory in the modern threat landscape.
The history of Zero Trust security
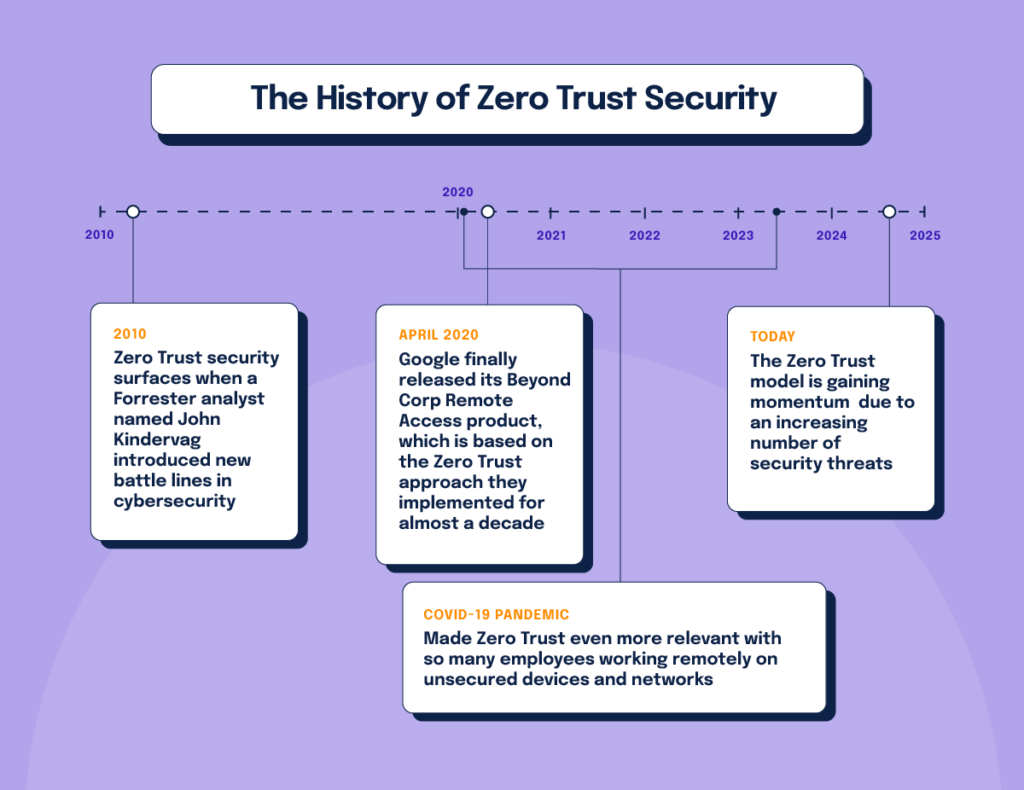
As you probably know, Zero Trust isn’t a new concept. It surfaced in 2010 when a Forrester analyst named John Kindervag introduced new battle lines in cybersecurity. He recognized data wasn’t neatly behind protected walls anymore, and the only way to keep it safe was in a trust-free environment. Google’s adoption and implementation of Zero Trust methodologies created a wider interest. In April 2020, Google finally released its Beyond Corp Remote Access product, which is based on the Zero Trust approach they implemented for almost a decade.
The Zero Trust model is gaining momentum today due to an increasing number of security threats. Organizations are aware of this trend and recognize the severity of its impact on their business. If your business holds personal data, your customers will be concerned about the security of your infrastructure and your ability to adequately protect their sensitive information. Meanwhile, the recent COVID-19 pandemic has made Zero Trust even more relevant, with so many employees working remotely on unsecured devices and networks.
Values and principles of the Zero Trust security model
Zero Trust network security models recognize attackers can come from inside or outside your network. Here is an eye-opening statistic – 18% of data breaches involve internal actors, according to the 2022 Verizon Breach Investigations Report. In Zero Trust, breaches are a given — you must assume the danger is already inside. Thus, everything and everyone is seen as a potential threat. This naturally leads to extremely strict controls on all user and device access within a Zero Trust environment.
Zero Trust is also data-centric — all organizations must identify their data and meticulously map its flow. Keep in mind with no defined perimeters, security must now follow your data.
Access inside a Zero Trust network can be based on either least-privilege or least-functionality. Least-privilege grants access, as needed, based on an individual’s role. Does the user need access to do their job? If so, the user’s identity is verified in real-time through multi-factor authentication. Least-privilege recognizes employees can be accidentally negligent or work in insecure environments such as at home during a pandemic. Least-functionality is different as it monitors access based on the system the individual needs to engage in rather than the person’s role.
Why Zero Trust security systems matter

Zero Trust security matters today because the way the world does business has changed so dramatically. As organizations strive to digitize around the globe, employees, and data are no longer confined behind corporate fortresses. With this mobility comes the monumental challenge of securing a rapidly expanding sea of attack surfaces. Attackers, armed with automation and the newest technology, continue to increase the type and frequency of security threats. In short, cybersecurity has become a virtual street fight where no one can afford the luxury of trust. The numbers are indeed discouraging. Since 2005, the number of breaches has risen consistently in the United States, with 1,802 breaches recorded in 2022 And more than 442 million individuals impacted.
Secondly, regulators have raised the security bar by imposing formidable duties of care for the customer data a company possesses. Strict regulations like the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and the New York Shield Act hold companies responsible for third parties working with that data on the company’s behalf. Failing to comply isn’t an option either, as steep financial penalties can result when a user’s personal information is compromised due to system vulnerabilities.
Lastly, a lack of security is a significant obstacle to customer and market access. Customers want to do business with companies that keep their data safe. And really, can you blame them? Nobody wants to hear their credit card information is possibly circulating in the depths of the dark web. Customers want to see your security risks are under control so they can comfortably entrust you with their personal data.
Technologies and strategies behind Zero Trust security
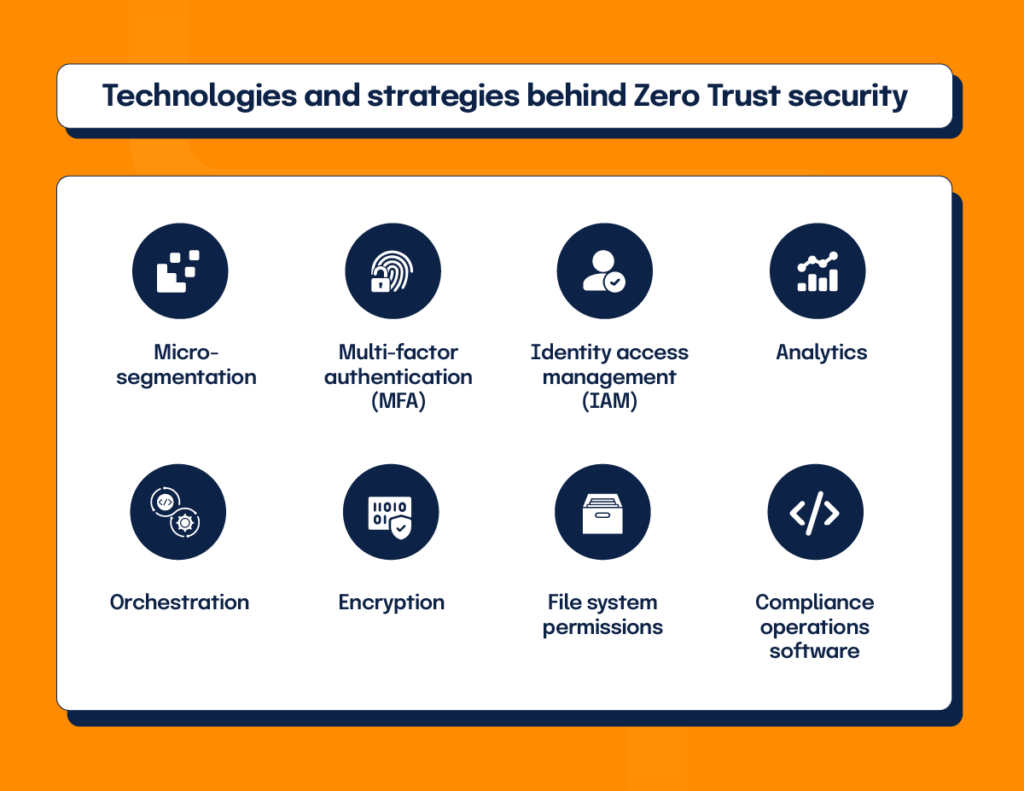
What are the fundamental principles behind Zero Trust’s success? Let’s take a moment and explore a few.
Microsegmentation
This fundamental principle involves breaking networks into separate zones to compartmentalize the damage should a breach occur. Like firefighters locking off sections of a building to control a fire, micro-segmentation reduces the immediate attack surface and gives security teams more control over lateral movement.
Multi-factor authentication (MFA)
This practice is considered essential to maintaining a Zero Trust environment, and many feel even this isn’t strict enough to keep out malicious invaders. Users are granted network access upon showing two or more forms of identification based either on what they know (password), possess (physical item like token or cellphone), or inherently contain (fingerprint or retina).
Identity access management (IAM)
Zero Trust models are built on this practice, which requires positive user identification for access to a network’s resources. IAM uses features like MFA and Single Sign-On (SSO) to verify users and determine the level of access they will be granted.
Analytics
Successfully implementing a Zero Trust security model demands data—lots and lots of it. Applying analytics to user and device behavior data generates risk scores. These scores allow access or sound the alarm siren, triggering alerts requesting further verification.
Orchestration
Think of orchestration as the necessary conductor of your entire security ecosystem. As such, true Zero Trust can’t happen without it. Orchestration aligns your processes for rapid response, replaces slow manual functions with automation, commands action to the needed enforcement points, and consolidates your entire security operation.
Encryption
This practice of converting sensitive data into code to prevent unauthorized use is critically important when operating a Zero Trust environment. With everyone a potential threat, it naturally follows all internal communications, and passwords should be coded in the event they fall into the wrong hands. Remember that the bad guys attack encrypted data through key access, and efficient key management is crucial to maintaining your Zero Trust posture.
File system permissions
These accesses control the user’s ability to view, navigate, change, or execute the contents of a protected file system. Functions may be made available or hidden based on a user’s permission level.
Compliance operations software
This type of software helps risk, compliance, and security officers continuously audit internal security and maintain a secure and compliant information system far easier than manual workflows.
Today’s strict regulations and customer demand mandate the continuous auditing of compliance. Companies must continually prove they are protecting data, effectively managing vendor risk, and staying compliant. Security teams can run ragged with this chore — software that automates compliance workflows (e.g., gathering evidence of controls’ effectiveness, assigning remediation tasks) eases this burden and allows security teams to focus on thwarting hackers and keeping networks secure.
How to get started with the Zero Trust security model

If you are ready for Zero Trust security in your organization, here are the recommended steps:
1. Assess your risk
This must be your first step, starting with an inventory of your assets.
Ask yourself:
- What data is most valuable and needs to be protected?
- What systems process what data?
- Which degree of protection does it need?
- How does data flow between different systems?
2. Segregate your network
Dr. Kenneth Cooper, DCS and CISSP, weighs in here, “To implement full Zero Trust the first thing that needs to be in place is network segregation. All organizational units, devices, and network locations need to be segregated within the actual network, with all subnets and active directory groups for all users set up and in place.” Only with network segmentation in place are you ready to start thinking about your access requirements.
3. Configure specific access
Now it’s time to decide who you will let in, and what they will be able to do once inside. You will need to configure specific per-user, per-application, and per-role, access based on clearly defined identity rules. In Zero Trust these rules are strict with multi-factor authentication always in favor. Access to one environment never means automatic access to others.
Here is where many attempts at Zero Trust go wrong, as Dr. Cooper explains, “Most organizations fail by not killing system-to-system connections for devices sitting in the same domain or network. They also fail to remove or disable default admin credentials across domains. For a true Zero Trust environment, you must deliberately address both these issues.”
4. Train your people
Training and preparing your team for security awareness can make all the difference in the success of your Zero Trust initiative. Employees and contractors can represent a significant risk, even if unintentionally. Melody Kaufman, a Cybersecurity Specialist at Saviynt, reiterates what we all know too well. “As much as you educate, your people will always be one of your weakest links.”
It’s critical to teach your team the overall importance of security and the granular habits they can practice for network safety. Teach employees to recognize common schemes such as phishing and email spoofing. Ask them to use password management systems like LastPass.
5. Enforce least access
Diligently practice both least-privilege and least-functionality access to your most valuable resources. Access is granted only as needed based on the user’s jobs or systems they’re accessing.
6. Use analytics to maintain and monitor your ecosystem
Zero Trust thrives on data, so position your team to maximize the collection and breakdown of this valuable resource. Be prepared to continually test systems and networks to verify the success of your Zero Trust initiative.
Zero Trust Security Final Thoughts
Keeping our information systems and networks secure and compliant is more challenging, and at the same time, more important than ever. The hurdles are higher, and the pitfalls more costly, yet organizations see little forgiveness when they stumble. We live in a mobile world with new battle lines, where trust equals vulnerability, and no one is beyond suspicion.
Are you ready to embrace enhanced security for your organization’s information systems, networks, customers, and future? Learn how the “never trust, always verify” model of Zero Trust can provide protection in the face of remote workforces, dispersed data, and potential attacks from all directions. Take the next steps towards securing your assets – choose Zero Trust today.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?