How Zoom’s Surging Popularity Had Become Its Achilles Heel
When Zoom CEO Eric Yuan announced that his company is giving K-12 schools his video conference tools for free in late February, the story landed an exclusive on Forbes Daily Cover. Zoom’s user base has ballooned massively since that announcement, from 10 million to 200 million daily active users in March. Zoom’s growth in March was truly a historic moment for the company. It’s every company founder’s dream come true.
Yet, just days later, security writer Ivan Metha of TNW has characterized Zoom as “a godforsaken mess”, the FBI has warned citizens about its products, school districts have started banning Zoom from classrooms, and the attorneys general of several states have banded together to investigate Zoom’s privacy and security practices.
In this article, we’ll document the key events around the meteoric rise and fast fall of Zoom. But even more importantly, we’ll comment on the key lessons every risk and compliance leader should take from this turn of events.
Zooming ahead: a quick overview of Zoom’s rise
Zoom has been around for nine years, but Zoom’s easy-to-use video conferencing app became a favorite for hundreds of millions of people around the world as the coronavirus has forced the vast majority of individuals into self-isolation.
According to a Forbes Exclusive published on March 12, CEO Eric Yuan said Zoom had started to brace itself for big changes when the COVID-19 virus disrupted business in China in starting in January. Zoom’s corporate customers like Walmart and Dell reached out with concerns, wondering if their local employees would be able to move full-time communications through Zoom.
Zoom had done a number of things in the run-up to its IPO (April 2019) to be prepared for natural disasters. According to CEO Eric Yuan, Zoom operates a cloud infrastructure using auto scaling, a method that monitors usage of applications and makes it easier to add more computing power when demand increases, then ramp it back down to save costs when demand drops. Because Zoom’s data centers were set up to handle massive surges of traffic, the company felt it was well-prepared to handle the work from home boost.
By early March, Zoom has made its video communication tools free to schools in affected regions, including Japan, Italy and the U.S. The company also removed the time limit from video chats using Zoom’s free service for affected regions in China and elsewhere. As a result of these measures, new downloads of Zoom have exploded in affected regions.
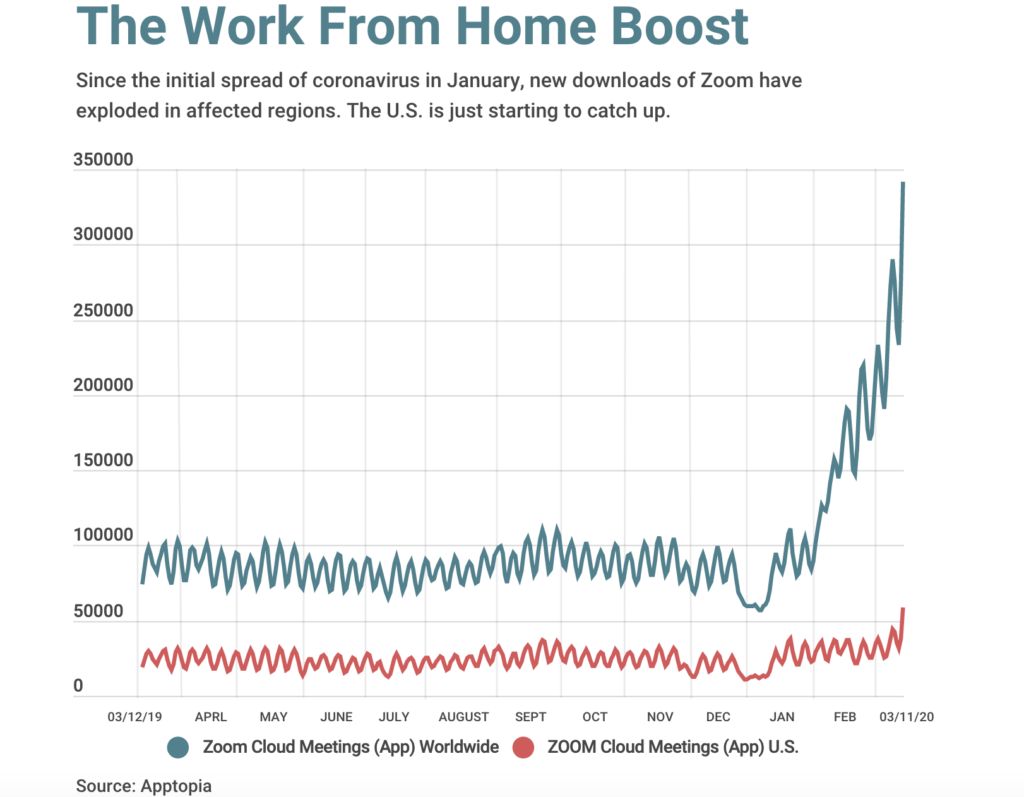
However, the public has recently discovered that Zoom has a dark side and an FBI warning.
Documented privacy and security issues with Zoom
- “Zoom Bombing”
“Zoom Bombing” is a new form of harassment in which intruders hijack video calls and post hate speech and offensive images such as pornography. The issue has become so alarming that the FBI has issued a warning about using Zoom.
No one is immune from this threat. Take for example, founder and editor in chief of tech website The Information, Jessica Lessin, who tweeted a week ago about how her video call was hijacked by someone who shared pornography.
Zoombombing occurs because many of the virtual events people are creating are public — meaning anyone with the link can join the event. As Zoom has become wildly popular, it’s become a prime target for hackers.
One of the best ways for a user to protect themselves from this type of attack is to take precautions, including allowing only signed-in users to join a meeting, locking the meeting, muting controls, and setting up two-factor authentication. All of these are settings Zoom offers within its app.
To Zoom’s credit, the company has given users detailed guidance on how to avoid this phenomenon, in a March 20 blog post titled How to Keep Uninvited Guests Out of Your Zoom Event. Zoom also has an organized library of Training Resources to help users.
However, these measures are probably too late, as the media backlash against Zoom is intensifying. School districts, including New York City’s, have started banning Zoom because of its online security issues.
A screenshot of recent media coverage on Zoom’s security flaws.
2. UNC vulnerability that lets hackers steal Windows credentials via chat
On April 1, HackerNews reported that Zoom has a vulnerability that lets hackers compromise Windows and its login password.
According to cybersecurity expert @_g0dmode, the Zoom video conferencing software for Windows is vulnerable to a classic ‘UNC path injection’ vulnerability that could allow remote attackers to steal victims’ Windows login credentials and even execute arbitrary commands on their systems.
As the article details: “Such attacks are possible because Zoom for Windows supports remote UNC paths that convert potentially insecure URIs into hyperlinks when received via chat messages to a recipient in a personal or group chat.
Security researchers confirmed that Windows automatically exposes a user’s login username and NTLM password hashes to a remote SMB server when attempting to connect and download a file hosted on it.
To steal Windows login credentials of a targeted user, an attacker simply needs to send a crafted URL (i.e., \\x.x.x.x\abc_file) to a victim via a chat interface. Once clicked, the attack would eventually allow the attacker-controlled SMB server SMB share to automatically capture authentication data from Windows, without the knowledge of the targeted user.”
Later on April 1, Zoom CEO Eric Yuan confirmed in a blog post that Zoom has released an update that would fix the UNC vulnerability. The fix appears to be pushing out automatically to users. PCWorld staff reported on the fix and said that they received this as the fixed version number 4.6.9 (19253.0401).
3. Mac Zoom Client allows malicious websites to enable a user’s camera without their permission (July 2019)
Zoom has had privacy issues before the latest batch of news. In July 2019, Jonathan Leitschuh wrote on Medium about a vulnerability in the Mac Zoom client that allows any malicious website to forcibly join a user to a Zoom call, with their camera activated, without the user’s permission. On top of this, this vulnerability would have allowed any website page to DOS (Denial of Service) a Mac by repeatedly joining a user to an invalid call.
Zoom had fixed this vulnerability in July 2019.
4. The Electronic Frontier Foundation raises concerns about the types of data Zoom meeting hosts can see

Highlighting some of the privacy risks associated with using Zoom’s products, the EEF has said hosts of Zoom calls can see if participants have the Zoom video window active or not to track if they are paying attention. Administrators can also see the IP address, location data, and device information of each participant.
5. Multiple state Attorney Generals Looking into Zoom’s Privacy Practices
To pile on top of all the bad press, Zoom is also currently under investigation by multiple states’ attorneys general for its privacy and security practices. It’s the biggest sign to date that its regulatory woes are ballooning as its adoption surges during the coronavirus outbreak.
“We’re alarmed by the Zoom-bombing incidents and are seeking more information from the company about its privacy and security measures in coordination with other state attorneys general,” Connecticut Attorney General William Tong told POLITICO in a statement.
Based on POLITICO reporting, we know that Florida Attorney General Ashley Moody is a part of the coordinated effort and has been in contact with Zoom. On March 31, a University of Florida student meeting on Zoom was bombarded with racist messages pornography and death threats.
In response, Zoom has released a statement, saying, “We appreciate the outreach we have received on these issues from various elected officials and look forward to engaging with them.”
What Zoom’s leadership has said in response to criticism

Zoom CEO Eric Yuan broadly addressed various parties’ criticisms in a blog post on April 1, saying the company plans to shift its resources for the next three months toward improving privacy and security features.
When asked about the school districts that are banning its platform, Zoom said in a statement:
We are deeply upset to hear about the incidents involving this type of attack and we strongly condemn such behavior. Starting on March 20th, we have been actively educating users on how they can protect their meetings and help prevent incidents of harassment through features like waiting rooms, passwords, muting controls and limiting screen sharing. We have also been offering trainings, tutorials, and webinars to help users understand their own account features and how to best use the platform. We are listening to our community of users to help us evolve our approach — for example, we recently changed the default settings for education users to enable waiting rooms by default and ensure teachers by default are the only ones who can share content in class. Finally, we encourage users to report any incidents of this kind directly to https://support.zoom.us/hc/en-us/requests/new so we can take appropriate action.” (source: The Washington Post)
Additionally, Zoom is responding to new criticism on a daily basis by publishing the facts on their security and privacy features (see articles like “Response to Research From University of Toronto’s Citizen Lab” and “The Facts Around Zoom and Encryption for Meetings/Webinars“)
4 Essential risk and compliance lessons we’ve taken from Zoom
1. Risk assessments and mitigation strategies need to accommodate unexpected events — including new user types
The events endured by Zoom have highlighted the critical importance of conducting risk assessments on a regular basis, reprioritizing risks when a company is poised to go through an inflection point (e.g. hypergrowth), and preventing new users from making user errors that magnify risk.
Leaders need to conduct risk assessments whenever they anticipate significant growth, identify emerging risks and put new control processes in place.
Zoom had built a platform with one primary segment in mind — large institutions with full IT support. Zoom’s CEO Eric Yuan admitted in the April 2 blog post that “They did not design the product with the foresight that… [they] would have a much broader set of users who are utilizing our product in a myriad of unexpected ways.”
These new Zoom users are students, teachers, parents and others without tech background. They don’t have the same level of security knowledge or training as employees who work in big banks or global healthcare organizations (Zoom’s typical customer profiles). They can make user errors (not follow security best practices), become victims of cyber attacks/harassments –and all of it will reflect badly on the company.
We don’t know what type of risk assessment Zoom’s risk management function conducted before the company announced their free software offer to school districts back in late February. However, based on public information from Zoom’s website, we can reasonably assume that Zoom didn’t anticipate the need to devote more resources towards addressing the security and privacy ramifications of getting a sudden influx of new users –many of whom have little knowledge of how to protect themselves online.
To avoid what has happened, Zoom could have reviewed their video communication app for security and privacy risks, and put risk mitigation mechanisms in place (e.g. patches, security training for new users) before making their free software announcement.
Related content: Conducting an Information Security Risk Assessment: a Primer
The importance of training users

The lack of user education on how to use Zoom settings appropriately to protect meetings is a leading cause of Zoom’s publicity nightmare.
While the Zoom app itself did have some security issues (e.g., the Windows client vulnerability), much of the damage was around “Zoom Bombing”, which happened because newer users were creating public meetings and failing to use appropriate Zoom settings (e.g. meeting password, only allow signed-in users to join, two-factor authentication) to make their meetings secure.
While Zoom does have a fair amount of user documentation, they could have made a much bigger push to educate their new users on how to protect their meetings and stay safe online before giving them free access. It looks like the company didn’t act on an insight that’s common knowledge in security circles —from a security perspective, your users are your weakest link.
2. Be transparent about your flaws. Apologize sincerely.
When you make a mistake, know that you have a chance to turn things around. Your customers — whether individuals or enterprises — are capable of understanding your position and forgiving your wrongs as long as they get a sincere and timely apology, and a credible promise that the same mistakes won’t happen again.
To Zoom’s credit, the company provided a timely and sincere apology. On April 2nd, their CEO Eric S. Yuan put out a message to their users, admitting that Zoom “[has] fallen short of the community’s — and [their] own — privacy and security expectations.”
Not only that, but Zoom was also quick to respond to the immediate issues to prevent further damage. Which brings us to the next point.
3. Respond quickly to minimize further loss.

While we don’t have enough facts to score Zoom on their incident response process in general, we’re willing to give the company points for activating its incident response plans fairly quickly once reporters started to publish articles on “Zoombombing” and the Windows vulnerability this past week.
Zoom was quick to patch up the Windows vulnerability and put out guidance to newer users on how to Keep Uninvited Guests Out of Your Zoom Event. (March 20, 2020), Zoom has also updated its privacy policy (March 29) to be clear and transparent around what data it collects and how it is used — explicitly clarifying that the firm does not sell their users’ data and has no intention of selling users’ data going forward.
Over the next 90 days, Zoom has announced that it is “dedicating the resources needed to better identify, address, and fix issues proactively.” This includes:
- Enacting a feature freeze and shifting all engineering resources to focus on their biggest trust, safety and privacy issues
- Conducting a comprehensive security review with third-party experts
- Preparing a transparency report that details information related to requests for data, records, or content
- Kicking off a weekly webinar to provide privacy and security updates to their community.
- And more
Related content: How to Create a Cybersecurity Incident Response Plan
4. Don’t wait for public outcry to address security, privacy and compliance issues
Although Zoom is doing a fine job of navigating through the sticky situation it has found itself in, it is unfortunate that things turned out this way for a company that’s sincerely trying to do some good in the midst of the Coronavirus crisis.
Zoom is likely to pay a hefty price as a result of negative media attention and regulatory scrutiny. Even though a portion of users will see the company’s promise to do better as a reason to continue to use the service, others will not be as forgiving. This unfortunate turn of events can be a boon to Zoom competitors.
Additionally, reputational damage and loss of customers aren’t the only costs Zoom will have to pay. According to Zoom’s blog post on April 2, the firm is enacting a feature freeze, effectively immediately, to devote all engineering resources to focus on safety, trust and privacy issues.
A feature freeze feels like a massive price to pay for restoring trust, and it was likely incredibly difficult it was for Zoom’s leaders to make such a decision. While the decision seems like the right call for the company as a whole, it’s easy to picture how this could impact morale on the engineering team. Again, this creates a window for competitors to catch up to Zoom.
Related content:
The Four Signs of an Effective Compliance Program
The Complete Guide to Governance, Risk and Compliance
Last Thoughts
While there are many products that have security and data privacy issues, Zoom was singled out in the media this week and by regulators as an example — because of its meteoric rise.
In the first couple of weeks of March, it looked like Zoom’s rise was unstoppable. It is unfortunate that its darling status was quashed so quickly because of safety, security and privacy compliance issues. All product-centric companies should take these lessons from Zoom — to ensure that your growth doesn’t become your achilles heel.
If you’re interested in hearing more about Hyperproof and how we can help your organization build your business on a solid compliance foundation, we’d love to talk. You can reach out to us here and we’ll get in touch soon.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?










