Guide
5 Steps to Creating an Effective Third-Party Risk Management Program

Why You Need to Have a Third-Party Risk Management Program
Maintaining information security used to be much simpler — or at least it seemed to be, right? In the past, most business applications were hosted on-premises and security teams guarded defined perimeters and secured corporate networks.

Oh, how the game has changed. Right now your company is probably working with dozens if not hundreds of third parties (e.g., SaaS vendors, cloud infrastructure, professional service firms) to handle all kinds of business processes.
According to a Deloitte survey, more and more companies today engage vendors to fulfill critical business functions: 70% of businesses rate their dependence on outside vendors as moderate to high. Many vendors now have access to sensitive customer data while performing their jobs, and vendor-caused risk incidents have become incredibly common. In fact, 47% of businesses surveyed by Deloitte experienced a risk incident involving an outside vendor.
Customers trust you with their sensitive data, and if you choose to work with a third-party vendor that doesn’t have adequate data protection safeguards, you’re putting your customers’ privacy and peace of mind in jeopardy and your own reputation on the line.
Threats to customer data can come from a vendor whose IT team forgot to apply the latest patches to their own software, or from rogue insiders who abuse their inside knowledge for personal gain (e.g., trading on confidential information about your business or stealing intellectual property). Natural disasters or financial failure can shut down an unprepared vendor, leaving you in a position where you’re unable to deliver a mission-critical service to your customers.
These unfortunate outcomes can be avoided when organizations take the time to understand the risks each potential vendor poses and only work with those that have responsible security safeguards, business continuity plans, and disaster recovery plans in place. To that end, organizations need to maintain strong governance over their vendor network.

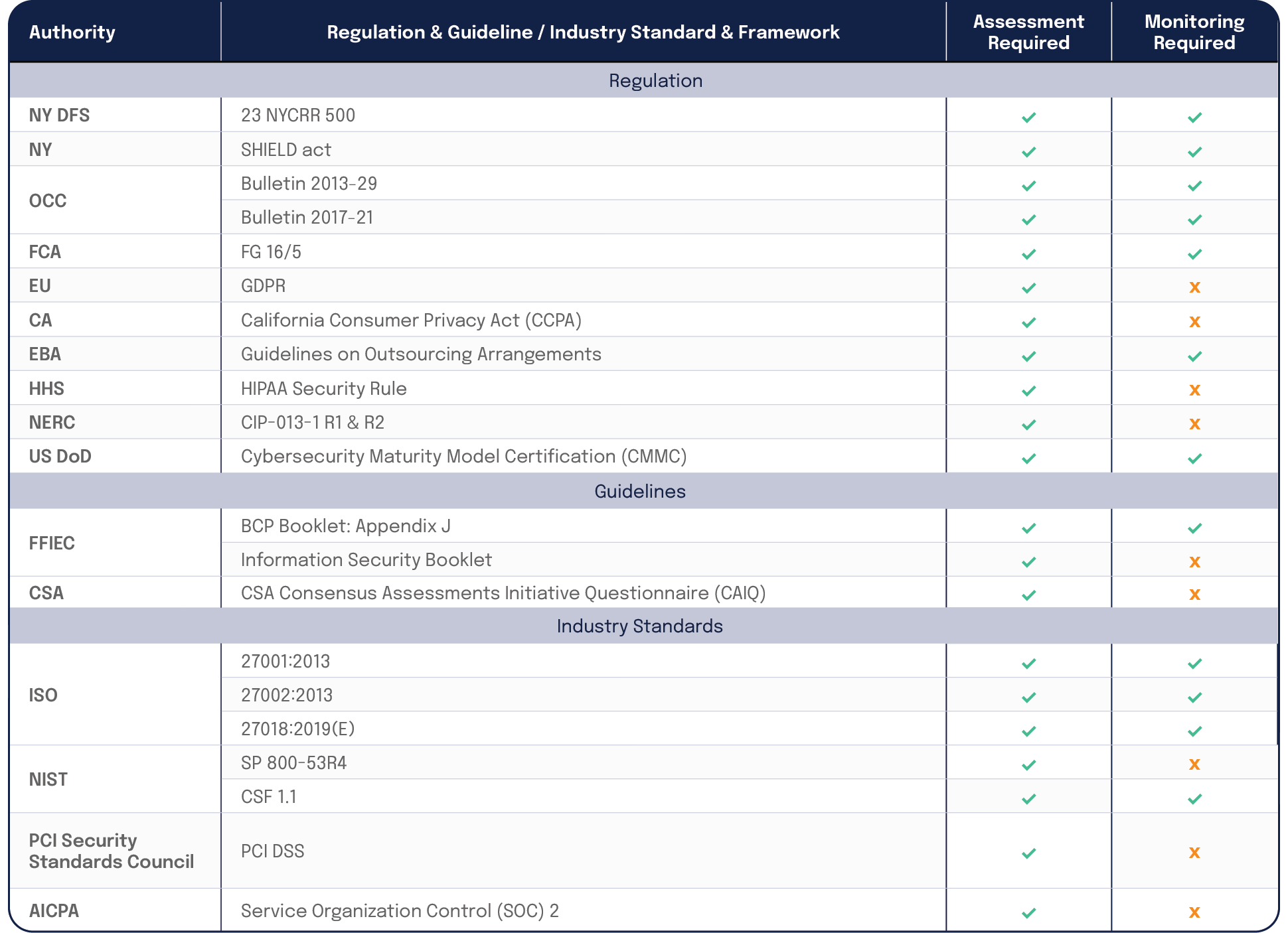
Further, an increase in third-party regulations ranging from CMMC, GDPR, the SHIELD Act, CCPA, as well as authorities including SOC 2®, CSA STAR, EBA, HIPAA, ISO 27001, NIST CSF, and PCI DSS, has forced companies to develop effective third-party risk management programs to meet regulatory compliance and deepen IT security controls.
However, this is easier said than done. Organizations often struggle with the initial step of creating an effective vendor risk management program: knowing which of their vendors pose the greatest risk to their operations. In fact, when Hyperproof surveyed over 1,000 risk and security professionals across North America and the UK in December 2020, we found that 1 in 2 respondents said they have trouble understanding the true risk profile of their vendors.
In this eBook, we’ll walk you through the nuts and bolts of how to build an effective vendor risk management program.
Understand the types of risks vendors can pose
How to Maintain Strong Governance Over Your Vendor Ecosystem: 5 Essential Steps
If you want to maintain strong governance over your vendors, you’ll need the following steps:
1. Know who your vendors are and which ones are critical

You can’t maintain strong governance over your vendors if you don’t know who they are. Start by getting a comprehensive picture of your vendor landscape. Different vendors present different risk levels and should not all be evaluated with a cookie-cutter approach. For instance, an HRIS system working with sensitive employee and company information presents a much higher level of inherent risk than a contracted copyeditor hired by your marketing team.
You’ll need to define whether a vendor is “critical” to your organization. To identify whether a particular third-party meets this bar, considering asking:
Understanding the Types of Risks Vendors can pose
When a vendor has significant access to your company’s internal operations and plans or your customers’ data, that access creates a lot of risks. The most immediate and dangerous ones include:
The list above is by no means exhaustive, but it illustrates that a compliance or risk management failure at one of your vendors can leave your business exposed to significant compliance, litigation, and operational risks of your own.
Understanding Thirdy-Party Risk Management Compliance Requirements
If you’re looking to do business with large enterprises in highly regulated industries, government agencies, or consumers in the EU, you will have to achieve a number of security compliance regulations and frameworks. Many of them have requirements specifically around managing third-party risk. CMMC (from the US DoD), GDPR (from the EU), SHIELD Act (from New York), CCPA (from California), as well as authorities including AICPA (SOC 2®), CSA (CAIQ), EBA, HHS (HIPAA), ISO, NIST and PCI have dictated third-party risk management requirements for organizations, including:
- Set the rules of third-party engagement based on your organization’s risk tolerance and data security and privacy policies
- Include these rules, as well as auditing requirements, in third-party contracts
- Evaluate third-parties via risk assessments in the form of questionnaires or surveys
- Continuously monitor third parties to verify compliance
On the next page is a summary table of regulations, guidelines and industry standards that require the use of internal third-party risk assessments.
If you do not take necessary steps to manage third-party risks, you could get into hot water (legally speaking) for your vendors’ mistakes. For example, to be compliant with GDPR, organizations must take necessary measures to protect citizens’ data in their care, including data that is shared with third parties.
Because many data breaches occur through third-party relationships, GDPR plainly states that these parties (known as data processors) must handle data security and privacy in a way that is compliant with regulation. If you work with a data processor and you didn’t vet their data security and privacy practices, if they experience a breach regulatory authorities can act against you, with fines totaling up to 4% of annual global revenue or 20 million euro, whichever is greater.
2. Assess vendors’ risk level to your organization

Once you’ve identified your critical vendors, you want to understand what they’re currently doing to mitigate security, operational, and compliance risks. There are a few options for assessing vendors’ risk level ranging in cost and level of effort.
- Send the vendor a security questionnaire
- Ask your vendors to send you proof or documentation from their recent IT security audits (e.g., SOC 2® Type 2 report)
- Conduct a full-blown evaluation with an onsite visit 4. Use third-party security ratings
These options are complementary and can be combined or utilized separately depending on vendor type, criticality, and risk level.
Security questionnaireS
The most common method organizations use today is to send the vendor a risk assessment questionnaire to understand what risk management processes a vendor has in place, how they approach data security, business continuity and disaster recovery. Questionnaires can help you make a reasonable determination about whether a vendor can be trusted to handle your business process and data.
Security questionnaires should be tailored to particular vendors, not one-size-fits all, and creating a highly relevant vendor security questionnaire is not an easy feat by any means. This task will likely involve at several people, including someone from the risk management/security team who’s well-versed in security best practices and knows your internal security standards, someone else who knows about all the legal requirements your company is subject to as it pertains to vetting third parties, and a third person who is a power user of the particular vendor application.
To ask the vendor questions that generate meaningful risk insights, the questionnaire designer (e.g., a risk or security or vendor management professional) needs to gather information such as:
Typical subjects covered in a security questionnaire include information security and privacy policies, physical and data center security, web application security, infrastructure security, hiring and personnel policies, and business continuity and disaster recovery plans.
Standard best practice is to use an industry standard questionnaire as the starting point and then tailor it based on your organization’s needs. Here are some industry standard security assessment methodologies you can start with:
CIS Critical Security Controls (CIS First 5 / CIS Top 20): The Center for Internet Security (CIS) is a non-profit entity that wants to safeguard private and public organizations against cyber threats. CIS’s 18 controls are a prioritized set of actions designed to protect critical systems and data from common cyber attacks. These are highly effective controls that reduce cybersecurity risk and map to most major frameworks, such as the NIST CSF, NIST 800-53, ISO 27000 series, and regulations like PCI DSS, HIPAA, NERC CIP and FISMA.
Consensus Assessments Initiative Questionnaire (CAIQ). Created by the Cloud Security Alliance, it provides a set of Yes/No questions you may wish to ask of a cloud service provider to determine if their cloud services are reliably secure.
Standardized Information Gathering Questionnaire (SIG / SIG-Lite): SIG and SIG-Lite were created by the Shared Assessments Program, a trusted source for third-party risk management resources including tools and best practices to manage vendor risk. The SIG questionnaire is a tool to assess cybersecurity, IT, privacy, data security, and business resiliency. SIG-Lite is a compilation of higher level questions from SIG and is generally used for low risk vendors.
Keep in mind that questionnaire responses only provide you a momentary snapshot of a vendor’s risk position.
Security Audit reports and penetration testing reports

Instead of sending one-off security questionnaires to each vendor, many procurement and IT risk teams will ask their prospective vendors to show them their most recent security audit reports (e.g., SOC 2®Type 1 and SOC 2® Type 2 reports). A SOC 2® report details a CPA firm’s independent opinion on a company’s control design and control operating effectiveness over a period of time. The report answers common questions regarding an organization’s controls related to security, availability, confidentiality, processing integrity, and privacy.
Security teams may also ask their vendors to show their latest penetration test report — a report written by an independent party who tested the organization’s security set-up to uncover vulnerabilities to affected assets. Pen test reports can give your security team a deeper level of confidence in vendor hiring decisions; they include detailed write-ups on all detected vulnerabilities, how the vulnerability can be exploited, and the likelihood of exploitation. The pen tester will also include remediation advice in the report.
On-site security audit
On-site audits are exactly what they sound like: an independent security auditor would come to your offices to audit digital assets (e.g., configurations and code), controls, and evidence of their effectiveness. The auditor may physically observe processes happening in certain digital systems, and they would meet with people who have access to digital assets.
During the meeting, the asset would be presented and key artifacts (e.g., logs, screenshots, config files, etc.) would be provided (e.g., sent to by email, copied to a thumb drive, or uploaded to a portal) to the auditor for further examination. An auditor may audit non-digital assets (like physical security) or digital assets connected to physical endpoints (e.g., LAN access from a physical access).
Security Ratings
Another option you might consider are security ratings. Security ratings companies such as BitSight do their own data aggregation and analysis on many companies to determine each company’s security ratings. They provide users visibility into issues impacting their vendors that is backed by data that correlates to potential security incidents.
3. Streamline your evidence management workflows

Once you’ve collected information to help you understand your key vendors’ security posture, you’ll need to make the call on what you want to do about it. Are you comfortable using the vendor’s software or service as-is? Or would you want to invest additional resources to get your organization to a place where they would be comfortable utilizing that vendor? Or is it time to part ways and find a different vendor?
The answer is that it depends on your internal vendor risk appetite: the amount of risk you’re willing to tolerate. This is something that needs to be agreed-upon by internal stakeholders, most likely a cross-functional group of individuals in roles including:
4. Mitigate risks with a contract

For vendors and risks you’re genuinely concerned about, you can put measures (or controls) in place to reduce the likelihood that certain risk scenarios will materialize. One of the most effective things you can do is to create clear, comprehensive contracts with your vendors. This is where you can list the risks that matter to you and negotiate the measures the service/software provider will need to take to address those concerns. Give this document all the time and attention you believe it needs.
Realistically, the largest companies — the Googles and Salesforces and Amazon Web Services of the world — will give most customers virtually zero room to negotiate specific contract language. You will take what they provide on their terms, or you look elsewhere. Even then, the contract is still important because it helps you understand what your risks are. From there, you can engineer the compliance policies and controls you’ll need in place to use those services successfully.
However, there are many smaller vendors who will negotiate contract terms with you. In that case, you want to maintain several important provisions.
Those are only some examples of clauses you could include in a contract with your SaaS provider, and accuracy in the details is crucial. Make sure to consult with legal counsel to ensure you have a contract that addresses what’s important to you and does so in the right way.
5. Monitor, test, and audit vendors

It is possible that a vendor will make a promise and not live up to it, so as important as a contract is, testing, monitoring, and internal controls are still crucial to a successful relationship.
For instance, test the access controls and other security protocols your software provider uses. You want the assurance that those protocols work as promised; and even if those security measures don’t meet your ideal standards, you at least want to understand them so you can implement remediation steps at your own organization.
Along similar lines, monitor security incidents within your own organization, and scan the internet to check whether your data is published somewhere without your authorization. Then trace those incidents back to the source and see if any of your vendors is the cause.
Challenges You May Face Throughout the Vendor Management Lifecycle
1. Maintaining an up-to-date list of vendors

In Hyperproof’s 2021 IT compliance benchmark survey, we found that even seemingly simple tasks, such as maintaining an up-to-date list of all vendors and getting complete questionnaire responses back from vendors, are harder than they seem. 55% of all respondents struggle to get complete risk information on third-parties (and have trouble understanding the true risk profiles of their vendors).
Many organizations aren’t using a central system to track all of their vendors, what each vendor is used for, who owns the vendor relationship, etc. When certain basic information is missing, it is incredibly difficult for risk and security professionals to even start to put together a meaningful vendor security questionnaire.
2. Developing a security questionnaire that generates meaningful insights about a vendor’s risk profile
Creating a highly relevant vendor security questionnaire takes time and thoughtful effort. To develop questions that generate meaningful risk insights, the questionnaire designer (likely the risk/security professional) needs to know who’s using the vendor system, what business processes are supported by the vendor system, what types of data are processed through the system, how it connects with other systems, and more. The risk manager also needs to learn about the legal/compliance risks involved in this vendor relationship and whom to work with at the vendor side to work through the questionnaire.
Once the security questionnaire designer has this context, they still need to put in the time to generate thoughtful questions that will elicit accurate responses from the vendor. Unfortunately, many IT risk and security professionals don’t have the luxury of time to develop effective questionnaires because they’re struggling with the basic mechanics of collecting vendor risk information. In fact, 51 percent of surveyed professionals told Hyperproof that collecting vendor risk information is a manual and highly tedious process. Many are doing this work in ad-hoc tools like Google Forms, email threads, and spreadsheets and, as a result, spending vast amounts of time to piece together the full picture of a vendor’s risk profile.
3. Managing remediation projects and monitoring vendors after onboarding
As if gathering relevant, timely vendor risk information isn’t tough enough on its own, post-assessment, risk/security professionals also need to ensure that remediations are happening on time and any changes to vendors’ risk level are discovered quickly. Since most organizations don’t have tools that automatically collect this data and alert the right individuals when there are issues with particular vendors, risk managers are struggling through these tasks manually with makeshift tech stacks.
In fact, 45% of all respondents to Hyperproof’s 2021 IT Compliance Benchmark Report told us that ongoing vendor monitoring and due diligence is one of the most difficult challenges they face in the vendor risk management process!

4. Providing proof of vendor risk management activities for compliance purposes
As we mentioned earlier, many regulations and security frameworks have obligated companies to collect proof of their vendor risk management activities. If you haven’t been organizing your compliance artifacts (e.g., vendor questionnaire responses, additional tickets created to track remediations, contracts detailing requirements for vendors to mitigate security risks) all along, it will be a big headache to track down all the documents you need to show to auditors when audit day arrives.
How VRM Software Supports Strong Governance Over Your Vendors and Makes the Process More Efficient
Vendor risk management software (VRM) solutions enable vendor management, risk, security, and procurement professionals to effectively manage the assessment process for third parties and vendors over the life cycle of their relationships. They can also help you manage your compliance efforts.
These solutions can be used to collect and aggregate a range of risk data from vendors, third parties, and external content sources to support regulatory vendor risk requirements, as well as internal policies governing the engagement of vendors.
As you look to evolve your vendor risk management program to keep up with organizational growth, vendor risk management solutions like Hyperproof can provide the tools to automate risk assessment and remediation processes, provide risk and performance reporting, support better risk-based decisions, and make compliance work much more efficient. With Hyperproof you can:
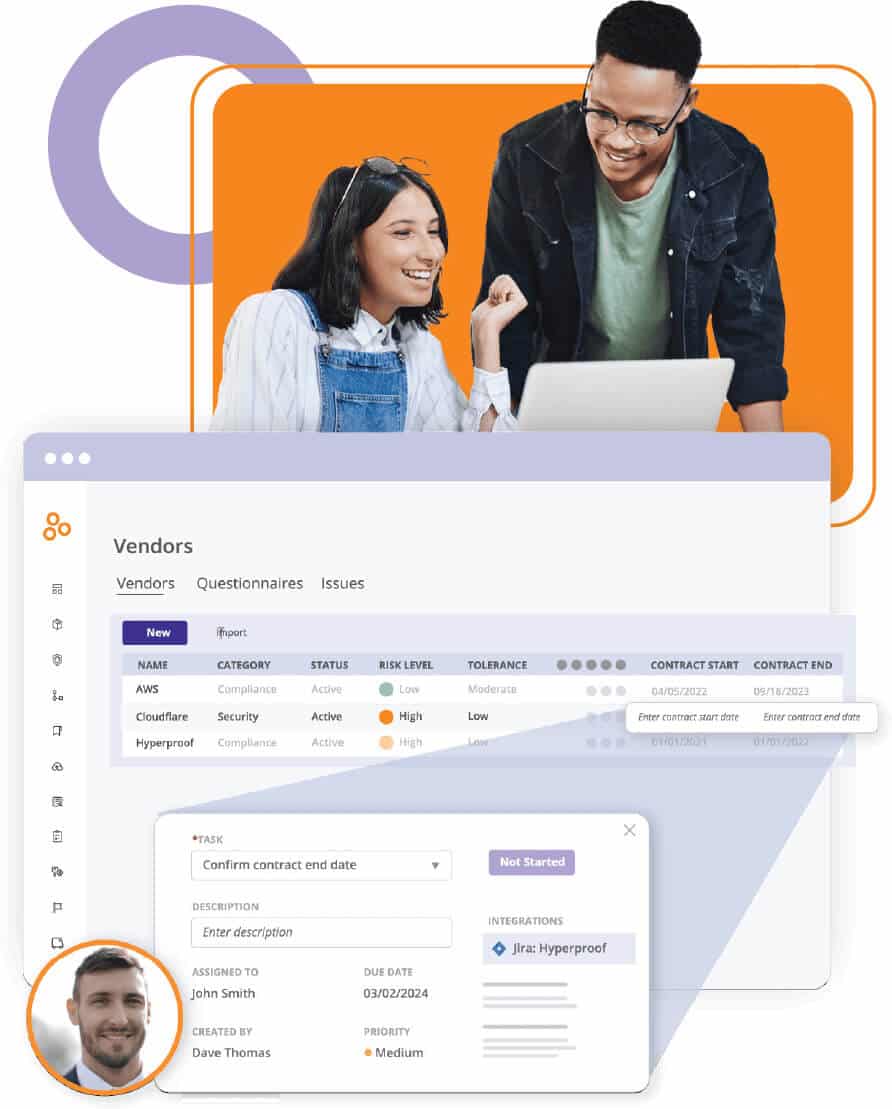
1. Maintain oversight of all vendors
Hyperproof can be the home for all of your contracts, documents, and vendors. You can use tools in Hyperproof to manage, assess, track, and report on your vendors to improve oversight of vendor relationships and the relationships’ health.
2. Assess vendors through questionnaires
Hyperproof provides intuitive built-in tools for risk assessment, vendor criticality, and risk scoring. You can utilize pre-built or tailored questionnaires and send them to vendors to collect relevant information, and all responses will come back to a central location and be easily accessible for decision-makers.
3. Collaborate with vendors and internal stakeholders through risk assessment and remediation processes
Once you’ve reviewed responses from a vendor’s security questionnaire and have decided that you would like them to do something to give your team greater assurance, you can issue a vendor (or internally stakeholder) a task directly from Hyperproof. Tasks can be tailored by vendor criticality and questionnaire responses.
In addition to our built-in project management system, Hyperproof also integrates with many project management and communication tools (e.g, Jira, Slack, Microsoft Teams, Outlook, and Gmail), allowing everyone to work in their preferred tool and for all the messages and tasks to be automatically synced into Hyperproof in the right place (i.e., directly tied to a vendor). Hyperproof also provides tools to automate tasks, alerts, and reminders—helping stakeholders stay on top of all their tasks.
Having a great project/task management system for vendor risk management can make a big difference to security. After all, when someone responsible for testing the access controls and other security protocols of your software vendor forgets to do the work, one missed vulnerability can be exploited to launch an attack that compromises your customers’ data which then causes your company millions in losses.
4. Reduce vendor risks
You can add controls to mitigate specific risks — and Hyperproof will show you the residual risk on your vendors. Hyperproof comes with visual reports so you can see residual risk for each vendor, which vendors still need to complete questionnaires or respond to followup questions. All of this makes it easy to determine what vendors and tasks require attention.
5. Demonstrate compliance with no extra effort
Within Hyperproof, all vendor management activities — including questionnaire responses and tasks around remediation projects — can be linked to risks, controls, regulatory compliance requirements you’ve already added within the software. Hyperproof provides dozens of built-in templates for security and data privacy standards such as SOC 2, CMMC, NIST CSF, ISO 27001, PCI DSS, and more — and it can serve as the central hub for managing all of your organization’s compliance efforts. Using Hyperproof to manage vendor risk and ensure that your security program aligns to industry security standards also makes it easy to retrieve proof of vendor due diligence activities within seconds for an audit.
Download the PDF