Vendor Risk Assessment Challenges: What You Need to Know

Right now, your company is likely working with dozens or hundreds of third-parties (e.g., SaaS vendors, cloud infrastructure, professional service firms) to handle all kinds of business processes. Some of them are in possession of your company’s IP and/or sensitive (and regulated) customer data. Do you know who these critical vendors are? Have you made sure that they’re really able to protect valuable information from sophisticated threat actors?
Doing due diligence on your vendors — starting with conducting a vendor risk assessment — isn’t just a good, common-sense practice; it’s also required legally. A number of regulations ranging from CMMC (from the US Department of Defense) and GDPR (from the EU) to the SHIELD Act (from New York) and CCPA (from California), as well as authorities including AICPA (SOC 2), CSA (CAIQ), HHS (HIPAA), ISO, NIST and PCI, require companies to develop effective third-party risk management programs to meet regulatory compliance requirements and deepen IT security controls.
Hyperproof wasn’t surprised to find in our 2023 IT Compliance Benchmark Report that 29% of security, compliance, and risk management professionals surveyed said that third-party risk is their number one source of stress, second only to cybersecurity risks. With this in mind, we’ll take a look at the top challenges of vendor risk assessments and how a third-party risk management software can go a long way toward bringing greater peace of mind
5 Essential Steps to Creating an Effective Third-Party Risk Management Program

Four common vendor risk assessment challenges
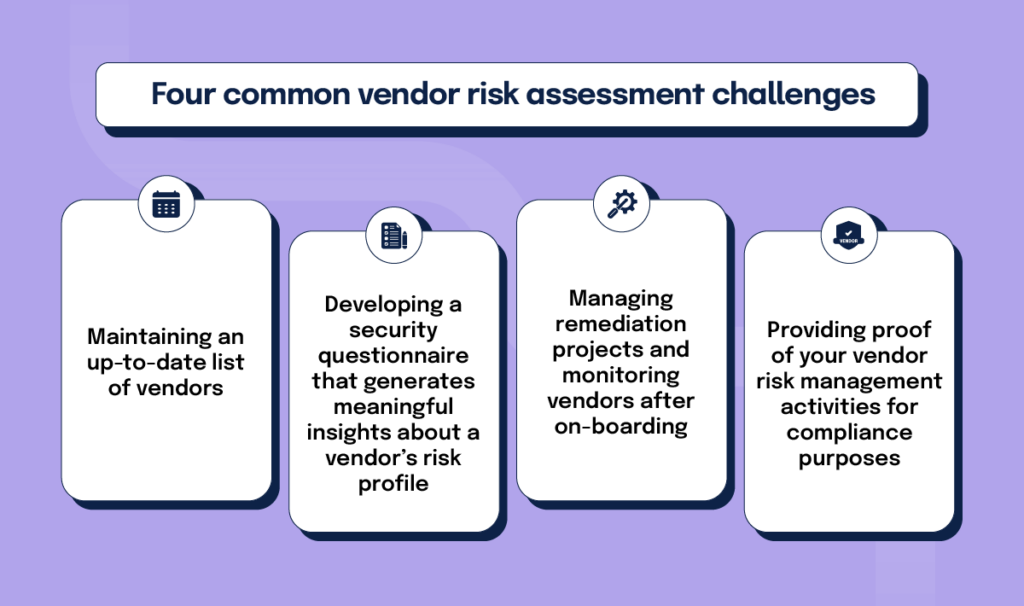
Organizations face a myriad of challenges when conducting vendor risk assessments. To start, gathering quality information from your vendors to understand their true risk profile takes a lot of time, which is often in short supply, and involves many manual and administrative tasks.
Challenge #1: Maintaining an up-to-date list of vendors
In Hyperproof’s 2021 IT compliance benchmark survey, we found that even seemingly simple tasks, such as maintaining an up-to-date list of all vendors and getting complete questionnaire responses back from vendors, are harder than they seem. 55% of all respondents said they struggle to get complete risk information on third-parties (and have trouble understanding the true risk profiles of their vendors). That trend has only compounded into 2023, as organizations now are relying on even more third parties than ever.
Many organizations aren’t using a central system to track all of their vendors, what each vendor is used for, who owns the vendor relationship, etc. When certain basic information is missing, it is incredibly difficult for risk, vendor management, and security professionals to even start to put together a meaningful vendor security questionnaire.
Challenge #2: Developing a security questionnaire that generates meaningful insights about a vendor’s risk profile
To develop questions that generate meaningful risk insights, the questionnaire designer (most likely a risk/security professional) needs to know who’s using the vendor system, what business processes are supported by the vendor system, what types of data is processed through the system, and how it connects with other systems and more. The risk manager also needs to be aware of the legal and compliance risks involved in each vendor relationship and who to work with at the vendor side to complete the questionnaire.
Once the security questionnaire designer has this context, they still need to put in the time to generate thoughtful questions to elicit accurate responses from the vendor.
Unfortunately, many IT risk and security professionals don’t have the luxury of time when developing effective questionnaires because they’re struggling with the basic mechanics of collecting vendor risk information. For example, in Hyperproof’s 2023 IT Compliance Benchmark Report, 39% of surveyed professionals said that they are using forms and/or questionnaires made in Microsoft Office or Google Suite to manage third-party risk. 38% reported using a ticketing or task management system and 23% reported using spreadsheets. Doing this work in ad-hoc tools like Google Forms, email threads, and spreadsheets is a manual and highly-tedious process, and, as a result, takes vast amounts of time to piece together the full picture of a vendor’s risk profile.
Challenge #3: Managing remediation projects and monitoring vendors after on-boarding
As if gathering relevant, timely vendor risk information isn’t tough enough on its own, post-assessment, risk and security professionals also need to ensure that remediations are happening on time and any changes to vendors’ risk level are discovered quickly. Since most organizations don’t have tools that automatically collect this data and alert the right individuals when there are issues with particular vendors, risk managers are struggling through these tasks manually using makeshift tech stacks.
In a staggering finding, 74% of respondents in our 2023 Benchmark Report have experienced (or are expecting) an audit finding that they cannot promptly resolve related to third-party risk Management. This is in large part due to companies not having the right tools and processes in place or the right risk data that would help them determine which of their vendors to prioritize.
Challenge #4: Providing proof of your vendor risk management activities for compliance purposes
As we mentioned earlier, many regulations and security frameworks have obligated companies to collect proof of their vendor risk management activities. If you haven’t been organizing your compliance artifacts and don’t have a system for evidence collection (e.g., vendor questionnaire responses, additional tickets created to track remediations, contracts detailing requirements for vendors to mitigate security risks) all along, it will be a big headache to track down all the documents you’ll need to show to auditors when audit day arrives.
How vendor risk management software can relieve the burden

Vendor risk management software (VRM) solutions enable vendor management, risk, security, and procurement professionals to effectively manage the assessment process for third parties and vendors over the life cycle of their relationships. They can also help you manage your compliance efforts.
These solutions can be used to collect and aggregate a range of risk data from vendors, third-parties, and external content sources to support regulatory vendor risk requirements, as well as internal policies governing the engagement of vendors.
Automate vendor risk assessment and remediation processes
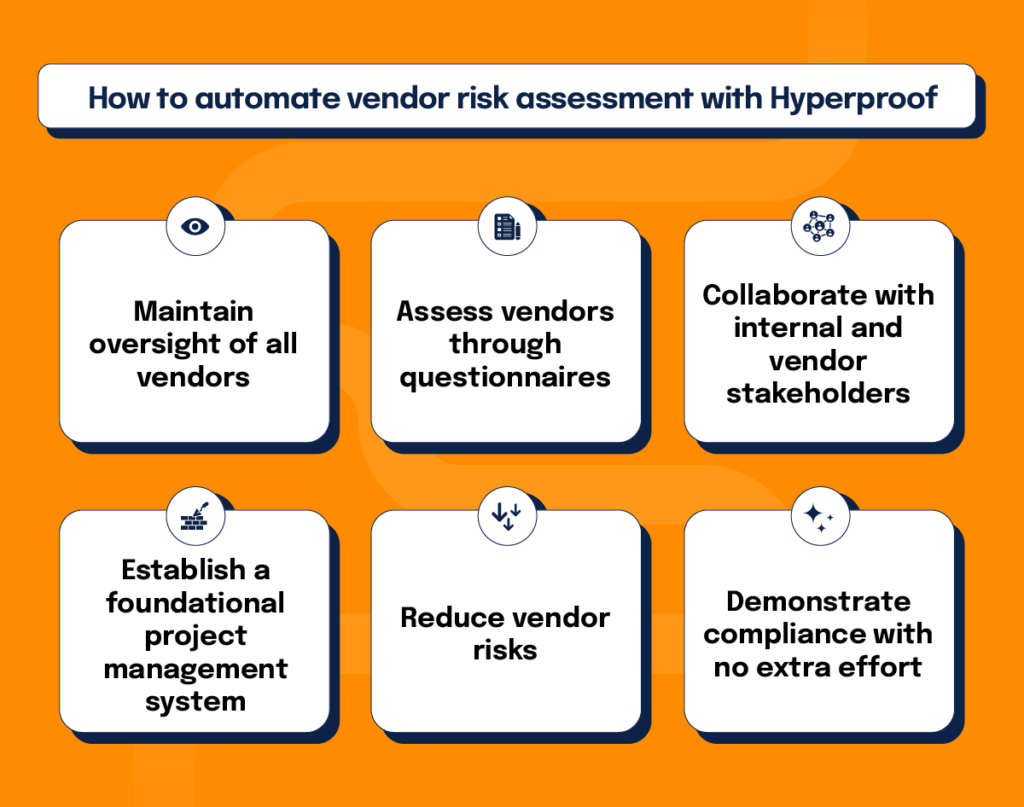
As you look to evolve your vendor risk management program to keep up with organizational growth, vendor risk management solutions like Hyperproof can provide the tools to automate risk assessment and remediation processes, provide risk and performance reporting, support better risk-based decisions, and make compliance work much more efficient. With Hyperproof you can:
Maintain oversight of all vendors
Hyperproof can be the home for all of your contracts, documents and vendors. You can use tools in Hyperproof to manage, assess, track, and report on your vendors, improving oversight of vendor relationships and their health.
Assess vendors through questionnaires
Hyperproof provides intuitive, built-in tools for risk assessment, vendor criticality, and risk scoring. You can utilize prebuilt or tailored questionnaires and send them to vendors to collect relevant information. All responses come back to a central location and are easily accessible for decision makers.
Collaborate with internal and vendor stakeholders
Once you’ve reviewed responses from a vendor’s security questionnaire and decided that you would like them to do something to give your team greater assurance, you can issue a vendor (or internal stakeholder) a task directly from Hyperproof. Tasks can be tailored by vendor criticality and questionnaire responses.
In addition to our built-in project management system, Hyperproof also integrates with many project management and communication tools (e.g., Jira, Slack, Microsoft Teams, Outlook, Gmail), allowing everyone to work in their preferred tool and for all the messages and tasks to be automatically synced into Hyperproof in the right place (e.g. directly tied to a vendor). Hyperproof also provides tools to automate tasks, alerts, and reminders — helping stakeholders stay on top of all their tasks.
Establish a foundational project management system
Having a great project and task management system for vendor risk management can make a big difference to security. After all, when someone responsible for testing the access controls and other security protocols of your software vendor forgets to do the work, the missed vulnerability can be exploited to launch an attack that may compromise your customers’ data and potentially cause your company millions in losses.
Reduce vendor risks
You can add controls to mitigate specific risks — and Hyperproof will show you residual risk on your vendors. Hyperproof comes with visual reports so you can see residual risk for each vendor and which vendors still need to complete questionnaires or respond to follow-up questions. All of this makes it easy to determine what vendors and tasks require attention so your team can take the right steps to reduce risk.
Demonstrate compliance with no extra effort
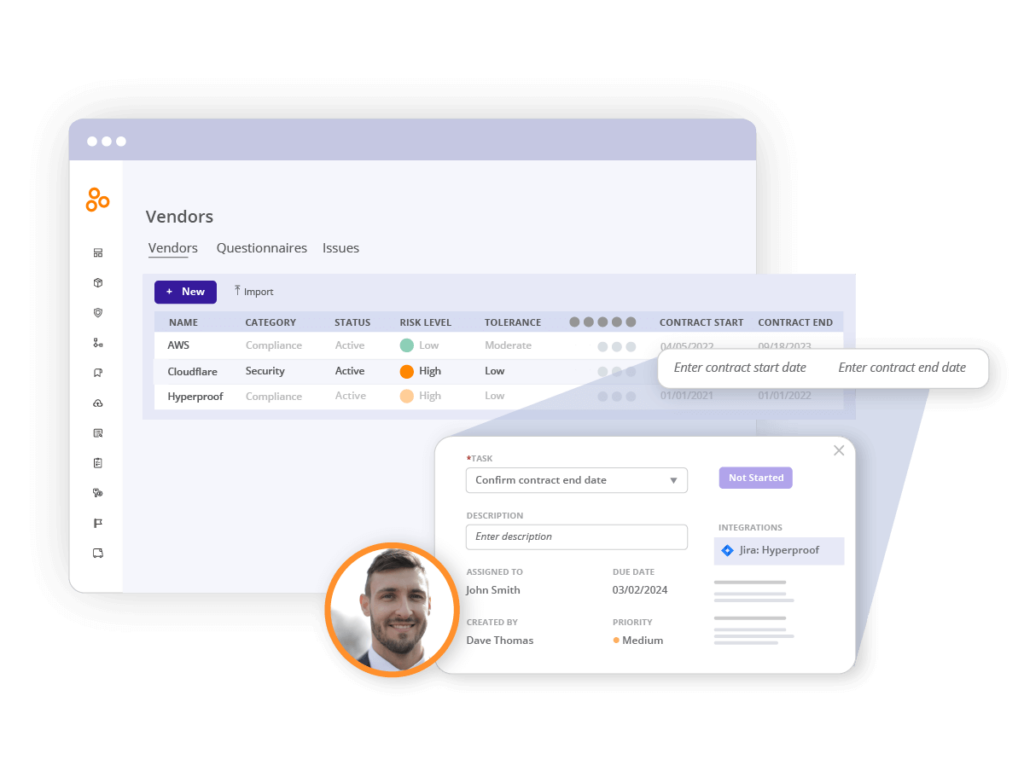
Within Hyperproof, all vendor management activities — including questionnaire responses and tasks around remediation projects — can be linked to risks, controls, and security standards or regulatory requirements you’ve already added within the software. Hyperproof provides dozens of built-in templates for security and data privacy standards such as SOC 2, CMMC, NIST CSF, ISO 27001, PCI DSS, etc. — and can serve as the central hub for managing all of your compliance efforts. Using Hyperproof to manage vendor risk and ensure that your security program aligns to industry security standards, you’ll be able to retrieve proof of vendor due diligence activities within seconds for an audit.
Hyperproof Is the Solution to Your Vendor Risk Assessment Challenges
In a landscape where vendor risk assessment challenges are a pressing concern, Hyperproof enables organizations to navigate these complexities confidently and efficiently. Our platform offers a comprehensive approach to vendor risk management, ensuring your operations remain secure, compliant, and resilient in evolving vendor landscapes.
Take control of your vendor risk management with Hyperproof and safeguard your operations for a secure, compliant, and resilient future – sign up for a personalized demo.
Ready to find a better vendor risk management solution?
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












