Build a Strong Information Security Policy: Template & Examples

Every organization needs to have security measures and policies in place to safeguard its data. One of the best and most important measures you can take to protect your data (and that of your customers) is simply to have a robust information security policy.
Of course, that idea sounds simple enough. In practice, however, it’s anything but. So, let’s unpack exactly what an information security policy should include and how you can develop one.
What is an information security policy?
An information security policy brings together all of the policies, procedures, and technology that protect your company’s data into one overall document.
According to Infosec Institute, the main purposes of an information security policy are the following:
- To establish a general approach to information security.
- To detect and prevent the compromise of information security, such as misuse of data, networks, computer systems, and applications.
- To protect the reputation of the company by upholding its ethical and legal responsibilities.
- To observe the rights of customers; such as by providing effective mechanisms for responding to complaints and queries concerning real or perceived non-compliance with the policy.
Information security is a central theme of many IT-focused compliance frameworks. If you’re doing business with large enterprises, healthcare customers, or government agencies, compliance is a necessity.
Standards such as SOC 2, HIPAA, and FEDRAMP are often required by regulation or contract; and even if they aren’t, embracing those standards is just good business sense. A detailed information security plan will put you much closer to compliance with the frameworks that make you a viable business partner for many organizations.
Are you taking an organized approach to managing cyber risks? See how you can get organized with our webinar.
On-demand webinar: Taking a Disciplined Approach to Manage IT Risks ›
Popular compliance frameworks with information security requirements
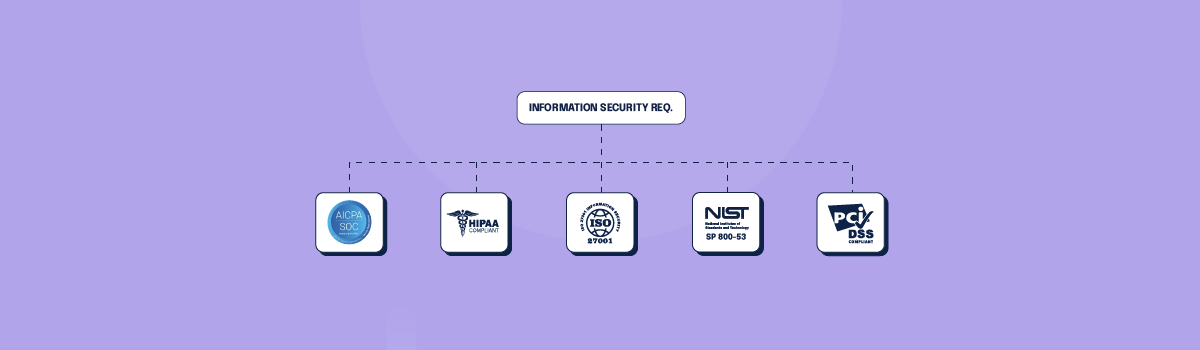
Numerous compliance frameworks include information security requirements that might help your company if you embraced them. Here are some of the most well-known.
SOC 2
SOC 2 is a compliance framework typically used by technology providers and other vendors to document their cybersecurity posture. Developed by the American Institute of Certified Public Accountants, SOC 2 requires you to develop and follow strict information security requirements to maintain the integrity of your customer’s data and ensure it is protected. The standard isn’t required by law, but large enterprise customers will routinely want to see a SOC 2 audit report before engaging with a vendor.
HIPAA
HIPAA is a federal law to protect personal health information. Under HIPAA, a “covered entity” (any organization providing treatment, payment, or operations in healthcare) or its business associates who have access to patient information must follow a strict set of rules. HIPAA breaches can have serious consequences, including fines, lawsuits, or even criminal charges.
ISO 27001
ISO 27001 is a security standard that lays out specific requirements for an organization’s information security management system (ISMS). This security standard is noteworthy because it doesn’t just cover electronic information; it includes guidelines for protecting information such as intellectual property and trade secrets. It isn’t required by law, but it is widely considered necessary for any company handling sensitive information.
NIST SP 800-53
NIST SP 800-53 is a collection of hundreds of specific measures that can be used to protect an organization’s operations and data and individuals’ privacy. It provides a catalog of controls that U.S. federal agencies can use to maintain the integrity, confidentiality, and security of federal information systems.
The standard was originally designed for use by government agencies, and today is widely used by businesses in other industries to help them improve their information security systems. In many cases, following NIST guidelines and recommendations will help organizations ensure compliance with other data protection regulations and standards because many frameworks use NIST as the reference framework.
PCI DSS
PCI DSS, shorthand for Payment Card Industry Data Security Standard, is a framework that helps businesses that accept, process, store, or transmit credit card data and keep that data secure. It applies to any company that handles credit card data or cardholder information. A business must comply with one of four PCI DSS compliance levels, based on that company’s transaction volume and whether or not it stores cardholder data.
Related: Conducting an Information Security Risk Assessment: a Primer
What should be in an information security policy?

An information security policy can be tough to build from scratch; it needs to be robust and to secure your organization from all ends. It should cover all software, hardware, physical parameters, human resources, information, and access control. It also needs to be flexible, with room for revision and updating.
Most importantly, the policy needs to be practical and enforceable. Wishful thinking won’t help you when you’re developing an information security policy. You need to work with the major stakeholders to develop a policy that works for your company and the employees who will be responsible for carrying out the policy.
Here are a few of the most important information security policies, and guidelines for tailoring them for your organization.
Acceptable use policy
This policy outlines the acceptable use of computer equipment and the internet at your organization. Improper use of the internet or computers opens your company up to risks such as virus attacks, compromised network systems, and services, and legal issues, so it’s important to have in writing what is and isn’t acceptable use.
An acceptable use policy should outline what employees are responsible for protecting the company’s equipment, such as locking their computers when they’re away from their desks or safeguarding tablets or other electronic devices that might contain sensitive information. It should also outline the company’s rights and what activities are not prohibited on the company’s equipment and network.
Acceptable use policies are a best practice for HIPAA compliance because exposing a healthcare company’s system to viruses or data breaches can mean allowing access to personal and sensitive health information.
Clean desk policy
A clean desk policy focuses on protecting physical assets and information. Ideally, this policy will ensure that all sensitive and confidential materials are locked away or otherwise secured when not in use or an employee leaves the desk.
This policy should establish the minimum requirements for maintaining a clean desk, such as where sensitive information about employees, intellectual property, customers, and vendors can be stored and accessed. It should also cover issues such as what kinds of materials should be shredded or thrown away, whether passwords need to be used to retrieve documents from a printer, and what information or property has to be secured with a physical lock.
A clean desk policy is a common and important part of any information security policy. It is also ISO 27001-compliant and will help your business pass a certification audit.
Data breach response policy
This is also known as an incident response plan. A data breach response policy establishes the goals and vision for how your organization will respond to a data breach. This plan will help to mitigate the risks of being a victim of a cyber attack because it will detail how your organization plans to protect data assets throughout the incident response process.
This policy should define whom it covers and when it comes into effect, including the definition of a breach, staff roles and responsibilities, standards and metrics, reporting, remediation, and feedback mechanisms.
Disaster recovery plan policy
This policy is different from a data breach response plan because it is a general contingency plan for what to do during a disaster or any event that causes an extended service delay. This policy should describe the process of recovering systems, applications, and data during or after any type of disaster that causes a major outage. The plan should be updated on an annual basis.
The contingency plan should cover these elements:
- Emergency outreach. Explicitly list who needs to be contacted, when they need to be contacted, and how you will contact them?
- Succession. Describe the flow of responsibility when normal staff aren’t available to perform their duties.
- Data classification. Detail all the data stored on all systems, its criticality, and its confidentiality.
- Criticality of service list. List all the services provided and their order of importance.
- Data backup and restoration. Detail which data is backed up, where, and how often. Also, explain how the data can be recovered.
- Equipment replacement. Describe which infrastructure services are necessary to resume providing services to customers.
- Public communications. Document who will own the external PR function and provide guidelines on what information can and should be shared.
It’s important that the management team set aside time to test the disaster recovery plan. During these tests(also known as tabletop exercises), the goal is to identify issues that may not be obvious in the planning phase that could cause the plan to fail. This way, the team can adjust the plan before a disaster takes place.
Email policy
The misuse of email can pose many threats to your company’s security, whether it’s employees using email to distribute confidential information or inadvertently exposing your network to a virus. It’s important for all employees, contractors, and agents operating on behalf of your company to understand appropriate email use and to have policies and procedures laid out for archiving, flagging, and reviewing emails when necessary.
This policy needs to outline the appropriate use of company email addresses and cover topics such as prohibited communications, data security standards for attachments, rules regarding email retention, and whether the company is monitoring emails.
This policy should also be clearly laid out for your employees so that they understand their responsibility to use their email addresses and the company’s responsibility to ensure emails are being used properly. This email policy isn’t about creating a “gotcha” policy to catch employees misusing their email, but to avoid a situation where employees are misusing email because they don’t understand what is and isn’t allowed.
End-user encryption key protection policy
Certain documents and communications inside your company or distributed to your end-users may need to be encrypted for security purposes. Have a policy to protect those encryption keys so they aren’t disclosed or fraudulently used.
This policy should outline all the requirements for protecting encryption keys and list out the specific operational and technical controls in place to keep them safe. This includes steps such as tamper-resistant hardware, backup procedures, and what to do if an encryption key is lost, stolen, or fraudulently used.
Password protection policy
Your employees likely have numerous passwords they need to remember and use on a daily basis, and your business should have clear, explicit standards for creating strong passwords for their computers, email accounts, electronic devices, and any point of access to your data or network.
This policy must also outline what employees can or can’t do with their passwords. It might seem obvious that they shouldn’t put their passwords in an email or share them with colleagues, but you shouldn’t assume that this is common knowledge for everyone. Give employees all the information they need to create strong passwords and keep them safe to minimize the risk of data breaches.
Finally, this policy should outline what your developers and IT staff need to do to ensure that your company’s applications or websites are following security precautions to keep user passwords safe.
Security response plan policy
A security response plan lays out what each team or business unit needs to do in the event of a security incident, such as a data breach. According to the SANS Institute, this policy should define, “a product description, contact information, escalation paths, expected service level agreements (SLA), severity and impact classification, and mitigation/remediation timelines.”
The security response plan policy helps all the different teams integrate their efforts so that any security incident can be mitigated as quickly as possible. While each department might have its own response plans, the policy details how they will coordinate with each other to ensure a quick and thorough response to a security incident.
Information security policy template
A number of reputable organizations provide information security policy templates. For instance, the SANS Institute collaborated with information security leaders and experts to develop a set of security policy templates for your use. You can get them from the SANS website.
Further, if you’re working with a security or compliance advisory firm, they may be able to provide you with security policy templates and specific guidance on how to create policies that make sense for your business (and ensure you stay compliant with your legal obligations).
Keep in mind that templates are the starting point for developing your own policies; they must be customized to fit your organization’s processes and needs.
Information security policy examples

The National Institute for Standards and Technology (NIST) Cybersecurity Framework offers a great outline for drafting policies for a comprehensive cyber security program.
The five functions system
The “Five Functions” system covers five pillars for a successful and holistic cyber security program. These functions are:
1. Identify
The organization should have an understanding of the cybersecurity risks it faces so it can prioritize its efforts.
2. Protect
Put appropriate safeguards in place to protect data assets and limit or contain the impact of a potential cybersecurity event. This includes educating and empowering staff members within the organization to be aware of risks, establishing procedures that focus on protecting network security and assets, and potentially using cyber liability insurance to protect a company financially when a cybercriminal bypasses the protections that are in place.
3. Detect
Outline the activities that assist in discovering the occurrence of a cyber attack and enable timely response to the event. To diagnose a cyber attack quickly and efficiently, companies should implement data classification, asset management, and risk management protocols that alert them when data appears to be compromised.
4. Respond
Document the appropriate actions that should be taken following the detection of cybersecurity threats. A company’s response should include proper and thorough communication with staff, shareholders, partners, and customers as well as with law enforcement and legal counsel as needed.
5. Recover
Determine how an organization can recover and restore any capabilities or services that were impaired due to a cyber attack.
Almost every security standard must include a requirement for some type of incident response plan because even the most robust information security plans and compliance programs can still fall victim to a data breach.
For more details on what needs to be in your cybersecurity incident response plan, check out this article: How to Create a Cybersecurity Incident Response Plan. Fortunately, the Center for Internet Security and the Multi-State Information Sharing & Analysis Center has provided a security policy template guide that provides correlations between the security activities recommended in the Cybersecurity Framework and applicable policy and standard templates. You can download a copy for free here.
Incorporate security awareness training

With all of these policies and programs in place, the final piece of the puzzle is to ensure that your employees are trained on and understand the information security policy.
Training should start on each employee’s first day, and you should continually provide opportunities for them to revisit the policies and refresh their memory. It’s also important to find ways to ensure the training is sticking and that employees aren’t just skimming through a policy and signing a document. Interactive training or testing employees, when they’ve completed their training, will make it more likely that they will pay attention and retain information about your policies.
You should also look for ways to give your employees reminders about your policies or provide them with updates on new or changing policies. Monthly all-staff meetings and team meetings are great opportunities to review policies with employees and show them that management believes these policies are important. Making information security a part of your culture will make it that much more likely that your employees will take those policies seriously and take steps to secure data.
Technology allows easy implementation of security policies and procedures

While it’s critical to ensure that your employees are trained on and follow your information security policy, you can implement technology that will help fill the gaps of human error, too.
Antivirus software
Antivirus solutions are broad, and depending on your company’s size and industry, your needs will be unique. But at the very least, antivirus software should be able to scan your employee’s computers for malicious files and vulnerabilities. Some antivirus programs can also monitor web and email traffic, which can be helpful if employees visit sites that make their computers vulnerable.
Firewalls
Firewalls are a basic but vitally important security measure. They filter incoming and outgoing data and intercept malware and viruses before they make their way to a machine or into your network.
Resource monitoring
If there is an issue with an electronic resource, you want to know as soon as possible so that you can address it. Resource monitoring software can not only help you keep an eye on your electronic resources; it can also keep logs of events and users who have interacted with those resources so that you can go back and view the events leading up to a security issue.
Vulnerability tracking
Software programs such as Nmap and OpenVAS can pinpoint vulnerabilities in your systems and list them out for you, allowing your IT team to either shore up the vulnerabilities or monitor them to ensure that there aren’t any security events.
Password management software
To ensure your employees aren’t writing their passwords down or depending on their browser to save their passwords, consider implementing password management software. Remembering different passwords for different services isn’t easy; many people go for the path of least resistance and choose the same password for multiple systems. Providing password management software can help employees keep their passwords secure and avoid security incidents because of careless password protection.
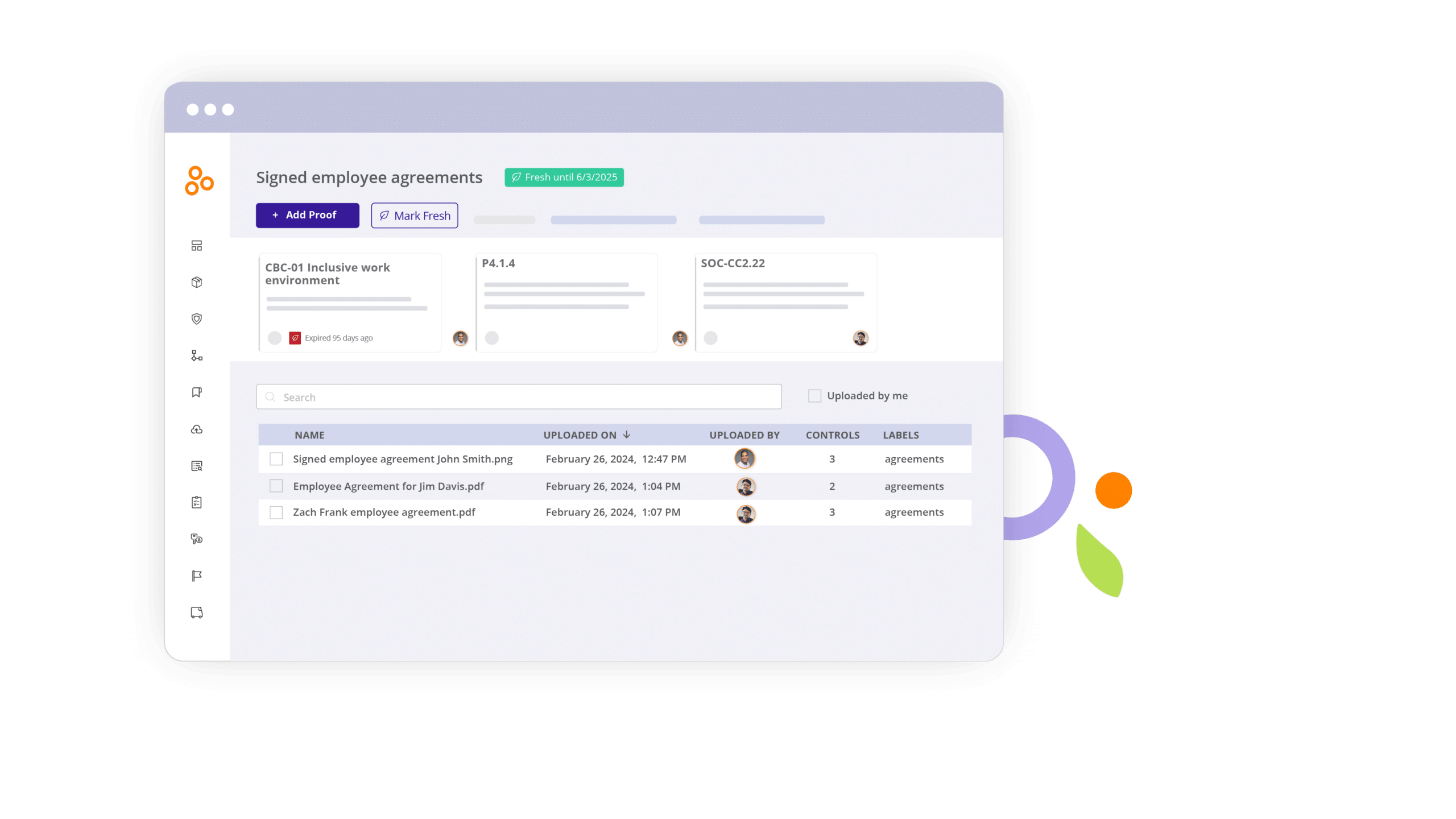
Compliance software
Dedicated compliance operations software can help you track all of your compliance activities, monitor your internal controls to manage cyber risk, and ensure that all controls are working consistently as they were designed — so your security team can catch control failures early and remediate vulnerabilities before you experience a data breach.
Compliance operations software such as Hyperproof also provides a secure, central place to keep track of your information security policy, data breach incident response policy, and other evidence files that you’ll need to produce when regulators or auditors come knocking after a security incident. Hyperproof also helps your organization quickly implement SOC 2, ISO 27001, GDPR, and other security/privacy frameworks, and removes a significant amount of administrative overhead from compliance audits.
Elevate your information security policy with Hyperproof
An effective policy isn’t just about compliance; it’s a roadmap to resilient, secure operations, giving you peace of mind in an era of growing digital threats.
Don’t let policy creation become a bottleneck in your security strategy. With Hyperproof, the process will be smoother and more efficient. Our solution streamlines policy management, giving you complete control over every aspect of your information security policy.
Ready to experience the difference? Request a demo of Hyperproof today and see how we can transform your information security policy from a static document into a dynamic asset for your business.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?