Secure Software Development: Best Practices, Frameworks, and Resources

Just how important is building secure software today? Well, given the never-ending string of cyberattacks that succeed by taking advantage of software vulnerabilities, it’s become essential for organizations to purchase and use only the safest software. In other words, security for software is no longer optional or “nice to have” – it’s a core requirement for protecting your customers and your business.
Consider some examples of software vulnerabilities gone wrong, of which we have no shortage:
- Solarwinds, the IT services provider hacked by Russian operatives in 2020. Hundreds of businesses and government agencies then downloaded that contaminated software, giving Russia exposure to the highest levels of Corporate America and the U.S. government.
- MOVEit, a file transfer software product widely used by corporate organizations. In 2023 Russian hackers discovered and exploited a vulnerability in MOVEit to pilfer the data of organizations such as the Big 4 accounting firms, UCLA, Siemens Energy, and more.
- Barracuda Networks suffered a hack into its email software technology in 2023. Hackers believed to be from China used the vulnerability to target hundreds of Barracuda customers around the world.
Not only can customers suffer grave damage from vulnerable software; regulators increasingly hold software developers accountable for poor development practices. The Securities and Exchange Commission and the Federal Trade Commission, for example, have both sanctioned software firms for making rosy promises about their software development practices when the truth was nothing of the sort.
This article will discuss best practices and frameworks for building secure software and how to identify and respond to vulnerabilities early in the development process when it costs less and is more effective. In addition, we’ll highlight expert-developed resources you can leverage for your own security software development effort.
What is secure software development?

Secure software development is a methodology (often associated with DevSecOps) for creating software that incorporates security for software into every phase of the software development life cycle (SDLC). Security is baked into the code from inception rather than addressed after testing reveals critical product flaws. Security becomes part of the planning phase, incorporated long before a single line of code is written.
Traditionally, security is viewed as an impediment to innovation and creativity by developers that creates delays in getting the product to market. This thinking hurts a business’s bottom line, as it’s six times more costly to fix a bug during implementation and 15 times more expensive during testing than to fix the same bug during design.
Most importantly, how happy will customers be with the cool new features of an application if the product is laden with vulnerabilities for hackers to exploit? Security deserves a preeminent position in the software engineering process today, and organizations must do so to find themselves able to compete.
So, how can security become part of the SDLC from the beginning?
First, testing early and often. A secure software development philosophy stresses employing static and dynamic security testing throughout the development process. Second, development teams should also document software security requirements alongside the functional requirements. Finally, conducting risk analysis during design can be beneficial in helping you identify potential environmental threats.
Organizations looking to offer secure software must lay the foundation for success by effectively preparing their people, processes, and technology for this challenge. Proper preparation takes the form of a well-constructed secure software development policy, which every organization committed to building secure software needs.
What is a secure software development policy?

A secure software development policy (sometimes called a secure system development policy) is a set of guidelines detailing the practices and procedures an organization should follow to decrease the risk of vulnerabilities during software development. In addition, the policy should provide detailed instructions on viewing, assessing, and demonstrating security through each phase of the SDLC, including risk management approaches.
Secure software development policy must establish rules for your people. Team members must clearly understand their duties, receive thorough training, and undergo strict employee screening. Instituting segregation of duties ensures no one person has total control or knowledge of a project. Testing protocols need to assess all employee work in order to ensure acceptable standards.
Secure software development policy must also discuss the necessary processes for protecting software. One of the most critical — separation of development, testing, and operational environments — breeds autonomy while preventing test bias and unauthorized code changes. Access control, another essential process, assures that employees can only access job-relevant data. Finally, version control is a helpful process to track all sources and times of code alteration.
The first tech-related action step in a secure software development policy should create the governing rules for programming languages and coding. Coding languages can contain numerous vulnerabilities, so developers must be well-schooled on the hardening strategies that minimize attack routes. A secure software development policy should also provide instructions on establishing secure repositories to manage and store code.
Not only is a secure software development policy recommended – it’s also mandatory in certain instances. For example, organizations adhering to SOC 2® or ISO 27001 standards for cybersecurity are expected to maintain a documented system development policy that defines how software is designed, built, tested, and released securely. For example, organizations adhering to SOC 2® or ISO 27001 standards for cybersecurity must have a secure development policy. Your team can build your policy from scratch or use resources like the ISO 27001 template guide.
What should your organization keep in mind when creating a secure software development policy? Dave Brennan, Vice President of Engineering at Hyperproof, weighs in with some advice:
“You need to take a lot of different approaches. Start by understanding what’s happening in the industry and what the risks are. Next, train your engineering team to be aware of common threats and vulnerabilities, the necessary processes to follow, and the tools to run. Finally, use checklists to ensure your policies and procedures are up-to-date and monitor these monthly. It’s not just one approach that’s going to keep your software secure — you’re going to need all of them.”
Dave Brennan, Vice President of Engineering at Hyperproof
Using a secure software development framework to ensure consistency and best practices
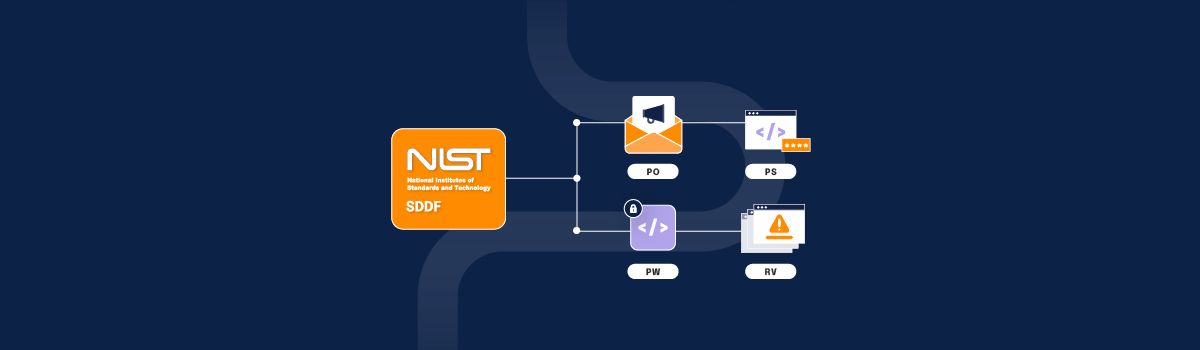
Many organizations benefit from aligning their practices with a well-established framework, such as NIST’s Secure Software Development Framework (SSDF). Organizations such as OWASP and SAFEcode have created a collection of foundational secure software development resources that discuss software security in detail, supplying the necessary guidance to reduce the number, lessen the impact, and prevent future vulnerabilities in software releases.
Let’s take a moment to examine the NIST framework recommended secure software development processes, which NIST organizes into four stages:
- Prepare the Organization (PO): Ensure that an organization’s people, processes, and technology are prepared to perform secure software development at the organization level and, in some cases, for each individual project.
- Protect the software (PS): Protect all components of the software from tampering and unauthorized access.
- Produce Well-secured Software (PW): Software that has minimal vulnerabilities in its releases
- Respond to Vulnerabilities (RV): Identify vulnerabilities in software releases and respond appropriately to address these vulnerabilities and prevent similar vulnerabilities from occurring in the future.
Each practice is defined with the following elements:
- Practice: A brief statement of the practice, along with a unique identifier and an explanation of what the practice is and why it is beneficial.
- Task: An individual action (or actions) needed to accomplish a practice.
- Implementation Example: A given scenario that could be used to demonstrate a practice.
- Reference: An established secure development practice document and its mappings to a particular task.
The following sections provide a more in-depth explanation of NIST’s four secure software development processes.
Prepare the organization: practices, tasks, and examples
This process begins by clearly defining both internal (e.g., Policies, risk management strategies) and external (e.g., Laws, regulations) software development security requirements for your organization. SSDF roles are assigned, and teams prepare with role-specific training. Supporting tools are engaged to improve speed and efficiency across the SDLC, then security checks are installed to ensure software meets organizational standards.
Tasks include identifying, communicating, and maintaining all security requirements over time. Training regimes are prepared, management support is engaged, and tools are selected. Finally, benchmarks are defined to document the achievement of set security standards.
Examples include:
- Defining specifics, like coding practices and architecture requirements for developers
- Reviewing and updating security requirements at least yearly, especially after incidents
- Assigning SSDF-related roles training plans, then installing periodic reviews and preparing to update on any role changes over time
- Defining toolchain categories, specifying tools for each, and incorporating automation for toolchain operation and management
- Creating an audit trail of secure development-related actions
- Identifying key performance indicators, using an automated toolchain to gather feedback, and reviewing and documenting all security check evidence to support defined standards
Protect the software: practices, tasks, and examples

Protecting the code and ensuring software integrity until it reaches the end customer is paramount. This process focuses on safeguarding code from unauthorized access and tampering, verifying the software’s integrity, and protecting the software after release.
A primary task is storing code based on the least-privilege principle to ensure only authorized access. Also, a copy of every release with listed components and integrity verification information is provided to every customer.
Examples include:
- Storing code in secure, restricted-access repositories
- Using version control to track all code changes
- Posting cryptographic hashes for released software and using only trusted certificate authorities for code signing
Produce well-secured software: practices, tasks, examples
As you can imagine, this process includes many steps and involves numerous actors and practices. First, the software is designed and reviewed to align with identified security requirements. Next, third parties are thoroughly evaluated for compliance with these requirements. Then, developers use security best practices to write code, configuring the build process around boosting product security. All code is then reviewed, analyzed, and tested, employing manual and automated means to uncover vulnerabilities and ensure compliance. Finally, the software is configured with secure default settings for protection out-of-the-box, and trusted components are often reused in production.
Specific tasks include creating a trusted component list, using threat modeling to assess risk, studying external security requirements, communicating standards to third parties while verifying their compliance, using secure coding best practices while employing top industry tools, and examining code from all angles through review or analysis. Final tasks include designing and performing vulnerability tests, documenting the results, and fixing all discovered issues.
Another important task, which some may consider above and beyond, is setting secure defaults, ensuring they align with other platform security features, then explaining their importance to administrators.
Examples include:
- Training a development team in secure building best practices and risk assessment techniques
- Studying vulnerability reports on previous releases while reviewing current designs to ensure all potential risks and security requirements are addressed
- Including security requirements in third-party contracts while creating policies to manage third-party risks
- Avoiding all unsafe building functions and only developing in environments that mandate safe coding practices
- Using only current, validated versions of compiler build tools
- Employing a combination of peer reviews, dynamic/static analysis testing, and penetration testing to detect software vulnerabilities, then documenting results and lessons learned
- Creating an organizational repository of trusted building components
- Verifying the setting of approved security default configurations and documenting proper usage to administrators
Respond to vulnerabilities: practices, tasks, examples

Finding vulnerabilities is only part of a security professional’s job — the other critical component is remediation. This final process focuses on correcting current vulnerabilities and gathering data for future prevention. Once identified and confirmed, vulnerabilities must be expediently prioritized and fixed. Speed is essential in reducing the window of opportunity threat actors have to launch attacks. Additionally, it’s beneficial to analyze a vulnerability’s cause once mitigated to help prevent future occurrences.
Tasks in this final process include gathering customer information and diligently reviewing/testing code for any undiscovered flaws, preparing a team, plan, and processes for rapid vulnerability response and mitigation, creating and implementing a remediation plan for each identified vulnerability, and determining the root causes to construct a knowledge base for future prevention.
In addition, root causes should be analyzed over time to identify patterns. These patterns then can be spotted and remediated in other software. Finally, the entire SDLC can be periodically updated to eliminate similar issues in future releases.
Examples include:
- Creating a vulnerability reporting and response program
- Employing automation to monitor vulnerability data and conduct automated code analysis
- Gauging the impact of and resources required to fix each vulnerability while prioritizing remediation
- Identifying and documenting root causes of vulnerabilities while advancing the toolchain for automatic future detection and implementing suitable adjustments to the SSDF
Top 10 software security best practices

In today’s constantly expanding threat environment, developing secure software is undoubtedly challenging, but it couldn’t be more critical as more and more successful software-linked attacks grab headlines. So, we compiled a list of ten secure software development best practices to help you strengthen security for software you build and keep your organization from becoming a software cyberattack statistic. So, here they are — our top ten software security development best practices:
1. Think security from the beginning
Before creating a single line of code, begin planning how to integrate security into every phase of the SDLC. Engage the power of automation in testing and monitoring vulnerabilities from day one. Security needs to be baked into your culture and code, and there’s no better place to start than in the earliest development phase.
2. Create a secure software development policy
This will provide a guideline for preparing your people, processes, and technology to perform secure software development. This formal policy supplies specific instructions for approaching and instrumenting security in each phase of the SDLC. In addition, it provides the governing rules and defines roles to help your people, processes, and tools minimize the vulnerability risk in software production.
3. Employ a secure software development framework
A proven framework like NIST SSDF will add structure and consistency to your team’s effort to adhere to secure software best practices. Frameworks can help answer the “What do we do next?” question and benefit all new software developers.
4. Design software with best practices to meet security requirements
Clearly define all security requirements, then train developers to write code in alignment with these parameters using only secure coding practices. Ensure all your third-party vendors are aware of your security requirements and demonstrate compliance, as they can provide an easy pathway for an attack.
5. Protect code integrity
Keep all code in secure repositories, allowing only authorized access to prevent tampering. Strictly regulate all contact with the code, monitor changes, and closely oversee the code signing process to preserve integrity.
6. Review and test code early and often
Breakaway from the traditional development pattern of testing code toward the end of the SDLC. Instead, use both developer reviews and automated testing to continually examine code for flaws. Catching vulnerabilities early in the life cycle saves money and time while preventing developer frustration later on.
7. Be prepared to mitigate vulnerabilities quickly
Vulnerabilities are a fact of life in software development. It’s not if they occur, but when, so be ready with a team, plan, and processes in place to address incidents in real-time. Remember, the faster you can identify and respond to vulnerabilities the better, shortening the window of opportunity for exploitation.
8. Configure secure default settings
Many customers remain vulnerable simply for lack of knowledge of their new software’s functions. This added customer service touch ensures the consumer will be protected in the early stages of adoption.
9. Use checklists
There are many moving parts to track and monitor during secure software development. Help your team by using action checklists at periodic intervals such as weekly or monthly meetings to ensure all necessary security policies and procedures are current and functional.
10. Remain agile and active
Wise software developers study vulnerabilities — learning their root causes, spotting patterns, preventing repeat occurrences, and updating their SDLC with improved knowledge. They also watch trends and stay up-to-date on best practices. Dave Brennan offers some parting advice here, “The big picture is knowing and staying current on the industry and best practices. The space is always evolving; security best practice approaches aren’t standing still. So no matter what you’re doing with security, it’s critical to look ahead to see what’s coming, keep learning, and identify better ways to secure your software development process.”
FAQs: system development policy and security for software
What is a system development policy?
A system development policy is a formal document that defines how your organization designs, develops, tests, and releases software or systems securely. It sets expectations for coding standards, access control, separation of environments, code review, and security testing so that secure practices are followed consistently across the SDLC.
Why is “security for software” so important today?
As more critical business processes depend on software and more attacks exploit application-layer vulnerabilities, strong security for software is essential. It reduces the likelihood of breaches, supports compliance with frameworks like SOC 2 and ISO 27001, and protects customer trust by ensuring your applications are resilient against common threats.
How Hyperproof supports information security compliance initiatives

One of the most challenging parts of maintaining information security is that people often don’t follow through and complete their assigned tasks. Unfortunately, these human errors are most often at the heart of security problems. As organizations grow their technology footprint and evolve their business processes, security and compliance professionals need platforms that give them the ability to define security requirements, document and assign security tasks, monitor whether people perform tasks on time, and maintain accountability.
Hyperproof is built as a project management and accountability system for security and compliance leaders. In Hyperproof, it’s easy to implement best-in-class security and privacy frameworks, such as the NIST SSDF, the NIST Cybersecurity Framework, ISO 27001, or SOC 2, and distribute security tasks to engineers, IT professionals, and other system administrators while testing and monitoring the effectiveness of controls over time.
With Hyperproof, it’s easy to see who’s responsible for performing certain security/compliance tasks and if those tasks are completed. In addition, Hyperproof can be configured to automatically collect proof that security review tasks have been performed (and configurations are correct) from different cloud-based systems and developer tools. This allows security and compliance managers to focus on strategic tasks, such as evaluating the effectiveness of specific controls, instead of gathering evidence manually. To learn more about Hyperproof, sign up for a personal demo.
Gain the visibility, efficiency, and consistency you need to stay on top of all your security assurance and compliance work.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?