Guide
You’ve Done SOC 2®, What’s Next?
Using SOC 2® as the Stepping Stone to Achieve Other IT Security Certifications and Standards

Introduction
These days, a SOC 2® report is considered a must-have for any organization that manages customer data. Getting a SOC 2® type 2 report signals that an organization demonstrates a baseline level of maturity when it comes to safeguarding data and ensuring privacy, data confidentiality, availability, and processing integrity.
Chances are, you decided to get a SOC 2® report because several of your prospective customers told you they must see this report before they’re able to do business with your firm.
Launching an IT compliance effort to achieve a SOC 2® type 2 report is no easy feat. It’s often the first major compliance milestone young organizations achieve.
Now that this big milestone is behind you, you’re trying to figure out where to go from here. You’re wondering:
The good news is that you’ve already done quite a bit of work for SOC 2® that can be leveraged to comply with a variety of other IT compliance standards and frameworks.
In this ebook, we will answer the questions above and help you develop a strategic blueprint for your IT compliance program aligned to your business goals. We’ll also give you a playbook to scale up and mature your security assurance function in the most efficient and cost-effective way, leveraging the work you’ve already done for SOC 2®.
What security certifications and frameworks should you consider adopting next?
No single cybersecurity framework or standard tis inherently better than another. What you work on next should be based on your understanding of your market, the needs of your customers, regulatory requirements relevant to your organization, and the risks your business needs to manage. Key factors to consider include:
1. Business goals and customer requirements
How do you want to grow as a business? What types of customers do you want to serve in the next one to three years? Your target customers will have specific IT compliance requirements for their vendors depending on their industry, region, and the regulatory environment they’re in. For instance, here are some specific standards, certifications, and frameworks to consider:
Want to do business in Europe? Consider ISO/IEC 27000 series. When an organization is ISO 27001 certified, it means that the organization’s information security management system (ISMS) conforms to the ISO 27001 standard. ISO 27001 is seen as a gold standard in information security by organizations around the world. You’ll also need to comply with Europe’s GDPR in order to earn the trust of your European customers.
Want to do business with healthcare providers or health insurers? You need to be HIPAA compliant and may need to sign a Business Associate agreement to ensure that your organization will appropriately safeguard protected health information.
Want to service the federal government? You need to prepare for the Cybersecurity Maturity Model Certification (CMMC) if you’d like to bid for contracts from the Department of Defense. If you want to sell a SaaS product, you’ll need to achieve a FedRAMP authorization.
Is your company planning to go public in the next 2-3 years? If so, you’ll need to prepare to comply with the Sarbanes-Oxley Act (SOX).
Achieving certain certifications and authorizations can be quite expensive and time-consuming. You’ll need to think carefully about whether it makes sense for your organization to invest the resources required to achieve compliance vs. the market opportunity opened up by having certain certifications and authorizations.
Want to know which data protection regulations and standards your business needs to adhere to? Take our Data Protection Compliance Quiz.
2. Security needs
At this time, cyber attacks methods evolve quickly and they’re becoming increasingly sophisticated. Global cybercrime costs businesses 16.4 billion every day, with a ransom attack occurring every eleven seconds.
Chances are you have some security gaps at the moment. For instance, how would you score your organization’s capabilities in security assessment, access control, incident management and response, and configuration management? In addition to protecting your networks, systems, and data, your risk management plan should also cover your vendors. When over half of all data breaches are due to third-party vulnerabilities, you need to have a sound approach to vendor risk management.
Given your current security state and the risk landscape you’re operating in, it may be time to bring more rigor and discipline into your security and compliance program. At this time, many companies needing help in creating a rigorous approach to managing cyber risk have turned to voluntary security frameworks such as the NIST Cybersecurity Framework (CSF).
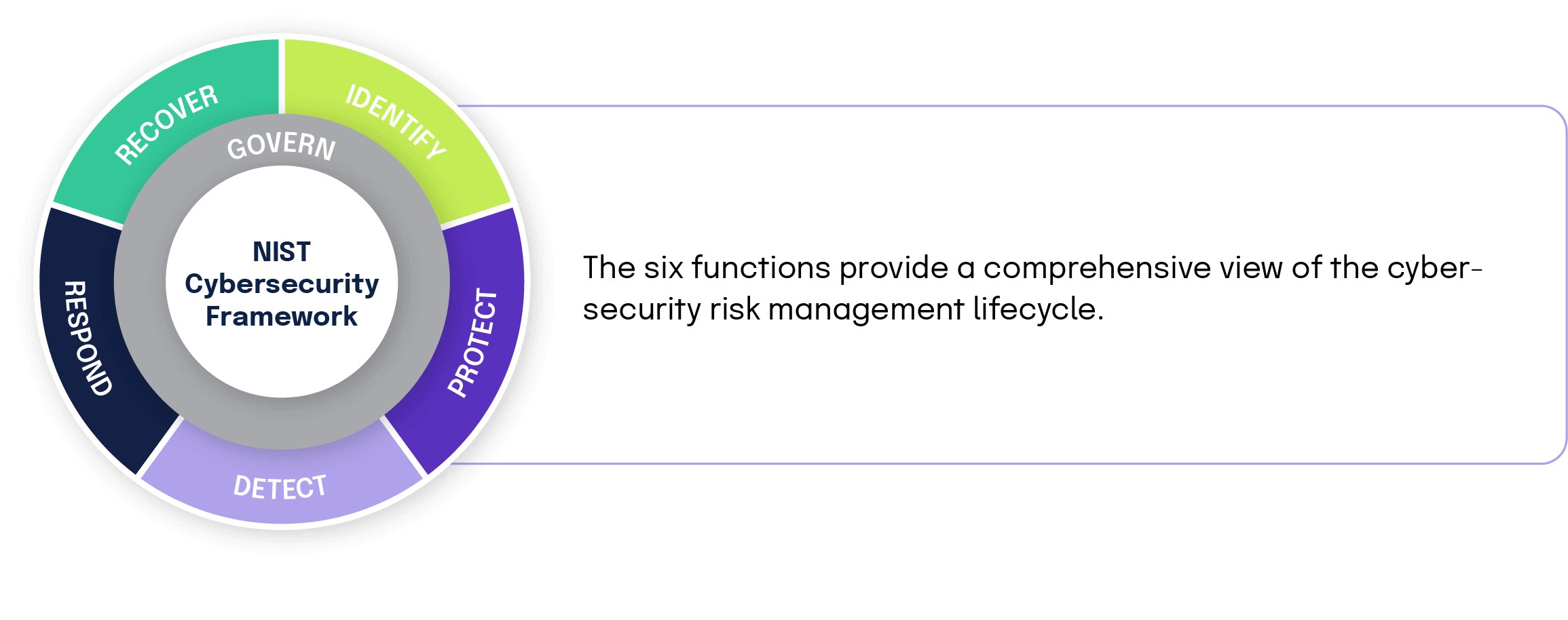
Developed by the National Institute of Standards and Technology, the NIST Cybersecurity Framework is a list of standards, guidelines, and practices designed to help organizations better manage and reduce cyber risk. It rests on industry best practices gathered from various documents and standards like ISO 27001 and COBIT 5. Security teams can use this framework to assess risk levels (both acceptable and current), align on risk tolerance objectives, set improved security priorities, and determine a budget to mitigate cyber threats.
The NIST CSF is outcome-driven but flexible on how each organization can achieve security objectives. This flexibility allows all companies, from the smallest and newest to the largest and most established to benefit from this guiding framework. By aligning your internal controls to the suggested security activities in NIST CSF, you’ll be in a position to meet the requirements of other industry-specific or regional cybersecurity standards and regulations easier.
Overview of NIST CSF
The NIST framework for implementing cybersecurity is composed of three components:
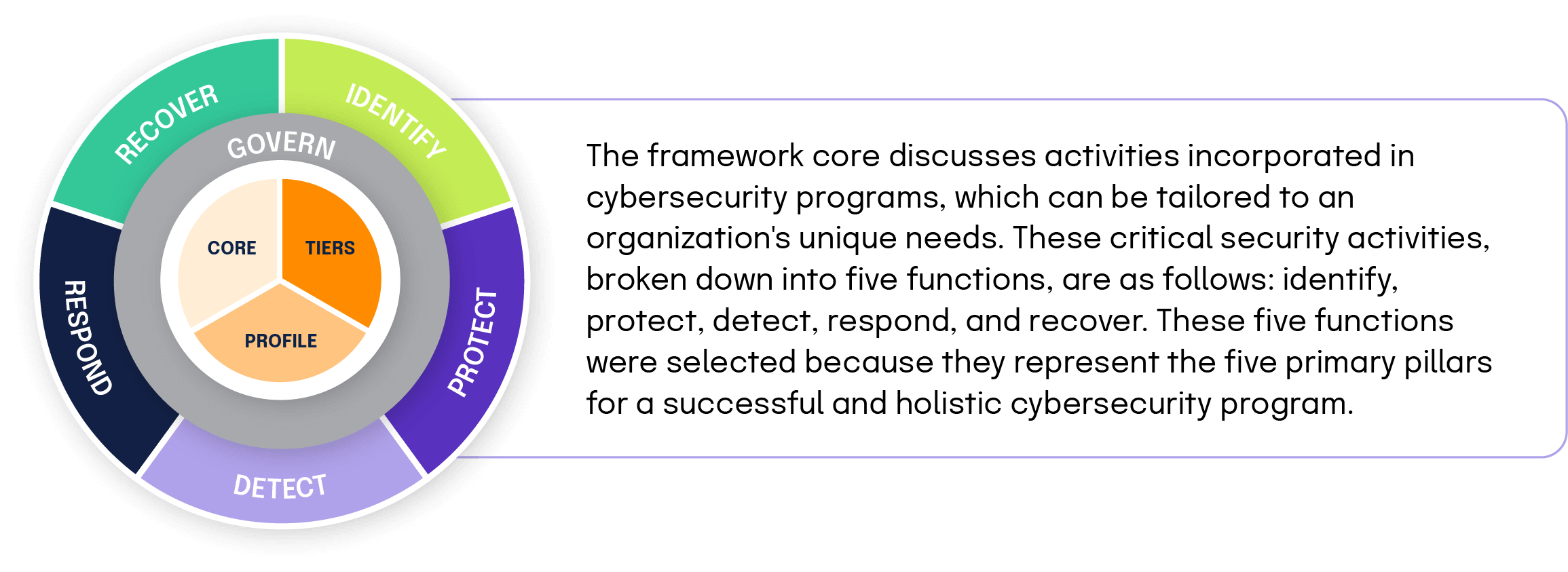
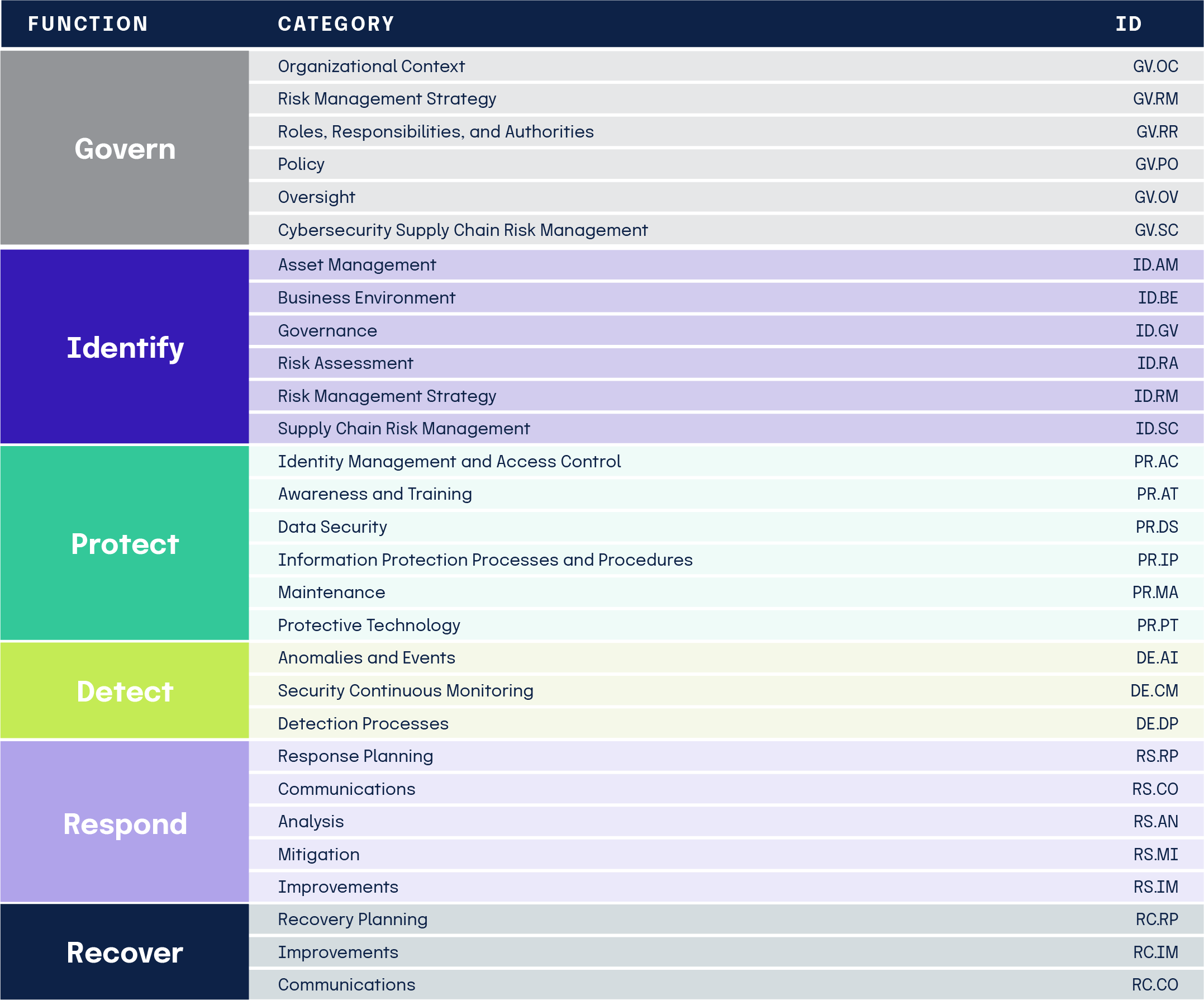
The categories were designed to cover the breadth of cybersecurity objectives for an organization. Subcategories (not shown here) are the deepest level in the CORE. There are 108 Subcategories, which are outcome-driven statements that provide considerations for creating or improving a cybersecurity program.
Examples of Subcategories include
- External information systems are cataloged
- Data-at-rest is protected, and
- Notifications from intrusion detection systems are investigated.
Framework implementation tiers provide context on cybersecurity risk management and guides organizations on an appropriate level of rigor for cybersecurity programs.
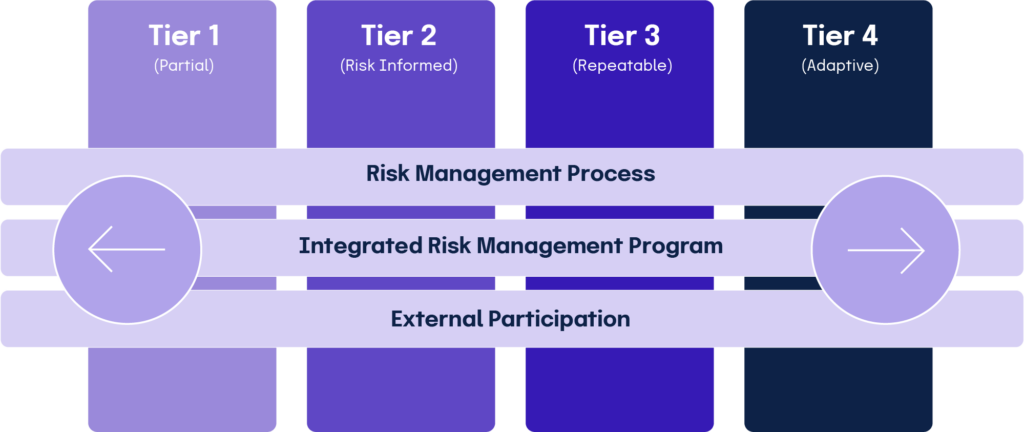
Framework Profiles compare an organization’s objectives, risk appetite, and resources against the framework core’s desired outcomes. Comparing current profiles with target profiles helps teams identify opportunities for improvement.
Guide
How to Use NIST’s Cybersecurity Framework to Foster a Culture of Security
States are starting to offer liability protection in data breach lawsuits for organizations that have adopted NIST CSF
Adopting the NIST CSF may give you an additional benefit: liability protection when your organization falls victim to ransomware and other cyber attacks.
Given the high frequency of ransomware and nation-state actors targeting US critical infrastructure, federal lawmakers are considering liability protection for organizations that experience malicious intrusions. However, lawmakers have said that if organizations want this protection, they need to step up their game to implement better cybersecurity practices.
During a Senate Intelligence Committee hearing in February 2021, Chairman Mark Warner (D-VA) said, “While I am very open to some level of liability protection, I’m not interested in a liability protection that excuses the kind of sloppy behavior, for example, that took place in Equifax, where the didn’t even do basic hygiene.”
In addition to federal level activities, a number of states (Ohio, Utah, and Nevada) have moved forward with their own liability exemption measures that seek to boost cybersecurity practices. These states have enacted laws that incentivize the adoption of robust and thorough industry-leading cybersecurity frameworks and recommendations such as the NIST Cybersecurity Framework or the Center for Internet Security’s (CIS) Critical Security Controls by making them requirements for obtaining liability protection.
Moving beyond SOC 2®: challenges you’ll likely face
Managing an IT compliance program that encompasses multiple standards come with a set of challenges you need to be aware of, such as:
Coordinating people and tasks
As you seek to expand your IT compliance program, you’ll likely need to involve an additional set of people in your organization in this effort. They’ll need to understand the value of this undertaking and their respective roles in the initiative.
Keeping everyone on the same page and moving in the same direction will become more difficult. Communication will likely increase, and you’ll need a way to manage communications and collaboration effectively.
Mapping out overlapping areas between multiple standards and frameworks
Many security compliance frameworks have overlapping requirements. How can you approach work in a way that minimizes duplicate effort when testing controls and collecting evidence across meeting multiple frameworks’ requirements? To manage things efficiently, you’ll need to map out how requirements are related and what common controls you can use to satisfy multiple requirements. This is really hard to do in a spreadsheet.
More ongoing work to manage
To align your security program closer with guidelines within a new standard or framework, you will likely create new controls related to governance, identity management and access, supply chain management, etc. Developing new controls may involve creating new policies, procedures or processes, launching training or implementing new technical solutions. With a greater number of controls in place, ensuring that all controls are suitable to your current environment and their operating effectiveness will become more challenging.
Having to spend more money on audits
If you’re looking to achieve a certification for certain standards (e.g., ISO 27001 or CMMC), you’ll need to find a qualified auditor, schedule the audit, and pay for it. Certain audits and certification processes can be quite costly, even in the six figures. However, depending on the frameworks you choose, it may be possible to work with an auditor who’s able to audit against multiple standards at once to drive down costs and the time involved.
Why you shouldn’t use spreadsheets for your compliance efforts
Although you can use spreadsheets and other ad-hoc tools like Sharepoint, Dropbox, Jira, and email to manage your IT compliance efforts, these tools make it difficult to stay organized and maintain solid processes over time. Here are a few reasons why using spreadsheets can be limiting:
A playbook to maturing and scaling up your security assurance function
Although scaling up your security compliance program may seem daunting, the process becomes quite manageable if you prioritize standing up good processes, ironing out workflows, and leverage a dedicated compliance operations software to facilitate the work. In this section, we’ll show you steps to take to streamline work, standardize processes and workflows, and automate routine tasks. You’ll be on your way to scaling up your IT compliance program in no time!
1. Move your SOC 2® work into a compliance operations platform

When you use a compliance operations (or “ComOps”) platform like Hyperproof to manage your IT compliance effort centrally, you’ll be able to leverage the work already done for SOC 2® to comply with additional frameworks and standards more easily.
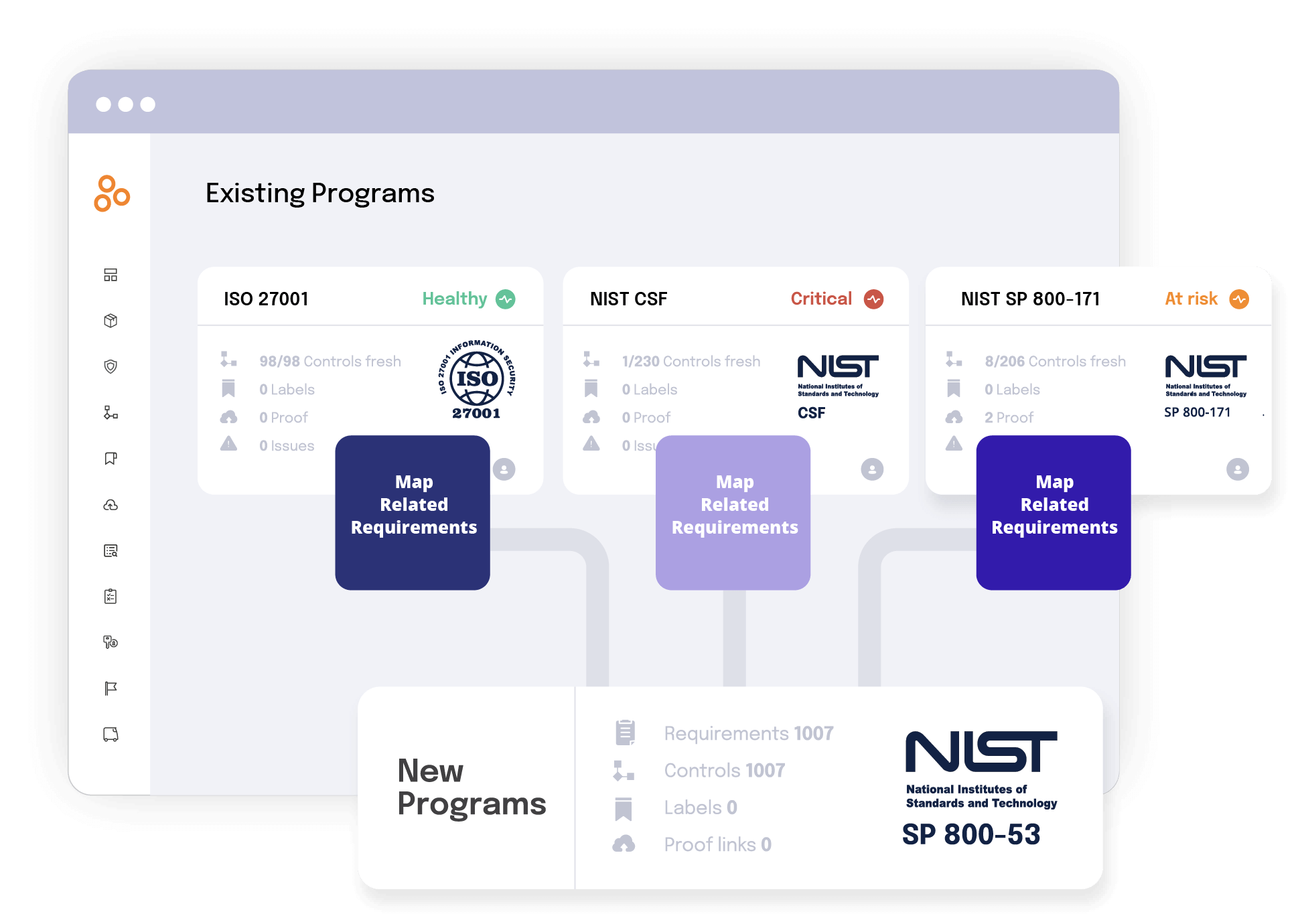
By using a compliance operations platform, you can stand up multiple cybersecurity and data privacy programs and frameworks, see the program requirements (or guidelines) within a compliance framework in a clear way, and map internal controls against the program’s requirements (or guidelines).
Controls can be mapped to multiple requirements in a compliance operations platform. Once controls are mapped, compliance professionals are able to manage a smaller set of controls and collect the same evidence once and re-use it across multiple frameworks.
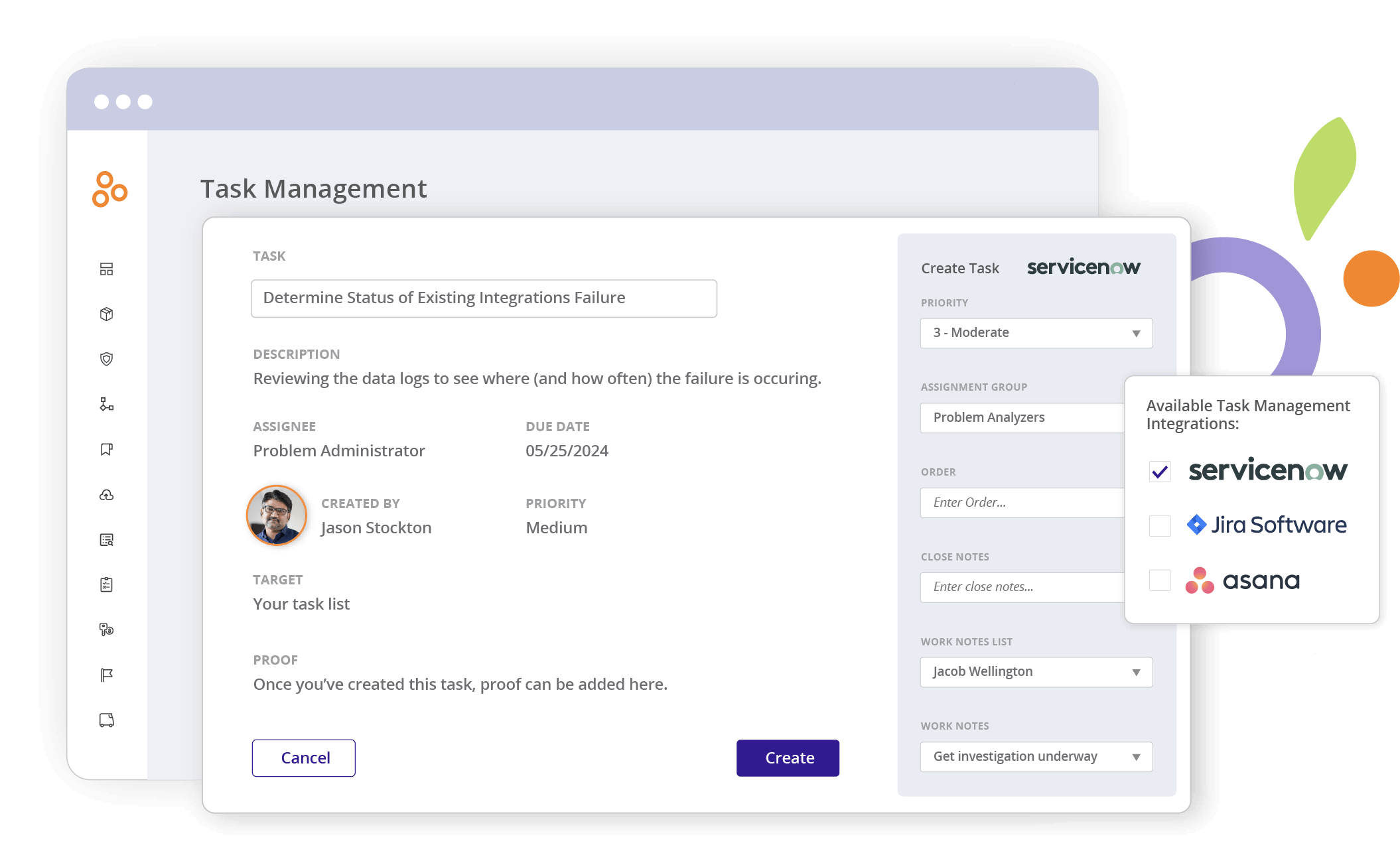
Messages and tasks can be initiated within the platform to people within and outside of your organization (e.g., compliance consultants) — and their responses are tracked centrally. To facilitate seamless collaboration between those in and outside the IT compliance function, Hyperproof integrates natively with multiple communication and project management systems. Messages can be sent out in Hyperproof by compliance professionals and responded to from Slack or Microsoft Teams, or vice versa.
A compliance pro can create tasks for others to complete in Hyperproof, the assignee of the task can complete it in a project management system they’re already familiar with, like Jira. Any change to a task made in Jira are immediately reflected in Hyperproof, making project management easy.
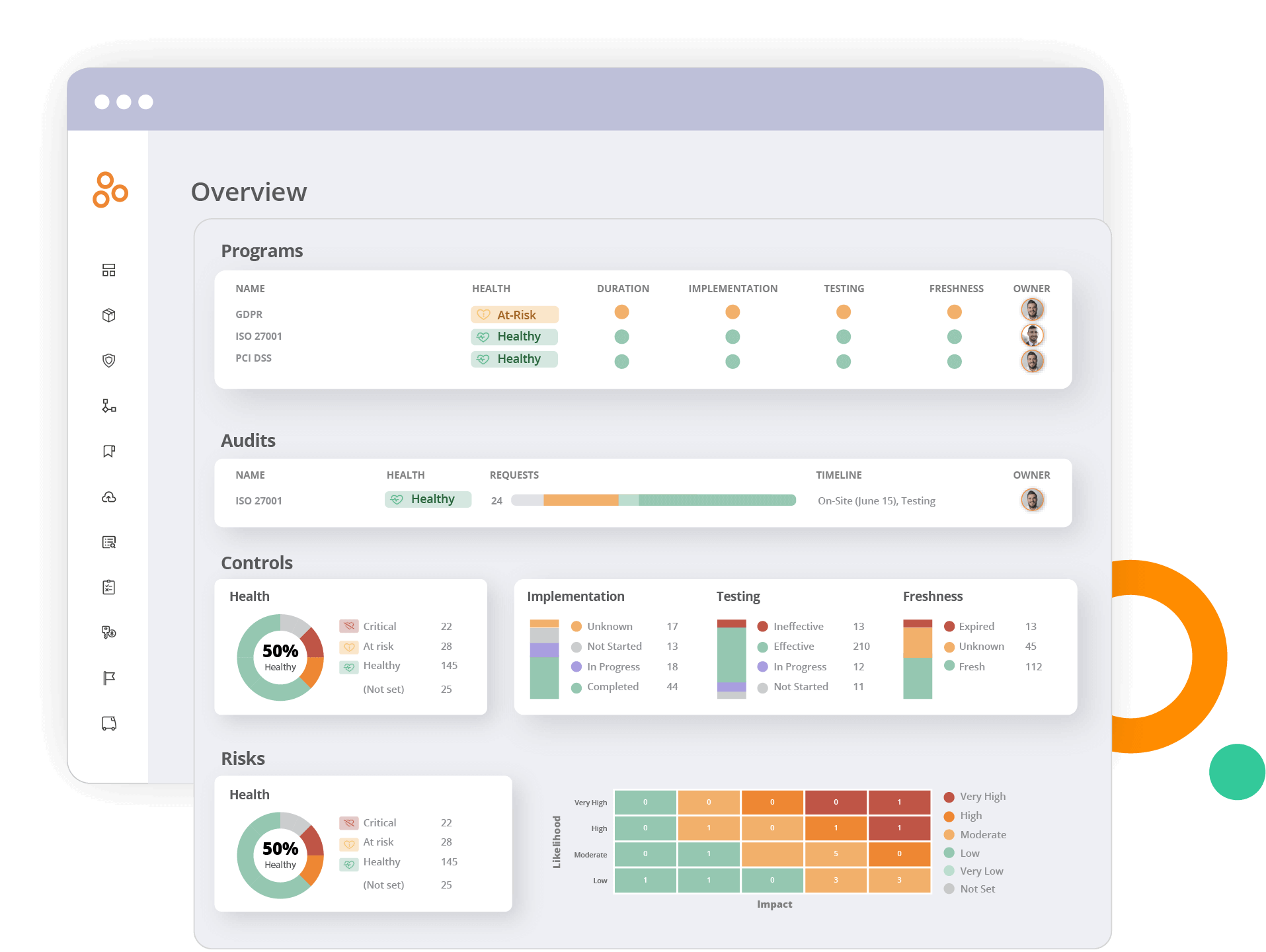
Hyperproof also comes with dashboards and drill-down reports to give compliance professionals actionable insights about their security posture and compliance gaps.
You can have your SOC 2® program stood up in Hyperproof within a couple of hours. This process is straightforward and involves the following steps:
2. Identify SOC 2® controls you can leverage to meet requirements within additional compliance programs, frameworks and standards
Once you’ve stood up a SOC 2® program in Hyperproof, it is time to do a control mapping exercise: figuring out which existing controls can be reused to satisfy requirements within a new compliance standard or framework. With a compliance operations platform, this exercise is straightforward and requires just a few steps:
How does Hyperproof know which controls to suggest? Hyperproof has built-in crosswalks based on the Secure Controls Framework (CSF), a comprehensive catalog of controls that enables companies to design, build, and maintain secure processes, systems, and applications. The framework currently incorporates over 850 controls, is baselined across more than 150 regulations and standards, and is updated every few months.
By streamlining your controls set and leveraging common controls to meet the requirements of multiple IT security frameworks, you’ve created a more efficient approach for managing your IT compliance projects. Now, you can collect evidence for a smaller set of controls and save hours or weeks worth of work. You can focus your energy on more strategic tasks, such as ensuring that those responsible for executing security tasks are doing their part.
3. Shift into a controls and operational mindset

Compliance violations and data breaches are often caused by human error — when someone in your company didn’t do something you know is necessary to safeguard your systems, data, and network.
For example, say an organization has a policy to conduct daily and weekly backups. A policy may dictate a test of those backups twice a year. However, the person responsible for the test forgets — because the task happens just twice a year. When disaster strikes, the backup fails. It was people who failed to test the backups. It was people who failed to ask when the backups were last tested.
By using a compliance operations platform like Hyperproof, you can set up automated tasks, alerts, and reminders to help everyone remember to do their part in security — so control deficiencies, security incidents, and business disruptions due to human errors can be avoided. When someone forgets to do something, it’s easy to see that in Hyperproof, allowing a compliance professional to follow up with that individual and resolve the issue promptly.
Download the PDF