Guide
What is GRC?
The ultimate guide to governance, risk, and compliance

Introduction
In an increasingly complex and regulated business environment, Governance, Risk, and Compliance (GRC) have become essential components of an organization’s strategy. This guide details the critical aspects of GRC including what to look for in a GRC tool, how to assess your organization’s GRC maturity, and how Hyperproof’s platform can help organizations achieve their GRC goals.
What is GRC?
Governance, risk, and compliance (GRC) is a comprehensive strategy that integrates three critical areas into a unified approach, to ensure that an organization operates ethically, manages risks effectively, and complies with applicable laws and regulations.
The OCEG coined the acronym “GRC” as a shorthand reference to “the critical capabilities that must work together to achieve “Principled Performance” — capabilities that “integrate the governance, management, and assurance of performance, risk and compliance activities.”

OCEG’s definition asserts that “all roles must work together to achieve Principled Performance. This includes the work done by departments like governance and strategy, risk management, internal audit, compliance management, HR, IT, and security.”
Regardless of the type or size of organization you lead or work for, we can all agree there is a universal set of positive outcomes that all organizations want to achieve. High-performing organizations share a common set of traits with one another:
In short, high-performing organizations are able to reliably achieve their business objectives while managing uncertainty and acting with integrity.
Why do organizations need GRC?
The OCEG says developing strong GRC capabilities can help organizations navigate and thrive in today’s challenging and complex business environment. After all, businesses today must grapple with a variety of factors:

The OCEG emphasizes the importance of shared responsibility and integration in GRC activities. Their research found that when risk management, compliance, corporate social responsibility programs, and departments are siloed, they are often ineffective and create issues like high costs, lack of visibility into risks, inability to address risks, and difficulty measuring risk-adjusted performance.
On the other hand, when the different functions of an organization are working as a cohesive team, sharing information, using standard processes and a shared technology stack, organizations can ensure that “the right people get the right information at the right times; that the right objectives are established, and that the right actions and controls are put in place to address uncertainty and act with integrity.” This integrated way of approaching GRC leads to reduced costs, reduced duplication of activities, and reduced impact on operations. It helps an organization achieve a more complete view of its risks and improves the organization’s ability to gather information more quickly and achieve greater ability to repeat processes consistently.
The importance of GRC for enterprises
The OCEG model of GRC was borne from the challenges and experiences of large organizations. The complexity and scale of operations in large organizations make GRC not just a necessity but a critical component of business strategy for enterprises. Here’s a deeper look into why GRC is vital for enterprises:
1. Regulatory compliance at scale
Large enterprises operate across multiple jurisdictions, each with its own set of regulatory requirements. These regulations can vary significantly, making compliance a challenging and resource-intensive task. A robust GRC strategy ensures that the enterprise can track and adhere to all relevant regulations, minimizing the risk of non-compliance and avoiding costly penalties.
For example, global financial institutions must comply with regulations such as GDPR in Europe, CCPA in California, and the Dodd-Frank Act in the United States. Each of these regulations has unique requirements, and failure to comply with any of them can result in significant financial and reputational damage.
2. Risk management in complex environments
Enterprises face a broad spectrum of risks, ranging from financial and operational risks to cybersecurity threats and reputational risks. Managing these risks effectively requires a comprehensive risk management strategy that is integrated into the organization’s overall GRC framework.
A mature GRC program allows enterprises to identify, assess, and mitigate risks in a structured and consistent manner. For example, a multinational corporation may face supply chain disruptions, geopolitical risks, and currency fluctuations, all of which need to be managed within a unified GRC framework.
3. Governance across global operations
As enterprises expand globally, ensuring consistent governance across all business units becomes increasingly challenging. Different regions may have different cultural norms, legal requirements, and operational practices, making it difficult to enforce a uniform governance structure.
A robust GRC framework enables enterprises to establish and maintain governance practices that are consistent, transparent, and aligned with corporate objectives. This includes setting up governance policies that can be applied across different regions while allowing for local adaptations where necessary.
4. Strategic alignment and operational efficiency
GRC is not just about compliance and risk management; it’s also about ensuring that the organization’s operations are aligned with its strategic goals. By integrating GRC into the organization’s overall strategy, enterprises can ensure that every decision, process, and activity supports the achievement of their long-term objectives.
Moreover, a unified GRC framework can lead to significant operational efficiencies. By consolidating governance, risk management, and compliance activities, enterprises can eliminate redundancies, reduce costs, and improve overall performance.
5. Building stakeholder confidence
Stakeholders, including investors, customers, and regulators, demand transparency and accountability. A mature GRC program helps enterprises demonstrate their commitment to ethical conduct, risk management, and regulatory compliance, thereby building trust and confidence.
How Hyperproof makes GRC easier for enterprises
1. Automated compliance management
Hyperproof automates the process of managing compliance obligations, reducing the burden on your team and ensuring that all regulatory requirements are met. This includes features like automated audit trails, compliance checklists, and real-time alerts for regulatory changes.
2. Risk management and mitigation
The Hyperproof platform provides tools for identifying, assessing, and mitigating risks across the organization. This includes risk assessment templates, risk scoring models, and integrated risk reporting, allowing enterprises to manage risks proactively.
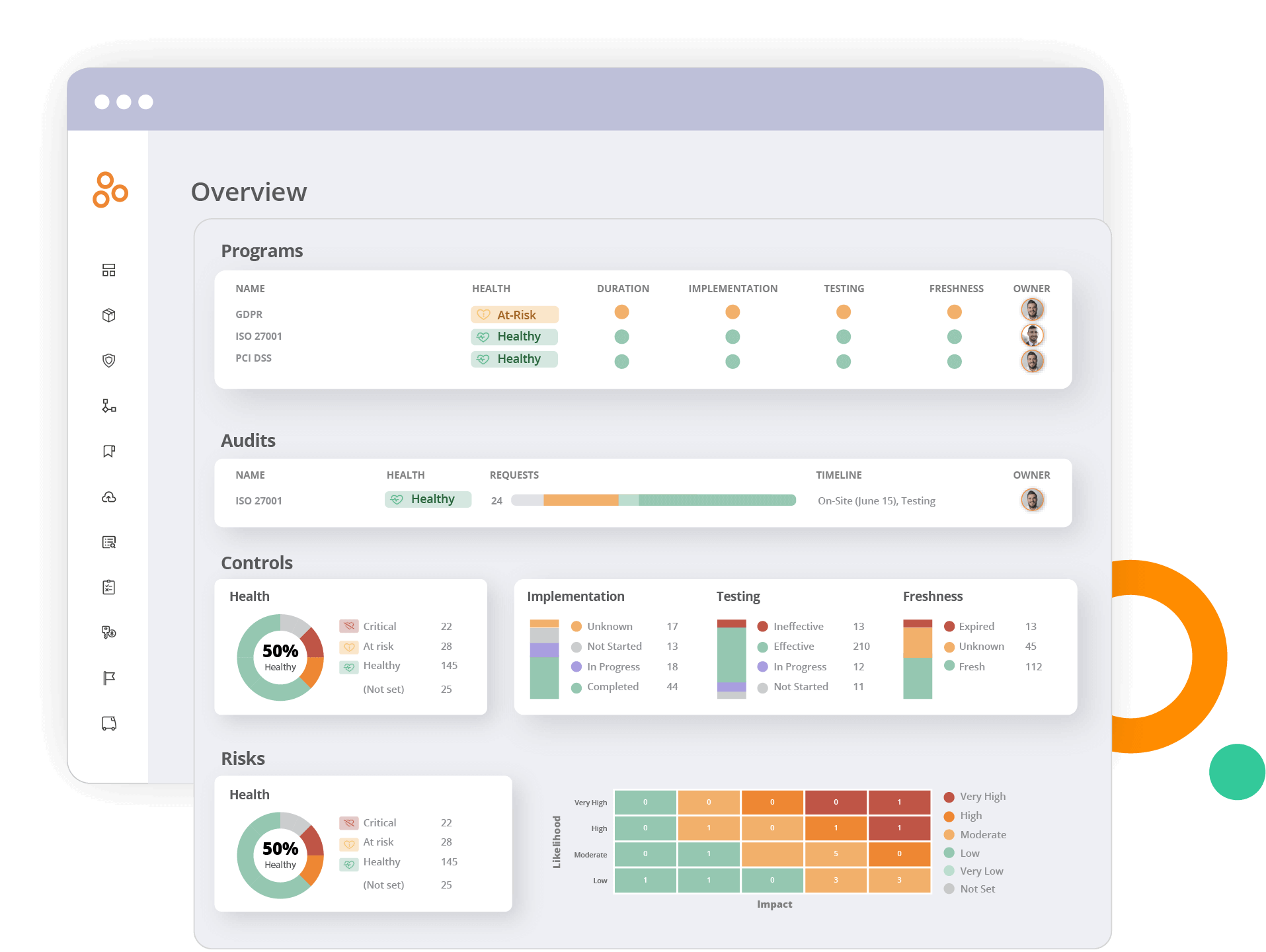
3. Real-time monitoring and reporting
Hyperproof provides real-time monitoring and reporting capabilities, providing enterprises with a comprehensive view of their GRC activities. This includes dashboards that display key metrics, customizable reports, and automated notifications for any deviations from established governance, risk, and compliance standards.
4. Scalable and flexible solutions
As enterprises grow and evolve, their GRC needs change. Hyperproof’s platform is designed to be scalable and flexible, allowing organizations to adapt their GRC programs as they expand into new markets, introduce new products, or face new regulatory challenges.
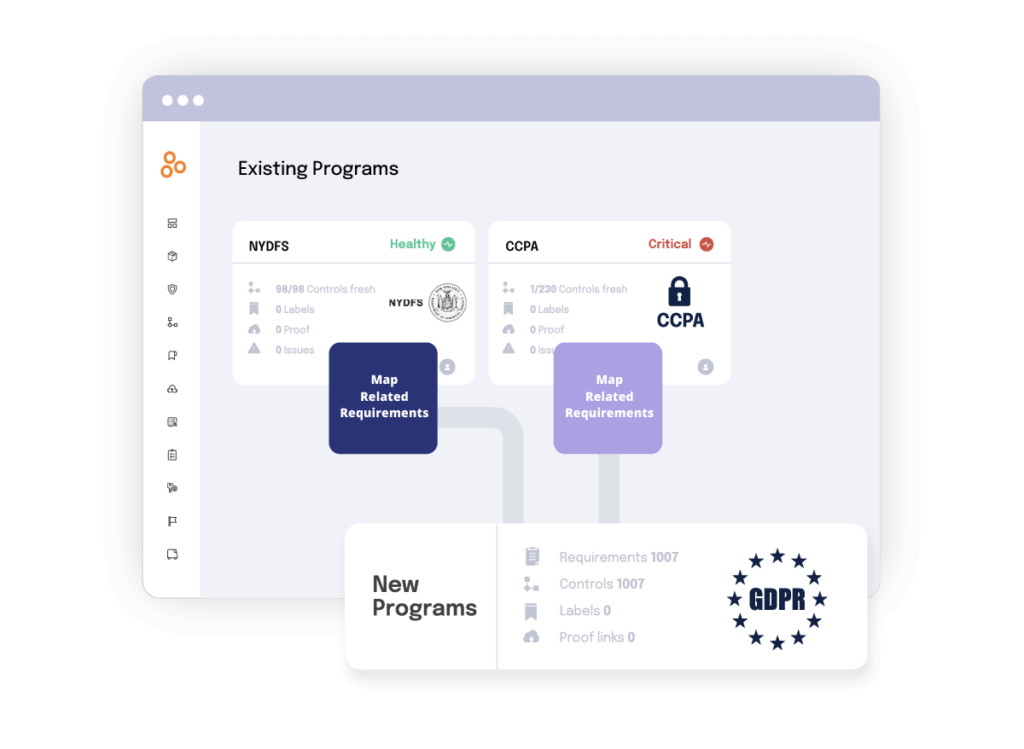
Hyperproof in action
Hyperproof has been successfully implemented by leading enterprises to enhance their GRC programs. Here are a few examples:
Outreach: Outreach, a sales engagement platform, leverages Hyperproof to streamline its compliance efforts and manage risks effectively. By using Hyperproof, Outreach was able to maintain consistent governance across its global operations and ensure compliance with relevant regulations.
Highspot: Highspot, a sales enablement and content management platform, built a continuous compliance program using Hyperproof. This enables Highspot to manage compliance requirements in real-time, mitigate risks proactively, and maintain a high level of operational efficiency.
A large enterprise with 22,000 employees: This organization uses Hyperproof (and our partner, HyperComply) to manage compliance and security questionnaires across its global workforce. By automating these processes, the organization was able to reduce the time and effort required to respond to compliance requests and improve overall governance.
Want to see Hyperproof in action?
Understanding what makes an effective GRC program:
The Hyperproof GRC Maturity Model
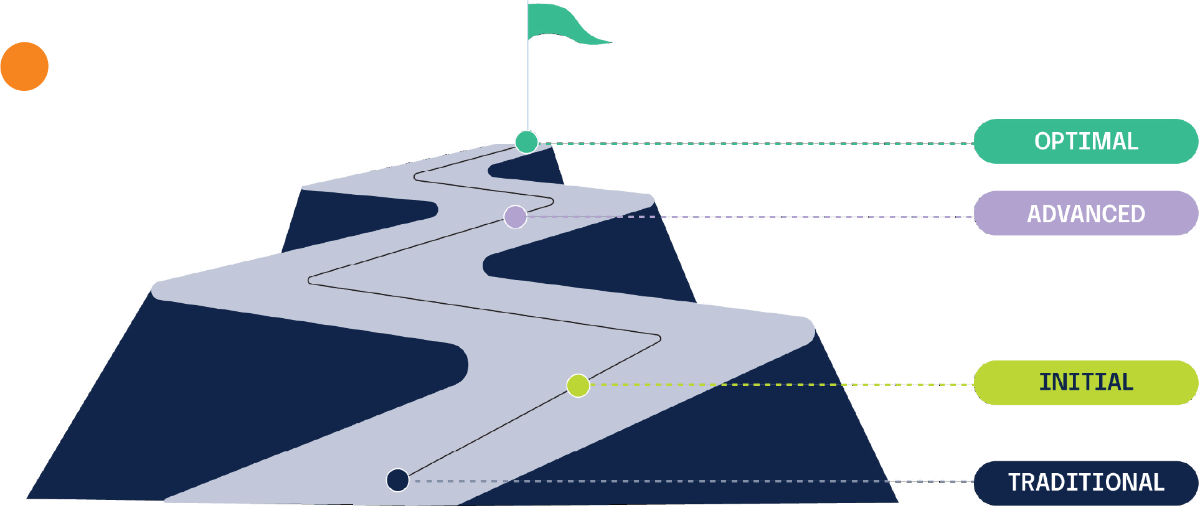
Understanding what makes a mature GRC program is key for organizations looking to gain a competitive advantage. Hyperproof’s Field CISO, Kayne McGladery, realized something was missing in the GRC market – a framework to assess an organization’s GRC maturity and provide actionable insight on how to build a case for change. Thus, the Hyperproof GRC Maturity Model was born.
Hyperproof’s GRC Maturity Model provides a roadmap for organizations to assess their current GRC capabilities and identify areas for improvement. The model outlines the stages of GRC maturity, from initial, ad-hoc processes to fully integrated and optimized systems.
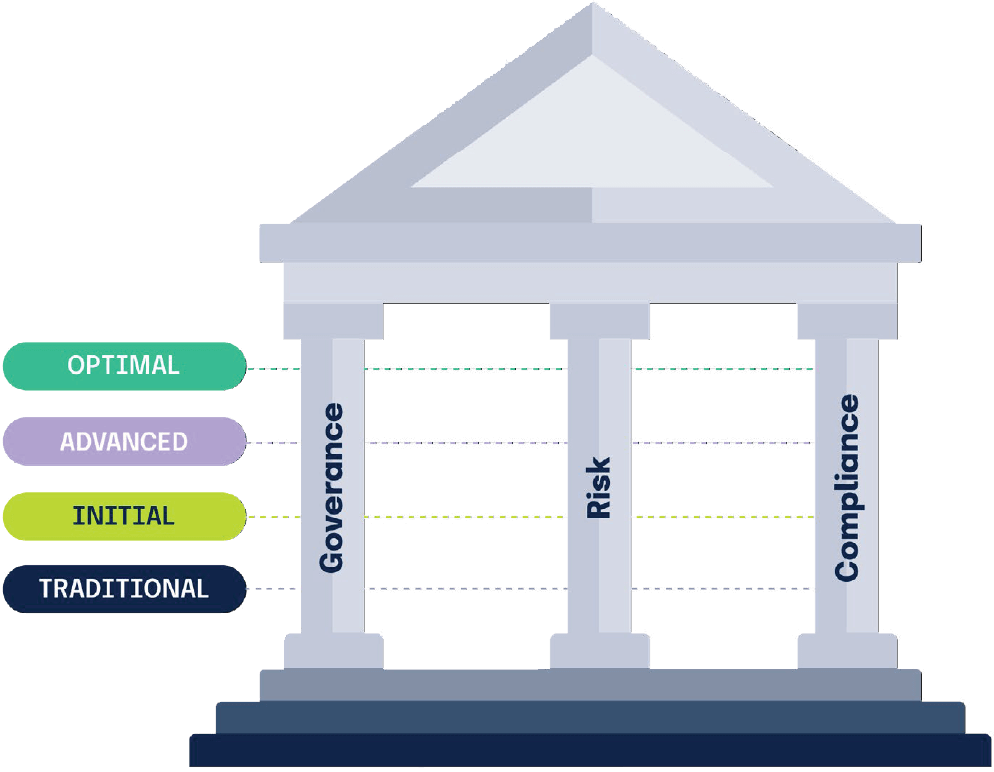
The model is segmented into four levels:
Traditional: reactive with insufficient or no planning
Initial: beginning to define processes at a departmental level
Advanced: establishing defined, repeatable processes at the organizational level
Optimal: proactively using measurements to continuously improve performance
Given the growing market of tools for GRC, security, and privacy management (all of which are related and support one another), using this framework can help mitigate knee-jerk reactions where stakeholders jump too quickly into conversations about purchasing software (and potentially end up overspending on tools without actually mitigating key risks).
Building up GRC capabilities from scratch: 5 key steps
In addition to the GRC Maturity Model, here are five key steps you can take to iteratively improve your GRC capabilities. These elements are the foundation for any GRC function.
1. Sort out governance questions
GRC affects the whole business and cannot be the sole responsibility of a single individual or a department. Board members, senior leadership, IT leaders, product leaders, business operators, and compliance professionals all have roles to play. For example, IT and security managers implement specific security controls as part of the cybersecurity risk management process.
Developers must know what encryption standard to use during software development and follow the designated process to review code for security gaps. Senior leadership must set the tone from the top, dictate the organization’s risk tolerance profile, and approve employee reward plans. HR plays a role in influencing employees to complete compliance training on topics such as data privacy and cybersecurity awareness.
You need to determine who will be accountable for your GRC compliance program, what responsibilities reside with each key player, how GRC information will be shared and escalated, and what resources will be dedicated to GRC.
Coordination and effective collaboration matter. A compliance officer (or the technology leader stepping into that role) needs to make sure that different issues are routed to the right group and that there’s no duplication of effort or groups operating at cross-purposes.
Roles of key stakeholders in GRC success

Board/governing body
Provide oversight and high-level directions to management, including setting the mission, vision, and values, as well as risk appetite, risk tolerance, ethical guidelines, and a high-level statement of goals and objectives.
Communicate changes in objectives, decision-making criteria, and strategic plans to business operators, risk, compliance professionals, and audit professionals so they can ensure appropriate communication about the requirements, threats, and opportunities in return.

Chief Financial Officer (CFO)
The CFO helps managers by establishing and explaining the decision-making criteria related to the financial mindset of the organization. The support of CFO is very important to GRC success because the CFO can pull the “purse strings” to support the initiatives they deem most important to achieving organizational objectives (e.g., improving the organization’s security posture).

Risk/Compliance Manager/Internal Audit Manager
Risk and compliance may be separate roles in larger organizations, but often fall to one person or team in smaller organizations.
The risk manager looks at threats and opportunities presented to the organization and conducts periodic risk assessments.
The compliance manager makes sure the organization stays within certain boundaries (legally or internally mandated) while striving to meet objectives. This is achieved by using management actions and control.
The compliance leader and their team are responsible for the compliance program’s day-to-day operations. They collaborate with the CIO, business operators, and others to accomplish things.

Chief Information Officer (CIO)/Chief Technical Officer (CTO)/Head of Engineering
The Chief Information/Technical Officer establishes systems to ensure the organization collects and maintains information in a way so information is delivered to the right people or systems, at the right time, and in the right formats.
CIOs, along with IT, protect an organization’s information security and ensure the necessary technology resources and information are secured for this undertaking.
CTOs help design the GRC technology stack and work with business operators and compliance managers to determine what technology shall be used to meet organizational objectives.

Business Unit Operators and Managers
They are responsible for identifying and managing risks directly as they arise in business operations. They take responsibility for ensuring compliance and meeting performance objectives.

HR Leader
Human Resources role involves developing the code of conduct, an employee handbook, and compliance training. Along with the compliance leader, HR is responsible for ensuring employees know what’s expected of them and what to do to avoid risks and protect the organization.
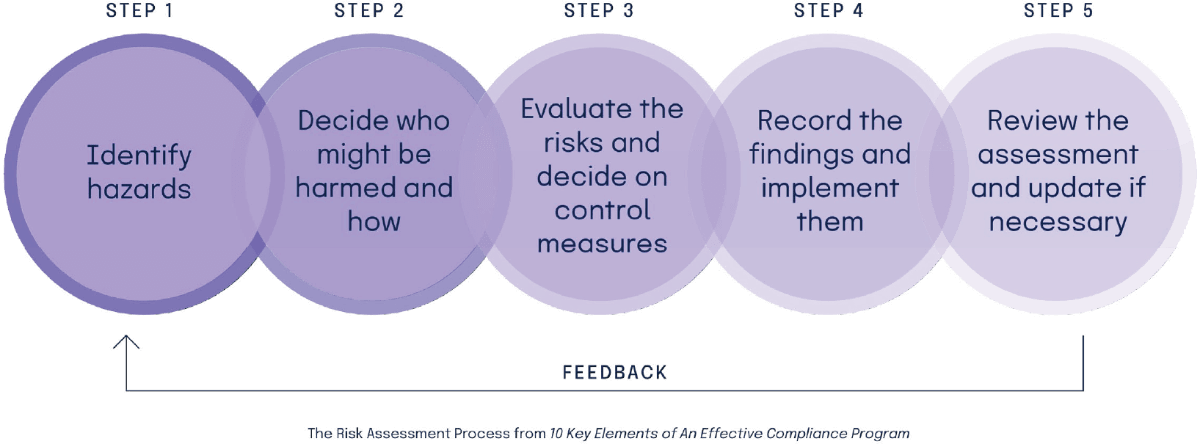
2. Assess risks
Your GRC activities must be customized to your organization’s business model, key objectives, risk landscape, risk tolerance profile, and regulatory context. An effective risk assessment should begin with a detailed picture of your company’s landscape: where are you doing business, with whom are you in business with (and plan to do business with), and what regulations cover businesses like yours?
An effective risk assessment must also include a clear picture of how your organization operates. Map out the “who, what, where, when, and how” of day-to-day operations happening on the ground in your company. In addition, make sure to evaluate your vendor relationships, especially vendors that process data on your behalf, as your organization may be held responsible for their missteps.
Lastly, as your business changes, your risks and the regulations you are subjected to will change, too. Risk assessments should be reviewed periodically or whenever events such as acquiring new companies, moving into new geographical or sector markets, corporate reorganization, and engagement with new customers happen.
3. Create basic InfoSec and data privacy policies and procedures
Every organization needs to have core policies and procedures to “get their house in order.” Consider the items below as homework to complete before you begin to pursue any particular compliance certifications (e.g., SOC 2® or ISO 27001). Once you have these basics in place, you will have made significant progress toward certification. Here is the list of the most important policies, documents and processes to work through:
Related Content
4. Determine the next compliance standard to implement and go through an audit
At this time, there are over a dozen well-known compliance standards and frameworks that detail security and data privacy requirements. For example, SOC 2®, ISO 27001, NIST, PCI-DSS, FedRAMP, and HITRUST are all standards concerning data security of information systems. CCPA, GDPR, and HIPAA are just a few examples of data privacy regulations covered companies must comply with.
Because frameworks are well-known and widely accepted, many organizations require their vendors to demonstrate compliance (e.g., produce a SOC 2® certification) as part of their procurement process. Depending on your target market, your customers and partners may require you to be compliant and certified against one or more frameworks.
Achieving compliance with these standards (and maintaining compliance over time) is a major part of any GRC program and requires dedicated resources and tools.
Which programs/frameworks does your organization need to be compliant with?
To determine which specific program/certification you need, it’s important to conduct customer research and hold internal conversations with key stakeholders. The following information will help you determine which framework(s) you should pursue:
Customer expectations should be a primary factor when selecting the compliance standards you want to adhere to. If you are selling products to enterprise customers, or if you’re selling products in highly regulated industries, you may need to demonstrate adherence with particular compliance frameworks before you can close a deal. Some customers may directly ask you to demonstrate a SOC 2® report (or something else that’s important in their industry) before signing a contract.

Partners can be another important stakeholder as you consider how much you need to invest in data security and privacy compliance. In general, larger enterprises are beginning to require proof of compliance from their smaller partners (e.g., Microsoft’s Supplier Privacy & Assurance Standards). Fortune 500 organizations often have their own GRC compliance programs for their partners, because they view strong privacy and security practices as mission-critical and essential to customer trust. It is common for the smaller partner to have to complete a set of specific compliance requirements dictated by the larger partner and go through an annual compliance review cycle in order to work with the larger partner.
Outside of customer and partner expectations, you’ll also want to examine the key architectural elements of the system you are designing and the function of each one. You will want to classify the data in your core system and understand its sensitivity level and how it is being handled. Consider how the data is manipulated by both code in the system and the people who have operational access to this data during all phases of system development, debugging, and operation.
Once you have your data classified, you can zero in on the most sensitive data and how it’s being handled. For example, if you are sharing private information with third parties, you will want to make sure how it should be handled is explicitly called out in your privacy policy, terms of service, and vendor contracts. SOC and ISO both include security requirements for these areas and, therefore, may be good programs to consider for your needs.

Last but not least, keep in mind that many of the frameworks have overlapping requirements — so one process or one internal control may satisfy requirements in multiple frameworks. For example, ISO 27001 builds upon SOC 2®, and it overlaps significantly with HIPAA. Many organizations can leverage their work for GDPR to meet CCPA requirements. You’ll want to do your own research and comparison to see how to tackle these standards in a time-efficient and cost-effective way.
On the security front, organizations like Adobe have reviewed a variety of compliance frameworks, determined where they overlap, and released a common controls framework that enables itself and its customers to comply with a multitude of certifications, standards, and regulations.
Their Common Controls Framework is open-source so any organization can leverage it. On the privacy front, Nymity, a privacy management software, has done the work of mapping both GDPR and CCPA requirements and identified a set of privacy management activities and technical and organizational measures that are relevant to both.
How to prepare for an audit: 6 simple steps
Once you’ve determined which compliance standards you want to implement, you will go through the program planning, program launch, audit readiness assessment, and audit stages. Here are further details about the key steps you’ll need to take when preparing for an IT compliance audit:
Step 1: Develop a project plan
Implementing a new data security framework is like a project, and it must be managed closely. Develop a timeline, make sure the right people are involved, and ensure everyone understands the importance of successfully completing this project.
Step 2: Perform a risk assessment
Risk assessments are foundational to an effective compliance program. After all, your compliance measures should be tailored to minimize the risks that are material to your organization. To properly identify risks to your information systems, you’ll need to inventory your data assets, get a clear view of where your data resides, and understand who has access to what.
Step 3: Design and implement controls
Once you know your risks, you can develop internal controls to mitigate them. Controls are processes designed to provide assurance that your business is meeting its objectives in terms of security, data privacy, and the effectiveness of your operations.
Step 4: Document your work
During an audit, one of the main ways you will show compliance is through documentation. You should keep detailed records on your processes, policies, training, implementation, internal and external audits, and any other activities related to your compliance efforts because auditors will need them to verify the efficacy of your internal controls.
Step 5: Conduct an audit readiness assessment
To mitigate the risk of failing an audit, your organization should conduct a compliance audit readiness assessment before the formal audit. Although this is a voluntary exercise, it can be a highly beneficial exercise, especially if you’re going through an audit for the first time.
You can think of an audit readiness assessment as a “preparatory test” before the real test or as your dress rehearsal before a performance in front of a live, paying audience. It’s an opportunity to discover weaknesses in your internal control environment so you can fix those issues before the formal audit happens.
During an audit readiness assessment, which should ideally happen a couple of months before the formal audit, the auditor will talk with the key personnel involved in compliance within your organization. These interviews allow auditors to understand your key policies and compliance processes. Once their interviews are complete, your auditor will write up a report outlining the gaps in your program or areas where your organization’s compliance efforts need more work.
Step 6: Conduct a formal audit
At this point, you should have completed an audit readiness assessment, seen what wasn’t working, and taken the time to shore up any aspects of your compliance program that needed work. If you’ve done all of this work beforehand and know what to expect from the auditors, this process should be relatively smooth and hopefully won’t uncover any gaps in your program you weren’t aware of.
A caveat about formal audits: it’s important to remember that a formal audit will not catch all of the potential vulnerabilities in your security or compliance programs. They are a point-in-time exercise and only give you a snapshot of how your compliance program is working at the time the audit is conducted. To adequately mitigate risk, it’s crucial to test your controls and remediate identified weaknesses on an ongoing basis.
5. Establish monitoring and evidence collection mechanisms
To inculcate a culture of ethics and compliance, you need to document your compliance measures and collect evidence on an ongoing basis to ensure your controls are working as intended. Along with potentially protecting your company from being fined in the event of an incident such as a data breach, having evidence of your compliance processes on hand can give you an opportunity to find your compliance blind spots. If your compliance evidence doesn’t exist, you’re likely not meeting standards.
Furthermore, if you establish a habit of collecting evidence on a regular basis, it makes external audits smoother and less stressful because you won’t need to scramble to find the evidence you need just days before the auditor shows up at your office.
Going forward, we can expect to see increasing regulations in areas such as user privacy, security, and others at the local, state, federal, and international levels. To reduce compliance risks, you’ll want to dedicate resources to help your organization stay up-to-date with new laws that may impact your business so that you can update your internal control environment to mitigate risks sufficiently.
For more details, check out our guide 10 Key Elements of an Effective Compliance Program.
GRC tools and software
Organizations today have access to a wide range of GRC tools and software designed to support their governance, risk management, and compliance activities. These tools can help organizations automate processes, manage risks more effectively, and ensure compliance with relevant regulations.
For enterprises that need to manage complex frameworks at scale, modern enterprise GRC solutions bring governance, risk, and compliance into a single, integrated platform.
What to look for in a GRC tool
When selecting a GRC tool, organizations should consider the following factors:
GRC tools market
Governance and Policy Management
Audit Management
Day-to-Day Compliance Operations
Ever since the OCEG formed as an organization and defined the GRC discipline, a myriad of GRC software companies have entered into the GRC space. As of fall of 2019, OCEG’s GRC Technology Solutions Guide has 40 defined categories of GRC technology. Gartner uses a different terminology to describe GRM tools (their terminology is “integrated risk management/IRM”), and has produced a Magic Quadrant covering 16 distinct vendors.
Hyperproof has done our research on the GRC tools market. We evaluated almost two dozen different tools and found that GRC tools tackle one or more of the following areas:
For an organization to sufficiently inoculate itself against risks and threats, it must first understand the different risks it has exposure to given its current business model and go-to-market plan. The organization must also determine its risk position or the level of risk that is considered “acceptable” to its senior leaders.
Within the GRC tools market, some software applications primarily focus on helping risk and compliance professionals and business leaders understand risks. The tools facilitate a risk identification process, help users develop a model of their risks, and categorize their risks according to various criteria (e.g., criticality level, likelihood). This risk assessment serves as the foundation for an organization to develop the appropriate governance structure and risk-mitigation policies and controls.
This top section of the GRC tools market is served by some of the most established vendors in the market. Most of these vendors’ clients are in highly regulated industries such as financial services and healthcare
Not sure what to look for in a GRC platform?
Governance and policy management

Once risks have been identified and policies are developed, organizations get into the block-and-tackle work of compliance. These include tasks such as establishing internal controls and operating procedures to ensure that policies are being followed and requirements are met, monitoring the internal controls environment, and testing various controls to make sure they are working as intended. This category of work also includes scheduling and preparing for external audits.
Security audits and third-party attestations have become increasingly important in B2B technology purchase decisions in today’s digital age. Not only do they provide an objective third-party verification of an organization’s compliance measures, which can alleviate enterprises’ concerns about a vendor’s security, but audits also provide helpful information about the soft spots or weaknesses in an organization’s internal control environment. In other words, findings from a security audit can serve as a recipe for reducing risks.
Through primary research, we’ve found that most organizations today rely heavily on formal audit findings to gain information about the health of their compliance program and the soft spots and weaknesses in their processes and systems. Outside of formal external audits — which provide a point-in-time view of an organization’s compliance posture — most small and midsize organizations do little to nothing to identify and address their vulnerabilities. Not addressing risks continuously (e.g., reviewing and updating internal controls) puts organizations in danger because they are exposed to risks and threats continuously.
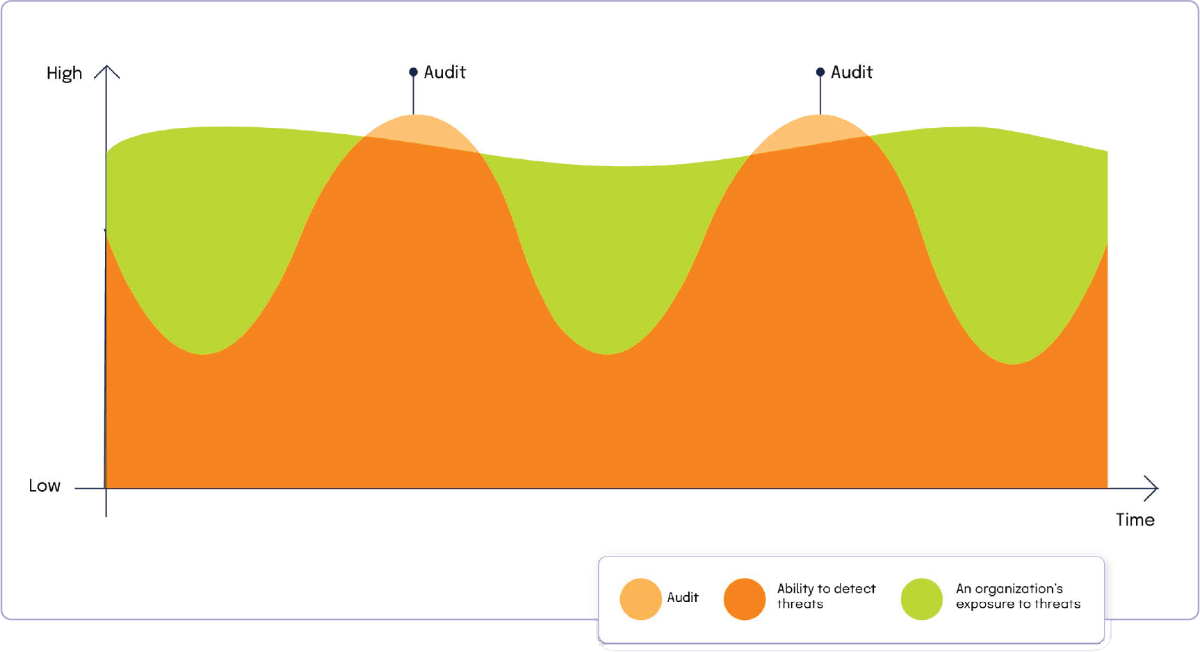
Going through an external audit is typically an extremely time-consuming process. Process owners across teams (IT, Accounting, Finance, Engineering) must submit hundreds of files and documents to their auditors to review. For even a single audit, it can take over 100 hours for a compliance team to produce, locate, verify, and organize all the documents and evidence they must submit to their auditors.
At this time, several companies tried to carve out a niche for themselves in the GRC tools market by building software to simplify and streamline the audit process. These tools are built to eliminate or reduce the amount of time compliance teams spend on manual processes. They come with features that help compliance teams and business process owners collaborate with auditors to gain visibility into controls, certifications, and PBC evidence requests. In general, audit management tools allow compliance and audit professionals to manage all PBC requests in a single place, centralize communication between process owners and auditors, and remind key process owners to complete their tasks on time.
While these tools do provide IT security and compliance professionals a better way to work with their auditors, they are not built to support users with the third, and arguably the most critical workstream of GRC: the ongoing, day-to-day management of risk and compliance projects.
Day-to-day compliance operations
To create adequate protection against today’s ever-evolving cyber threat landscape and keep up with new regulations, organizations need to treat compliance not as a point-in-time exercise but rather as an ongoing operational program.

Unfortunately, compliance professionals today are struggling to make the time for this ongoing, operational work. First, given how long it takes to prepare for external audits, compliance teams have little time to focus on other key tasks (e.g., keeping controls up-to-date, leveraging new security technology, updating policies, etc.). Second, given that compliance data tends to live in disparate systems and spreadsheets, it’s hard for compliance professionals to understand how well they’re solving for their risks and what else they need to do. For instance, when you have hundreds of security controls managed by a dozen different people, and half of those controls need to be reviewed quarterly, it’s all too easy for things to slip through the cracks.
Unfortunately, these issues pose significant negative costs to individuals and organizations: Compliance professionals are often overwhelmed and stressed out; they aren’t sure that control operators are keeping up with what they need to do. They are left with little time to devote to other strategic projects aimed at improving the security and compliance posture of their organizations. Organizations’ leaders are left in the dark about the real issues and risks.
That’s where compliance operations software comes in. ComOps software such as Hyperproof eliminates the tedious, repetitive tasks traditionally associated with managing compliance projects and audits, and helps compliance and security teams effectively collaborate with stakeholders to keep internal controls and evidence fresh on a continuous basis, which ultimately leads to reduced risks and improved security.
For example, after working with Hyperproof, Outreach, a market-leading sales execution platform, reduced audit prep time by 75% and saw a 50% reduction in time spent on evidence collection, collaboration, and project management.
Hyperproof does the job through 4 mechanisms:
Mechanism 1
Guided implementation of regulatory GRC requirements, industry standards, and compliance frameworks
Hyperproof has created a series of starter compliance templates to help organizations jump-start their journey to compliance. Currently, we’ve launched templates for the most popular cybersecurity and data privacy frameworks in the market, including SOC 2®, ISO 27001, GDPR, CCPA, PCI DSS, NIST SP 800-53, and more. Each template comes with requisite requirements and illustrative controls. Once you choose a template, you can easily upload existing files, tailor controls to their specific environment, create new controls and iterate your way to full compliance.
You can also upload your existing compliance framework (as a CSV file) into Hyperproof and manage it in the software. Once a program (e.g., SOC 2®) is up and running, Hyperproof will automatically notify process/control owners if and when any requirements change, so they know what they need to update/change to stay in compliance.

Mechanism 2
Collaboration and accountability
Many of us recognize that successful compliance efforts require cooperation from various stakeholders. Yet, compliance teams have traditionally had difficulty enticing cooperation from their business counterparts. Compliance Ops software facilitates this cooperation: compliance professionals/project owners can assign tasks to business stakeholders, explain their responsibilities, and remind them to complete their tasks on a cadence.
Business stakeholders do not need to learn the language of compliance or any new tools. They can receive notifications to complete their tasks through the tools they already use (e.g., Outlook, Slack, Gmail), complete the tasks in those tools, and have information routed back and reflected in Hyperproof.
Mechanism 3
Streamlined evidence collection
Hyperproof streamlines audit processes by eliminating administrative overhead from the entire evidence collection and management process. Hyperproof serves as a single source of truth for all of your evidence files. Once files have been uploaded into Hyperproof, a compliance project manager can link evidence to controls across multiple programs and multiple requirements, and retrieve the right file instantaneously through the search function.
With Hyperproof, you can retain a detailed trail of all former audits, both internal and external. The software can capture metadata with each evidence file, so new employees (or someone new to a particular audit) can use that information to immediately impact preparation activities. They will know where artifacts were sourced, when the last person did it, and from whom. It will reduce the time and confusion that comes with aggregating information to something almost trivial in the audit process.

Mechanism 4
Real-time feedback on audit preparedness
When managing many different programs, frameworks, and standards, having a holistic view of where things stand is no longer an optional output of the compliance function — it’s an expectation. Hyperproof can help compliance professionals meet that expectation.
Hyperproof not only provides the ability to manage multiple evidence files and controls across multiple programs, but it also provides users with real-time feedback on how prepared they are for upcoming audits through dashboards, freshness metrics, and other data visualization. Additionally, a user will know and be alerted as soon as something needs to be reviewed and refreshed.
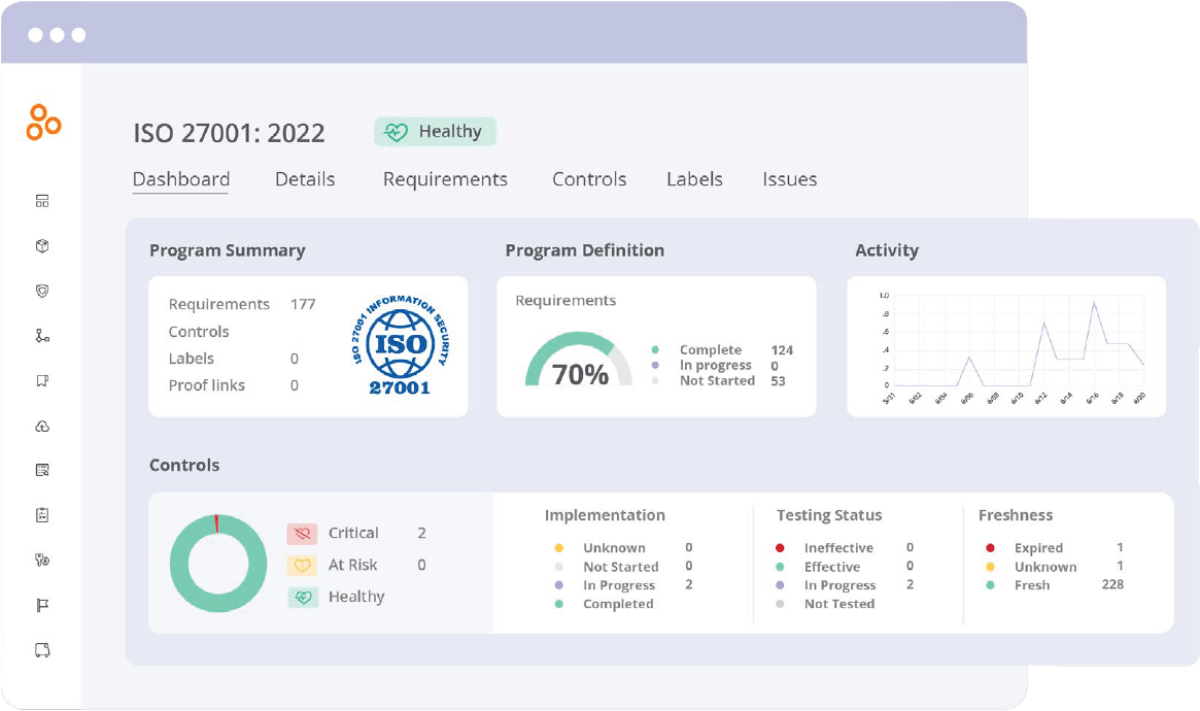
GRC and cybersecurity
Cybersecurity risks pose significant threats to organizations, from data breaches to operational disruptions. Integrating cybersecurity into the broader GRC framework ensures that these risks are managed effectively and in alignment with the organization’s overall objectives.
GRC frameworks play a crucial role in managing cybersecurity risks by:
Hyperproof’s role in cybersecurity
Hyperproof offers specific features designed to help organizations manage cybersecurity risks within a GRC program. These include:
Governance, Risk, and Compliance (GRC): Frequently Asked Questions (FAQ)
Staying updated with regulatory changes
This is one of the most persistent challenges of GRC as the regulatory landscape is constantly evolving. A few factors that make this challenging include:
Managing risk across complex global operations
For organizations with global operations, managing risks becomes exponentially more challenging due to:
Ensuring consistent governance across all business units
Effective governance ensures that an organization’s policies, procedures, and decisions align with its overall goals. However, ensuring consistent governance across decentralized or complex organizations presents its own set of challenges:
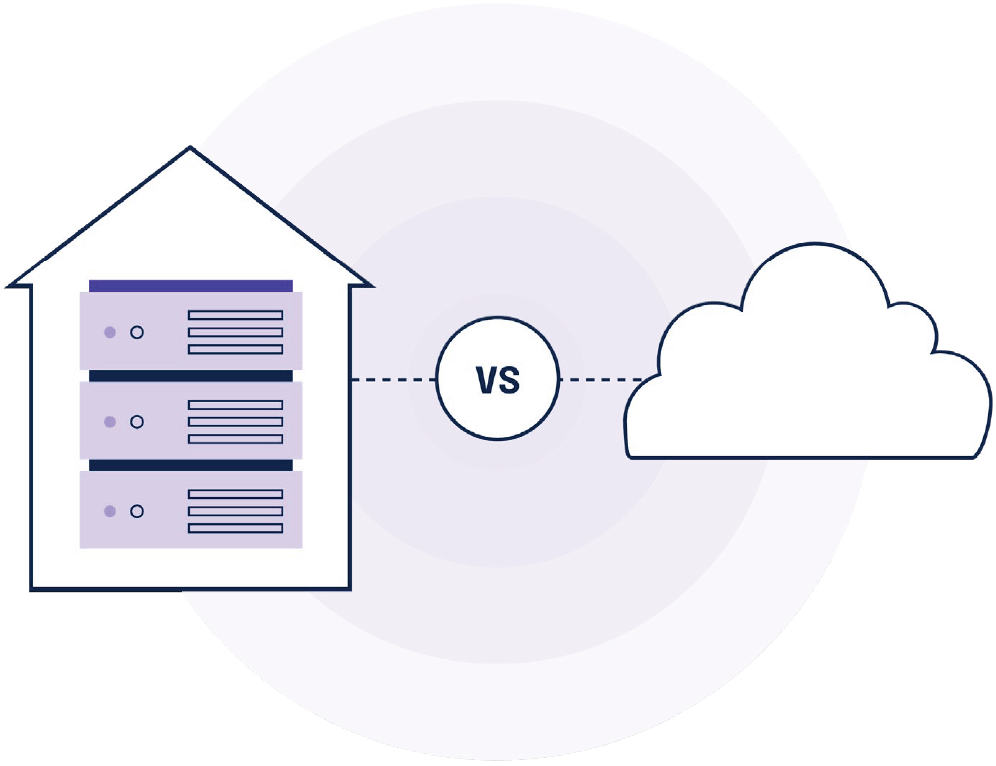
What is the difference between on-premise and cloud-based GRC?
On-premise GRC solutions are installed and managed on the organization’s own servers, while cloud-based GRC solutions are hosted on external servers and accessed via the internet. Cloud-based GRC solutions often offer greater flexibility and scalability.
Elevate your GRC program with Hyperproof
Governance, risk, and compliance are not just buzzwords—they are the pillars of a successful and sustainable business. By implementing a robust GRC program, organizations can achieve their business objectives, manage risks effectively, and maintain compliance with regulatory requirements. However, achieving GRC excellence requires the right tools and resources.
Hyperproof offers a comprehensive GRC platform that supports organizations at every stage of their GRC journey. From automated risk assessments to continuous monitoring, Hyperproof provides the tools needed to manage governance, risk, and compliance activities effectively. With Hyperproof, organizations can streamline their GRC processes, reduce risks, and ensure that they are always prepared for whatever challenges the business environment may present.
Ready to elevate your GRC program?
Request a demo and see how Hyperproof can help your organization achieve its GRC goals ›

Download the PDF












