A Comprehensive Guide to Information Security Management Systems (ISMS)
What is an ISMS?
An Information Security Management System (ISMS) provides a systematic framework for protecting valuable information assets from sophisticated threats, transforming security from an IT concern into a critical business function. Simply put, an ISMS safeguards sensitive data. It enables organizations to effectively manage risks, ensure business continuity, gain competitive advantage, improve cost efficiency, and establish legal protection, ultimately aligning security practices with organizational goals and stakeholder expectations.
By clearly defining responsibilities and implementing appropriate security controls, an ISMS enables organizations to manage risks effectively. Implementing an ISMS aligns with international standards like ISO 27001, enhancing business efficiency, reducing redundancies, and promoting scalable security practices.
Key components of an ISMS
An ISMS consists of components that protect an organization’s information assets, including:
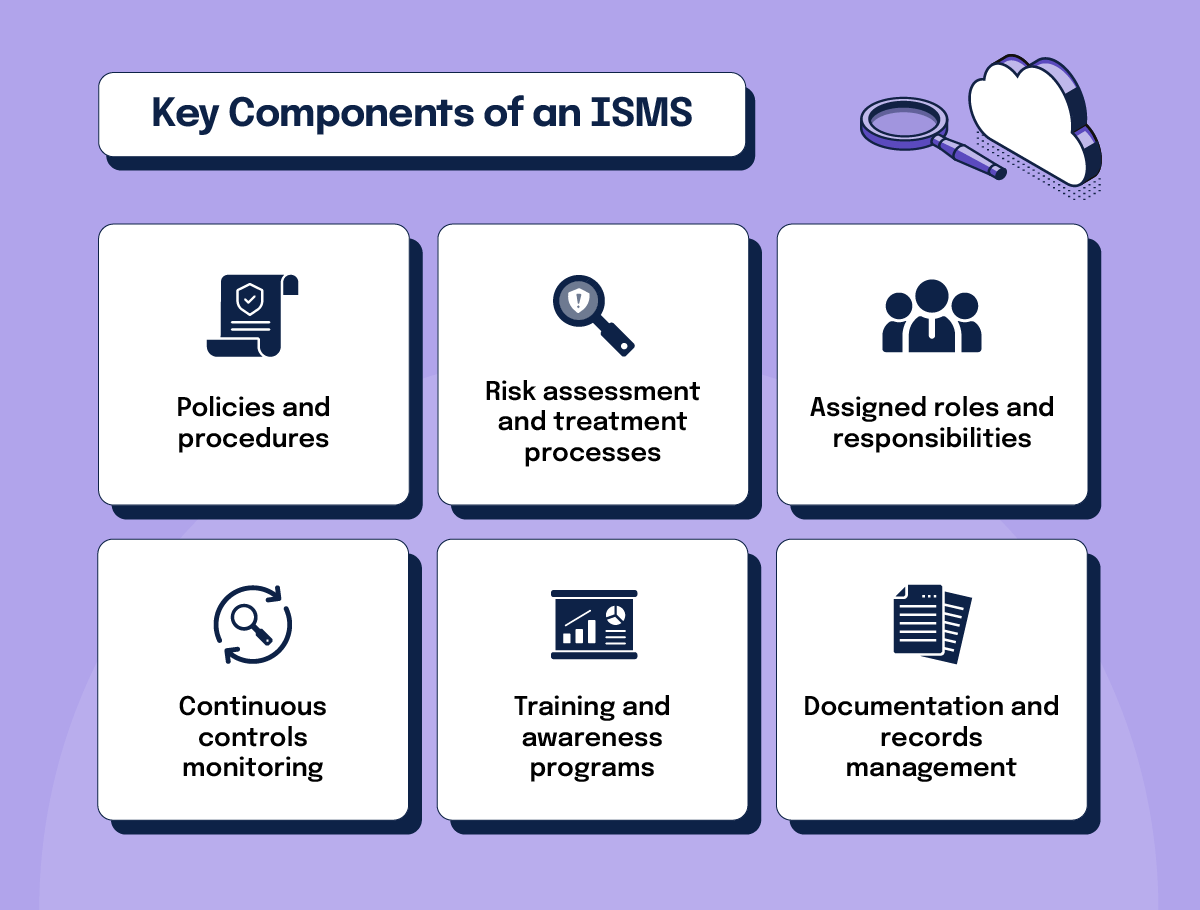
- Policies and procedures that establish the framework for managing information security and define the rules for handling data
- Risk assessment and treatment processes that identify potential threats and vulnerabilities so organizations can implement security controls
- Assigned roles and responsibilities, ensuring all personnel understand their role in maintaining security
- Continuous controls monitoring and review processes, which evaluate the effectiveness of security controls and allow for necessary adjustments
- Training and awareness programs, which keep employees informed about security policies and best practices
- Documentation and records management, ensuring all aspects of the ISMS are properly recorded and maintained for compliance and audit purposes
When should you adopt an ISMS?
By systematically identifying, assessing, and mitigating risks, organizations can implement security controls that protect sensitive data and align with legal obligations. Several signs indicate when an organization should formalize its ISMS:
- Frequent security incidents or data breaches that suggest inadequate security controls and processes
- Increasing regulatory requirements or client and partner pressure to comply with standards such as ISO 27001
- Challenges in managing security efforts across departments that require a more structured approach
- Inconsistent security practices and unclear policies that result in vulnerabilities and inefficiencies
- Lack of regular risk assessments and audits that lead to unidentified threats and security gaps
A formalized ISMS addresses these issues by providing a comprehensive framework for managing information security risks and ensuring compliance with regulatory and industry standards.
How an ISMS integrates with other compliance frameworks
Adopting an ISMS based on frameworks like ISO 27001 strengthens an organization’s ability to meet regulatory expectations, reducing the risk of legal penalties and reputational harm.
Many industry regulations emphasize the need for a structured security approach to ensure data protection and regulatory compliance. Key frameworks include:
General Data Protection Regulation (GDPR)
GDPR mandates stringent data protection measures for organizations handling the personal data of European Union citizens. Compliance requires robust security frameworks to safeguard sensitive information.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA establishes security standards for protecting healthcare patient information. Organizations must implement comprehensive controls to prevent unauthorized access and data breaches.
System and Organization Controls 2 (SOC 2®)
SOC 2® focuses on the security, availability, processing integrity, confidentiality, and customer data privacy. Organizations seeking SOC 2® compliance must implement and maintain effective security practices.
Beyond regulatory compliance, organizations across industries have successfully implemented ISMS frameworks to enhance security, risk management, and stakeholder confidence. Financial institutions adopt ISMS frameworks to comply with stringent regulatory requirements while safeguarding sensitive customer data, improving both security and trust. Healthcare organizations implement ISMS frameworks to protect patient information and meet HIPAA requirements, reducing the risk of data breaches. Technology companies align their ISMS with ISO 27001 to show a strong commitment to information security, which provides a competitive advantage when working with clients and partners.
Integrating an ISMS with enterprise risk management frameworks
An ISMS integrates into broader enterprise risk management (ERM) frameworks like the Committee of Sponsoring Organizations of the Treadway Commission (COSO) and the National Institute of Standards and Technology Risk Management Framework (NIST RMF) by providing a focused approach to managing information security risks within the overall risk landscape.
- COSO’s ERM framework emphasizes aligning risk management with organizational strategy, and an ISMS contributes by addressing specific information security risks that could affect strategic objectives.
- NIST RMF provides a structured approach to risk management, and an ISMS complements it by implementing detailed controls and processes to protect information assets.
Both frameworks benefit from an ISMS’s systematic risk assessment and treatment processes, which help identify, evaluate, and mitigate security risks. Additionally, an ISMS supports continuous monitoring and improvement, ensuring that security measures remain effective and aligned with organizational risk management goals.
How to implement an ISMS
Let’s start with getting in-depth understanding of the processes and controls required to manage information security risks and maintain compliance with relevant standards and regulations. We’ll cover the requirements of ISO 27001 and ISO 27002, offering guidance on aligning internal security practices with these standards.
Who plays a role in managing an ISMS?
Effective ISMS governance requires a structured approach to defining roles and responsibilities to manage information security across the organization. This governance structure ensures that information security is not treated as an isolated function but as a fundamental component of business operations. These roles include:
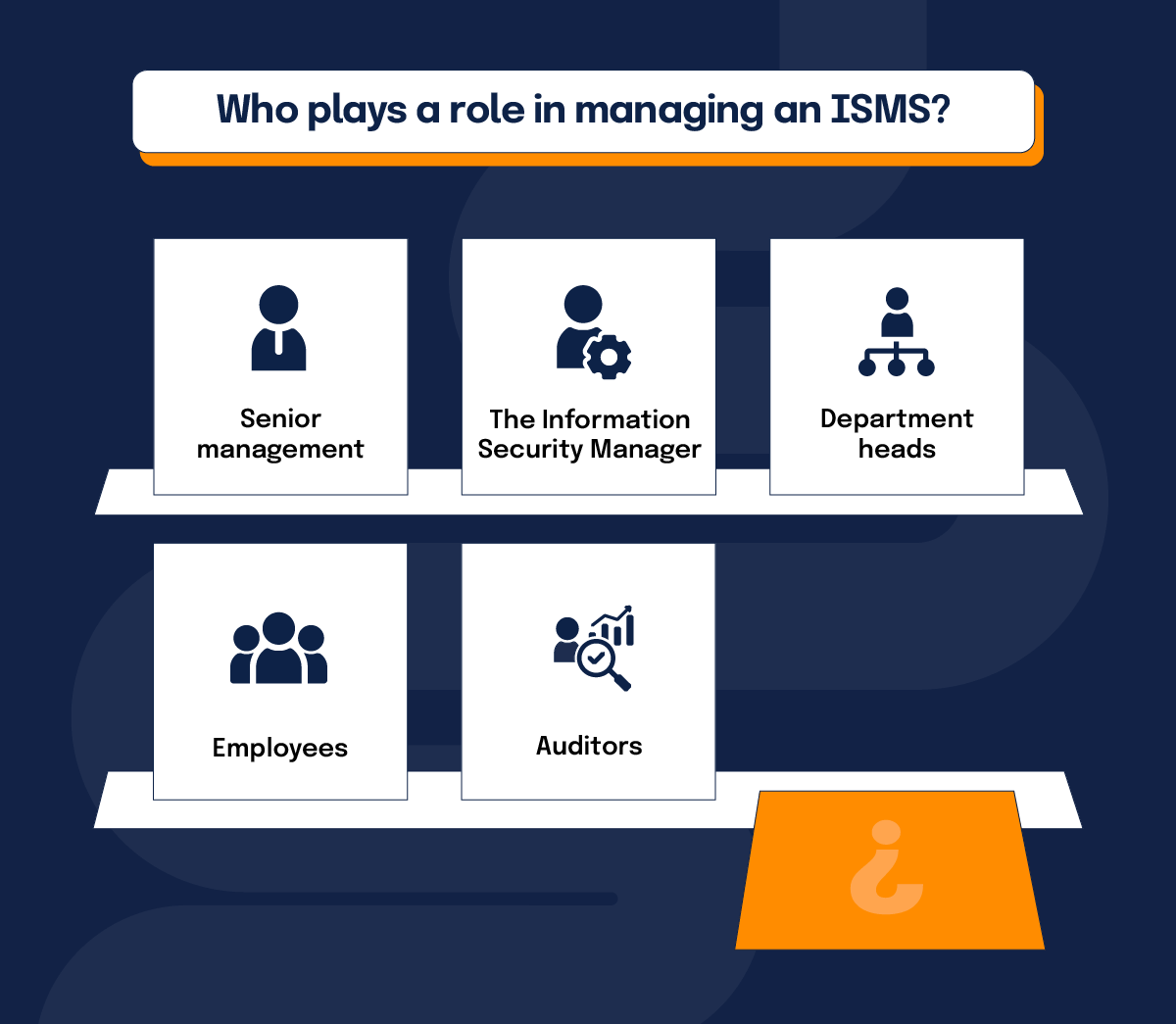
Senior management
Senior management provides strategic direction and ensures that the ISMS aligns with organizational goals and regulatory requirements. Their commitment is critical to securing resources and integrating security into the broader business strategy.
The information security manager/officer
The information security manager or officer oversees the development, implementation, and ISMS maintenance, coordinating efforts across departments to apply policies and controls.
Department heads
Department heads and managers ensure their teams adhere to security policies and integrate security practices into daily operations.
Employees
Employees play a vital role by following security guidelines and promptly reporting any incidents or vulnerabilities they encounter.
Auditors
Auditors and reviewers assess the effectiveness of the ISMS, identifying areas for improvement and ensuring that security measures remain aligned with organizational objectives and industry standards.
How to develop an ISMS
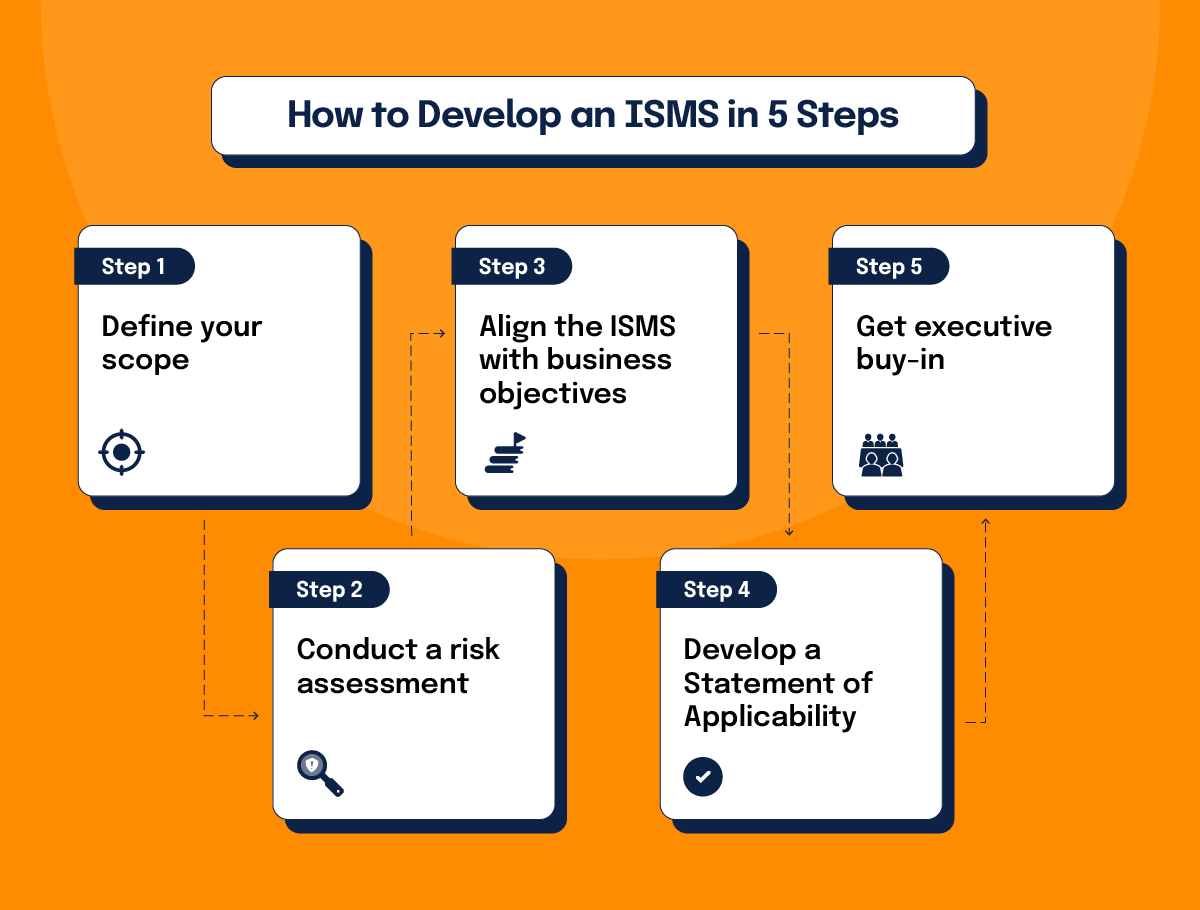
1. Define your scope
Establishing an ISMS begins with defining its scope, including identifying the boundaries and applicability of the system within the organization. A thorough risk assessment follows, focusing on identifying potential threats and vulnerabilities while evaluating their likelihood and impact. Organizations then develop a risk treatment plan to address identified risks by selecting appropriate security controls, often based on ISO 27002.
A well-defined information security policy serves as the foundation of the ISMS, outlining the organization’s commitment to information security and setting objectives aligned with business goals. Implementing the selected controls requires ensuring that all employees understand their roles and responsibilities through training and effective communication. Ongoing monitoring and measurement, supported by regular audits and reviews, ensures the ISMS remains effective and adaptable. Comprehensive documentation of processes supports compliance efforts and continuous improvement.
2. Align the ISMS with business objectives
For an ISMS to be effective, it must integrate with broader business objectives and corporate strategy. This requires identifying key business goals and determining how information security initiatives support them. Engaging senior management and key stakeholders early ensures alignment between security initiatives and business priorities while securing the resources necessary for implementation.
Establishing clear communication channels between the information security team and other departments ensures security measures are embedded in business processes and decision-making. Organizations should review and update the ISMS regularly to reflect changes in business objectives and external factors. Documenting how ISMS initiatives align with business strategy helps justify security investments and shows the value of information security to the organization.
3. Get executive buy-in and cross-functional support
Security leaders can gain executive support for ISMS implementation by clearly communicating its value in business terms. A well-structured business case should outline the potential risks of not implementing an ISMS, along with the benefits of improved security posture and regulatory compliance. Engaging executives early and involving them in key decision-making ensures alignment with organizational goals.
Fostering cross-functional collaboration is equally important. Demonstrating how the ISMS supports the objectives of different departments helps build support across the organization. Regular updates and transparent reporting on ISMS progress maintain stakeholder confidence and address concerns. Establishing a governance structure that includes representatives from multiple departments helps integrate the ISMS into the broader strategic framework.
4. Conduct a risk assessment and select controls
A comprehensive risk assessment informs ISMS controls by first identifying the information assets requiring protection, including data, systems, and processes. Organizations then assess potential threats and vulnerabilities, considering risks such as cyberattacks, human error, and natural disasters. Evaluating the likelihood and impact of these risks allows organizations to prioritize mitigation efforts.
Organizations must also establish a risk treatment strategy, selecting appropriate actions such as accepting, transferring, mitigating, or avoiding risks. Implementing security controls from ISO 27002 helps reduce risks to an acceptable level. Regularly updating risk assessments ensures they remain relevant as new threats emerge. Documenting the risk assessment process supports compliance requirements and provides a logical rationale for control selection.
5. Develop a Statement of Applicability
A Statement of Applicability (SoA) documents the security controls selected for implementation within the ISMS, based on risk assessment results. It specifies which controls from ISO 27002 do and do not apply and justifies their inclusion or exclusion.
The SoA serves as a reference for the organization’s security posture, demonstrating how identified risks are managed through specific controls. It provides a foundation for audits and compliance checks and ensures alignment between ISMS controls and risk management strategies. Clear documentation in the SoA helps communicate security measures to stakeholders, including regulators, clients, and internal leadership. Because risk environments change, organizations must update the SoA regularly to reflect changes in security requirements.
Want to learn how to write a Statement of Applicability?
Tools and resources for ISMS implementation
Organizations can leverage various tools and templates to streamline ISMS development:
- Document management systems facilitate the organization and retrieval of policies, procedures, and records.
- Risk assessment tools help identify and evaluate threats and vulnerabilities using a structured approach.
- Policy and procedure templates provide a foundation for developing security documents aligned with compliance requirements.
- Security software solutions automate processes such as access control, incident management, and compliance tracking.
- Training platforms deliver security awareness programs to employees, ensuring they understand their ISMS responsibilities.
Regularly updating these tools and templates ensures they remain effective and aligned with updated security standards and best practices.
Use ISO 27001 and ISO 27002 as a starting point
ISO 27001 and ISO 27002 together provide a comprehensive foundation for implementing and managing an ISMS. ISO 27001 specifies the requirements for establishing, maintaining, and continually improving an ISMS, while ISO 27002 offers practical guidance on selecting and implementing security controls.
ISO 27001: establishing an ISMS
ISO 27001 is an international standard that provides a structured framework for managing information security risks. It requires organizations to define security objectives and policies aligned with business goals and regulatory requirements, ensuring that security risks are systematically identified, assessed, and treated.
The core requirements of ISO 27001 are outlined in clauses 4 through 10, covering essential aspects of ISMS implementation:
- Clause 4: Understanding internal and external factors that affect the ISMS
- Clause 5: Leadership commitment and governance
- Clause 6: Risk assessment and security objectives
- Clause 7: Resource allocation, training, and communication
- Clause 8: Operational controls for security risk management
- Clause 9: Performance evaluation, monitoring, and measurement
- Clause 10: Continuous improvement and corrective actions
Organizations must also document their selection of security controls, detailing their applicability and effectiveness in mitigating identified risks. Regular audits and reviews ensure the ISMS remains effective and adapts to emerging threats and regulatory requirements.
ISO 27002: implementing ISMS controls
ISO 27002 complements ISO 27001 by providing detailed implementation guidance for information security controls. It acts as a reference for selecting controls during the risk treatment process, helping organizations apply best practices for managing risks to their information assets.
The controls outlined in Annex A of ISO 27001 are not mandatory, but provide recommended guidelines for organizations working toward compliance. ISO 27002 expands on these controls, offering practical advice on how to implement them effectively. This guidance includes specific implementation recommendations, best practices, and measurement approaches for each control.
For example, ISO 27002 provides detailed instructions on establishing access control mechanisms, developing incident response procedures, and implementing cryptographic safeguards. It also offers examples of documentation templates, security metrics, and implementation considerations that organizations should evaluate based on their risk profile. This ensures that organizations meet compliance requirements and establish security practices aligned with their operational and risk management needs.
By integrating ISO 27001 and ISO 27002, organizations can build a structured, effective ISMS that supports risk management, regulatory compliance, and continuous security improvements.
The three ISMS control categories
ISMS controls are classified into three major categories: organizational, technical, and physical controls. Each category of controls works together to establish a comprehensive security posture that mitigates various information security risks.
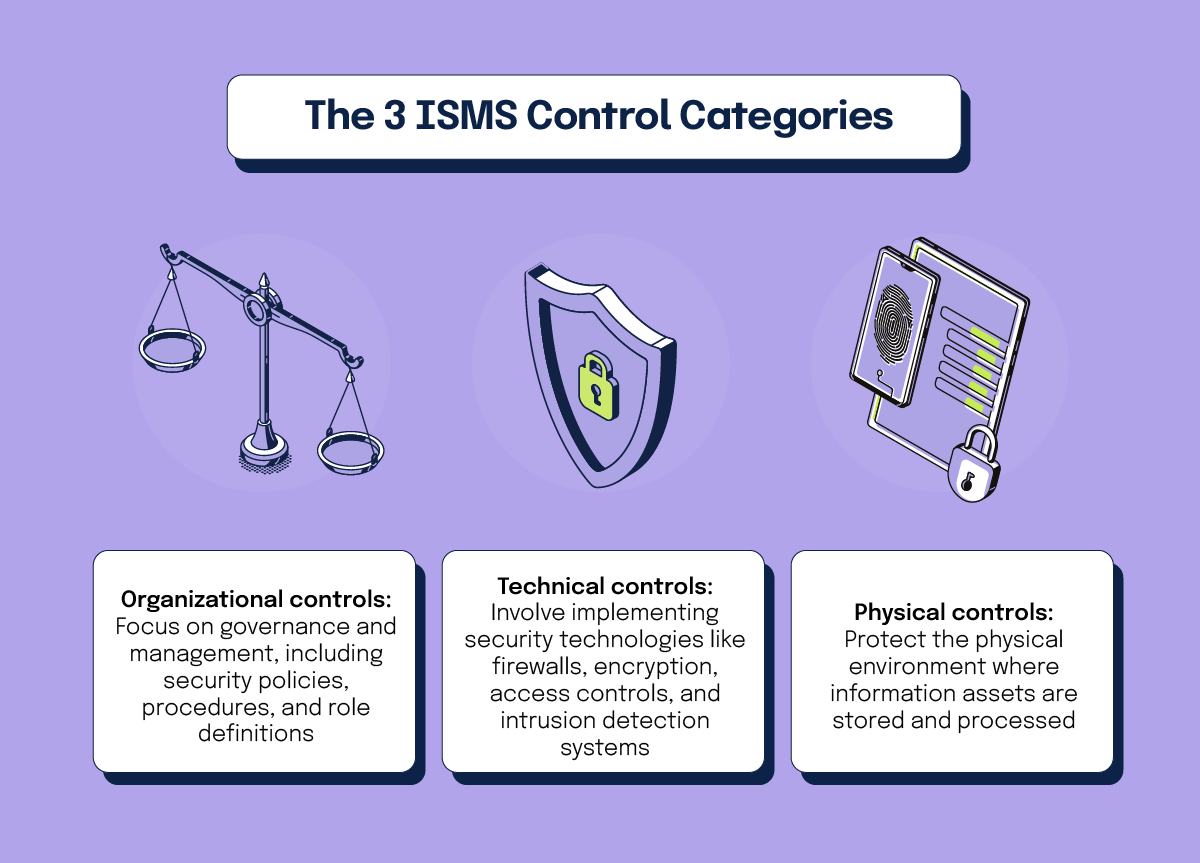
Organizational controls
Organizational controls focus on governance and management, including security policies, procedures, and role definitions. These controls ensure a structured approach to security risk management and clarify personnel responsibilities. Companies develop comprehensive security policies and procedures that define roles and responsibilities. Regular training sessions and awareness programs ensure employees understand and adhere to these policies.
Technical controls
Technical controls involve implementing security technologies like firewalls, encryption, access controls, and intrusion detection systems. Firewalls monitor and regulate network traffic, encryption technologies protect data in transit and at rest, and multi-factor authentication enhances access security. Intrusion detection and prevention systems identify and respond to potential threats in real-time.
Physical controls
Physical controls protect the physical environment where information assets are stored and processed. Access control systems such as key cards or biometric scanners secure facilities, while surveillance cameras monitor sensitive areas. Environmental controls, including fire suppression and climate regulation, protect hardware from physical damage.
How to prioritize ISMS controls
Organizations should prioritize controls based on a risk assessment that evaluates potential threats and vulnerabilities. Key considerations include:
Likelihood and impact
High-risk areas, such as those involving sensitive data or critical systems, should be addressed first.
Regulatory requirements
Compliance mandates may dictate the implementation of specific controls.
Business objectives
Controls should align with operational priorities to maximize security without disrupting core functions.
Maintaining, monitoring, and measuring ISMS effectiveness
Ensuring the ongoing effectiveness of an ISMS requires continuous monitoring, regular audits, and proactive adjustments to security policies and controls. By systematically assessing performance through internal reviews and key performance indicators (KPIs), organizations can maintain compliance, enhance security resilience, and respond effectively to emerging threats.

Regularly audit your ISMS
An ISMS must be regularly evaluated through internal audits, management reviews, and risk assessments to verify its effectiveness and alignment with organizational objectives. Internal audits ensure that security controls function as intended and effectively mitigate risks. Conducted periodically, these audits help identify non-conformities and areas for improvement. Management reviews assess ISMS performance by analyzing audit findings, risk assessments, and stakeholder feedback, supporting strategic decision-making for security enhancements.
Ongoing risk assessments play a critical role in identifying new threats and vulnerabilities, enabling organizations to adjust security controls and strategies accordingly. Incident monitoring and trend analysis further enhance ISMS effectiveness by detecting recurring security issues and highlighting areas that require attention. Regular updates to documentation and security policies ensure continued alignment with business goals and regulatory requirements, keeping the ISMS relevant over time.
Track KPIs
To assess and refine an ISMS, organizations should track key performance indicators (KPIs) that provide insight into security performance and compliance. These metrics include:
- Security incidents that have been detected and resolved, measuring how effectively threats are managed
- Incident response and recovery time, evaluating the efficiency of security operations
- Non-conformities identified in audits, highlighting areas that need corrective action
- Risk assessment frequency and results, demonstrating proactive risk management
- Compliance tracking, ensuring adherence to regulatory requirements and internal policies
By continuously monitoring these KPIs, organizations can identify trends, measure progress, and refine security strategies. This data-driven approach strengthens ISMS effectiveness, ensuring security measures remain aligned with risks and industry best practices.
Update your ISMS on a scheduled cadence
An effective ISMS must remain adaptable to emerging risks, technological advancements, and new regulatory requirements:
- Update risk assessment processes regularly to evaluate new threats and vulnerabilities.
- Stay informed by monitoring threat intelligence reports, engaging with industry forums, and tracking regulatory updates.
- Revise policies and procedures to reflect new security challenges and ensure compliance.
- Enhance training programs to educate employees on emerging threats and technologies.
- Implement continuous improvement initiatives to adjust security controls and strategies proactively.
- Conduct regular reviews and audits to verify that ISMS adaptations remain effective in mitigating additional risks.
By maintaining an agile ISMS, organizations can proactively address security challenges and regulatory shifts rather than reacting to them.
Build a culture of security awareness
A strong security culture enhances ISMS effectiveness by ensuring that security is embedded in daily operations. Organizations can foster this culture through:
- Comprehensive training programs that educate employees about security policies, threats, and their role in protecting information.
- Regular workshops and interactive sessions to reinforce best practices and engage employees in security discussions.
- Leadership commitment to security initiatives, demonstrating the importance of a security-first mindset.
- Encouraging open communication about security concerns and incidents, fostering accountability and proactive reporting.
- Recognizing and rewarding employees who demonstrate strong security practices, reinforcing positive behavior.
- Updating training materials with real-world scenarios to ensure relevance and practical application.
- Establishing clear reporting channels for security incidents, making it easy for employees to contribute to the organization’s security posture.
By embedding security awareness into organizational culture, companies can strengthen ISMS effectiveness and reduce the likelihood of security breaches.
Common challenges and misconceptions about ISMS
A frequent misconception about ISO 27001 is that certification guarantees complete security. In reality, the standard ensures a structured approach to managing security risks rather than eliminating them. Another misunderstanding is that all Annex A controls must be implemented, when in fact, only relevant controls need to be adopted based on risk assessment findings. Additionally, some organizations mistakenly view certification as a one-time achievement, whereas maintaining compliance requires ongoing audits and continuous improvement.
From a management perspective, challenges in implementing ISO 27001 and its supporting controls include resource allocation, employee resistance, and maintaining compliance over time. Security initiatives may require financial and human resources, and workflow disruptions can lead to employee resistance. Addressing these issues requires clear policies, effective training programs, and a commitment to ongoing security awareness. Regular reviews and updates to controls ensure their continued effectiveness amid changing regulatory and threat landscapes.
By integrating ISO 27001’s risk management framework with ISO 27002’s implementation guidance, organizations can establish a robust ISMS that strengthens information security while meeting regulatory and business requirements.
Overcoming resource constraints and employee resistance
Organizations often face challenges in securing adequate resources, gaining management support, and ensuring employee engagement when implementing an ISMS. Limited personnel can hinder the ability to establish and maintain necessary security controls, making it essential to prioritize initiatives based on risk assessments. Aligning the ISMS with business objectives and showing its value can help gain leadership support, ensuring long-term commitment and resource allocation.
Employee resistance is another common obstacle, as staff may be reluctant to adopt new security practices or view them as disruptions to established workflows. Providing comprehensive training and fostering a culture of security awareness can help mitigate this resistance. Additionally, organizations must stay compliant with new or updated regulatory requirements that necessitate continuous reviews and updates to ISMS policies and controls. Integrating security measures with existing business processes and systems requires careful planning and coordination across departments to ensure seamless adoption.
Addressing budget limitations and expertise gaps
Achieving ISO 27001 certification can also serve as a competitive advantage, demonstrating a commitment to security and regulatory compliance, particularly in business-to-business engagements where clients prioritize security assurances. However, resource constraints, including limited budgets and internal expertise, can hinder ISMS implementation. Organizations can overcome these challenges by prioritizing security initiatives based on risk assessments, ensuring that resources are allocated efficiently to address the most critical threats. For organizations lacking internal expertise, engaging external consultants or managed security service providers can offer valuable guidance on best practices and compliance requirements. Involving employees in the development and implementation of security controls fosters a sense of ownership and increases adoption.
Ensuring ISMS scalability as security needs grow
As organizations expand, their ISMS must remain adaptable to security requirements. Establishing flexible processes allows for adjustments as the business grows, reducing disruptions while maintaining security effectiveness. Modular security controls enable organizations to expand their ISMS in response to emerging threats, ensuring continued protection without significant operational overhauls.
Regularly updating risk assessments ensures that security measures remain aligned with the organization’s risk landscape. Scalable technologies, such as cloud-based security solutions, provide the infrastructure necessary to support growth efficiently. Clear governance structures help maintain consistency and accountability, while continuous training programs ensure employees remain prepared to handle increased security demands. Periodic reviews and audits help organizations refine their ISMS and identify areas for improvement.
Responding to a changing threat landscape
Maintaining ISMS effectiveness requires continuous monitoring, proactive threat intelligence, and adaptive security strategies. Organizations must regularly update risk assessments and adjust security controls to stay ahead of emerging threats. Threat modeling exercises allow security teams to anticipate attack vectors and develop proactive defense measures.
Employee training and awareness programs should be updated regularly to reflect the latest security threats, ensuring that staff remain vigilant. Collaborating with industry peers and taking part in information-sharing initiatives provides valuable insights into new risks and effective countermeasures. Regularly reviewing security policies ensures alignment with regulatory changes and industry best practices. Conducting both internal and external audits helps organizations validate the effectiveness of their security controls and identify areas that require adjustments.
Common mistakes to avoid when implementing an ISMS
Organizations frequently encounter challenges when implementing ISMS controls. Common mistakes include:
- Lack of alignment with business objectives: Controls should be directly linked to identified risks and strategic goals.
- Failure to conduct a thorough risk assessment: Overlooking key vulnerabilities can lead to ineffective resource allocation.
- Limited stakeholder involvement: Engaging teams across the organization fosters collaboration and ensures practical control implementation.
- Inadequate training and awareness programs: Employees play a crucial role in security; ongoing training helps reinforce best practices.
- Failure to regularly review and update controls: Security threats and regulatory requirements change over time, requiring periodic evaluations.
Establishing a structured schedule for control reviews and updates helps maintain an effective ISMS that adapts to emerging security risks and business needs.
Continuous improvement will set you up for success
Organizations at different maturity levels require tailored approaches to ISMS implementation. Whether you’re just beginning your security journey or refining an established system, the key to success lies in continuous improvement.
By regularly evaluating and enhancing their ISMS, organizations can strengthen their security resilience, maintain regulatory compliance, and build stakeholder trust. A well-maintained ISMS not only protects sensitive information but also integrates security as a fundamental component of business strategy, supporting sustainable growth and the competitive advantages afforded by external cybersecurity attestations like those from ISO 27001.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












