Cybersecurity Risk Management: Frameworks, Best Practices and Audit Readiness
In the modern landscape of cybersecurity risk management, one uncomfortable truth is clear: managing cyber risk across the enterprise is harder than ever. Keeping architectures and systems secure and compliant can seem overwhelming even for today’s most skilled teams.
More of our physical world is connecting to and being controlled by the virtual world, and as our business and personal information goes digital, the risks grow increasingly daunting. While it has never been more important to manage cybersecurity risk, it also has never been more difficult,” explains Dave Hatter, a cybersecurity consultant at Intrust IT and a 30-year industry veteran.
Why is managing cyber risk so much more complex today than ever before?
Start with the explosion of cloud services and third-party vendors contacting sensitive data. A Ponemon Institute study estimates the average company shares confidential information with 583 third parties. IT security teams have their hands full, managing complex infrastructures full of vendor risk.
Meanwhile, lawmakers and regulators are imposing a growing number of rules that require organizations to protect confidential data. Regulators now hold today’s enterprises accountable for third parties that process data on their behalf. As if handling your own risk wasn’t challenging enough, organizations must also manage vendor risk. Enterprises face increased responsibility with limited resources, all under the pressure of mounting regulations that carry steep penalties for non-compliance.
So, facing this multitude of obstacles, how can your organization hope to manage cybersecurity risk today?
It starts with building knowledge of the cybersecurity risk management process, identifying the critical action steps, and understanding the essential capabilities your organization will need to conduct assessments and effectively manage risk.
What is cybersecurity risk management?
Cybersecurity risk management is an ongoing process of identifying, analyzing, evaluating, and addressing your organization’s cybersecurity threats — and it begins with a shared understanding of the definition of cyber risk (also called cybersecurity risk or cyber security risk): the probability that a threat, system weakness, or human action will compromise the confidentiality, integrity, or availability of information systems, resulting in financial, operational, or reputational impact. You can find valuable benchmarks on cybersecurity risk management in the 2025 IT Risk and Compliance Benchmark Report. In many organizations, cybersecurity enterprise risk management is the discipline that connects technical security controls, business objectives, and board-level oversight into one coordinated program. In practice, cybersecurity risk analysis (sometimes called cyber security risk analysis) is the work of turning threats and vulnerabilities into ranked, decision-ready risks.
Cybersecurity risk management isn’t simply the job of the security team; everyone in the organization has a role to play. Often siloed, employees and business unit leaders view risk management separate from their business function. Regrettably, they lack the holistic perspective necessary to comprehensively and consistently address risk. That includes people-risk controls like access hygiene and training—often captured through an employee risk assessment cybersecurity lens.
So, who should own what part of security risk? The short answer is that everyone shares full ownership and responsibility. However, it becomes complicated when four business functions all have a stake in the game.
Each function has its agenda, often with limited understanding and empathy for others. IT leads with fresh ideas and new technologies, often viewing security and compliance as annoying roadblocks to progress. Security knows safety, but is often out of touch with regulations and the evolving technologies that drive them. The sales team is looking to keep their customers happy, clamoring for an efficient way to complete security audits. Compliance aims to prevent everyone from getting into trouble by strictly adhering to regulations, often operating without a thorough understanding of security.
To manage cybersecurity risk effectively, all functions must define their roles clearly and take responsibility for specific tasks. The days of siloed departments stumbling along in disconnected confusion are over. Today’s risk landscape requires a unified, coordinated, disciplined, and consistent management solution. Below are some key risk management action components all organizations must keep in mind:
Featured Cybersecurity Risk Management Framework: NIST Cybersecurity Framework
The cybersecurity risk management process
NIST SP 800-30 is a widely used cyber security risk assessment methodology for structuring preparation, assessment, communication, and ongoing maintenance.
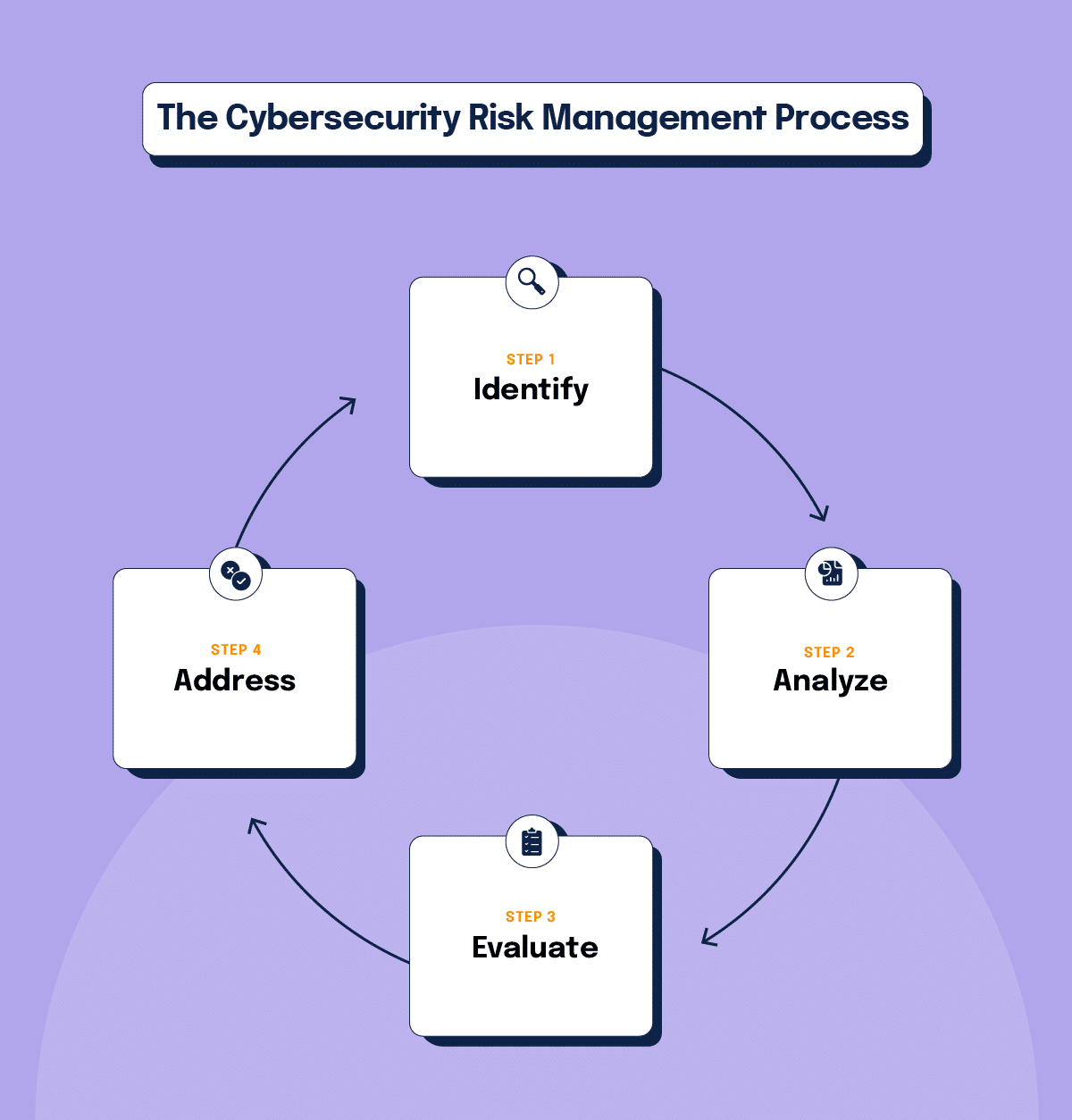
When it comes to managing risk, organizations generally follow a structured cybersecurity process, beginning with establishing the scope and objectives of risk management. This is followed by identifying risks that could impact the organization’s objectives. Next, risk is assessed to understand the likelihood and the potential impact. In the risk evaluation step, risks are compared against organizationally defined tolerances to prioritize risks for decision-making. This is where cyber security risk analytics becomes especially valuable – helping teams quantify likelihood and impact, spot patterns across incidents, and prioritize treatments with more confidence.
Then, risk treatment strategies are developed and documented, which may include mitigating, transferring, or accepting risks. The implementation of these strategies may require that some controls be implemented or improved. Finally, continuous monitoring and review involves tracking the identified risks and evaluating the effectiveness of risk responses to ensure that the risks remain below the organizational risk tolerance.
The good news for organizations looking to assess their risk level is that plenty of help is available. Many organizations also partner with cyber security risk assessment companies to accelerate the first assessment and validate scoring. The National Institute of Standards created a third-party risk management framework known as NIST Special Publication 800-30 to guide federal information systems’ risk assessments. The 800-30 framework builds upon the guidance outlined in Special Publication 800-39.
It is closely related to Special Publication 800-53, a cybersecurity control framework that provides a catalog of security and privacy controls for federal information systems. Though NIST SP 800-30 isn’t mandatory in the private sector, it provides a helpful guide for all organizations to choose controls to mitigate risks.
Develop a cybersecurity risk management plan

Let’s explore each step of the cybersecurity risk management process in more detail to develop a plan.
Identify cybersecurity risks
Gartner defines IT risk as “the potential for an unplanned, negative business outcome involving the failure or misuse of IT.” In other words, what are the odds of an existing threat exploiting a vulnerability, and if so, how dire would the consequences be? Risk identification is the first step in the management process. Modern security teams have their hands full with the growth of IT systems, the explosion of regulations, and the complications of vendor management, creating potential risks around every corner.
When identifying risk, it is essential to start by understanding threats, vulnerabilities, and the consequences of their convergence.
Threats are circumstances or events with the potential to negatively affect an organization’s operations or assets through unauthorized access of information systems. Threats can manifest in various forms, including hostile attacks, human errors, structural or configuration failures, and even natural disasters.
Vulnerabilities can be defined as weaknesses in an information system, security procedure, internal control, or implementation that a threat source can exploit. Often due to inadequate internal functions like security, vulnerabilities can also be found externally in supply chains or vendor relationships.
Consequences are the adverse results that occur when threats exploit vulnerabilities. Their impact measures the severity of consequences, and your organization will need to estimate such costs when assessing risk. Keep in mind that these costs usually come from lost or destroyed information, service downtime, and regulatory or legal penalties, which can be a significant business setback for any organization.
How mature are your organization’s cybersecurity risk management practices? Find out now.

Assess cybersecurity risks
Risk assessments offer a valuable opportunity to emphasize the importance of security throughout your organization. Assessing risk enables your team to practice effective communication and cooperation, playing a critical role in future risk management.
What is your organization’s level of risk? Assessment is the all-important step when the answer becomes clear. Start by naming all assets or business systems and prioritizing their importance. If you need a repeatable way to run cyber risk assessments, the linked guide breaks down a practical cybersecurity risk assessment process with clear cybersecurity risk assessment steps and what to include in a defensible cyber risk assessment report. Second, identify all possible threats and vulnerabilities in your environment. This is where a cyber attack risk assessment and cyber threat risk assessment help you validate likelihood, impact, and realistic attack paths. At this point, address all known vulnerabilities with appropriate controls. Next, attempt to determine the likelihood of a threat event occurring and conduct a business impact analysis to estimate its potential consequences and cost impact. Your resulting risk determination will serve as a guide to inform risk management decisions and risk response measures moving forward.
The NIST Guide for Conducting Risk Assessments, discussed in Special Publication 800-30, can help your team with a four-step progression. Prepare for your assessment by clarifying your purpose, scope, constraints, and risk model/analytics to be used. Conduct your assessment to list risks by likelihood and impact, determining overall risk. These results will be shared and drive your team’s mitigation efforts across the enterprise. Finally, this guide helps maintain your assessment by continually monitoring environments.
Risk assessments are strengthened through the consistent application of documented organizational risk tolerance levels. In risk tolerance cyber security conversations, this simply means defining how much uncertainty you’re willing to accept before action is required. Clear guidance from the board or senior leadership team about what constitutes an unacceptable risk makes risk decisions easier, as it is unlikely that a risk exceeding a defined risk tolerance level will receive attention or resources. Organizations can determine their risk tolerance level by deciding how much uncertainty is acceptable while still striving to achieve their organizational goals. This starts by defining objectives, like increasing profits, and pinpointing potential risks, like high financial losses caused by shareholder lawsuits and governmental investigations related to a data breach. To document this, the organization records risk tolerances in a risk management policy or risk register.
Identify possible cybersecurity risk mitigation measures
Identifying and assessing risk is just the beginning. What is your organization going to do about the risk you find? What will your mitigation response be for managing risk? How will you manage residual risk? History tells us the most successful risk management teams have a thoughtful plan in place to guide their risk response strategy for risks above the organizational risk tolerance.
A simple cybersecurity risk management example: if vendor access to production data is high-impact, you might mitigate with least privilege + MFA, and transfer residual risk with insurance.
Organizations can choose to mitigate, accept, or transfer risks. Functionally, any risks that are below the organizational risk tolerance are considered ‘accepted’. Risk transference involves either contractually transferring responsibility for risk impacts to suppliers or vendors or purchasing cyber insurance to help absorb some of the fallout from a risk materializing. Beyond just financial transference, organizations must have actionable cybersecurity plans in place to ensure that when a risk does materialize, the team can contain the damage and restore operations with minimal disruption.
Organizations can also mitigate risks by selecting and applying controls, which include people, processes, or technology, like:
Smart organizations know to base their risk response measures and risk management posture on real data. They prioritize risks as well as mitigation solutions using concrete data from real-world applications.
That brings us to residual cybersecurity risk. This is the risk left over after applying all mitigation measures, the type of unavoidable risk you can’t do much about. You have two choices for residual risk:learn to live with it or transfer it to an insurance provider who will shoulder it for a fee. Cybersecurity insurance offers a last-ditch option for mitigating residual risk and is poised to become more popular as the cost of cyber incidents becomes easier to calculate.
It has become increasingly necessary for organizations to accurately estimate the costs of damage. When estimating damage costs of cybersecurity risk, you need to consider three types of expenses. Operational costs involve lost time or resources and are easy to calculate. Fiscal costs can include fines for non-compliance or lost income when existing clients defect or new opportunities are lost. The reputational cost associated with breaches that violate customer privacy and trust is the hardest to calculate.
Once your team has a clear view of the threat landscape, the next step is establishing a defensible methodology for cybersecurity risk prioritization. This ensures that your remediation efforts are focused on the vulnerabilities with the highest impact, rather than simply addressing the most recent or visible issues.
Use ongoing monitoring
Your organization has identified, assessed, and mitigated risks within your environment. In a perfect world, that would be enough. But as we know, change is a constant, and your team will need to monitor environments to ensure internal controls maintain alignment with risk.
Your organization will want to monitor:
Together, these monitoring streams are the backbone of data security risk management in regulated environments. This ongoing visibility should feed directly into your cyber security planning, keeping your cyber threat security plan current as regulations, vendors, and internal systems change.
Note on Efficiency: To prevent your risk management plan from becoming a static document, many organizations now leverage automated security compliance tools. These systems integrate directly with your tech stack to provide real-time validation of controls, ensuring that your risk posture is updated automatically as your environment changes. Effective cybersecurity vendor risk management requires more than just initial vetting; it demands a system that continuously tracks third-party compliance and alerts your team to potential security gaps in your supply chain before they become breaches.
Standards and frameworks that require a cyber risk management approach

In addition to NIST SP 800-53, several other cybersecurity compliance standards/frameworks contain best practices and requirements for managing cyber risk. These standards provide a common language and structure for enterprise risk management cyber security initiatives, helping teams align controls, assessments, and reporting across the organization. Most organizations choose at least one cybersecurity risk framework to standardize assessment, controls, and reporting. Below are the most well-recognized frameworks:
ISO/IEC 27001
The international standard for information security management. If you’ve ever asked “which ISO contains controls for managing and controlling risk?” the primary answer is ISO/IEC 27001 (with ISO/IEC 27002 providing more detailed control guidance). Clause 6.1.2 of ISO 27001 states that an information security risk assessment must:
NIST Cybersecurity Framework Version 2.0
NIST Cybersecurity Framework (CSF) 2.0 provides a comprehensive set of cybersecurity outcomes designed to help organizations of all sizes and sectors manage and reduce cyber risks. This voluntary framework encompasses a taxonomy of high-level cybersecurity actions across six critical security functions: Govern, Identify, Protect, Detect, Respond, and Recover. These functions aim to address a wide array of cyber threats, including malware, password theft, phishing attacks, DDoS, traffic interception, social engineering, and others, while also extending to emerging technologies, privacy risks, and supply chain risks.
Within the document’s Identify function, which falls under the broader goal of understanding cybersecurity risks, CSF 2.0 states that “the organization understands the cybersecurity risk to organizational operations (including mission, function, image, or reputation), organizational assets, and individuals.” Specifically, it recommends organizations take the following steps:
Additionally, NIST CSF 2.0 introduces the Govern function, which focuses on establishing mission-aligned policies and risk management strategies. It states that “the organization’s priorities, constraints, risk tolerances, and assumptions need to be established to support operational risk decisions.” This function underscores the importance of aligning cybersecurity efforts with organizational goals and stakeholder expectations.
NIST CSF 2.0 provides detailed guidance on managing supply chain risks through its Cybersecurity Supply Chain Risk Management (C-SCRM) processes. It calls for organizations to establish and implement systematic approaches to identify, assess, and manage supply chain risks by crafting strategies, ranking suppliers by criticality, establishing security requirements, and integrating these efforts into broader risk and incident response frameworks.
NIST Risk Management Framework
The NIST Risk Management Framework provides a process that integrates security, privacy, and cyber supply-chain risk management activities into the system development life cycle. The RFM approach can be applied to new and legacy systems, any type of system or technology (e.g., IoT, control systems), and within any type of organization, regardless of size or sector. The key steps in the framework include the following:
| Step | Purpose |
| Prepare | Essential activities to prepare the organization to manage security and privacy risks. |
| Categorize | Inform organizational risk management processes and tasks by determining the adverse impact with respect to the loss of confidentiality, integrity, and availability of systems and the information processed, stored, and transmitted by those systems |
| Select | Select, tailor, and document the controls necessary to protect the system and organization commensurate with risk |
| Implement | Implement the controls in the security and privacy plans for the system and organization |
| Assess | Determine if the controls are implemented correctly, operating as intended, and producing the desired outcome in terms of meeting the security and privacy requirements for the system and the organization. |
| Authorize | Provide accountability by requiring a senior official to determine if the security and privacy risk based on the system’s operation or the use of common controls is acceptable |
| Monitor | Maintain ongoing situational awareness about the security and privacy posture of the system and organization to support risk management decisions. |
NIST has prepared multiple guides to make it easier for organizations to implement the RMF, which can be accessed on the NIST site.
See how Hyperproof can help you implement a risk management process that helps you maintain a continuously secure posture.
The roles internal compliance and audit teams play in risk management
In mature organizations, enterprise cybersecurity risk management depends on internal compliance and audit teams to keep risk assessments, controls, testing, and remediation moving in a consistent loop. Risk management is a continual process that should always include re-assessment, new testing, and ongoing mitigation. Keep in mind that internal compliance and audit teams can significantly control risk moving forward. Below are eight ways they can help:
- Identify and assess risks
- Plan, scope, and stress test micro risks
- Identify controls
- Assess effectiveness of controls
- Map controls to requirements
- Monitor and automate controls testing
- Capture, track, and report deficiencies
- Drive ongoing improvement
Critical capabilities for managing risk

Assessing risk has never been easy, and thanks to ongoing cyberattacks and economic uncertainty, conducting risk assessments is more challenging than ever. What capabilities will your team need to navigate these current challenges?
Glad you asked. Below, we outline some critical capabilities your organization will need to conduct assessments and effectively manage risk today.
Collaboration and communication tools
As teams across the enterprise participate in risk assessment and mitigation phases, they will require effective communication tools. These tools should provide a clear conversation record for team members in different locations, time zones, or countries.
Risk management frameworks
Ensure your team leverages third-party risk management frameworks, such as NIST Special Publication 800-30, to inform risk assessment and management. These third-party frameworks can help audit teams perform a swifter, more precise gap analysis between compliance requirements and current operations.
Analytics
This versatile capability is at the heart of risk analytics for cyber security. It can help with root cause analysis, trend detection, and the predictive analysis of emerging risks, so you can prioritize mitigation based on real data rather than gut feel.
Single data repository
Here, risk, compliance, and security professionals can store risk assessments, test results, documentation, and other relevant information.
Issues management tools
These instruments organize assignments of specific mitigation steps and automate reminders to complete tasks promptly. They also notify senior executives if tasks aren’t completed.
Versatile reporting
The flexibility to present IT risk management reports to business unit leaders and senior executives in the most desired and usable format.
Cybersecurity risk management FAQs
What is cybersecurity risk management in simple terms?
Cybersecurity risk management is the ongoing cybersecurity process of identifying your key assets, understanding threats and vulnerabilities, estimating impact and likelihood, and then deciding how to treat each risk (mitigate, transfer, or accept) based on your defined risk tolerance levels.
Which ISO contains controls for managing and controlling risk?
For most organizations, ISO/IEC 27001 is the primary standard that contains structured requirements for managing and controlling information security risk, while ISO/IEC 27002 provides detailed guidance on specific controls.
Navigating the complexities of cybersecurity risk management in the modern landscape
Managing risk across the enterprise is more complicated than ever today. Modern security landscapes change frequently, and the explosion of third-party vendors, evolving technologies, and a continually expanding minefield of regulations challenge organizations.
With this backdrop, it has become critical for your organization to implement a Risk Management Process. Identify and assess to create your risk determination, then choose a mitigation strategy and continually monitor your internal controls to align with risk. Keep in mind that re-assessment, new testing, and ongoing mitigation should always play a prominent role in any risk management initiative.
In the final analysis, there’s no rest in the modern pursuit of risk management. It hardly seems fair in a climate of continuous and unparalleled change, with threats and vulnerabilities multiplying by the minute. However, with the help of analytics, collaboration/communication/issue management tools, and third-party risk management frameworks, innovative and successful organizations will continue to hold their own in the battle to manage IT risk and maintain security across the enterprise.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?












